前言
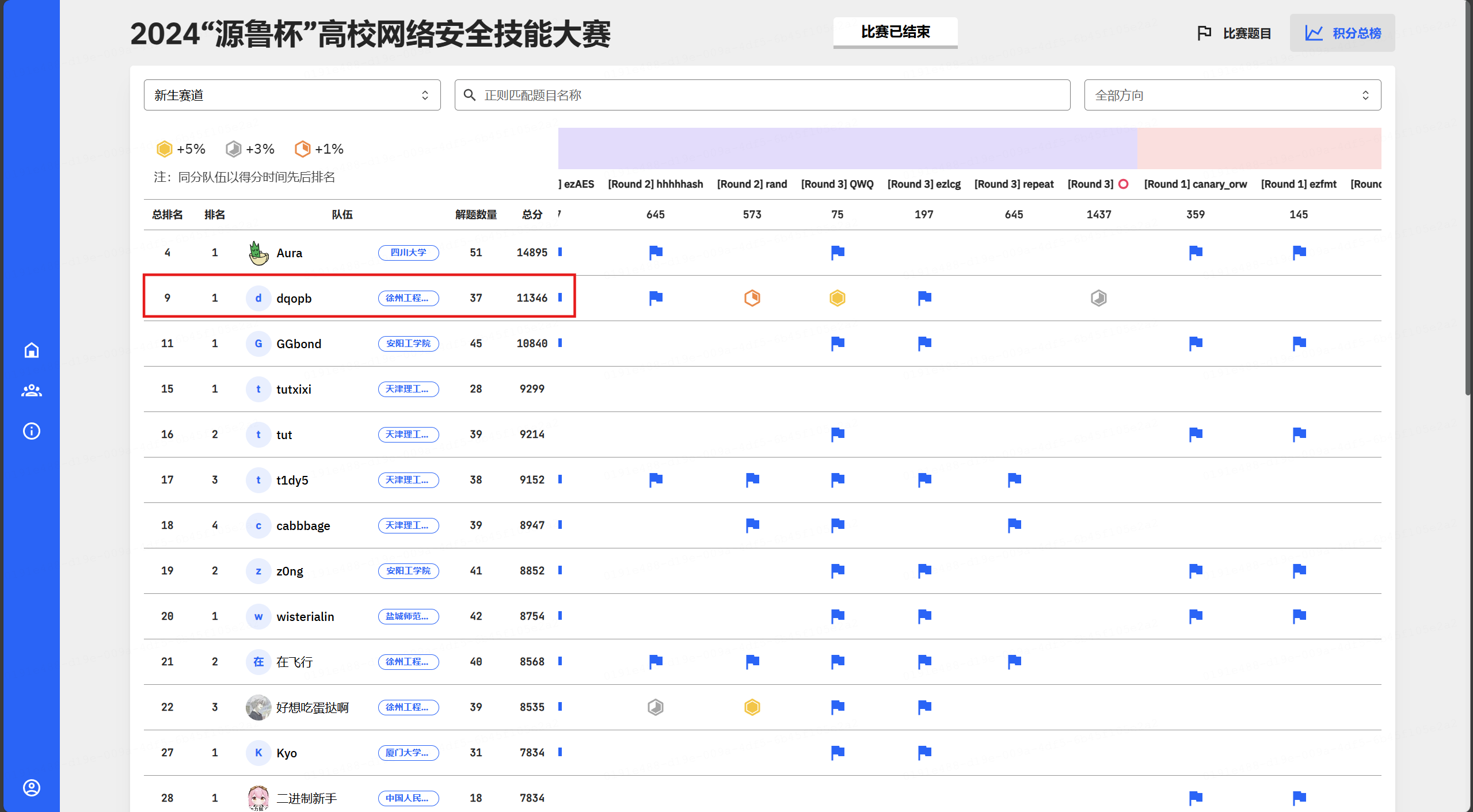
个人赛新生赛道第二,总排名第九,拿下二等奖
Re
twocry (二血)
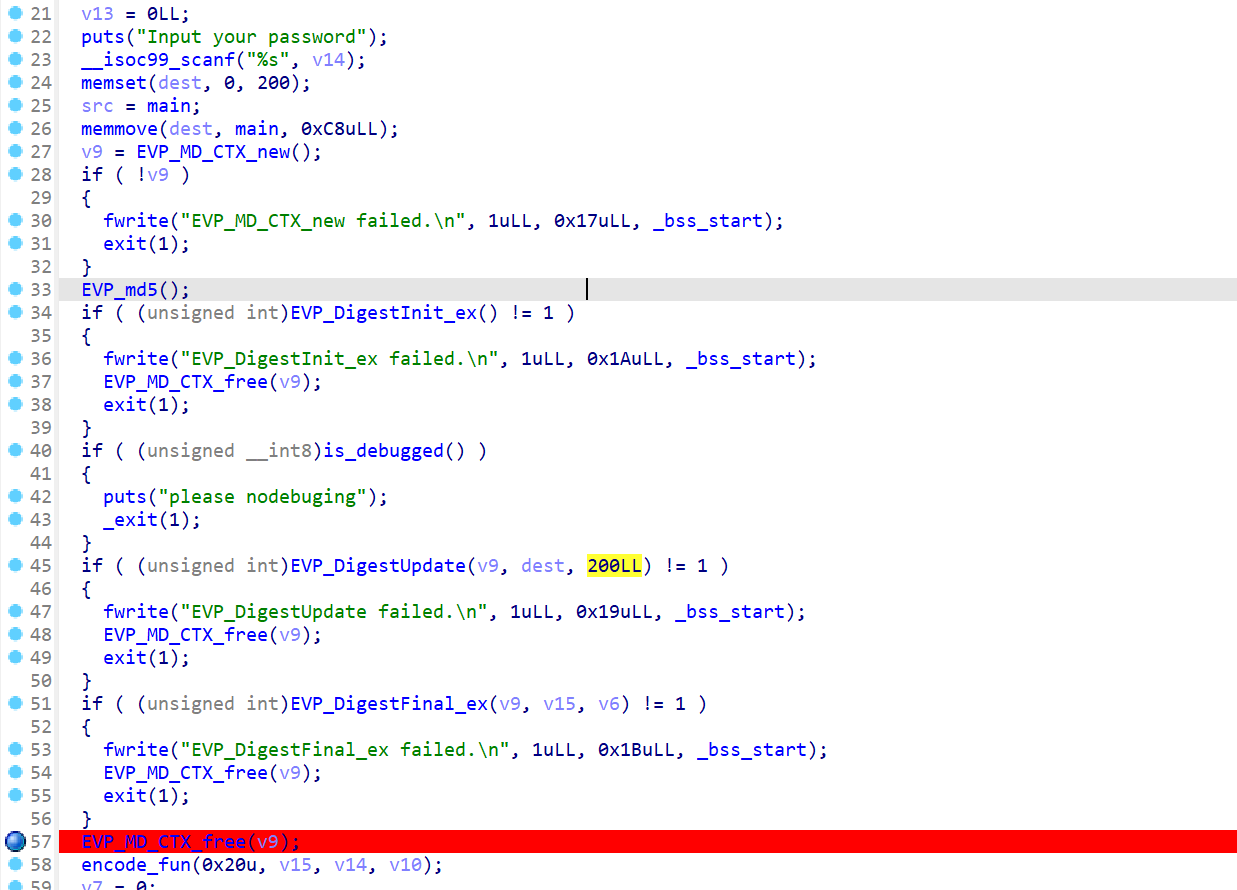
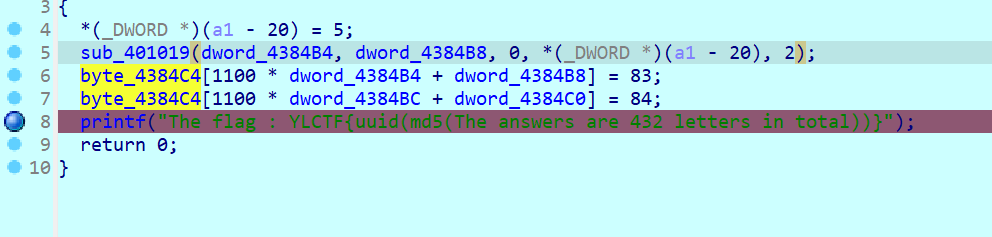
key是main的md5
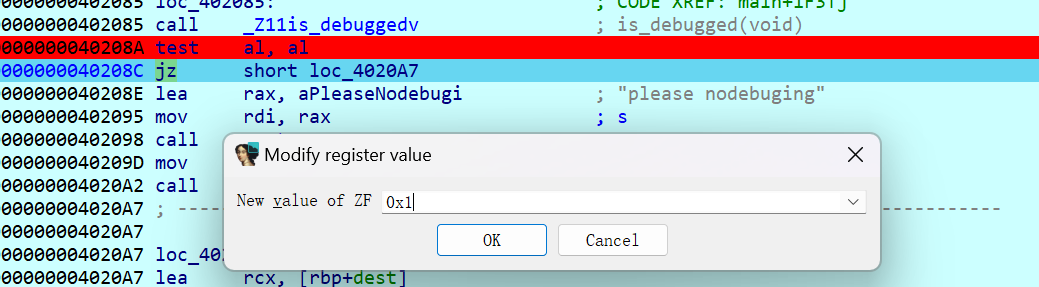
改ZF过反动调
key

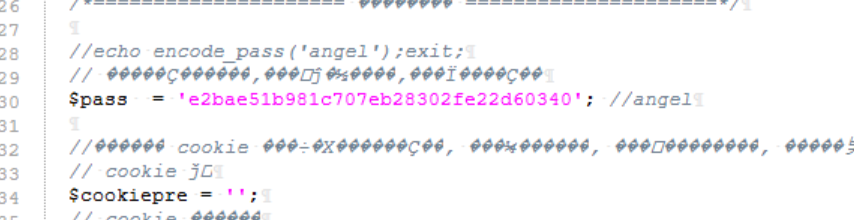
enc
sm4.h
#pragma once
#ifndef _SM4_H_
#define _SM4_H_
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
#define u8 unsigned char
#define u32 unsigned long
void four_uCh2uLong(u8* in, u32* out); //四字节转换成u32
void uLong2four_uCh(u32 in, u8* out); //u32转换成四字节
unsigned long move(u32 data, int length); //左移,保留丢弃位放置尾部
unsigned long func_key(u32 input); //先使用Sbox进行非线性变化,再将线性变换L置换为L'
unsigned long func_data(u32 input); //先使用Sbox进行非线性变化,再进行线性变换L
void print_hex(u8* data, int len); //无符号字符数组转16进制打印
void encode_fun(u8 len, u8* key, u8* input, u8* output); //加密函数
void decode_fun(u8 len, u8* key, u8* input, u8* output); //解密函数
/******************************定义系统参数FK的取值****************************************/
const u32 TBL_SYS_PARAMS[4] = {
0xA3B1BACC,
0x56AA335B,
0x677D919B,
0xB27022D1
};
/******************************定义固定参数CK的取值****************************************/
const u32 TBL_FIX_PARAMS[32] = {
0x00070e15,0x1c232a31,0x383f464d,0x545b6269,
0x70777e85,0x8c939aa1,0xa8afb6bd,0xc4cbd2d9,
0xe0e7eef5,0xfc030a11,0x181f262d,0x343b4249,
0x50575e65,0x6c737a81,0x888f969d,0xa4abb2b9,
0xc0c7ced5,0xdce3eaf1,0xf8ff060d,0x141b2229,
0x30373e45,0x4c535a61,0x686f767d,0x848b9299,
0xa0a7aeb5,0xbcc3cad1,0xd8dfe6ed,0xf4fb0209,
0x10171e25,0x2c333a41,0x484f565d,0x646b7279
};
/******************************SBox参数列表****************************************/
const u8 TBL_SBOX[256] = {
0xd6,0x90,0xe9,0xfe,0xcc,0xe1,0x3d,0xb7,0x16,0xb6,0x14,0xc2,0x28,0xfb,0x2c,0x05,
0x2b,0x67,0x9a,0x76,0x2a,0xbe,0x04,0xc3,0xaa,0x44,0x13,0x26,0x49,0x86,0x06,0x99,
0x9c,0x42,0x50,0xf4,0x91,0xef,0x98,0x7a,0x33,0x54,0x0b,0x43,0xed,0xcf,0xac,0x62,
0xe4,0xb3,0x1c,0xa9,0xc9,0x08,0xe8,0x95,0x80,0xdf,0x94,0xfa,0x75,0x8f,0x3f,0xa6,
0x47,0x07,0xa7,0xfc,0xf3,0x73,0x17,0xba,0x83,0x59,0x3c,0x19,0xe6,0x85,0x4f,0xa8,
0x68,0x6b,0x81,0xb2,0x71,0x64,0xda,0x8b,0xf8,0xeb,0x0f,0x4b,0x70,0x56,0x9d,0x35,
0x1e,0x24,0x0e,0x5e,0x63,0x58,0xd1,0xa2,0x25,0x22,0x7c,0x3b,0x01,0x21,0x78,0x87,
0xd4,0x00,0x46,0x57,0x9f,0xd3,0x27,0x52,0x4c,0x36,0x02,0xe7,0xa0,0xc4,0xc8,0x9e,
0xea,0xbf,0x8a,0xd2,0x40,0xc7,0x38,0xb5,0xa3,0xf7,0xf2,0xce,0xf9,0x61,0x15,0xa1,
0xe0,0xae,0x5d,0xa4,0x9b,0x34,0x1a,0x55,0xad,0x93,0x32,0x30,0xf5,0x8c,0xb1,0xe3,
0x1d,0xf6,0xe2,0x2e,0x82,0x66,0xca,0x60,0xc0,0x29,0x23,0xab,0x0d,0x53,0x4e,0x6f,
0xd5,0xdb,0x37,0x45,0xde,0xfd,0x8e,0x2f,0x03,0xff,0x6a,0x72,0x6d,0x6c,0x5b,0x51,
0x8d,0x1b,0xaf,0x92,0xbb,0xdd,0xbc,0x7f,0x11,0xd9,0x5c,0x41,0x1f,0x10,0x5a,0xd8,
0x0a,0xc1,0x31,0x88,0xa5,0xcd,0x7b,0xbd,0x2d,0x74,0xd0,0x12,0xb8,0xe5,0xb4,0xb0,
0x89,0x69,0x97,0x4a,0x0c,0x96,0x77,0x7e,0x65,0xb9,0xf1,0x09,0xc5,0x6e,0xc6,0x84,
0x18,0xf0,0x7d,0xec,0x3a,0xdc,0x4d,0x20,0x79,0xee,0x5f,0x3e,0xd7,0xcb,0x39,0x48
};
#endif
#include "sm4.h"
//4字节无符号数组转无符号long型
void four_uCh2uLong(u8* in, u32* out)
{
int i = 0;
*out = 0;
for (i = 0; i < 4; i++)
*out = ((u32)in[i] << (24 - i * 8)) ^ *out;
}
//无符号long型转4字节无符号数组
void uLong2four_uCh(u32 in, u8* out)
{
int i = 0;
//从32位unsigned long的高位开始取
