队伍获得赛道第四
以下为比赛时部分记录下来的个人题解
ssh登入
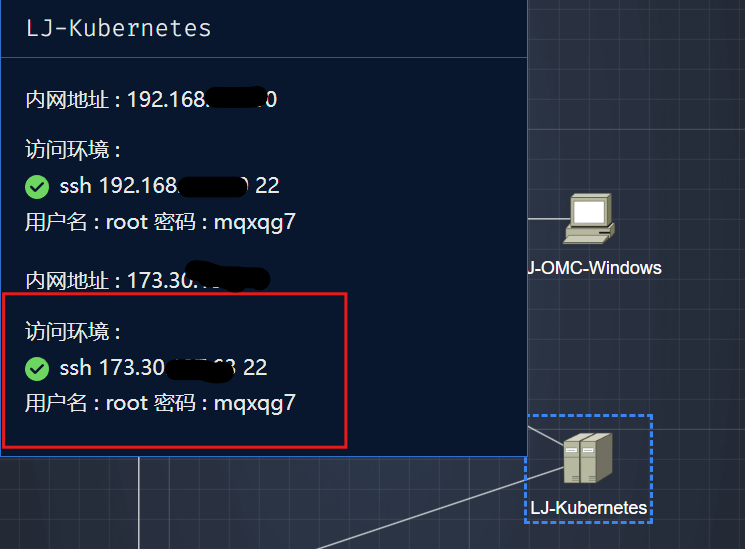
6. [k8s-check6] 攻击者为了能够持久控制集群,在服务器中留下了后门,用于正向连接集群服务器,请删除该后门
root@ubuntu18:~# rm .ssh/authorized_keys
cmd执行,ssh端口转发打内网
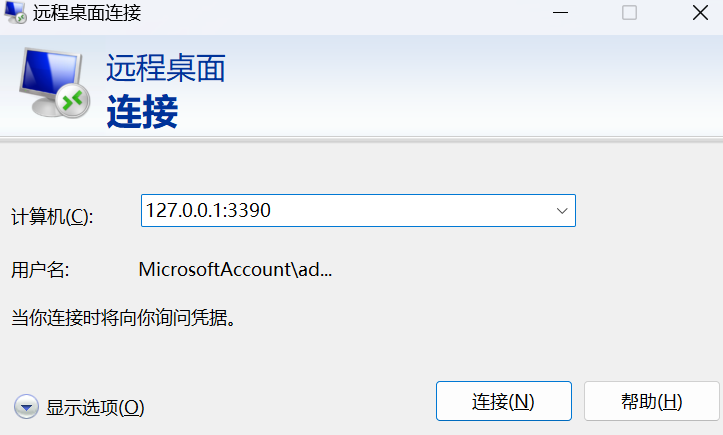
ssh -L 3390:192.168.20.201:3389 [email protected]
rdp
1. [DS-Check-1] 攻击者通过密码喷洒,成功以管理员身份登陆并接管了“智控运维平台”。请尝试对管理员密码进行加固。(将密码改为:PdzOy!ouI#nR6Z8)
mssql数据库1433端口弹出来
ssh -L 1433:192.168.20.201:1433 [email protected]
sa/CkXpZ!KqtO*Zn6连接上去(mssql管理工具或navicat)
bcrypt 11轮
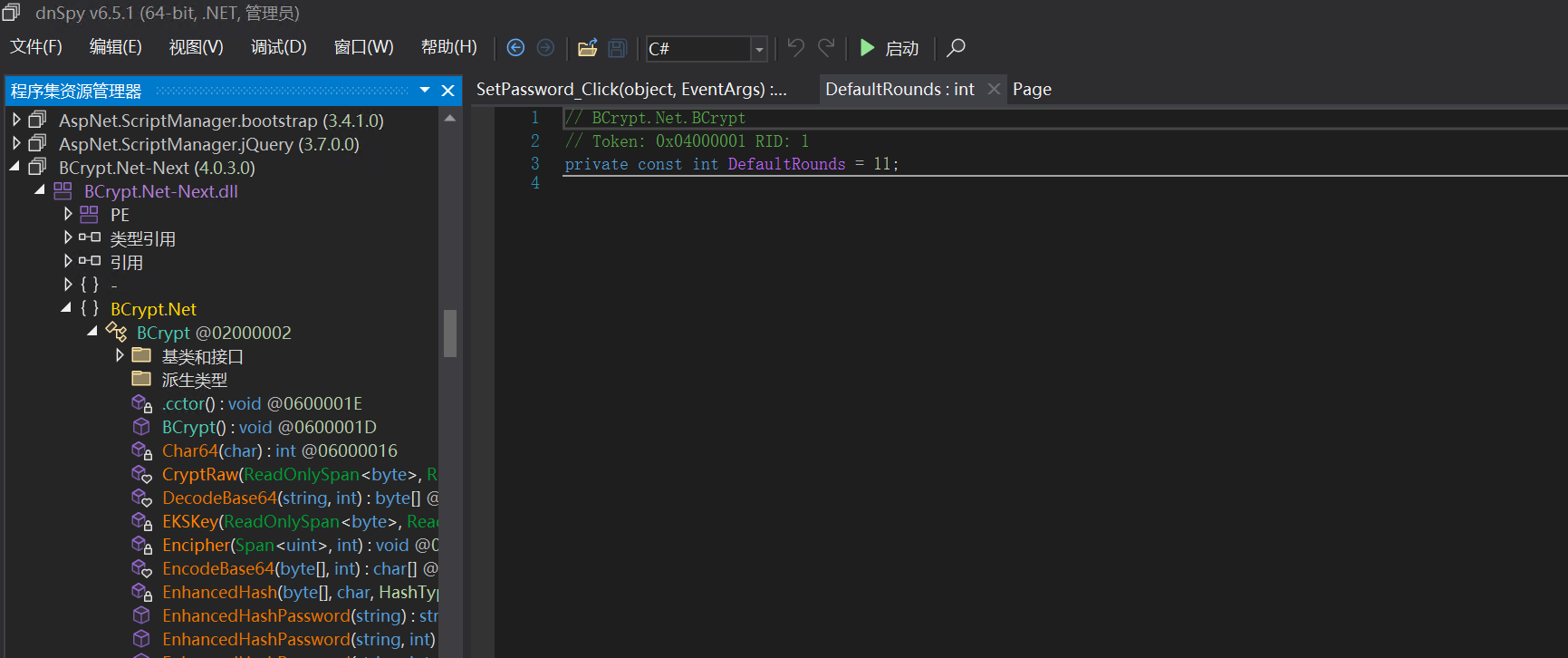
