CrownJewel-1
Forela 的域控制器受到攻击。据信域管理员帐户已被盗用,并且怀疑威胁行为者在 DC 上转储了 NTDS.dit 数据库。我们刚刚收到了 DC 上使用 vssadmin 的警报,由于这不是例行计划的一部分,我们有充分的理由相信攻击者滥用了这个 LOLBIN 实用程序来获得域环境皇冠上的明珠。对提供的工件进行一些分析,以便快速分类,如果可能,请尽早踢出攻击者。
Task 1
Attackers can abuse the vssadmin utility to create volume shadow snapshots and then extract sensitive files like NTDS.dit to bypass security mechanisms. Identify the time when the Volume Shadow Copy service entered a running state.
攻击者可以滥用 vssadmin 实用程序创建卷影快照,然后提取敏感文件(如 NTDS.dit)以绕过安全机制。确定卷影复制服务进入运行状态的时间。
cnm美国时区,系统默认北京时区还得-8小时
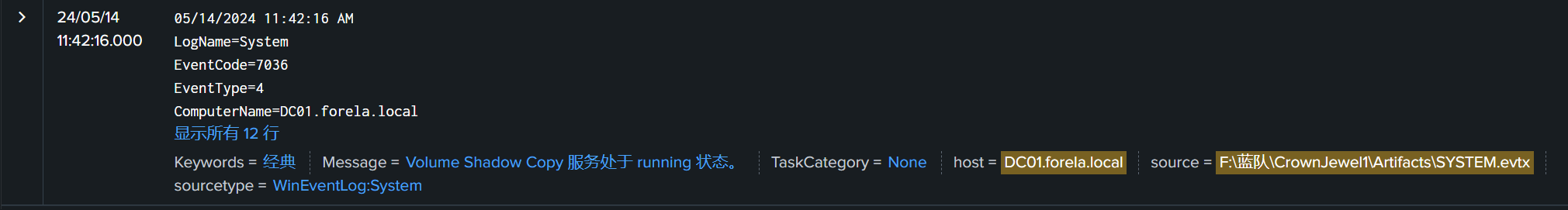
2024-05-14 03:42:16
Task 2