for (i = 0; i < 4; i++)
*(out + i) = (u32)(in >> (24 - i * 8));
}
//左移,保留丢弃位放置尾部
u32 move(u32 data, int length)
{
u32 result = 0;
result = (data << length) ^ (data >> (32 - length));
return result;
}
//秘钥处理函数,先使用Sbox进行非线性变化,再将线性变换L置换为L'
u32 func_key(u32 input)
{
int i = 0;
u32 ulTmp = 0;
u8 ucIndexList[4] = { 0 };
u8 ucSboxValueList[4] = { 0 };
uLong2four_uCh(input, ucIndexList);
for (i = 0; i < 4; i++)
{
ucSboxValueList[i] = TBL_SBOX[ucIndexList[i]];
}
four_uCh2uLong(ucSboxValueList, &ulTmp);
ulTmp = ulTmp ^ move(ulTmp, 13) ^ move(ulTmp, 23);
return ulTmp;
}
//加解密数据处理函数,先使用Sbox进行非线性变化,再进行线性变换L
u32 func_data(u32 input)
{
int i = 0;
u32 ulTmp = 0;
u8 ucIndexList[4] = { 0 };
u8 ucSboxValueList[4] = { 0 };
uLong2four_uCh(input, ucIndexList);
for (i = 0; i < 4; i++)
{
ucSboxValueList[i] = TBL_SBOX[ucIndexList[i]];
}
four_uCh2uLong(ucSboxValueList, &ulTmp);
ulTmp = ulTmp ^ move(ulTmp, 2) ^ move(ulTmp, 10) ^ move(ulTmp, 18) ^ move(ulTmp, 24);
return ulTmp;
}
//加密函数(可以加密任意长度数据,16字节为一次循环,不足部分补0凑齐16字节的整数倍)
//len:数据长度(任意长度数据) key:密钥(16字节) input:输入的原始数据 output:加密后输出数据
void encode_fun(u8 len, u8* key, u8* input, u8* output)
{
int i = 0, j = 0;
u8* p = (u8*)malloc(50); //定义一个50字节缓存区
u32 ulKeyTmpList[4] = { 0 }; //存储密钥的u32数据
u32 ulKeyList[36] = { 0 }; //用于密钥扩展算法与系统参数FK运算后的结果存储
u32 ulDataList[36] = { 0 }; //用于存放加密数据
/***************************开始生成子秘钥********************************************/
four_uCh2uLong(key, &(ulKeyTmpList[0]));
four_uCh2uLong(key + 4, &(ulKeyTmpList[1]));
four_uCh2uLong(key + 8, &(ulKeyTmpList[2]));
four_uCh2uLong(key + 12, &(ulKeyTmpList[3]));
ulKeyList[0] = ulKeyTmpList[0] ^ TBL_SYS_PARAMS[0];
ulKeyList[1] = ulKeyTmpList[1] ^ TBL_SYS_PARAMS[1];
ulKeyList[2] = ulKeyTmpList[2] ^ TBL_SYS_PARAMS[2];
ulKeyList[3] = ulKeyTmpList[3] ^ TBL_SYS_PARAMS[3];
for (i = 0; i < 32; i++) //32次循环迭代运算
{
//5-36为32个子秘钥
ulKeyList[i + 4] = ulKeyList[i] ^ key[i % 16] ^ func_key(ulKeyList[i + 1] ^ ulKeyList[i + 2] ^ ulKeyList[i + 3] ^ TBL_FIX_PARAMS[i]);
}
/***********************************生成32轮32位长子秘钥结束**********************************/
for (i = 0; i < len; i++) //将输入数据存放在p缓存区
*(p + i) = *(input + i);
for (i = 0; i < 16 - len % 16; i++)//将不足16位补0凑齐16的整数倍
*(p + len + i) = 0;
for (j = 0; j < len / 16 + ((len % 16) ? 1 : 0); j++) //进行循环加密,并将加密后数据保存(可以看出此处是以16字节为一次加密,进行循环,即若16字节则进行一次,17字节补0至32字节后进行加密两次,以此类推)
{
/*开始处理加密数据*/
four_uCh2uLong(p + 16 * j, &(ulDataList[0]));
four_uCh2uLong(p + 16 * j + 4, &(ulDataList[1]));
four_uCh2uLong(p + 16 * j + 8, &(ulDataList[2]));
four_uCh2uLong(p + 16 * j + 12, &(ulDataList[3]));
//加密
for (i = 0; i < 32; i++)
{
ulDataList[i + 4] = ulDataList[i] ^ func_data(ulDataList[i + 1] ^ ulDataList[i + 2] ^ ulDataList[i + 3] ^ ulKeyList[i + 4]);
}
/*将加密后数据输出*/
uLong2four_uCh(ulDataList[35], output + 16 * j);
uLong2four_uCh(ulDataList[34], output + 16 * j + 4);
uLong2four_uCh(ulDataList[33], output + 16 * j + 8);
uLong2four_uCh(ulDataList[32], output + 16 * j + 12);
}
free(p);
}
//解密函数(与加密函数基本一致,只是秘钥使用的顺序不同,即把钥匙反着用就是解密)
//len:数据长度 key:密钥 input:输入的加密后数据 output:输出的解密后数据
void decode_fun(u8 len, u8* key, u8* input, u8* output)
{
int i = 0, j = 0;
u32 ulKeyTmpList[4] = { 0 };//存储密钥的u32数据
u32 ulKeyList[36] = { 0 }; //用于密钥扩展算法与系统参数FK运算后的结果存储