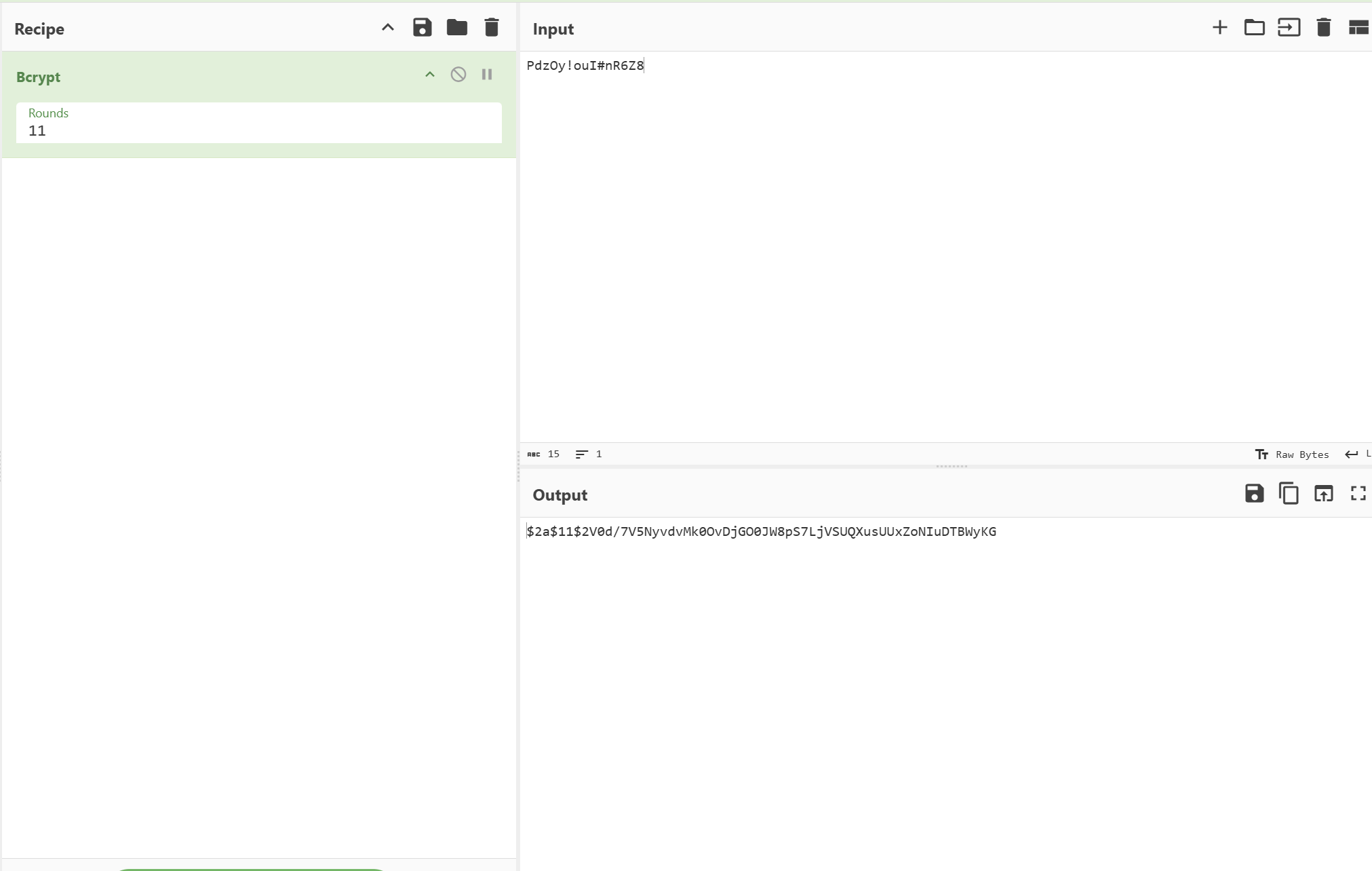
执行修改密码hash
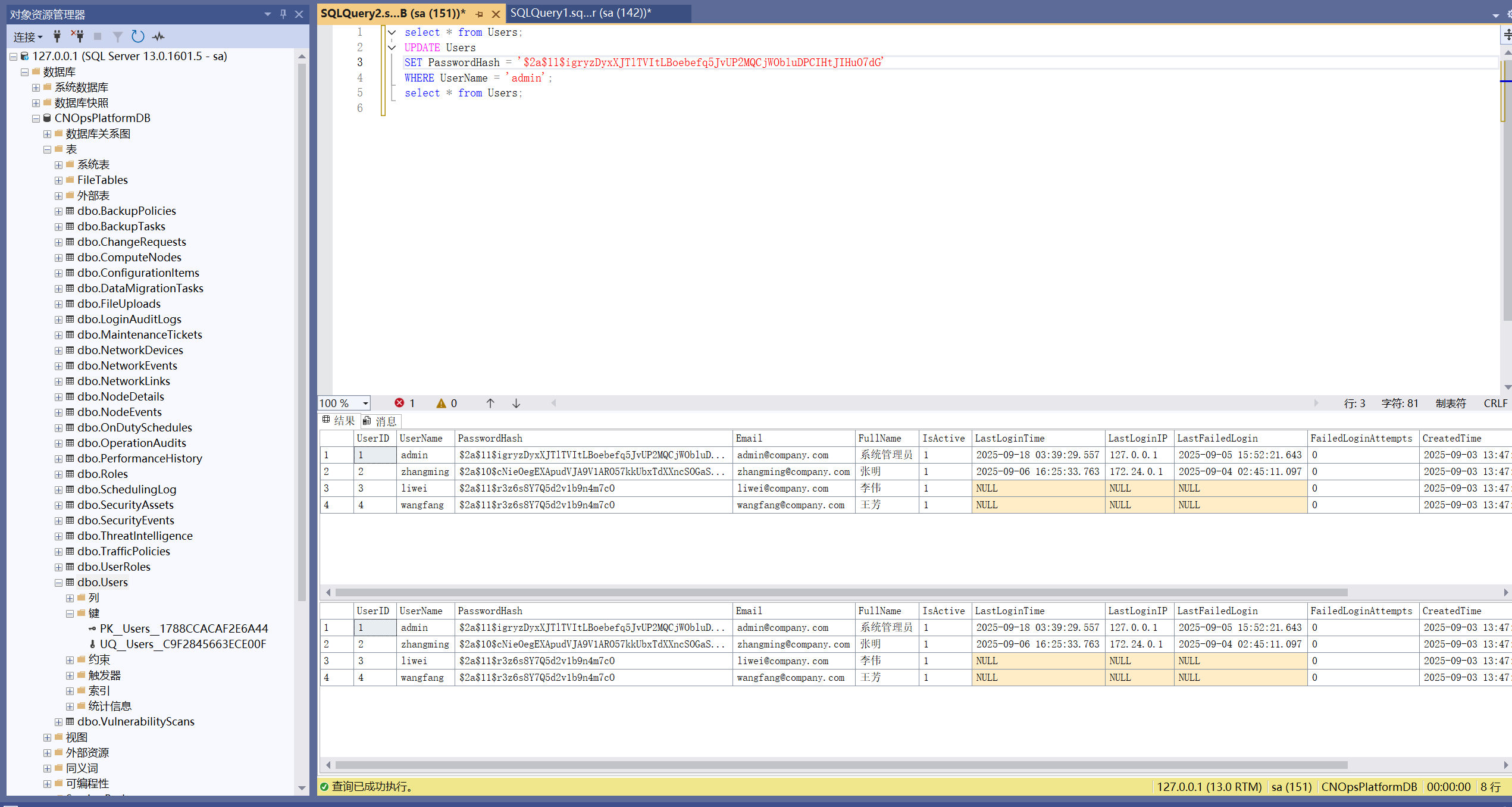
select * from Users;
UPDATE Users
SET PasswordHash = '$2a$11$igryzDyxXJTlTVItLBoebefq5JvUP2MQCjWObluDPCIHtJIHuO7dG'
WHERE UserName = 'admin';
select * from Users;
9. [DS-Check-9] 请尝试找到攻击者在“智控运维平台”中部署的 Web 后门,并对该后门及其可能造成的后续威胁进行清理与阻断。
D盾扫
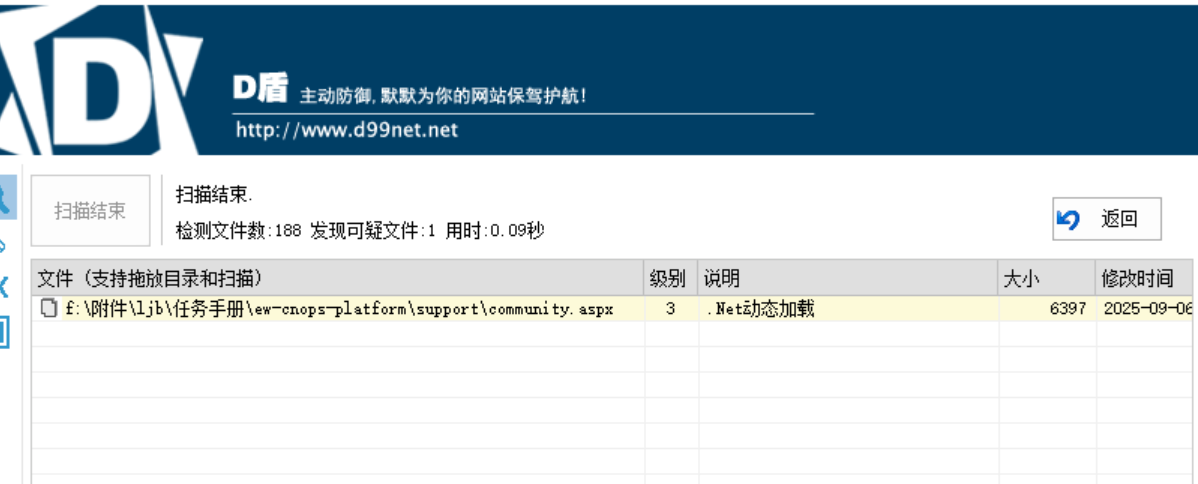
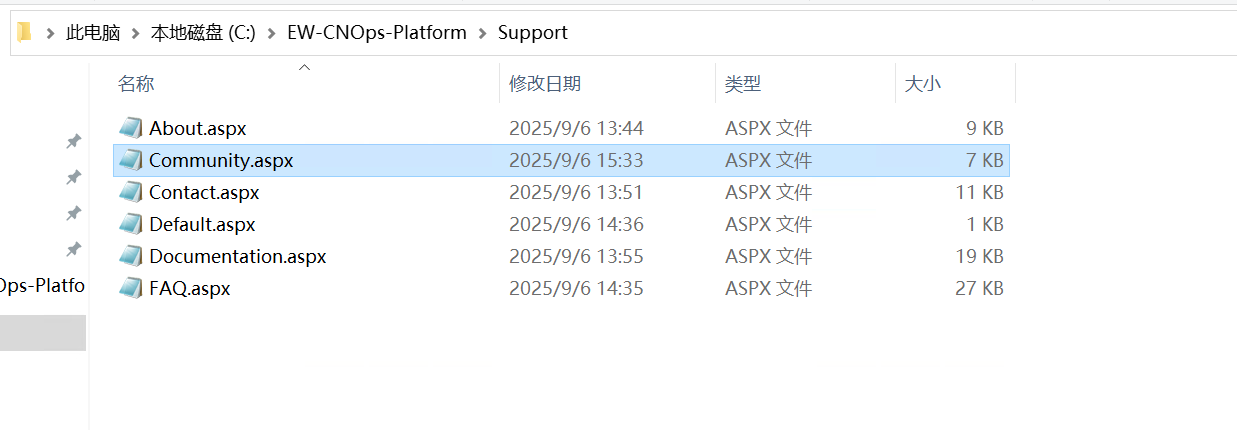
rdp登入后删除如下后门文件
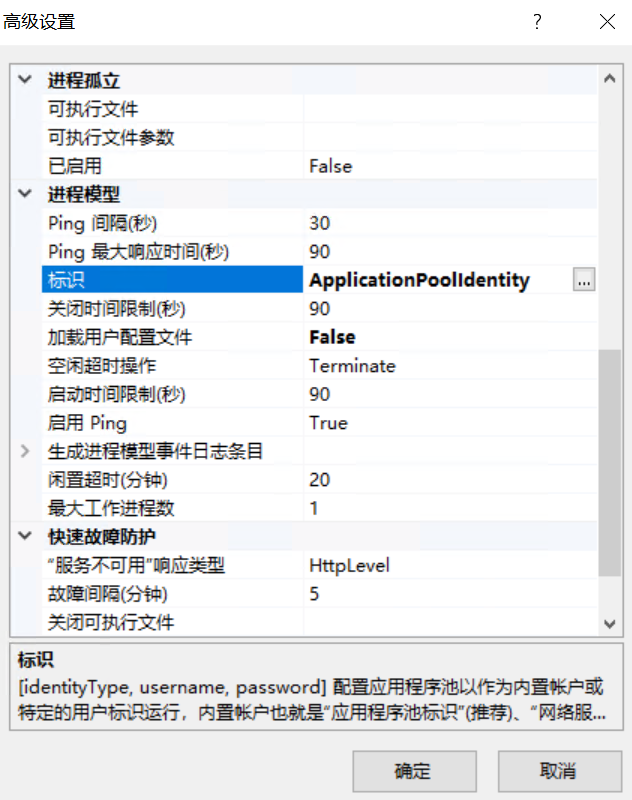