When a volume shadow snapshot is created, the Volume shadow copy service validates the privileges using the Machine account and enumerates User groups. Find the two user groups the volume shadow copy process queries and the machine account that did it.
创建卷影快照时,卷影复制服务使用计算机帐户验证权限并枚举用户组。找到两个用户组:卷影复制进程查询和执行该操作的计算机帐户。
这题也出生,每个逗号后面要加空格。。。
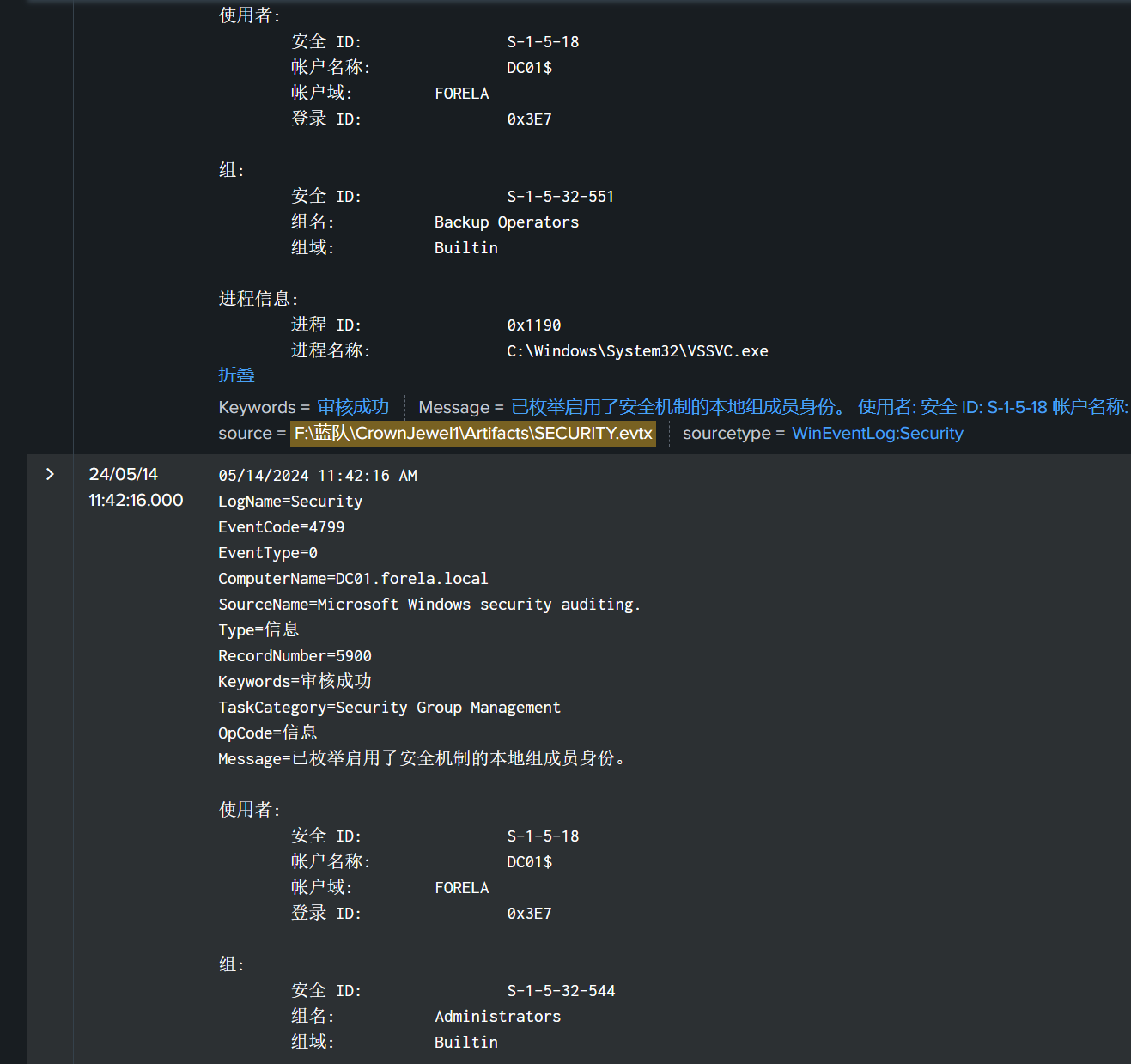
Administrators, Backup Operators, DC01$
Task 3
Identify the Process ID (in Decimal) of the volume shadow copy service process.
确定卷影复制服务进程的进程 ID(以十进制为单位)。
正则搜索Message="*vss*"
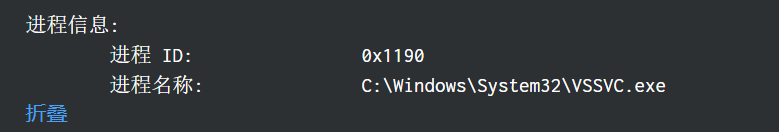
答案要求十进制4496
Task 4
Find the assigned Volume ID/GUID value to the Shadow copy snapshot when it was mounted.