u32 ulDataList[36] = { 0 }; //用于存放加密数据
/*开始生成子秘钥*/
four_uCh2uLong(key, &(ulKeyTmpList[0]));
four_uCh2uLong(key + 4, &(ulKeyTmpList[1]));
four_uCh2uLong(key + 8, &(ulKeyTmpList[2]));
four_uCh2uLong(key + 12, &(ulKeyTmpList[3]));
ulKeyList[0] = ulKeyTmpList[0] ^ TBL_SYS_PARAMS[0];
ulKeyList[1] = ulKeyTmpList[1] ^ TBL_SYS_PARAMS[1];
ulKeyList[2] = ulKeyTmpList[2] ^ TBL_SYS_PARAMS[2];
ulKeyList[3] = ulKeyTmpList[3] ^ TBL_SYS_PARAMS[3];
for (i = 0; i < 32; i++) //32次循环迭代运算
{
//5-36为32个子秘钥
ulKeyList[i + 4] = ulKeyList[i] ^ key[i % 16] ^ func_key(ulKeyList[i + 1] ^ ulKeyList[i + 2] ^ ulKeyList[i + 3] ^ TBL_FIX_PARAMS[i]);
}
/*生成32轮32位长子秘钥结束*/
for (j = 0; j < len / 16; j++) //进行循环加密,并将加密后数据保存
{
/*开始处理解密数据*/
four_uCh2uLong(input + 16 * j, &(ulDataList[0]));
four_uCh2uLong(input + 16 * j + 4, &(ulDataList[1]));
four_uCh2uLong(input + 16 * j + 8, &(ulDataList[2]));
four_uCh2uLong(input + 16 * j + 12, &(ulDataList[3]));
//解密
for (i = 0; i < 32; i++)
{
ulDataList[i + 4] = ulDataList[i] ^ func_data(ulDataList[i + 1] ^ ulDataList[i + 2] ^ ulDataList[i + 3] ^ ulKeyList[35 - i]);//与加密唯一不同的就是轮密钥的使用顺序
}
/*将解密后数据输出*/
uLong2four_uCh(ulDataList[35], output + 16 * j);
uLong2four_uCh(ulDataList[34], output + 16 * j + 4);
uLong2four_uCh(ulDataList[33], output + 16 * j + 8);
uLong2four_uCh(ulDataList[32], output + 16 * j + 12);
}
}
//无符号字符数组转16进制打印
void print_hex(u8* data, int len)
{
int i = 0;
char alTmp[16] = { '0','1','2','3','4','5','6','7','8','9','a','b','c','d','e','f' };
for (i = 0; i < len; i++)
{
printf("%c", alTmp[data[i] / 16]);
printf("%c", alTmp[data[i] % 16]);
putchar(' ');
}
putchar('\n');
}
/*在主函数中实现任意字节加密与解密,并且结果正确*/
int main(void)
{
u8 i, len;
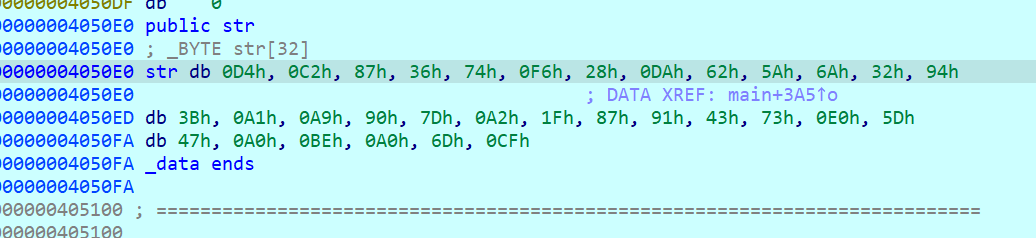
u8 encode_Result[64] = { 0xd4,0xc2,0x87,0x36,0x74,0xf6,0x28,0xda,0x62,0x5a,0x6a,0x32,0x94,0x3b,0xa1,0xa9,0x90,0x7d,0xa2,0x1f,0x87,0x91,0x43,0x73,0xe0,0x5d,0x47,0xa0,0xbe,0xa0,0x6d,0xcf }; //定义加密输出缓存区
u8 decode_Result[50] = { 0 }; //定义解密输出缓存区
u8 key[16] = { 0x6c,0xbc,0x9e,0xdd,0x36,0x34,0x2d,0x6a,0x15,0x4b,0x4c,0x49,0x36,0x8f,0xec,0x1b }; //定义16字节的密钥
//u8 Data_plain[18] = { 0x01,0x23,0x45,0x67,0x89,0xab,0xcd,0xef,0xfe,0xdc,0xba,0x98,0x76,0x54,0x32,0x10,0x01,0x23 };//定义18字节的原始输入数据(测试用)
//u8 Data_plain[32] = { 0x01,0x23,0x45,0x67,0x89,0xab,0xcd,0xef,0xfe,0xdc,0xba,0x98,0x76,0x54,0x32,0x10,0x01,0x23,0x45,0x67,0x89,0xab,0xcd,0xef,0xfe,0xdc,0xba,0x98,0x76,0x54,0x32,0x10 };//定义32字节的原始输入数据(测试用)
u8 Data_plain[16] = { 0x01,0x23,0,0,0,0,0,0,0,0,0,0,0,0,0,0 };//定义16字节的原始输入数据(测试用)
//encode_fun(sizeof(Data_plain), key, Data_plain, encode_Result); //数据加密
//printf("加密后数据是:\n");
//for (i = 0; i < len; i++)
// printf("%x ", *(encode_Result + i));
///*注意:此处解密函数的输入数据长度应为扩展后的数据长度,即必为16的倍数*/
decode_fun(0x20, key, encode_Result, decode_Result); //数据解密
printf("解密后数据是:\n");
for (i = 0; i < 0x20; i++)
printf("%c", *(decode_Result + i));
system("pause");
return 0;
}
ezmaze
ez迷宫,while前进
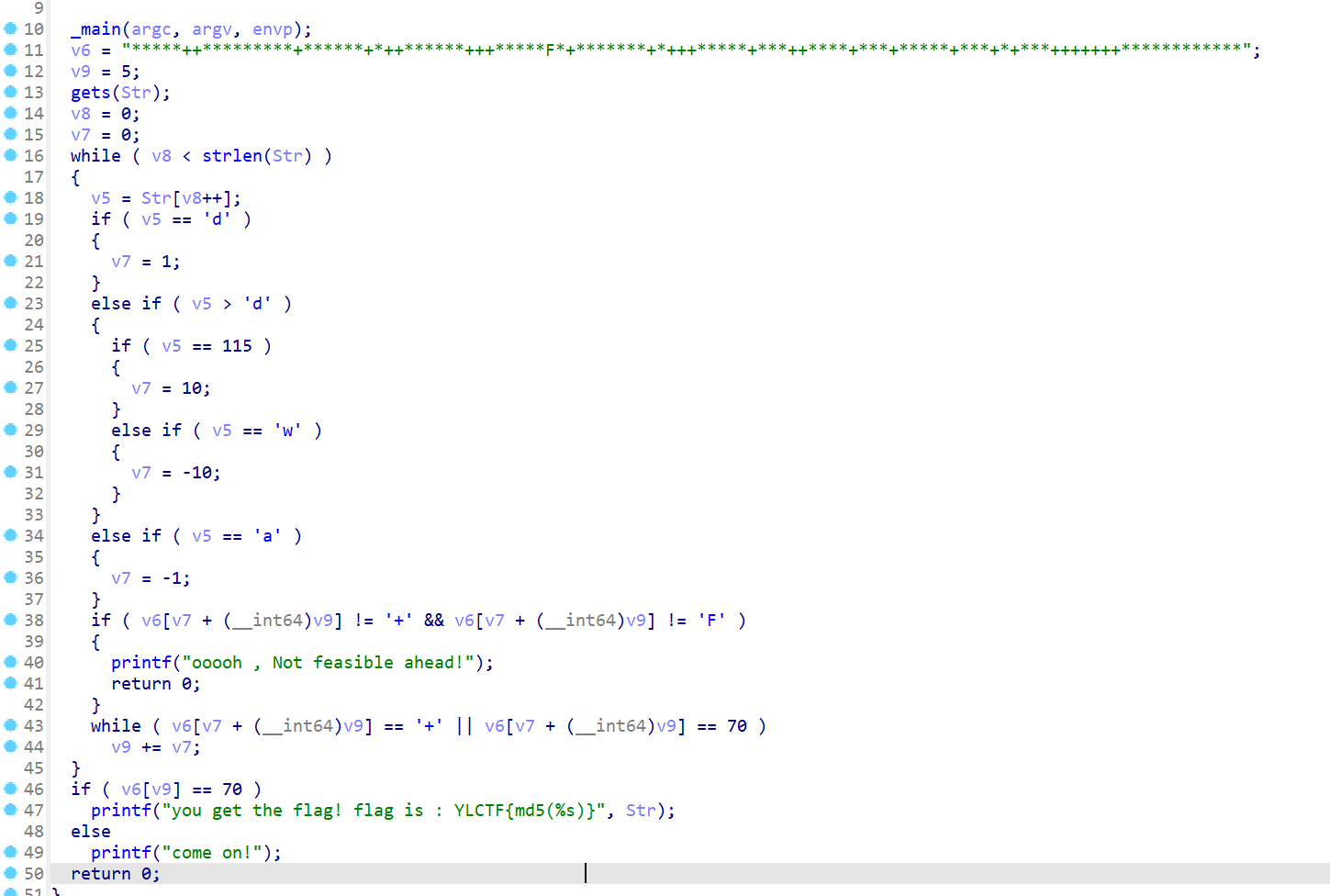
10*10迷宫,第一行第六位为起点,F为终点

YLCTF{efac19a75e413ad6680adec92504b654}
case
你怎么在随机说话啊,当我libc是hellokitty吗
伪随机数异或
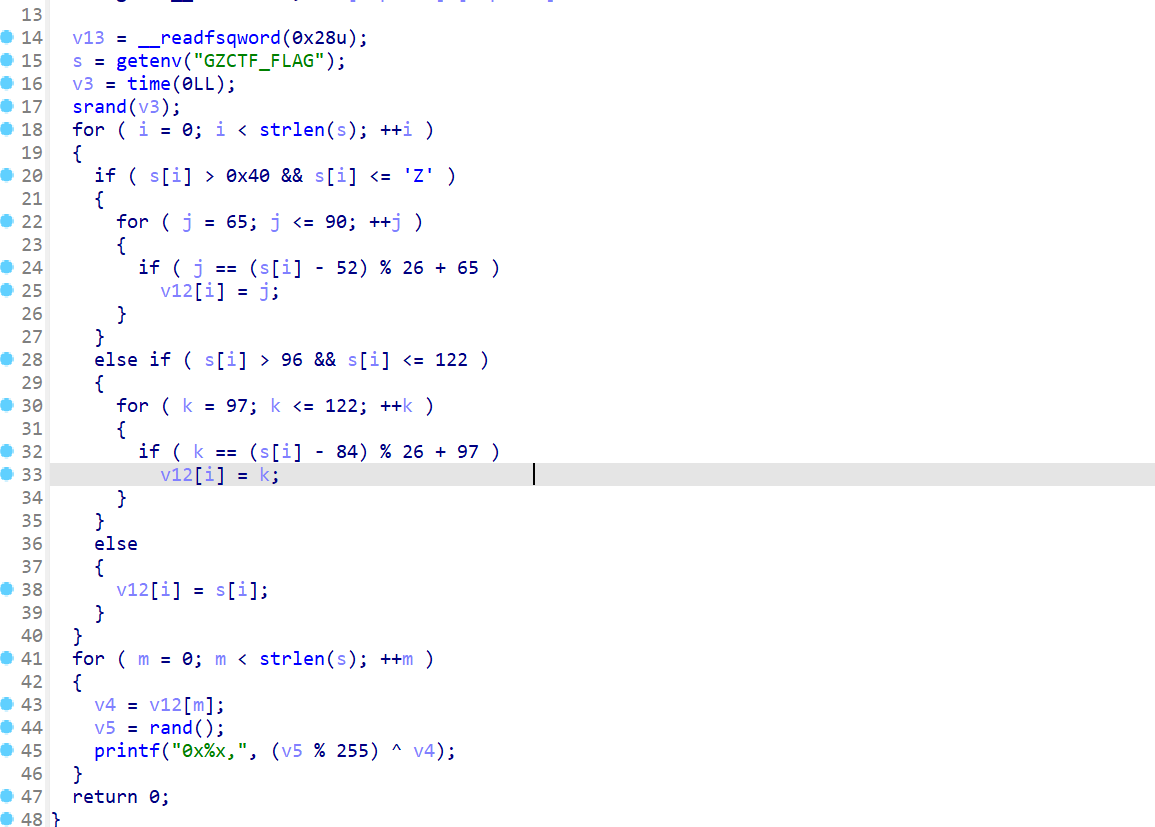
exp
import ctypes
from pwn import *
# 加载 libc.so.6
libc = ctypes.CDLL("./libc.so.6")
p=remote("challenge.yuanloo.com",49275)
enc=p.recv()