10. [DS-Check-10] 攻击者修改了“智控运维平台”网站的运行权限。请尝试将该网站的运行权限恢复为“应用程序池标识”帐户。
IIS应用程序池-标识
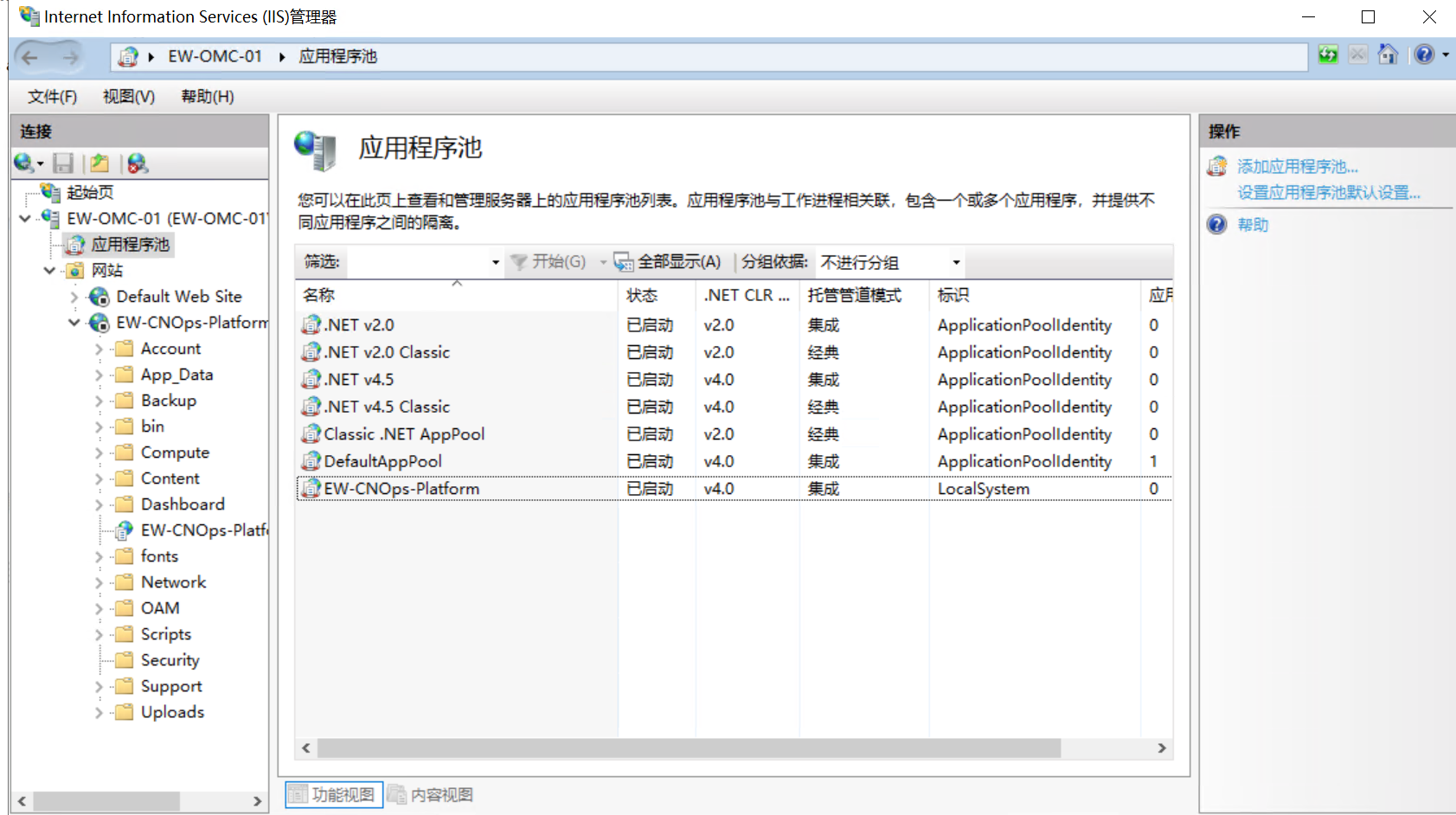
localsystem改为ApplicationPoolIdentity
8. [k8s-check8] 攻击者入侵了Kubernetes集群,创建了一个高权限凭证用于持久化,创建的凭证会在什么时候过期?请在/root/flags/flag8.txt中写入证书过期时间,例如:2030/10/10/10:10:10
root@ubuntu18:~# cat /etc/kubernetes/kubelet-user.config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: ""
server: https://192.168.58.2:8443
name: minikube
contexts:
- context:
cluster: minikube
user: kube-admin
name: minikube
current-context: minikube