在挂载卷影复制快照时,找到分配给卷影复制快照的卷 ID/GUID 值。
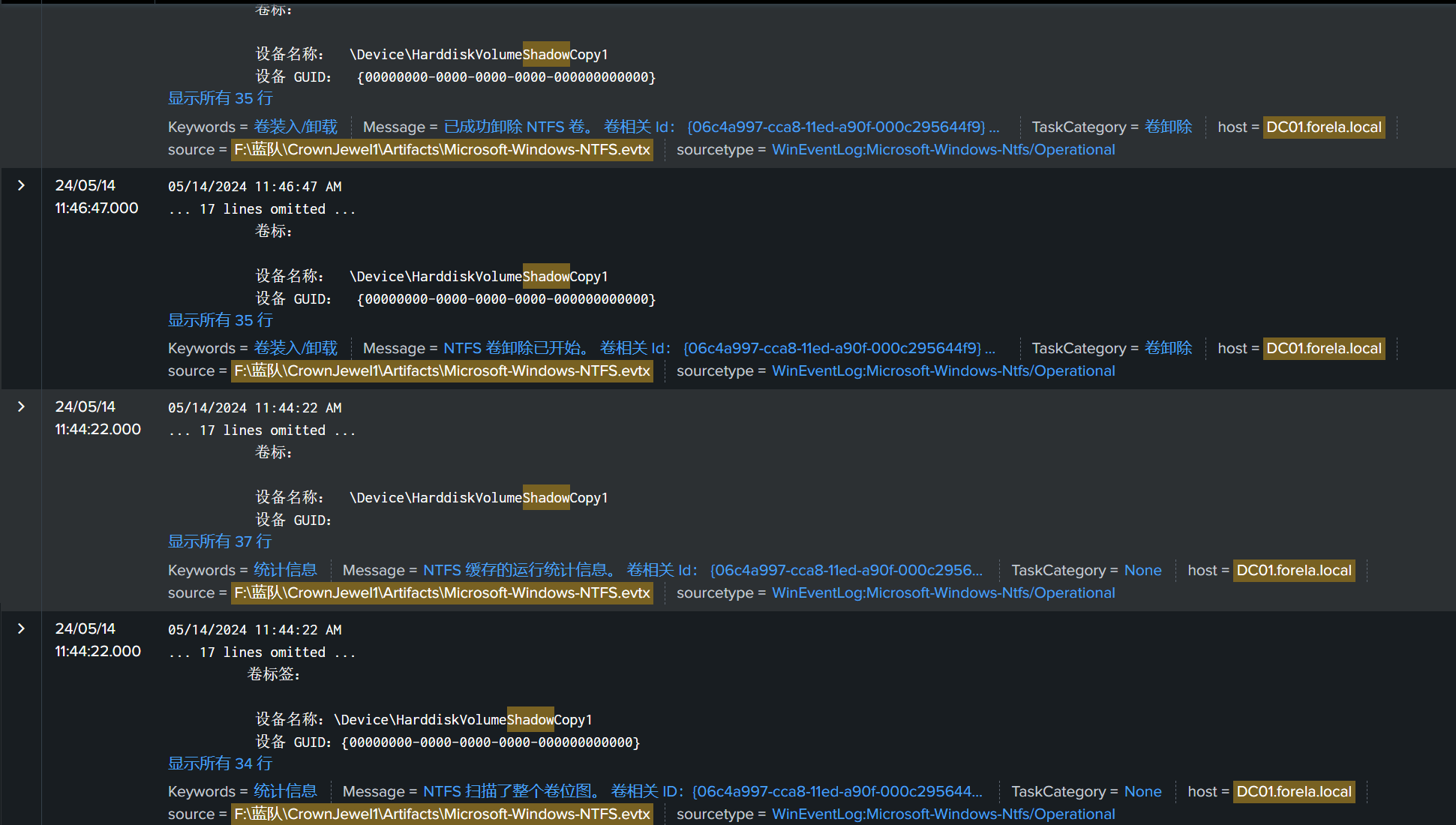
{06c4a997-cca8-11ed-a90f-000c295644f9}
Task 5
Identify the full path of the dumped NTDS database on disk.