# 获取 GZCTF_FLAG 环境变量
encrypted_flag = eval("["+enc.decode()+"]")
libc.srand(int(libc.time(0)))
flag=""
# 遍历每个加密字符
for encrypted_char in encrypted_flag:
rand_value = libc.rand() % 255 # 获取相同的随机值
# 反向求解原始字符的 ASCII 码
char = encrypted_char ^ rand_value
# 反向字符转换
if 65 <= char <= 90: # A-Z
char = char -13
if char < 65 :
char+=26
elif 97 <= char <= 122: # a-z
char = char -13
if char < 97 :
char+=26
else:
char = char # 其他字符不变
flag+=chr(char)
# 输出原始 flag
print("原始 GZCTF_FLAG:", flag)
YLCTF{e3ac3fd2-ce86-423d-8757-113829b60177}
MAZE
uncompyle报错
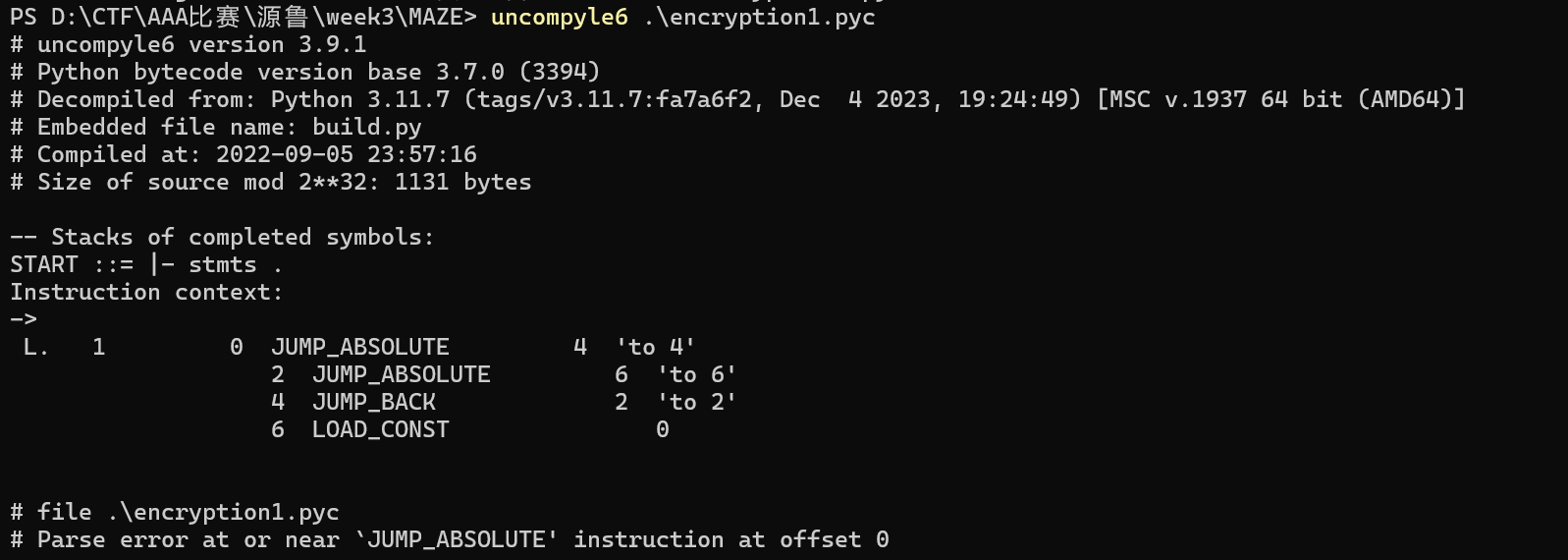

删除花指令
计算co_code长度


import random
T, S, Key = [], [], []
KeyStream = []
T = ["C", "B", "A"]
def init_S():
global S
for i in range(256):
S.append(i)
def init_T():
global T
def swap_S():
j = 0
for i in range(256):
j = (j + S[i] + ord(T[i % 3])) % 256
tmp = S[i]
S[i] = S[j]
S[j] = tmp
def Get_code(text):
global KeyStream
for i in range(4464, 4720):
text[i] ^= KeyStream[i]
def Get_KeyStream(len):
txtlen = len
j, t = (0, 0)
for i in range(txtlen):
i = i % 256
j = (j + S[i]) % 256
tmp = S[i]
S[i] = S[j]
S[j] = tmp
t = (S[i] + S[j]) % 256
KeyStream.append(S[t])
print("easy digitally signed")
fp = open("new_maze.exe", "rb")
text = []
len = fp.seek(0, 2)
fp.seek(0, 0)
for i in range(len):
text.append(int(fp.read(1).hex(), 16))
init_S()
init_T()
swap_S()
Get_KeyStream(len)
Get_code(text)
fp.close()
print(''.join(T))
fp= open(f"new_maze{''.join(T)}.exe","wb")
fp.write(bytearray(text))
fp.close()

哪个能跑哪个就是真的QAQ

打个断点
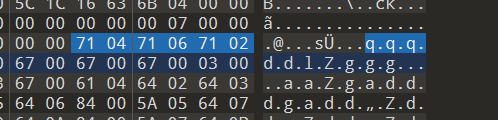
1210000

尼玛,内存攻击

好在maze只是其中一小部分
from idaapi import*
for i in range(121000):
byte=get_byte(0x4384C4+i)
if byte!=0:
print("'"+chr(byte)+"'",end=",")
exp
from collections import deque
# 定义迷宫的行和列
ROWS = 45
COLS = 45
# 初始化迷宫数据
maze=['1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','S','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','1','0','1','1','1','0','0','0','0','0','0','0','1','0','1','0','1','0','0','0','1','1','1','1','0','1','1','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','1','1','0','1','0','1','1','1','1','1','0','1','1','1','0','1','0','1','0','1','0','1','0','1','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','1','0','0','0','0','0','1','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','1','0','1','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','1','0','0','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','0','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','1','1','0','1','1','1','0','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','1','1','0','1','0','1','1','1','1','1','0','1','1','0','0','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','1','1','0','1','1','1','1','1','1','1','0','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','0','1','1','1','1','1','1','1','1','1','1','0','0','0','1','0','0','0','0','0','1','0','1','0','1','0','0','0','1','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','1','0','1','0','0','0','0','0','0','0','1','1','1','1','0','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','0','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','0','1','1','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','1','0','0','0','1','0','1','0','0','0','