kind: Config
preferences: {}
users:
- user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNnVENDQVdtZ0F3SUJBZ0lRYUdDVGRWSldGSjNyV2gvNXNtRVo1akFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwdGFXNXBhM1ZpWlVOQk1CNFhEVEkxTURrd09ERTBOVEl4T0ZvWERUSTJNRGt3T0RFMApOVEl4T0Zvd0lERUpNQWNHQTFVRUNoTUFNUk13RVFZRFZRUURFd3ByZFdKbExXRmtiV2x1TUlHZk1BMEdDU3FHClNJYjNEUUVCQVFVQUE0R05BRENCaVFLQmdRRG5IVEUwY2k3KzMzWWFHNEdTVjNIMkFYVEFPdlZVRFpVa2JuUUcKNGVLT2tHb2hXTnVkUjN5UXNSb1Q4RkxlU3FXNGpEdHZWam5yM0NiVUEvd0swSEYxdGVSZm9scjFCd2VWR0QrbwpaZ3Q5U2RMYTNmQWJTY1k4NTUrNjBQUkNXdnYwQUpzNzlWZ21FR2QxTWptRFlxYXFRUmhDdnc5ZFpIMVZqVnNLCjhoZUJJd0lEQVFBQm8wWXdSREFUQmdOVkhTVUVEREFLQmdnckJnRUZCUWNEQWpBTUJnTlZIUk1CQWY4RUFqQUEKTUI4R0ExVWRJd1FZTUJhQUZQQ3NFbGdVZnd2YWlnQVQvcHZ4L2Y5MnpHdWdNQTBHQ1NxR1NJYjNEUUVCQ3dVQQpBNElCQVFBRldQYnhFa3FuOWRaWXgremI2L2Erdnd6bjFOclRRNUlvd2tCKzI1Ym1POVVWc00zN0hvOGxmTWhJClVZNisrTndXZHk5Qzc3MkpqYVdiVUZKMmRiNFNzdHI2RkVpZGNtMHlBTTRSOExKeUVEUk1lNk1KbjlET1ViZHUKdHlkNUhMTmdMWGwra1dGaVZjTjgrMlBEOFlleXJmOXUvZ3RCTVpzakExNm5icTRkblpUemgwMmdEakdvNWVLQQo1b09ldVgvKy8vT244TU0yWUJWeDF2OU9PQnBRSFpsYUZ4SVRoeDF3aVMzT2tkQmJPc1RrVXVuSC9GTU5ia045Ci9RWVNvSllXbDVxSFR1Z3RnTEZyekZuYllQakFyem9zb3B1ZEI2S2wwWXRpNXZtK2xwbWIyNSs0OHcreE9HZHYKaGZ3dE03czRDenZSTll6QXBacnI1SjQ1TFhIUgotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlDWGdJQkFBS0JnUURuSFRFMGNpNyszM1lhRzRHU1YzSDJBWFRBT3ZWVURaVWtiblFHNGVLT2tHb2hXTnVkClIzeVFzUm9UOEZMZVNxVzRqRHR2VmpucjNDYlVBL3dLMEhGMXRlUmZvbHIxQndlVkdEK29aZ3Q5U2RMYTNmQWIKU2NZODU1KzYwUFJDV3Z2MEFKczc5VmdtRUdkMU1qbURZcWFxUVJoQ3Z3OWRaSDFWalZzSzhoZUJJd0lEQVFBQgpBb0dBU091WENOczJKTWpROUsvVkZCMXZJWldZQnNjVGZPL0VMUGlFdDE4eUlwVkNSejlJRzduZ2ZhN0RjYU1VCkluc2ZDcm1FVHo2L2k4R3NwcHlUTzc1RTdhdHIwWUVaWCtRdzhzbmRQemRndmdObFVzNm51U25EaWtHQmRRMTYKSG0zMFgxdzRHUVNaUm42Y25JajlHT2Jjc2daeGs2YkZrQ2ZZcWU5MjRUZWhQR0VDUVFENHpyc1l3a2FNRjc4MQppUjVxY2JseURibFBkRWNkVXBxSTJzSXp2OWNDVHZqYkI5dUNabjU3ejd2Zmw2M0NOcG1Sam1zQ29mdkE3M2J3Ci9Mc0phMGNyQWtFQTdjdUYwcTNLUkZxa0FmWGpWZzA3TmtvZUtpV3FBejNIbU9MWnJTK0VrNWlXTnhhUlpHR1AKSGt3cVFzbzRiQXlkbFpIS0tiU2hoMUVpYmJXVnVqMng2UUpCQUxKWGZNVENmTTd1