确定磁盘上转储的 NTDS 数据库的完整路径。
DiskGenius加载虚拟磁盘
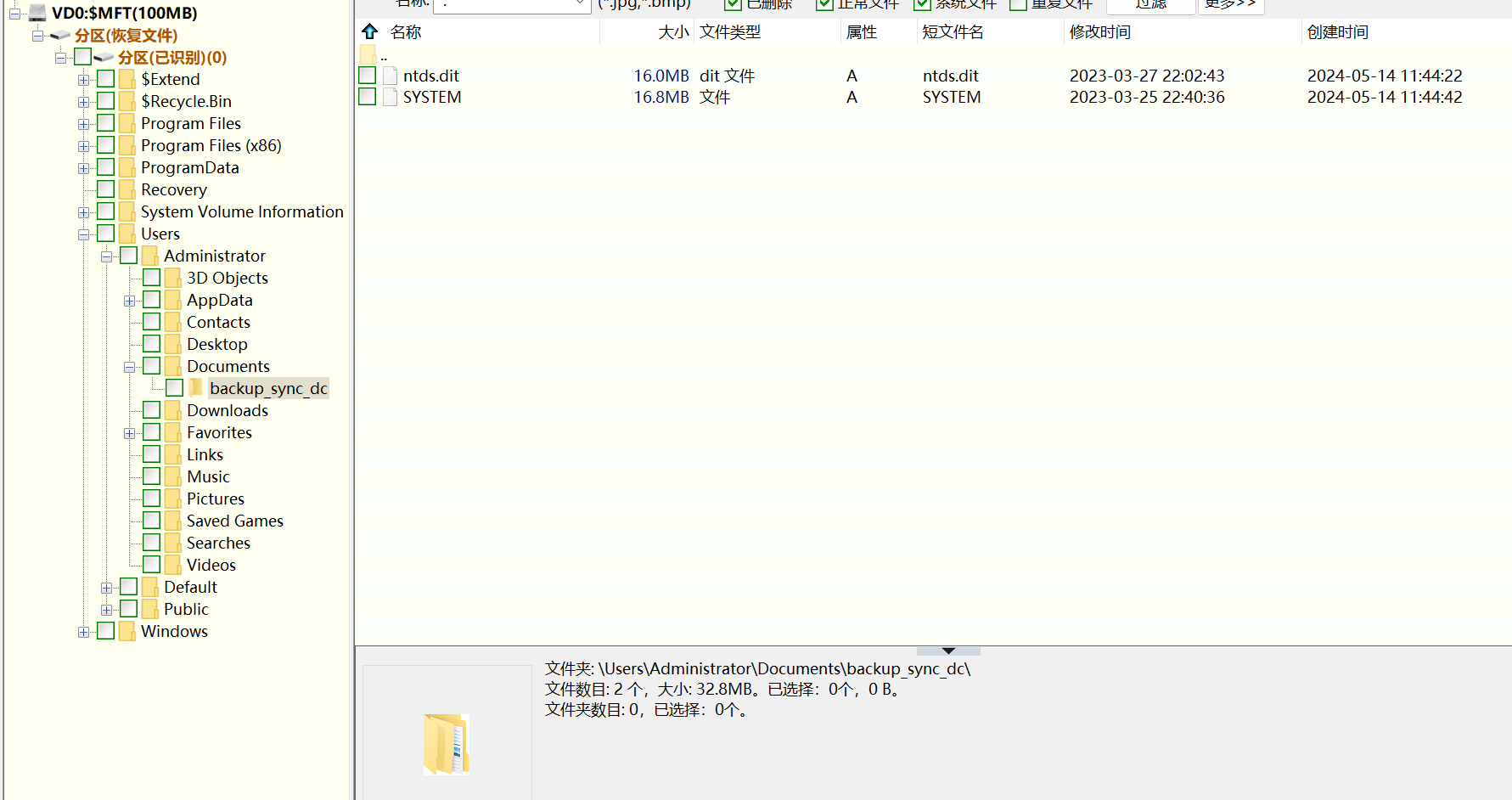
C:\Users\Administrator\Documents\backup_sync_dc\ntds.dit
Task 6
When was newly dumped ntds.dit created on disk?
新转储的 ntds.dit 是何时在磁盘上创建的?
2024-05-14 11:44:22 - 3h
2024-05-14 03:44:22
Task 7
A registry hive was also dumped alongside the NTDS database. Which registry hive was dumped and what is its file size in bytes?
注册表配置单元也与 NTDS 数据库一起转储。转储了哪个注册表配置单元,其文件大小(以字节为单位)是多少?
1.1MB=17563648B
SYSTEM, 17563648