1','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','1','1','1','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','0','1','1','1','1','1','1','1','1','1','1','1','0','1','1','0','0','0','1','0','0','0','0','0','0','0','0','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','1','0','1','0','0','0','0','0','0','0','0','0','0','0','1','0','1','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','1','1','1','1','0','1','1','1','1','1','0','1','1','1','0','1','1','1','1','1','1','1','0','1','0','1','1','1','0','1','1','0','1','0','0','0','0','0','0','0','1','0','1','0','1','0','0','0','1','0','0','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','1','0','1','0','1','0','0','0','1','1','0','1','0','1','1','1','1','1','0','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','0','1','1','0','0','0','1','0','0','0','0','0','0','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','1','0','1','0','0','0','1','0','0','0','1','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','1','0','1','0','1','0','0','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','1','0','0','0','0','0','0','0','0','0','1','0','0','0','0','0','1','1','1','1','1','1','0','1','1','1','0','1','0','1','0','1','1','1','1','1','0','1','1','1','1','1','1','1','0','1','1','1','1','1','1','1','1','1','1','1','0','1','1','1','1','1','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','1','0','0','0','0','0','1','0','1','1','0','1','0','1','1','1','1','1','1','1','1','1','0','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','0','1','1','0','0','0','0','0','0','0','0','0','1','0','1','0','1','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','0','0','1','0','1','0','1','0','0','0','0','0','0','0','1','1','1','1','0','1','1','1','1','1','0','1','0','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','1','1','1','1','0','1','0','1','0','1','1','1','1','1','1','1','0','1','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','1','0','1','1','0','1','1','1','1','1','0','1','1','1','0','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','0','1','1','1','0','1','1','0','0','0','0','0','0','0','1','0','1','0','1','0','1','0','1','0','0','0','0','0','0','0','0','0','1','0','0','0','1','0','1','0','1','T','0','0','1','0','1','0','0','0','1','1','0','1','0','1','1','1','1','1','0','1','0','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','0','1','1','1','1','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','1','0','1','1','1','1','1','1','0','1','0','1','1','1','1','1','0','1','1','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','1','0','0','0','0','0','1','0','0','0','1','0','0','0','1','0','1','0','0','0','0','0','0','0','1','0','0','0','0','0','1','0','1','0','0','0','0','0','1','0','0','0','1','0','1','1','1','1','0','1','1','1','1','1','0','1','0','1','1','1','0','1','0','1','1','1','1','1','1','1','0','1','1','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','1','0','0','0','1','0','0','0','0','0','0','0','1','0','1','0','0','0','1','0','0','0','1','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','1','0','0','0','1','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','1','1','1','1','0','1','0','1','0','1','0','