TnFDcEtLUWo0RWxnalBQbQo1Uktmb3lWMXFMNXZSQzdqYkgyVHBFUlVNMVdNRVo2em1sa2J5ZmdMbmFqRmN5OVlkbWxHdnNxQm13RUNRUUNyCmFONnhLL2MyYUlQNnFjMVN0VHp1ZUdUZ0NzQlBqOVAxMytmN0Q5cW9MZ0J4KzBHWXN6NWdINVVEQ2hPN3h5ZzgKclplbGtvQXhNNG4ydlVNTnVmVXBBa0VBNXJHVmxSUDdXMzdyVUZnWEs5QXErMUp2UVdhMGVQNWVNMjFkdklOYwpjZlpya3VGZlFjcmdkQ21BK1lQNUc0QjdENDh0bnlFWUUrQzV3MXV0bDdmMGhBPT0KLS0tLS1FTkQgUlNBIFBSSVZBVEUgS0VZLS0tLS0K
name: kube-admin
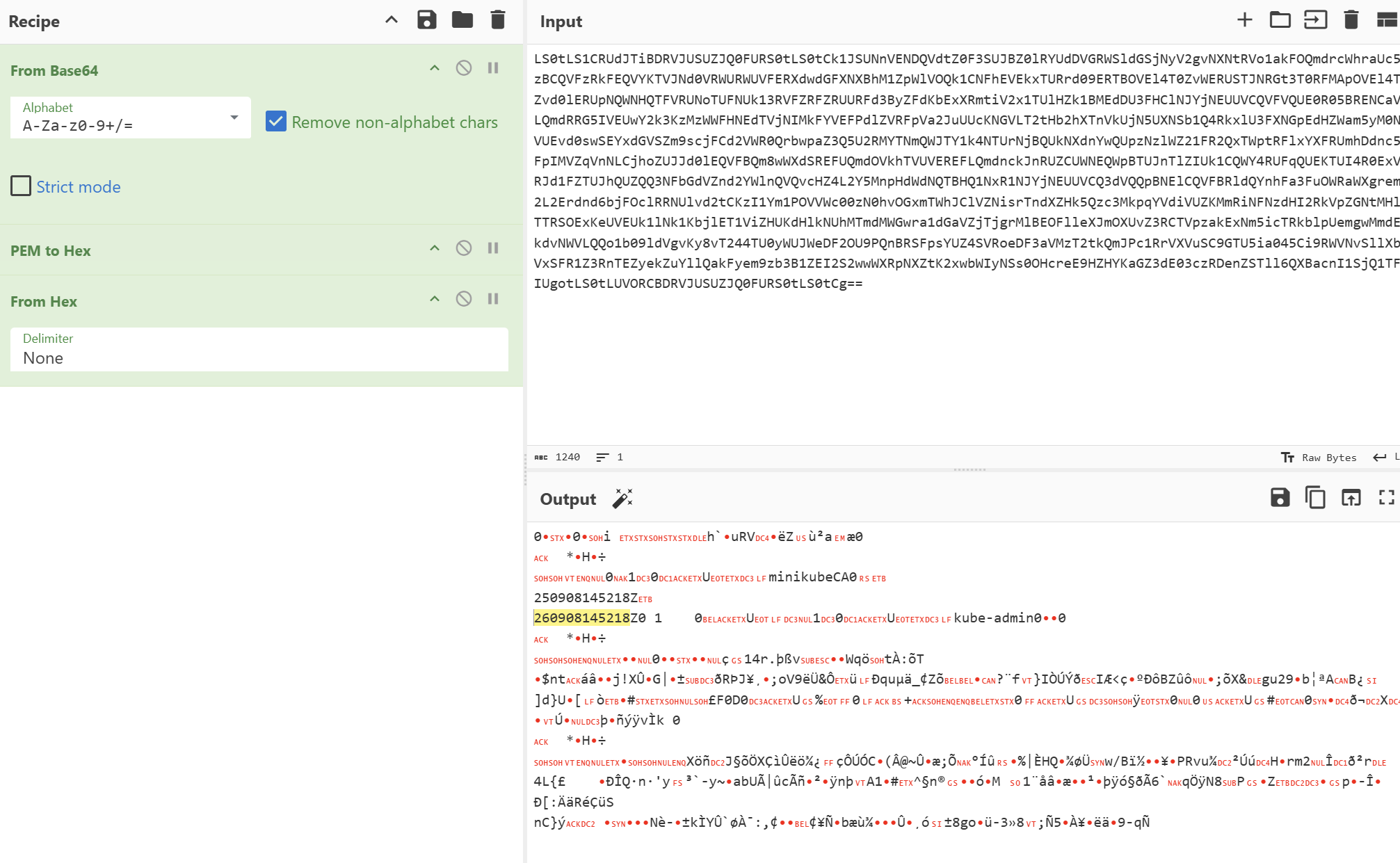
root@ubuntu18:~# echo '2026/09/08/14:52:18' > /root/flags/flag8.txt