1','0','1','1','1','1','1','1','1','1','1','0','1','1','1','1','1','0','1','1','0','0','0','1','0','0','0','0','0','1','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','1','0','0','0','1','0','1','0','1','1','0','1','0','1','1','1','0','1','0','1','0','1','0','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','1','1','1','1','0','1','0','1','1','1','0','1','0','1','1','0','1','0','0','0','1','0','1','0','0','0','1','0','0','0','1','0','0','0','1','0','1','0','0','0','0','0','1','0','1','0','1','0','0','0','1','0','1','0','0','0','0','0','1','1','0','1','1','1','0','1','0','1','1','1','1','1','1','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','1','1','1','1','0','1','0','1','1','1','1','1','1','0','0','0','1','0','1','0','1','0','0','0','0','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','0','0','1','0','0','0','0','0','0','0','1','0','0','0','1','0','1','1','0','1','0','1','1','1','0','1','0','1','0','1','0','1','0','1','0','1','0','1','1','1','1','1','1','1','0','1','0','1','0','1','1','1','0','1','1','1','0','1','0','1','0','1','1','0','1','0','0','0','1','0','1','0','1','0','1','0','1','0','0','0','0','0','1','0','1','0','0','0','0','0','1','0','1','0','1','0','0','0','1','0','1','0','1','0','1','0','1','1','0','1','1','1','0','1','0','1','1','1','0','1','1','1','1','1','1','1','1','1','0','1','0','1','1','1','0','1','1','1','0','1','1','1','1','1','0','1','1','1','0','1','0','1','1','0','1','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','0','1','0','0','0','0','0','1','0','0','0','0','0','0','0','0','0','0','0','0','0','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1','1']
# 将迷宫转换为二维矩阵索引
def get_index(row, col):
return row * COLS + col
# 查找起点和终点
def find_start_end(maze):
start = end = None
for i in range(ROWS):
for j in range(COLS):
if maze[get_index(i, j)] == 'S':
start = (i, j)
if maze[get_index(i, j)] == 'T':
end = (i, j)
return start, end
# 广度优先搜索 (BFS)
def bfs(maze, start, end):
# 四个方向:上、下、左、右,并分别对应 "W", "S", "A", "D"
directions = [(-1, 0, 'w'), (1, 0, 's'), (0, -1, 'a'), (0, 1, 'd')]
queue = deque([start])
visited = set()
visited.add(start)
parent = {start: None} # 保存每个节点的前驱
direction_map = {} # 保存每个节点的移动方向
while queue:
current = queue.popleft()
if current == end:
# 找到路径,回溯以输出方向
path = []
dir_path = []
while current:
path.append(current)
if current in direction_map:
dir_path.append(direction_map[current])
current = parent[current]
return path[::-1], dir_path[::-1] # 返回路径和方向(从起点到终点)
# 遍历四个方向
for direction in directions:
new_row, new_col, move = current[0] + direction[0], current[1] + direction[1], direction[2]
if 0 <= new_row < ROWS and 0 <= new_col < COLS: # 确保在边界内
new_pos = (new_row, new_col)
if new_pos not in visited and maze[get_index(new_row, new_col)] != '1': # 避开墙壁
queue.append(new_pos)
visited.add(new_pos)
parent[new_pos] = current
direction_map[new_pos] = move # 保存移动方向
return None, None # 如果没有找到路径
# 查找起点和终点
start, end = find_start_end(maze)
if start and end:
path, directions = bfs(maze, start, end)
if path and directions:
print("找到的路径为:")
for step in path:
print(step)
print("对应的移动方向为:")
print(''.join(directions))
else:
print("没有找到从起点到终点的路径")
else:
print("迷宫中缺少起点或终点")
crypto
QWQ
咦~ 这是什么捏 !(*´・д・)?
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (o^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (o^_^o)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');

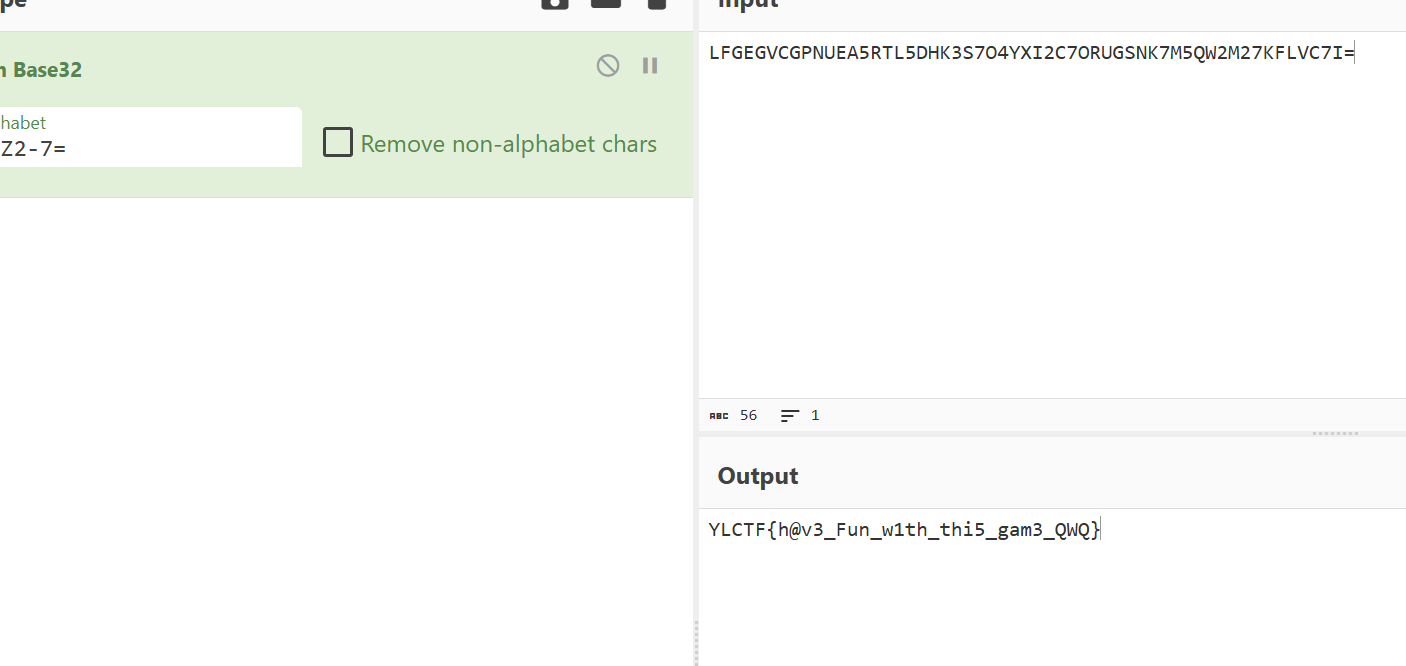
ezlcg
请你解决这么多的线性问题吧.
from Crypto.Util.number import inverse, getPrime, bytes_to_long, long_to_bytes
from random import randrange, randint
from pwn import *
# 给定参数
def solve(a,b,N,num1):
seed = (num1 - b) * inverse(a, N) % N
print(f"Recovered seed: {seed}")
# 使用恢复的 seed 继续后续操作
class LCG(object):
def __init__(self, seed):
self.N = N
self.a = a
self.b = b
self.seed = seed % self.N
self.state = self.seed
def next(self):
self.state = (self.a * self.state + self.b) % self.N
return self.state
# 验证
lcg = LCG(seed)
next_num = lcg.next()
return seed
def slove2(a,N,num1,num2):
b = (num2 - a * num1) % N
# 计算 seed
seed = (num1 - b) * inverse(a, N) % N
return seed
def slove3(a,num1,num2,num3):
a = ((num3 - num2) * inverse(num2 - num1, N)) % N
b = (num2 - a * num1) % N
seed = (num1 - b) * inverse(a, N) % N
return seed
p=remote("challenge.yuanloo.com",40504)
p.recvuntil(b"Round\n")
for i in range(50):
print(i)
p.recvuntil(b"=")
a = int(p.recvline().decode())
print(a)
p.recvuntil(b"=")
b = int(p.recvline().decode())
print(b)
p.recvuntil(b"=")
N = int(p.recvline().decode())
p.recvuntil(b"=")
num = int(p.recvline().decode())
ans=solve(a, b, N, num)
print(ans)
p.sendline(str(ans))
print(p.recvline())
p.recvline()
for i in range(30):
print(i)
p.recvuntil(b"=")
a = int(p.recvline().decode())
print(a)
p.recvuntil(b"=")
N = int(p.recvline().decode())
print(N)
p.recvuntil(b"=")
num1 = int(p.recvline().decode())
p.recvuntil(b"=")
num2 = int(p.recvline().decode())
ans=slove2(a, N, num1, num2)
print(ans)
p.sendline(str(ans))
print(p.recvline())
p.recvline()
for i in range(10):
print(i)
p.recvuntil(b"=")
N = int(p.recvline().decode())
print(N)
p.recvuntil(b"=")
num1 = int(p.recvline().decode())
print(num1)
p.recvuntil(b"=")
num2 = int(p.recvline().decode())
p.recvuntil(b"=")
num3 = int(p.recvline().decode())
ans=slove3(N, num1, num2,num3)
print(ans)
p.sendline(str(ans))
print(p.recvline())
p.interactive()
⭕(二血)
Alice和Bob通过一种量子密码学进行沟通,但是该加密方式存在某种漏洞,导致了Bob的信息密钥泄漏,你可以泄漏出该密钥吗
题目
from sage.all import ZZ, randint
from Crypto.Util.number import *
p = None
def generate_distortion_map(E):
if E.a_invariants() != (0,6,0,1,0):
raise NotImplementedError
return E.isogeny(E.lift_x(ZZ(1)), codomain=E)
def generate_torsion_points(E, a, b):
def get_l_torsion_basis(E, l):
n = (p+1) // l
return (n*G for G in E.gens())
P2, Q2 = get_l_torsion_basis(E, 2**a)
P3, Q3 = get_l_torsion_basis(E, 3**b)
return P2, Q2, P3, Q3
from flag import flag
flag = bytes_to_long(flag)
def generate_key(E_start, b, P2, Q2, P3, Q3):
bobs_key = flag
K = P3 + bobs_key*Q3
phi = E_start.isogeny(K, algorithm="factored")
EB = phi.codomain()
EB.set_order((p+1)**2, num_checks=0)
PB, QB = phi(P2), phi(Q2)
return bobs_key, EB, PB, QB
a = 305
b = 192
p = 2^a*3^b - 1
Fp2.<i> = GF(p^2, modulus=x^2+1)
R.<x> = PolynomialRing(Fp2)
E_start = EllipticCurve(Fp2, [0,6,0,1,0])
E_start.set_order((p+1)^2)
two_i = generate_distortion_map(E_start)
P2, Q2, P3, Q3 = generate_torsion_points(E_start, a, b)
flag_key, EB, PB, QB = generate_key(E_start, b, P2, Q2, P3, Q3)
print(EB)
print(PB)
print(QB)
"""
Elliptic Curve defined by y^2 = x^3 + 6*x^2 + (1109655386602666580941477264844188509870568726343453010771770543665511250648180561681677488303290640863245633469198578301207900328491716466654470349910400724631139969542193124833051079*i+2116239248619087101677214169270633679594454755906693836568034229947351325062332338053907457802709748610111020509037164276717020111001082512633925347579357851693517057782645336434230575)*x + (783233241190388171387544682511032475647421068250023300290363249038620119995420899574317207343308349718411589404085433006020673690798356551667106568546291827001684869794402242067695854*i+1972744566958070881282131795626840370625118459932253321456562523309337576438614381897961997884583203821363249684189786452976563714388989414218292121069137192174721660268448964759287049) over Finite Field in i of size 2638940411073262671963620699288286770183560231187222316750407556465639836010558150163225530335162533481049256757217964651333810422125728537407397155806079217346919294449255613110157311^2
(1792805099210360888864761590321391235025824991548234912676247217808406536821234881384389175924130468280991088357660252370848305634037983159579204419296531735459329230669983096853856246*i + 171253309786548245036128932419221024429140017061733162803654587078736014845338272553757000723916403099300493601067652633948439740076865619503812837361164299530464912490228468097800783 : 354858932953470647164407208876248915819655125217303333206005726572045601374950018701435041440177841288062762055220650414072032960690957944114792835539535784706989279413982852603736575*i + 652241231208054817913369235175691302162155547428861981772486556413182925887029191547328926720048813218596706336154397071250972427384520853013935344373831652140490902941929446372831718 : 1)
(2186267301001259402114997355550578512125192708867710349339620240110565042023451739162302255305174185314466942521888744412961910909391429250064295777978302914701578195376147036042606489*i + 1113400569081370973415138408967328130898700595223023714237127216136706721906751381588571638690905466982759185164650150666678077272021890081392532363649111691002821924551541633624805969 : 475011489753746240024500178367364859418901588829939924748705578009262827369222834659815495729670558797454143390912073311509838111085236909370323483802926909195458815683174215323355088*i + 925039345882842856209794407096335244092780460386698951051338086161413597699668891541282650447520394073160493795142052782764553543711321165686302397695781016000953589530090195707014184 : 1)
"""
修改项目做的,sage版本要求9.5以上
论文An efficient key recovery attack on SIDH
应该还可以直接利用write-up/2022/RCTF/S2DH at master · pcw109550/write-up
# Local imports
import public_values_aux
from public_values_aux import *
# Load Sage files
load('castryck_decru_shortcut.sage')
# Baby SIKEp64 parameters
a = 305
b = 192
p = 2^a*3^b - 1
public_values_aux.p = p
Fp2.<i> = GF(p^2, modulus=x^2+1)
R.<x> = PolynomialRing(Fp2)
E_start = EllipticCurve(Fp2, [0,6,0,1,0])
E_start.set_order((p+1)^2) # Speeds things up in Sage
# Generation of the endomorphism 2i
two_i = generate_distortion_map(E_start)
# Generate public torsion points, for SIKE implementations
# these are fixed but to save loading in constants we can
# just generate them on the fly
P2, Q2, P3, Q3 = generate_torsion_points(E_start, a, b)
check_torsion_points(E_start, a, b, P2, Q2, P3, Q3)
# Generate Bob's key pair
bob_private_key, EB, PB, QB = gen_bob_keypair(E_start, b, P2, Q2, P3, Q3)
print(bob_private_key)
# Define the finite field
p = 2**305 * 3**192 - 1
Fp2.<i> = GF(p^2, modulus=x^2+1)
# Coefficients from the output curve
a4 = (1109655386602666580941477264844188509870568726343453010771770543665511250648180561681677488303290640863245633469198578301207900328491716466654470349910400724631139969542193124833051079*i +
2116239248619087101677214169270633679594454755906693836568034229947351325062332338053907457802709748610111020509037164276717020111001082512633925347579357851693517057782645336434230575)
a6 = (783233241190388171387544682511032475647421068250023300290363249038620119995420899574317207343308349718411589404085433006020673690798356551667106568546291827001684869794402242067695854*i +
1972744566958070881282131795626840370625118459932253321456562523309337576438614381897961997884583203821363249684189786452976563714388989414218292121069137192174721660268448964759287049)
# Create the elliptic curve
EB = EllipticCurve(Fp2, [0, 6, 0, a4, a6])
# Point PB coordinates
PBx = (1792805099210360888864761590321391235025824991548234912676247217808406536821234881384389175924130468280991088357660252370848305634037983159579204419296531735459329230669983096853856246*i +
171253309786548245036128932419221024429140017061733162803654587078736014845338272553757000723916403099300493601067652633948439740076865619503812837361164299530464912490228468097800783)
PBy = (354858932953470647164407208876248915819655125217303333206005726572045601374950018701435041440177841288062762055220650414072032960690957944114792835539535784706989279413982852603736575*i +
652241231208054817913369235175691302162155547428861981772486556413182925887029191547328926720048813218596706336154397071250972427384520853013935344373831652140490902941929446372831718)
# Create point PB
PB = EB(PBx, PBy)
# Point QB coordinates
QBx = (2186267301001259402114997355550578512125192708867710349339620240110565042023451739162302255305174185314466942521888744412961910909391429250064295777978302914701578195376147036042606489*i +
1113400569081370973415138408967328130898700595223023714237127216136706721906751381588571638690905466982759185164650150666678077272021890081392532363649111691002821924551541633624805969)
QBy = (475011489753746240024500178367364859418901588829939924748705578009262827369222834659815495729670558797454143390912073311509838111085236909370323483802926909195458815683174215323355088*i +
925039345882842856209794407096335244092780460386698951051338086161413597699668891541282650447520394073160493795142052782764553543711321165686302397695781016000953589530090195707014184)
# Create point QB
QB = EB(QBx, QBy)
# Set the order of the curve
EB.set_order((p+1)**2, num_checks=0)
print("Conversion complete. The variables EB, PB, and QB now contain the curve and points.")
# 验证恢复是否成功
print(EB)
print(PB)
print(QB)
print(type(EB))
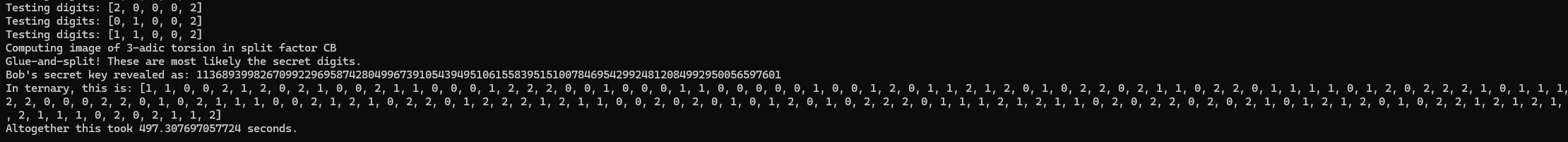
solution = Integer(bob_private_key).digits(base=3)
print(f"Running the attack against Baby SIDHp64 parameters, which has a prime: 2^{a}*3^{b} - 1")
print(f"If all goes well then the following digits should be found: {solution}")
# ===================================
# ===== ATTACK ====================
# ===================================
def RunAttack(num_cores):
return CastryckDecruAttack(E_start, P2, Q2, EB, PB, QB, two_i, num_cores=num_cores)
if __name__ == '__main__' and '__file__' in globals():
if '--parallel' in sys.argv:
# Set number of cores for parallel computation
num_cores = os.cpu_count()
print(f"Performing the attack in parallel using {num_cores} cores")
else:
num_cores = 1
recovered_key = RunAttack(num_cores)
misc
Blackdoor
小明的网站被黑了,你能帮小明分析一下网站后门吗?
Webshell后门的密码(已经做了md5加密)即为答案。
FLAG格式:YLCTF{后门密码}
seay直接扫